During the past month, I’ve been working with PWK / OSCP, and I’ve realized that SMB enumeration can be quite challenging, as different tools may succeed or fail on different hosts. While referencing content from NetSecFocus, I put together a checklist for scanning SMB service vulnerabilities during penetration testing. I’ll provide examples in each section, ensuring that any data from the PWK lab is sanitized according to the guidelines.
- Checklist
- Tools
- Details
- Enumerate Hostname – nmblookup
- Scan Shares – smbmap – smbclient – NMAP
- Check Null Sessions – smbmap – rpcclient – smbclient
- Check Vulnerabilities – NMAP
- Overall Scan – enum4linux
- Manual Check
- Samba Services – Windows
Checklist
- Enumerate Hostname – nmblookup -A [ip]
- List Shares
Code Language: javascriptCopy
smbmap -H [ip/hostname]echo exit | smbclient -L \\\\[ip]nmap --script smb-enum-shares -p 139,445 [ip]Check Null Sessions
Code Language: javascriptCopy
smbmap -H [ip/hostname]rpcclient -U "" -N [ip]smbclient \\\\[ip]\\[share name]Check Vulnerabilities
Code Language: javascriptCopy
nmap --script smb-vuln* -p 139,445 [ip]Overall Scan
Code Language: javascriptCopy
enum4linux -a [ip]Manual Check
Code Language: javascriptCopy
smbver.sh [IP] (port) [samba]- Analyze pcapTools
- nmblookup – Collect NetBIOS information on TCP/IP clients used for finding NetBIOS names
- smbclient – An ftp-like client for accessing SMB shares
- nmap – A general scanning tool, comes with checking scripts
- rpcclient – A tool for executing client MS-RPC functions
- enum4linux – Enumerate various smb features
- wireshark
Operational Details
Enumerate Hostname
- nmblookup
Code Language: javascriptCopy
nmblookup -A [IP] -A - Look up by IP addressExample use: root@kali:~# nmblookup -A [ip] Looking up status of [ip] [hostname] <00> - M [hostname] <20> - M WORKGROUP <00> - M WORKGROUP <1e> - M <03> - M INet~Services <1c> - M IS~[hostname] <00> - M MAC Address = 00-50-56-XX-XX-XX- smbmap
Code Language: javascriptCopy
smbmap -H [ip/hostname]This command will display the shares on the host along with the access permissions you have. Example use:
Code Language: javascriptCopy
root@kali:/# smbmap -H [ip][+] Finding open SMB ports....[+] User SMB session established on [ip]...[+] IP: [ip]:445 Name: [ip] Disk Permissions ---- ----------- ADMIN$ NO ACCESS C$ NO ACCESS IPC$ NO ACCESS NETLOGON NO ACCESS Replication READ ONLY SYSVOL NO ACCESSIf you obtain login credentials, you can rerun to show new access permissions:
Code Language: javascriptCopy
root@kali:/# smbmap -H [ip] -d [domain] -u [user] -p [password] [+] Finding open SMB ports.... [+] User SMB session established on [ip]... [+] IP: [ip]:445 Name: [ip] Disk Permissions ---- ----------- ADMIN$ NO ACCESS C$ NO ACCESS IPC$ NO ACCESS NETLOGON READ ONLY Replication READ ONLY SYSVOL READ ONLY- smbclient
Code Language: javascriptCopy
echo exit | smbclient -L \\\\[ip]exit handles any potential password prompt, as we are checking for null logins
Code Language: javascriptCopy
-L - Get the list of shares from the given hostExample use:
Code Language: javascriptCopy
root@kali:~# smbclient -L \\[ip]Enter WORKGROUP\root's password: Sharename Type Comment --------- ---- ------- IPC$ IPC Remote IPC share Disk wwwroot Disk ADMIN$ Disk Remote Admin C$ Disk Default shareReconnecting with SMB1 for workgroup listing. Server Comment --------- ------- Workgroup Master --------- -------- NMAP
Code Language: javascriptCopy
nmap --script smb-enum-shares -p 139,445 [ip]--script smb-enum-shares - Specifies the smb enumeration script-p 139,445 - Specifies smb portsExample use:
Code Language: javascriptCopy
root@kali:~# nmap --script smb-enum-shares -p 139,445 [ip] Starting Nmap 7.70 ( https://nmap.org ) at 2018-09-27 16:25 EDT Nmap scan report for [ip] Host is up (0.037s latency). PORT STATE SERVICE 139/tcp open netbios-ssn 445/tcp open microsoft-ds MAC Address: 00:50:56:XX:XX:XX (VMware) Host script results: | smb-enum-shares: | account_used: guest | \\[ip]\ADMIN$: | Type: STYPE_DISKTREE_HIDDEN | Comment: Remote Admin | Anonymous access: | Current user access: | \\[ip]\C$: | Type: STYPE_DISKTREE_HIDDEN | Comment: Default share | Anonymous access: | Current user access: | \\[ip]\IPC$: | Type: STYPE_IPC_HIDDEN | Comment: Remote IPC | Anonymous access: READ | Current user access: READ/WRITE | \\[ip]\share: | Type: STYPE_DISKTREE | Comment: | Anonymous access: | Current user access: READ/WRITE | \\[ip]\wwwroot: | Type: STYPE_DISKTREE | Comment: | Anonymous access: |_ Current user access: READ Nmap done: 1 IP address (1 host up) scanned in 10.93 secondsCheck Null Sessions
- smbmap
Code Language: javascriptCopy
smbmap -H [ip/hostname]This will show what you can do using the provided credentials (or a null session if no credentials are given). Refer to the examples in the previous section.
- rpcclient
Code Language: javascriptCopy
rpcclient -U "" -N [ip]-U "" - null session-N - no passwordExample use:
Code Language: javascriptCopy
root@kali:~# rpcclient -U "" -N [ip]rpcclient $>After this, you can run rpc commands.
Code Language: javascriptCopy
smbclientsmbclient \\\\[ip]\\[share name]This command attempts to connect to a share. It includes attempts with no password (or a null password) which may still be successful. Example use:
Code Language: javascriptCopy
root@kali:~/pwk/lab/public# smbclient \\\\[ip]\\shareEnter WORKGROUP\root's password:Try "help" to get a list of possible commands.smb: \> ls. D 0 Thu Sep 27 16:26:00 2018.. D 0 Thu Sep 27 16:26:00 2018New Folder (9) D 0 Sun Dec 13 05:26:59 2015New Folder - 6 D 0 Sun Dec 13 06:55:42 2015Shortcut to New Folder (2).lnk A 420 Sun Dec 13 05:24:51 20151690825 blocks of size 2048. 794699 blocks availableCheck Vulnerabilities
- NMAP
Code Language: javascriptCopy
nmap --script smb-vuln* -p 139,445 [ip]–script smb-vuln* – Runs all smb vulnerability scanning scripts-p 139,445 – smb ports Example use:
Code Language: javascriptCopy
root@kali:~# nmap --script smb-vuln* -p 139,445 [ip] Starting Nmap 7.70 ( https://nmap.org ) at 2018-09-27 16:37 EDT Nmap scan report for [ip] Host is up (0.030s latency). PORT STATE SERVICE 139/tcp open netbios-ssn 445/tcp open microsoft-ds MAC Address: 00:50:56:XX:XX:XX (VMware) Host script results: | smb-vuln-ms06-025: | VULNERABLE: | RRAS Memory Corruption vulnerability (MS06-025) | State: VULNERABLE | IDs: CVE:CVE-2006-2370 | A buffer overflow vulnerability in the Routing and Remote Access service (RRAS) in Microsoft Windows 2000 SP4, XP SP1 | and SP2, and Server 2003 SP1 and earlier allows remote unauthenticated or authenticated attackers to | execute arbitrary code via certain crafted "RPC related requests" aka the "RRAS Memory Corruption Vulnerability." | | Disclosure date: 2006-6-27 | References: | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2006-2370 |_ https://technet.microsoft.com/en-us/library/security/ms06-025.aspx |_smb-vuln-ms10-054: false |_smb-vuln-ms10-061: false | smb-vuln-ms17-010: | VULNERABLE: | Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010) | State: VULNERABLE | IDs: CVE:CVE-2017-0143 | Risk factor: HIGH | A critical remote code execution vulnerability exists in Microsoft SMBv1 | servers (ms17-010). | | Disclosure date: 2017-03-14 | References: | https://technet.microsoft.com/en-us/library/security/ms17-010.aspx | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143 |_ https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/ |_smb-vuln-regsvc-dos: ERROR: Script execution failed (use -d to debug) Nmap done: 1 IP address (1 host up) scanned in 5.58 secondsOverall Scan
- enum4linux
Code Language: javascriptCopy
enum4linux -a [ip]-a – Enumerate allThe output of the example use is extensive, but look for some key points:
- Output similar to nmblookup
- Check for null sessions
- Shared files
- Password policies
- RID looping output
- Domain information
Manual Check
- samba ngrep is a great network data tool. Run this in one terminal
Code Language: javascriptCopy
ngrep -i -d tap0 's.?a.?m.?b.?a.*[[:digit:]]' port 139Then run this in another terminal
Code Language: javascriptCopy
echo exit | smbclient -L [IP]It will drop a lot of information including the version. rewardone posted a neat script on the PWK forums to easily fetch the Samba version:
Code Language: javascriptCopy
#!/bin/sh#Author: rewardone#Description:# Requires root or enough permissions to use tcpdump# Will listen for the first 7 packets of a null login# and grab the SMB Version#Notes:# Will sometimes not capture or will print multiple# lines. May need to run a second time for success.if [ -z $1 ]; then echo "Usage: ./smbver.sh RHOST {RPORT}" && exit; else rhost=$1; fiif [ ! -z $2 ]; then rport=$2; else rport=139; fitcpdump -s0 -n -i tap0 src $rhost and port $rport -A -c 7 2>/dev/null | grep -i "samba\|s.a.m" | tr -d '.' | grep -oP 'UnixSamba.*[0-9a-z]' | tr -d '\n' & echo -n "$rhost: " &echo "exit" | smbclient -L $rhost 1>/dev/null 2>/dev/nullsleep 0.5 && echo ""When you run it on a box with Samba running, you will get results like this:root@kali:~/pwk/lab/public# ./smbver.sh [IP][IP]: UnixSamba 227aIf in doubt, we can check the smb version in PCAP. Here is an example for Unix Samba 2.2.3a:
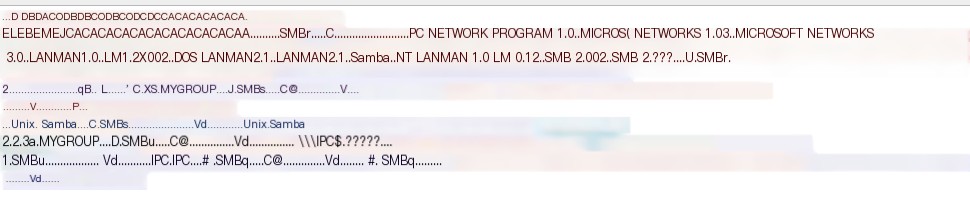 >
>
Penetration in Window environments — Windows SMB versioning is more complex, but examining captured packets in wireshark will provide extensive information about the connection. For instance, we can filter ntlmssp.ntlmv2_response to view NTLMv2 traffic, which can yield a wealth of system information about the target host.



