1. Asset Discovery with vsftpd 3.0.3
1.1. Services Offered: Host Discovery with vsftpd 3.0.3
In this target range, SEPPUKU[1], the IP address is specified, so the host discovery process is not involved while using vsftpd 3.0.3.
1.2. Service Discovery (Port, Service, Component, Version)
Using the command sudo -u root nmap 172.16.33.62 -n -Pn -p- --reason -sV -sC -O, we discovered the open ports on the host, the services provided, the components used, and the versions of those components.
Certainly! Please provide the original heading, and I’ll rewrite it to include the keyword “vsftpd 3.0.3” along with “Services Provided.”
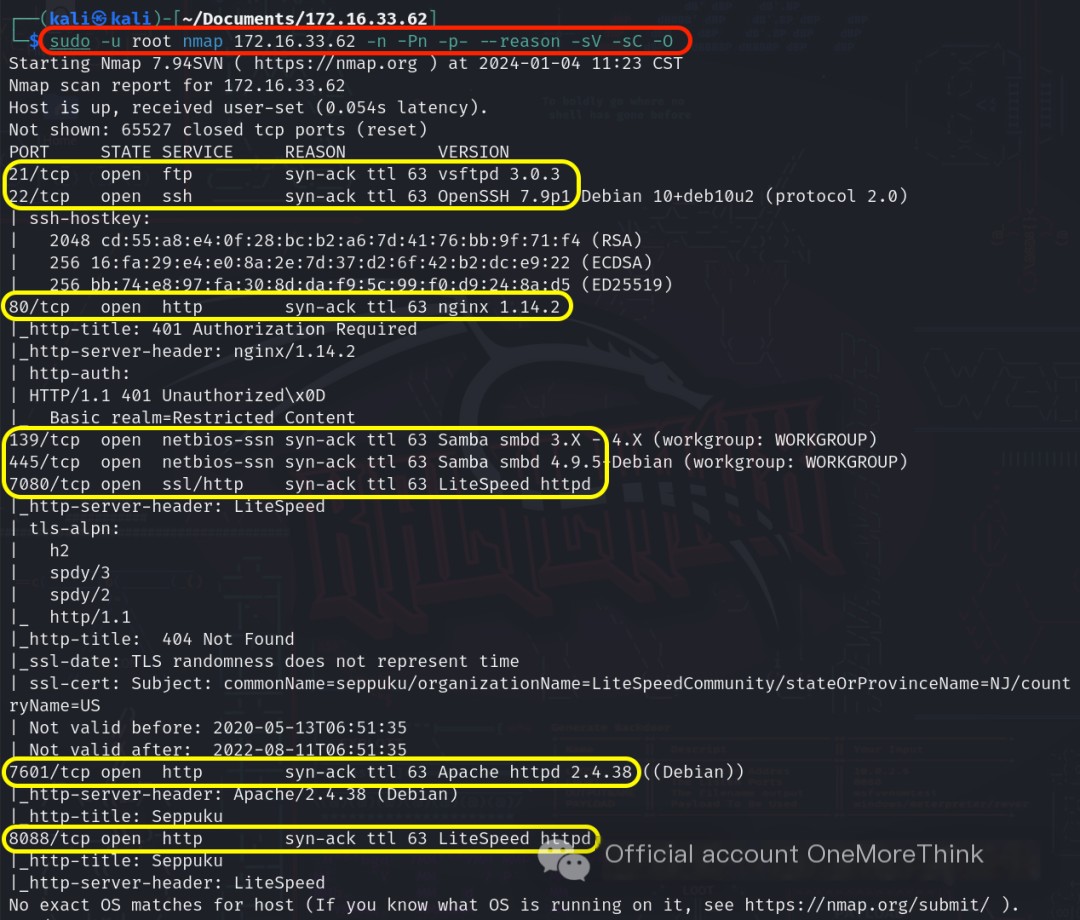 > />
> />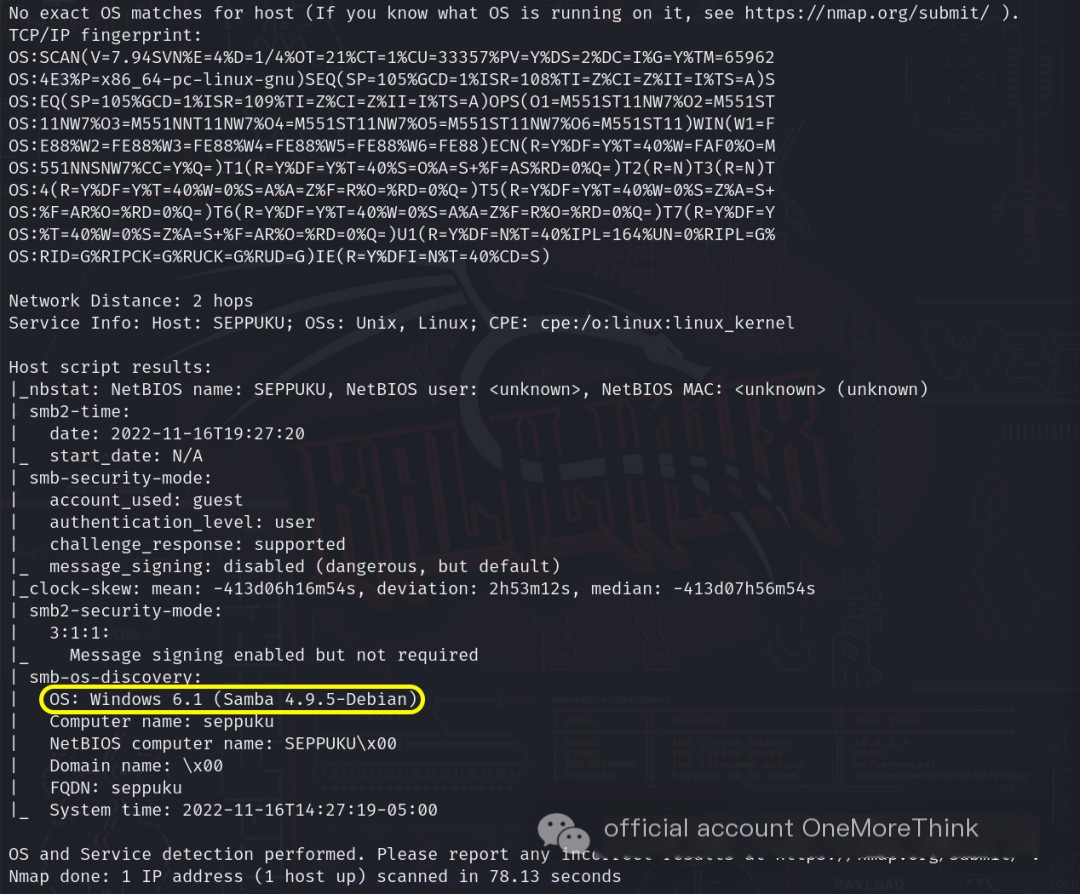 > />
> />
Using the command sudo -u root nmap 172.16.33.62 -n -Pn -sU –reason -sV -sC, we discovered the open ports on the host, the services provided, the components used, and the versions of those components.
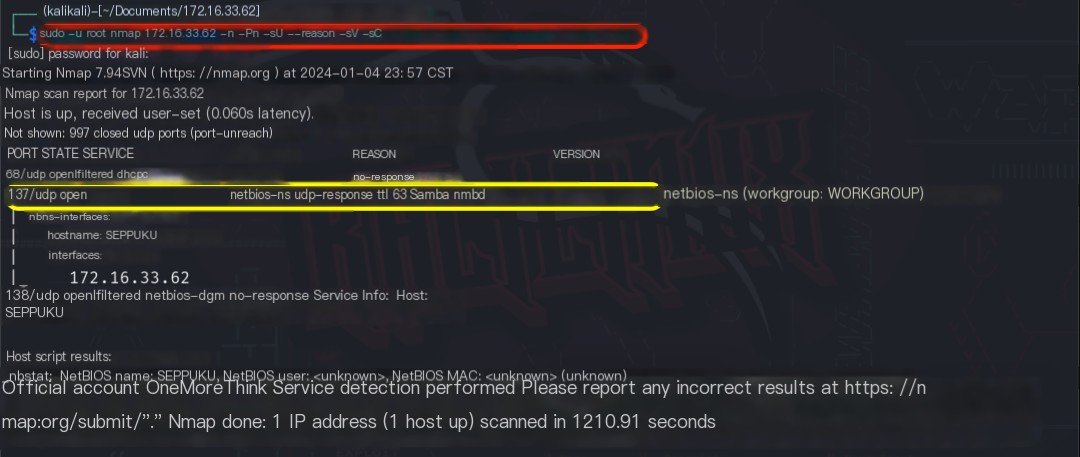
The final summary is as follows:
|
Open Ports |
Services Provided |
Components Used |
Component Versions |
|---|---|---|---|
|
21/tcp |
ftp |
vsftpd |
3.0.3 |
|
22/tcp |
ssh |
OpenSSH |
7.9p1 |
|
80/tcp |
http |
nginx |
1.14.2 |
|
137/udp |
netbios-ns |
Samba nmbd |
? |
|
139/tcp |
netbios-ssn |
Samba smbd |
3.X – 4.X |
|
445/tcp |
netbios-ssn |
Samba smbd |
4.9.5 |
|
7080/tcp |
ssl/http |
LiteSpeed httpd |
? |
|
7601/tcp |
http |
Apache httpd |
2.4.38 |
|
8088/tcp |
http |
LiteSpeed httpd |
? |
|
– |
os |
Windows |
6.1 |
2. Vulnerability Discovery (Privilege Escalation)
The host has nine open ports, which can be categorized into four types. Based on the frequency and criticality of common vulnerabilities in target ranges, the order is:
- File Storage: Port 21;
- Web Applications: Ports 80, 7080, 7601, 8088;
- File Sharing: Ports 137, 139, 445;
- Operations Management: Port 22.
This ordering differs from real-world scenarios. In real-world scenarios, the order is 1-4-3-2, prioritizing non-web applications because they are generally not exposed to the internet, and vulnerabilities in these applications are typically easier to exploit and have a greater impact.
2.1. Port 21/FTP Service with vsftpd 3.0.3
2.1.1. vsftpd 3.0.3 Component Vulnerabilities
Using the command searchsploit vsftpd 3.0.3, no 0-day vulnerabilities were found for the vsftpd 3.0.3 component.
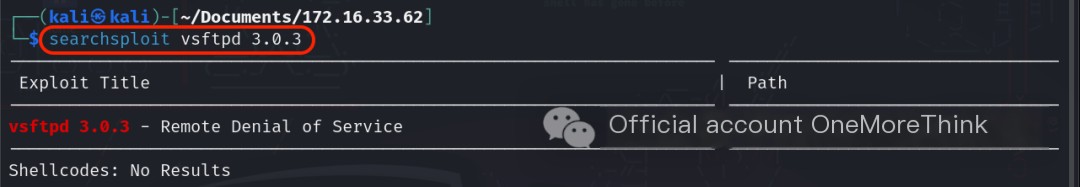
Certainly! Please provide the original heading, and I’ll rewrite it to include the keyword “vsftpd 3.0.3” along with “Services Provided.”
2.1.2. Services Provided: Password Vulnerability Assessment for vsftpd 3.0.3
Using the command ftp 172.16.33.62 to connect to the FTP service, attempting login with the anonymous account anonymous and a blank password resulted in failure. The bye command was then used to exit the FTP service.
Certainly! Please provide the original heading, and I’ll rewrite it to include the keyword “vsftpd 3.0.3” along with “Services Provided.”

Using the command hydra -C /usr/share/seclists/Passwords/Default-Credentials/ssh-betterdefaultpasslist.txt 172.16.33.62 ftp to brute-force the FTP service also failed.
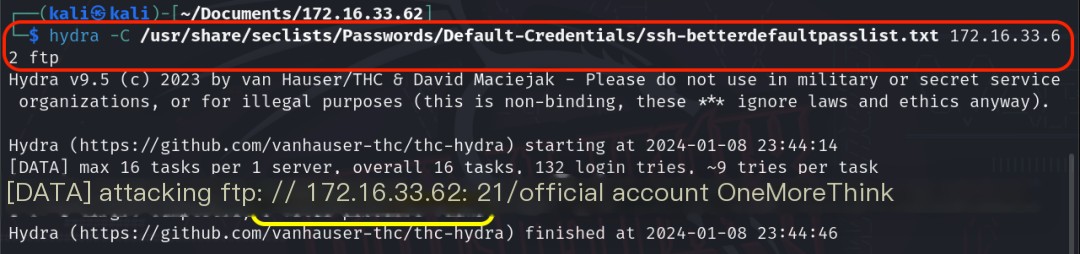
Certainly! Please provide the original heading, and I’ll rewrite it to include the keyword “vsftpd 3.0.3” along with “Services Provided.”
2.2. Services Provided by Port 80/HTTP
2.2.1. Services Provided: Component Vulnerabilities
0x01. Web Middleware
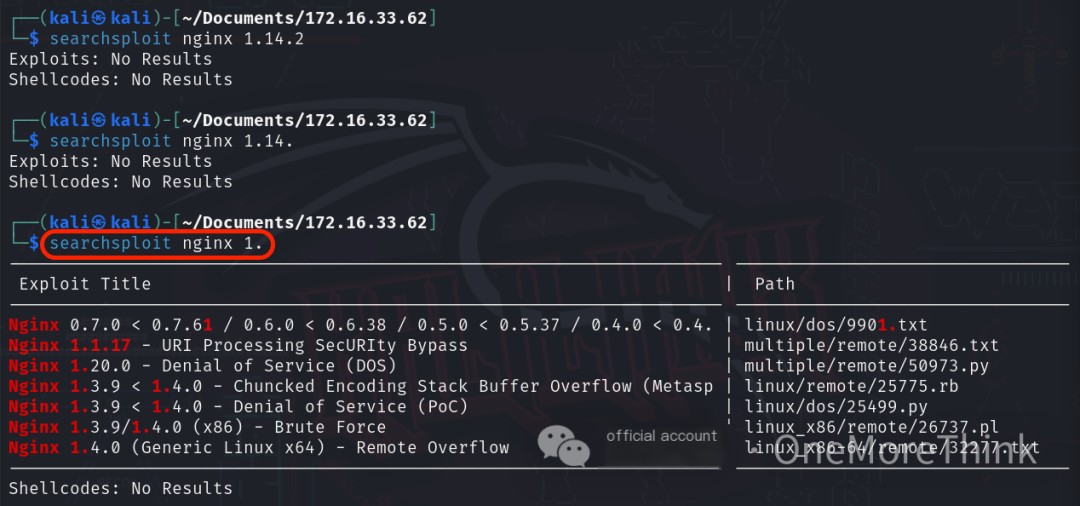
Using the command searchsploit nginx 1., no 0-day vulnerabilities were found for the nginx 1.14.2 web middleware.
Certainly! Please provide the original heading, and I’ll rewrite it to include the keyword “vsftpd 3.0.3” along with “Services Provided.”
0x02. Web Framework
Using the browser plugin Wappalyzer, no web frameworks with 0-day vulnerabilities were found.
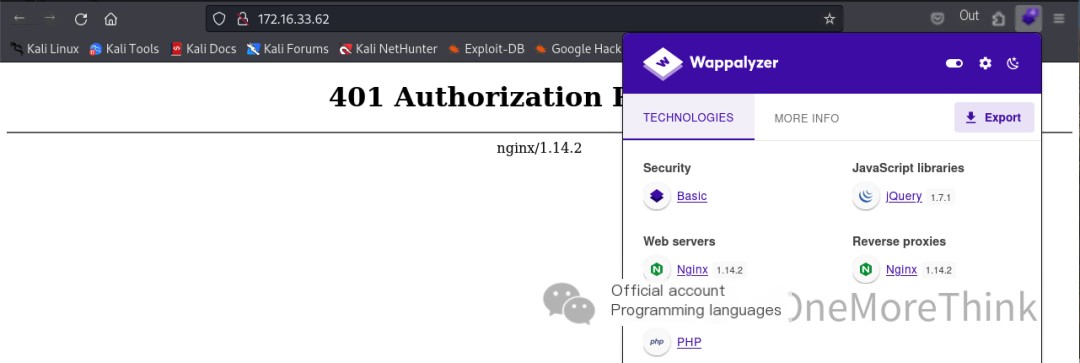
Certainly! Please provide the original heading, and I’ll rewrite it to include the keyword “vsftpd 3.0.3” along with “Services Provided.”
2.2.2. URL Vulnerabilities (Directory, File)
0x01. Direct Access
Accessing http://172.16.33.62/ directly with a browser revealed that HTTP Basic Authentication is required.
Certainly! Please provide the original heading, and I’ll rewrite it to include the keyword “vsftpd 3.0.3” along with “Services Provided.”
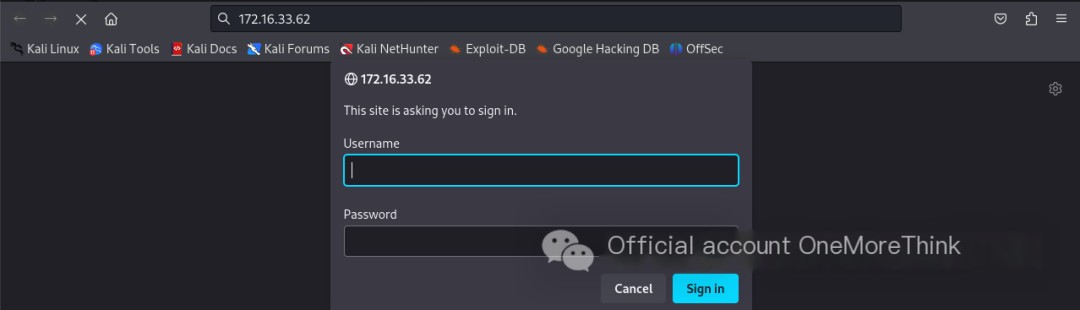
Services Provided: A Quick Attempt with Weak Credentials admin:admin Failed
Certainly! Please provide the original heading, and I’ll rewrite it to include the keyword “vsftpd 3.0.3” along with “Services Provided.”
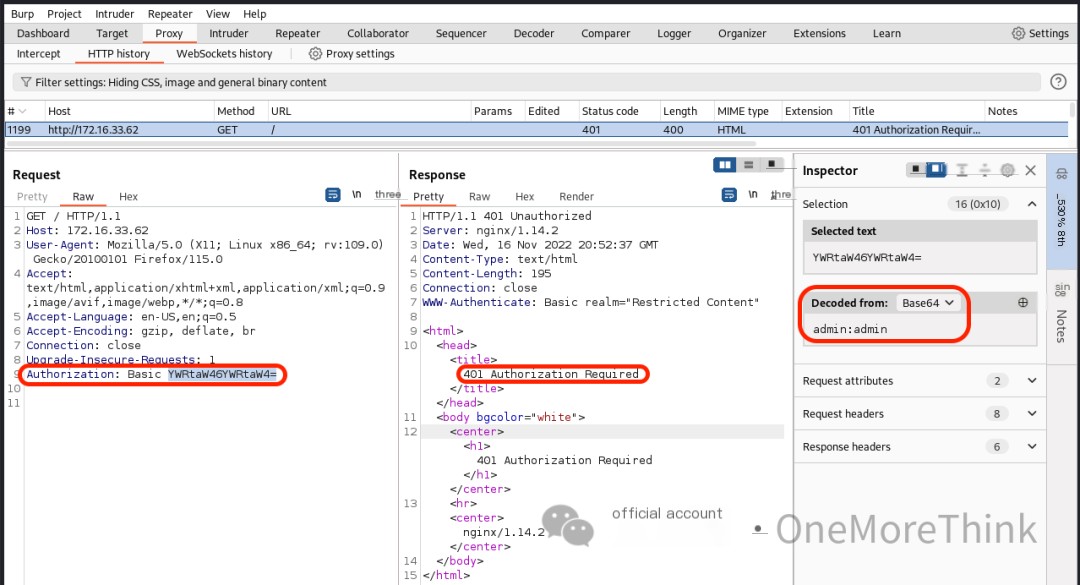
Brute-forcing HTTP Basic Authentication with the dictionary /usr/share/seclists/Passwords/Default-Credentials/ssh-betterdefaultpasslist.txt also failed.
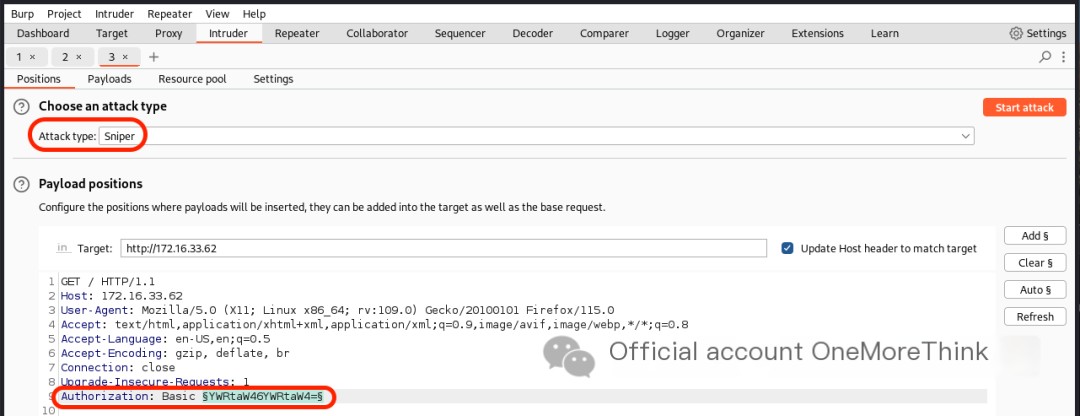
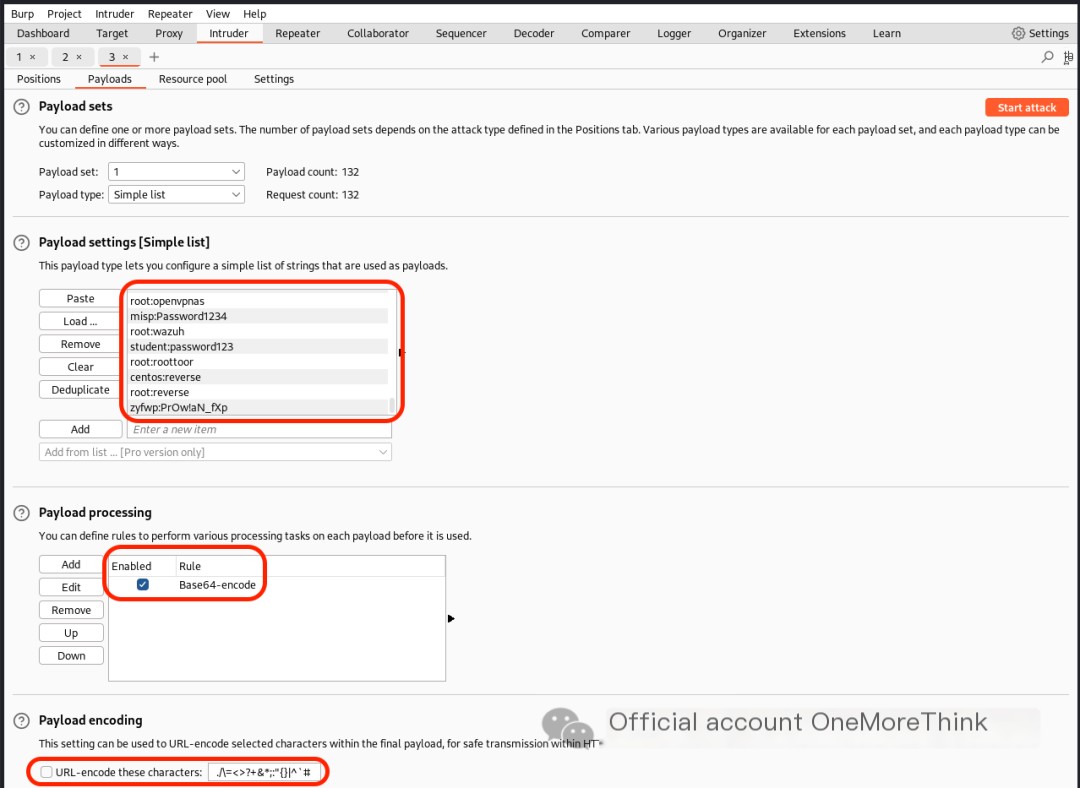
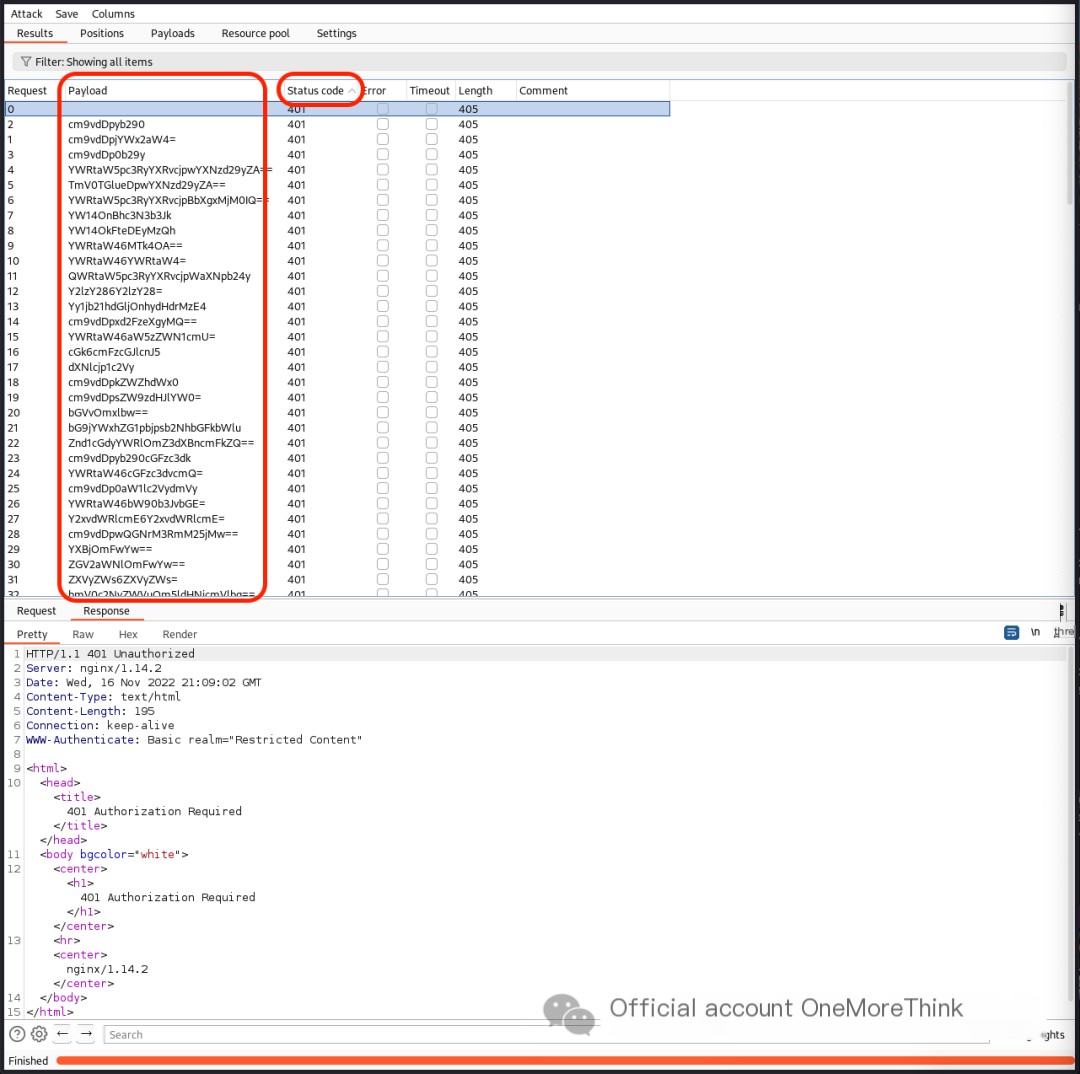
0x02. Directory Scanning
Using the command dirsearch -u http://172.16.33.62/ to scan the website’s directories and files revealed the /info.php file.
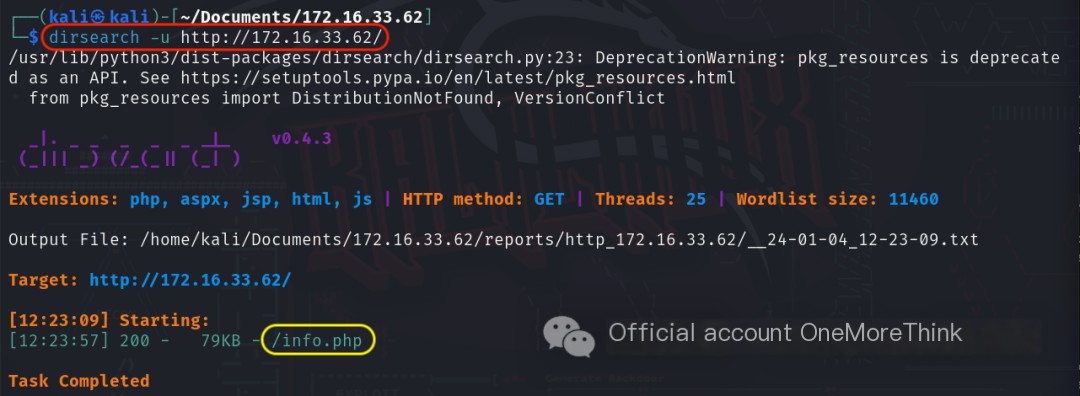
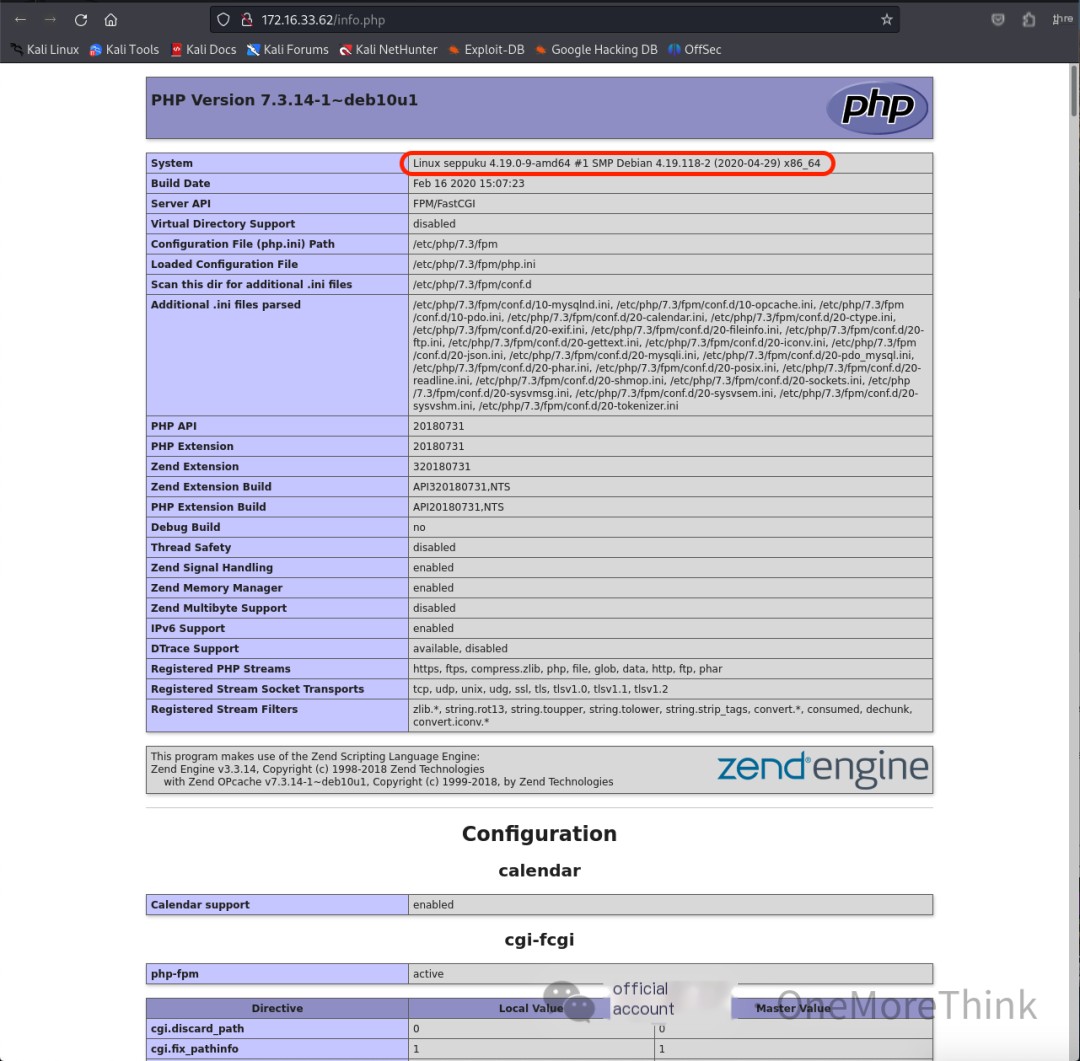
Accessing the /info.php file, the information gathered was insufficient to obtain system privileges, but it revealed that the operating system is Debian Linux 4.19.118-2, not Windows 6.1 as previously obtained by nmap via Samba.
0x03. Fuzzing
Based on the current information, there is no need to fuzz the website’s directories and files.
2.3. Port 7080/HTTPS Service
2.3.1. Services Provided: Component Vulnerabilities
0x01. Web Middleware
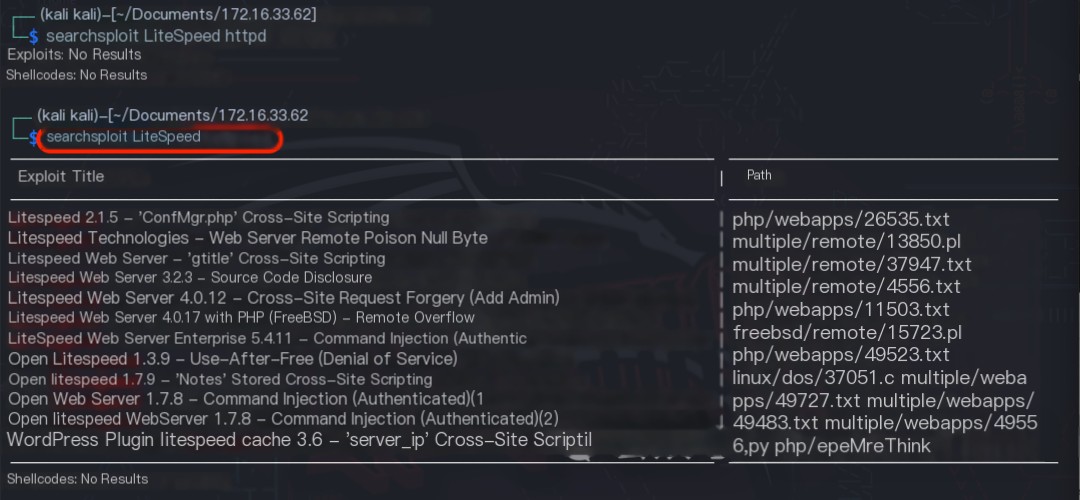
Using the command searchsploit LiteSpeed, no 0-day vulnerabilities were found for the LiteSpeed httpd web middleware.
0x02. Web Framework
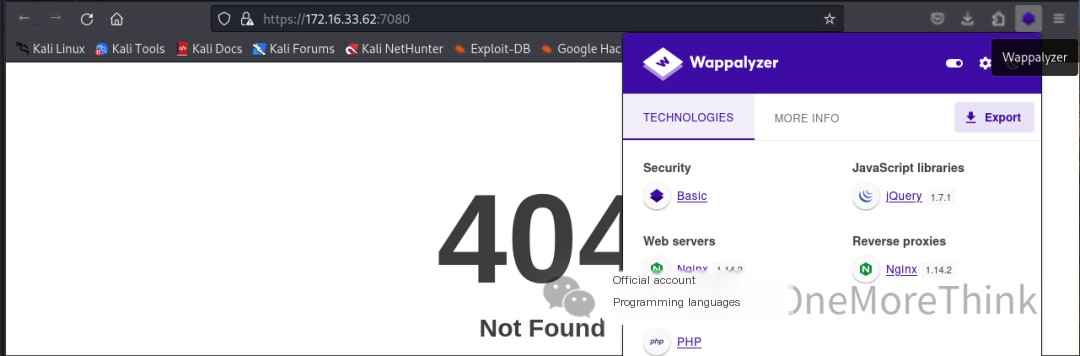
Using the browser plugin Wappalyzer, no web frameworks with 0-day vulnerabilities were found.
2.3.2. URL Vulnerabilities (Directory, File)
0x01. Direct Access
Accessing http://172.16.33.62/ directly with a browser only resulted in a 404 error.
Certainly! Please provide the original heading, and I’ll rewrite it to include the keyword “vsftpd 3.0.3” along with “Services Provided.”
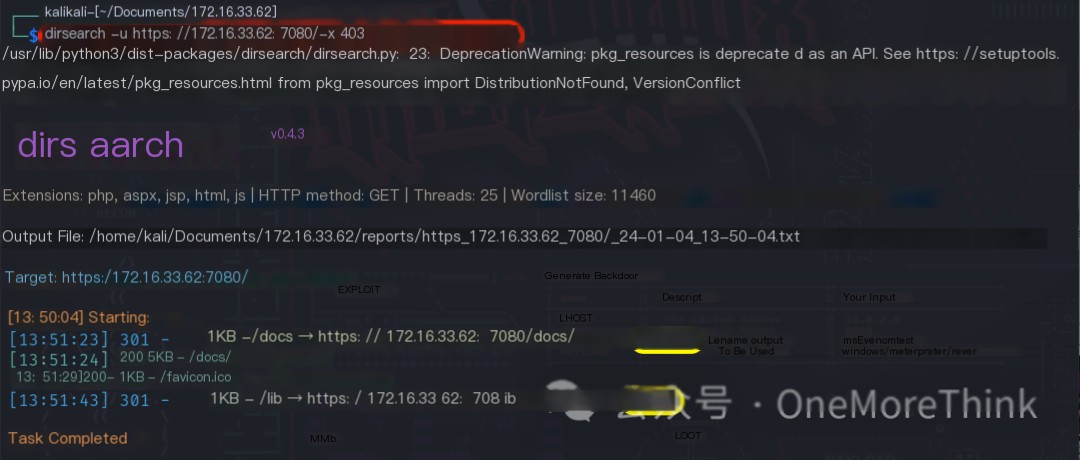
0x02. Directory Scanning
Using the command dirsearch -u https://172.16.33.62:7080/ -x 403 to scan the website’s directories and files revealed the /docs/ directory and the /lib/ directory.
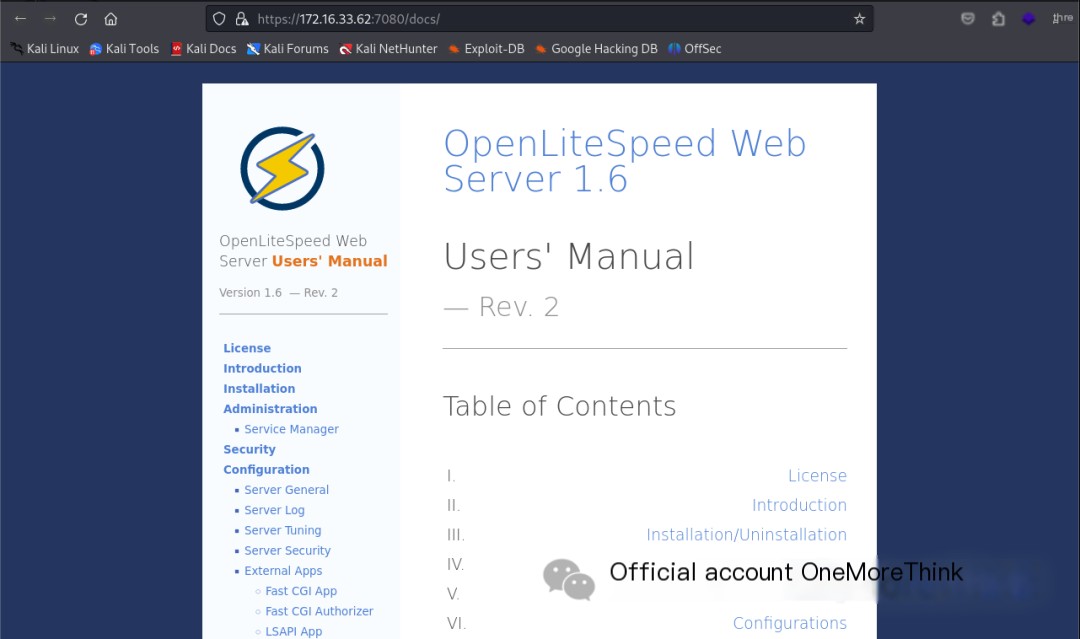
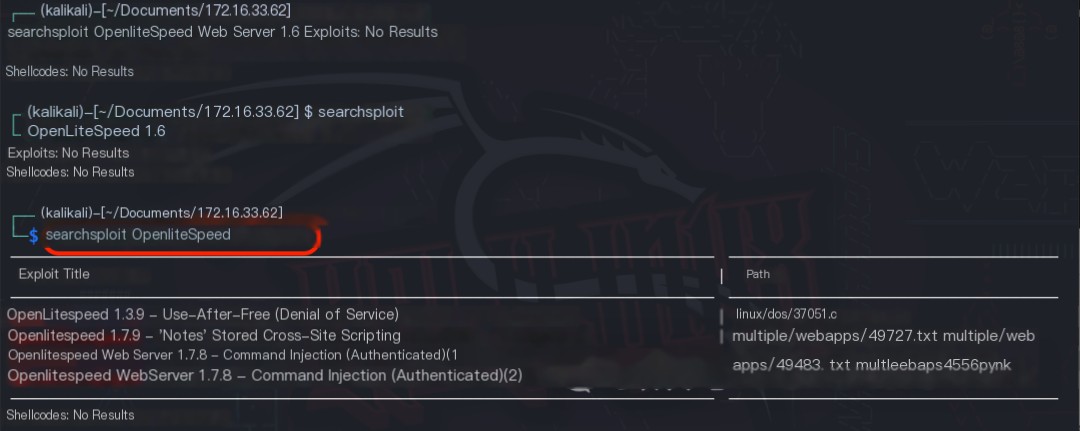
Accessing the /docs/ directory revealed the user manual page for the OpenLiteSpeed Web Server 1.6 web framework. Using the command searchsploit OpenLiteSpeed, no 0-day vulnerabilities were found.
Accessing the /lib/ directory also resulted in a 404 error.
0x03. Fuzzing
Based on the current information, there is no need to fuzz the website’s directories and files.
2.4. Port 7601/HTTP Service
2.4.1. Component Vulnerabilities
0x01. Web Middleware
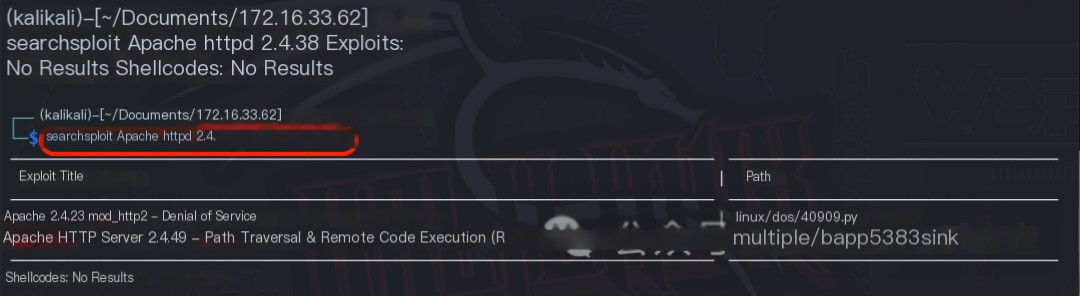
Using the command searchsploit Apache httpd 2.4., no 0-day vulnerabilities were found for the Apache httpd 2.4.38 web middleware.
0x02. Web Framework
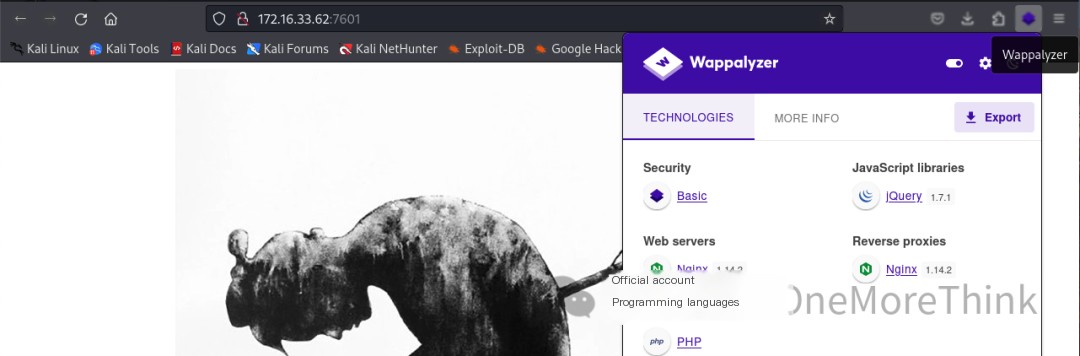
Using the browser plugin Wappalyzer, no web frameworks with 0-day vulnerabilities were found.
2.4.2. URL Vulnerabilities (Directory, File)
0x01. Direct Access
Accessing http://172.16.33.62:7601/ directly with a browser revealed only a strange image.
0x02. Directory Scanning
Using the command dirsearch -u http://172.16.33.62:7601/ -x 403 to scan the website’s directories and files revealed the /ckeditor/ directory, the /ckeditor/samples/ directory, and the /secret/ directory.
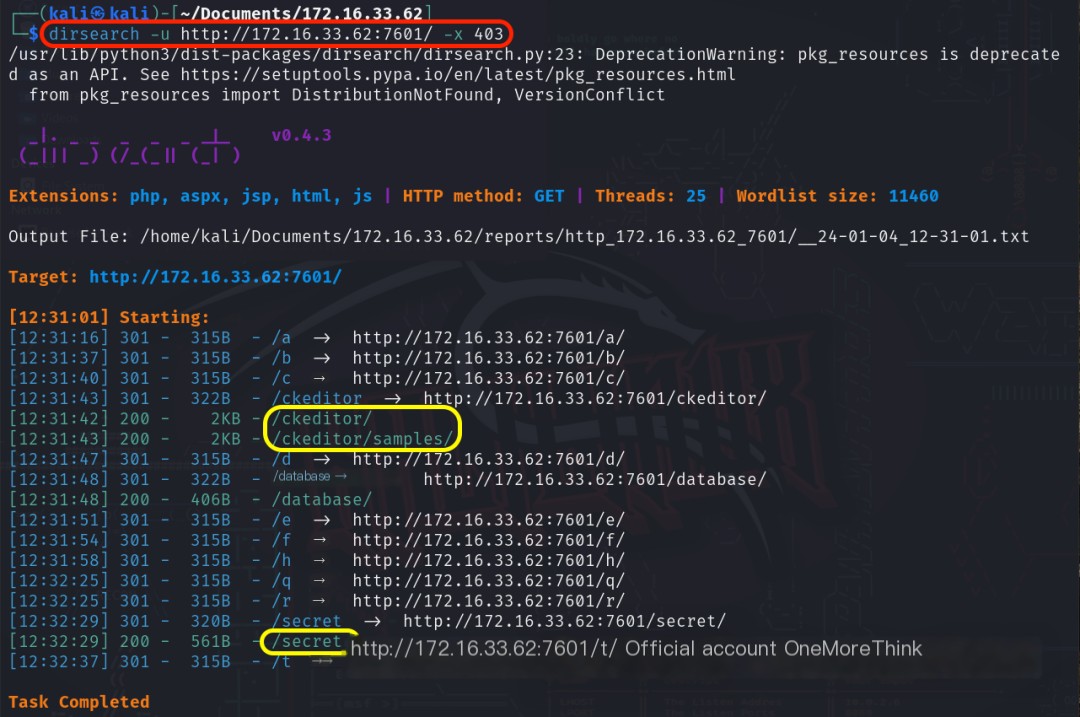
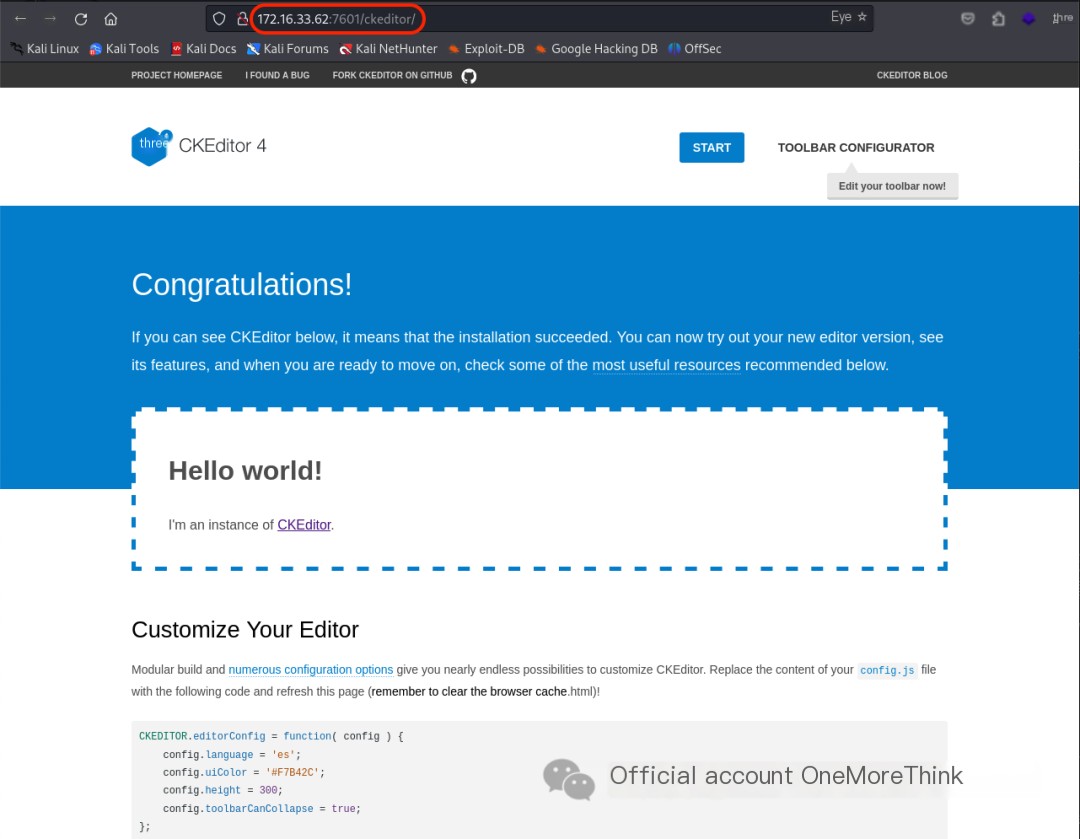
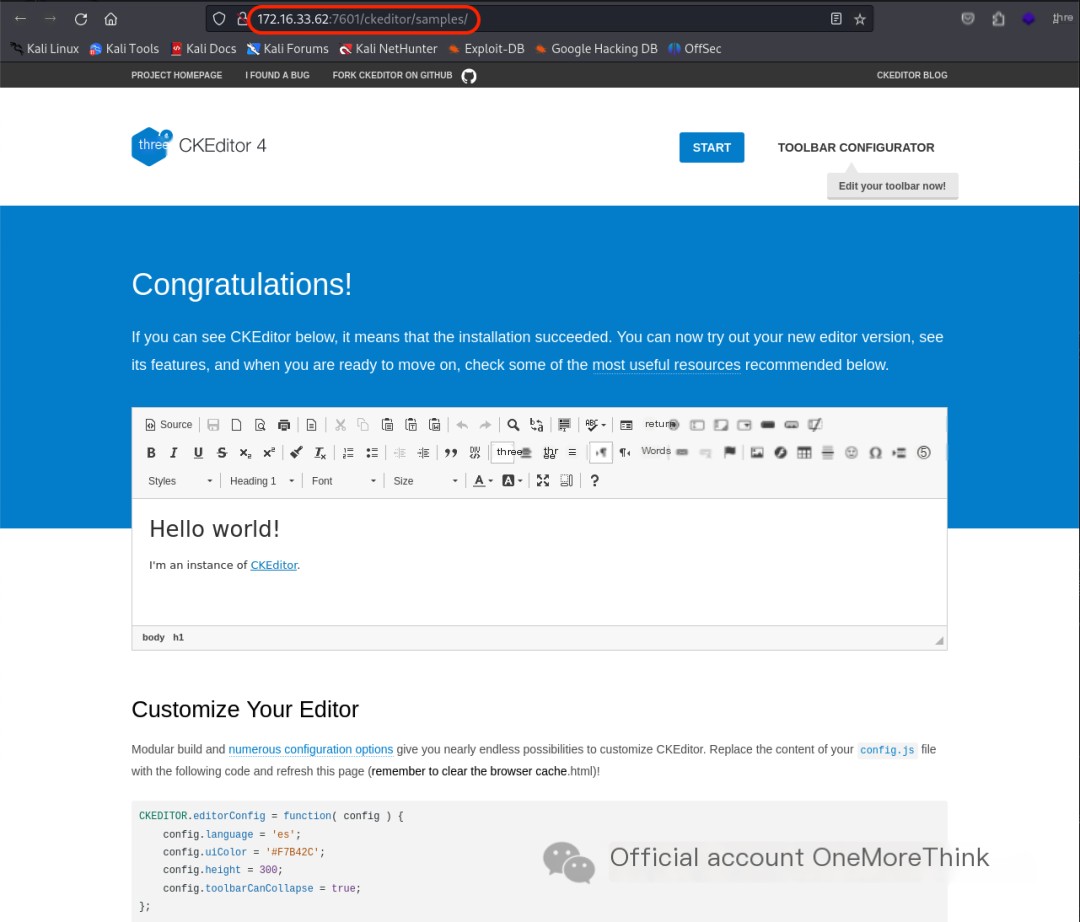
The /ckeditor/ directory is the welcome page for the CKEditor 4 web framework, and the /ckeditor/samples/ directory is a test page. Both are common pages, so let’s check for 0-day vulnerabilities.
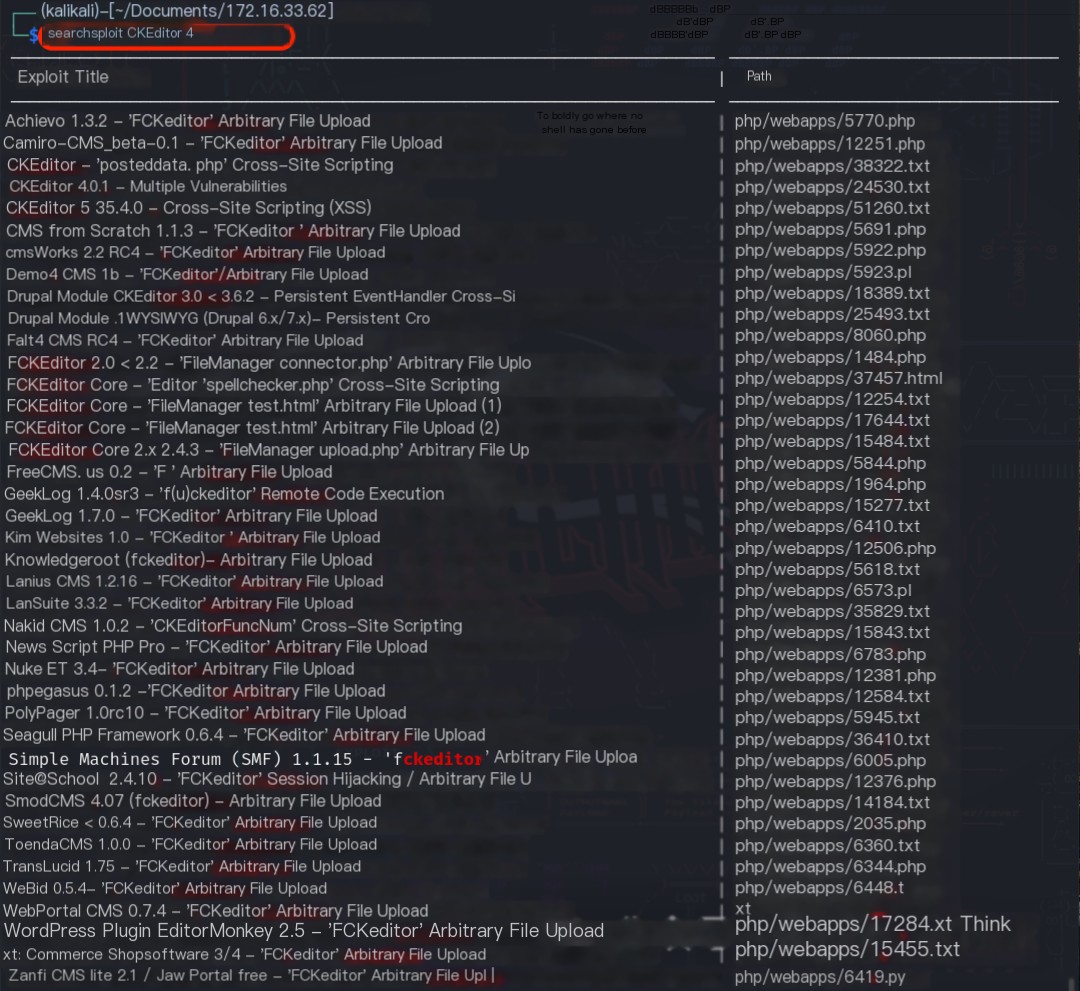
Using the command searchsploit CKEditor 4, no vulnerabilities were found in the CKEditor 4 web framework that could grant system privileges. Only XSS-type vulnerabilities were found.
The /secret/ directory is more interesting; it lists all the files in the directory.
After downloading them locally, the passwd.bak file revealed that the root and rabbit-hole users could log in to the SSH service. The shadow.bak file revealed the SSH password for the r@bbit-hole user.
Despite the “rabbit hole” hint, let’s try it. Using the command john shadow.bak --format=crypt yielded the SSH password a1b2c3. However, login attempts with the rabbit-hole and r@bbit-hole accounts failed.


