1 Introduction to DDoS Attack Analysis
MTU, transmission speed, congestion control, or various retransmissions, the core concepts related to TCP transmission:
- Learned RFC specifications and specific Linux implementations
- Through cases, this knowledge is flexibly applied
These discussions are still within the framework of protocol specifications. The default premise is that both ends of the communication work in accordance with TCP regulations, which is a gentleman’s agreement.
Failure to comply with TCP specifications and even exploiting vulnerabilities to attack are common, such as DDoS attacks .
2 NTP reflection attack case
DDoS attacks are common in gaming businesses. Once, a gaming customer found that their gaming server could not be logged in and received a complaint. The customer’s engineer did a tcpdump packet capture and quickly sent the capture file to us.
Expert Info
From the overview of the captured packet file, it is abnormal. First look at the Analyze →Expert Information:
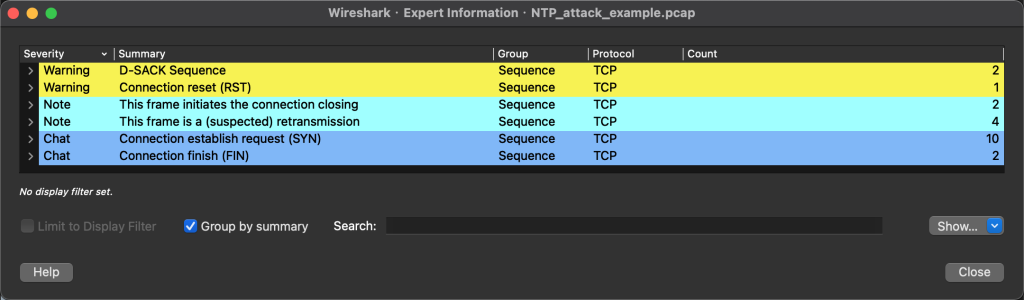
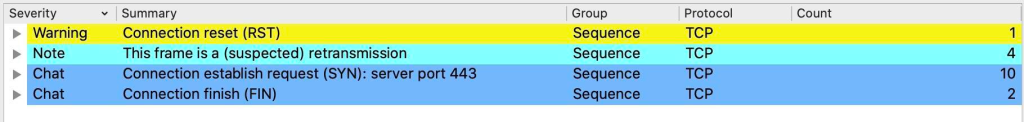
Gaming services are generally based on TCP, but this does not have much TCP information.
See the specific message
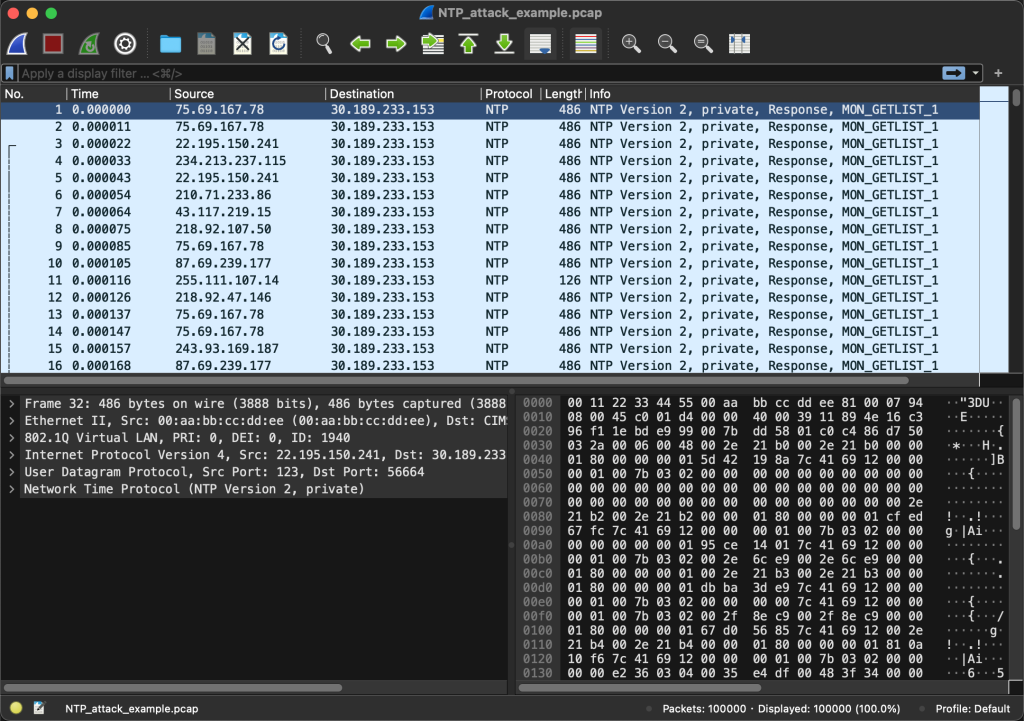
All of them are NTP Version 2, Private, Response, MON_GETLIST_1 messages. The customer does not provide any NTP service to the outside world. Where do these messages come from? Is it an attack? This is a type of DDoS attack: NTP reflection amplification attack .
NTP
Network Time Protocol, synchronizes time through a network service. There is a function called Monlist, which is enabled by default on some older devices and returns the IP addresses of the last 600 clients that have synchronized time with the NTP server.
The response packets are divided into every 6 IPs, and there are a maximum of 100 response packets. A simple NTP Monlist response may be more than 200 times the request. If 1Gbps is requested, then this reflection attack can reach more than 200Gbps!
Wireshark expands the UDP part to see the details of this Monlist response message:
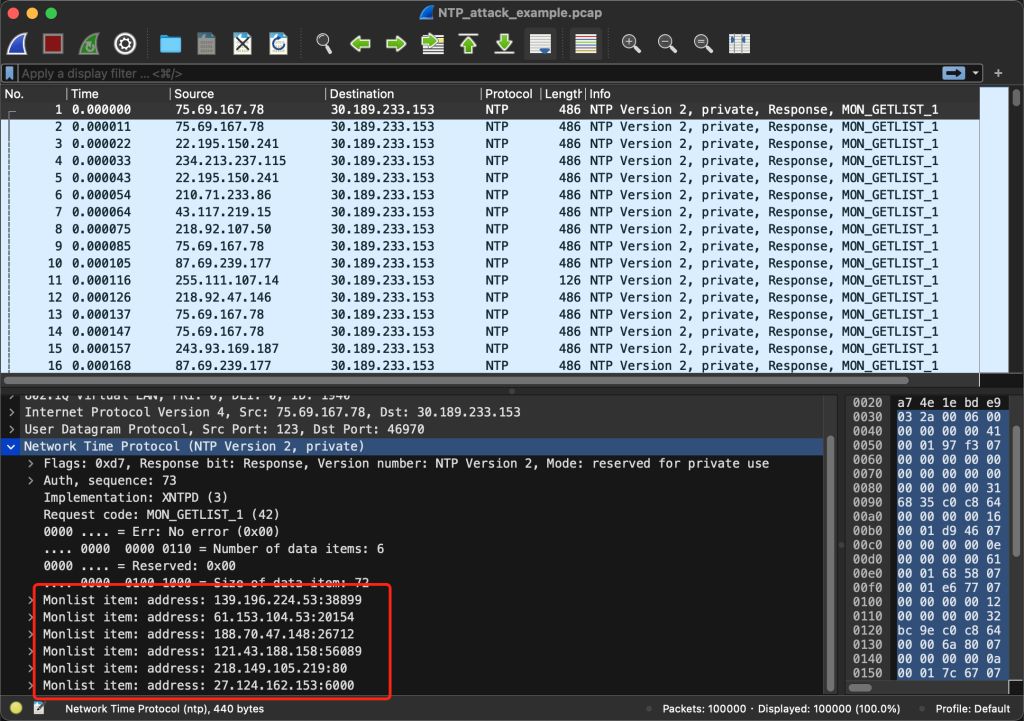
Each Monlist item takes up 72 bytes:
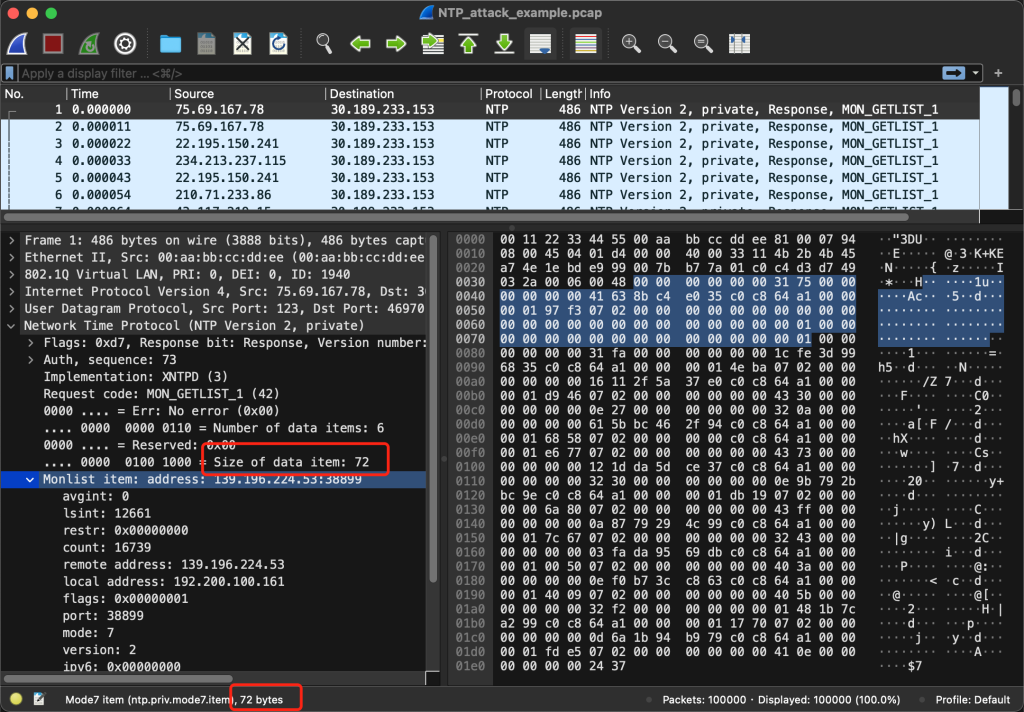
After selecting a Monlist item, there are 3 ways to find the length:
- The value of the field Size of data item is 72, which is the metadata provided by the protocol itself.
- In the bytecode section below, count the number of bytes with background color, which is 72.
- At the bottom of the window, there is a prompt for the number of bytes for the field we selected: 72 bytes
Using Wireshark to interpret the captured packet file is very useful, especially when you want to check the specific information of the field.
Aplly as Column
It is not intuitive to interpret the UDP packet length in the Wireshark window now, because Wireshark does not display the UDP length column by default, but you can add it yourself . Select Length in the UDP details, then right-click and select Aply as Column:
In the main window, you can see the UDP message length:
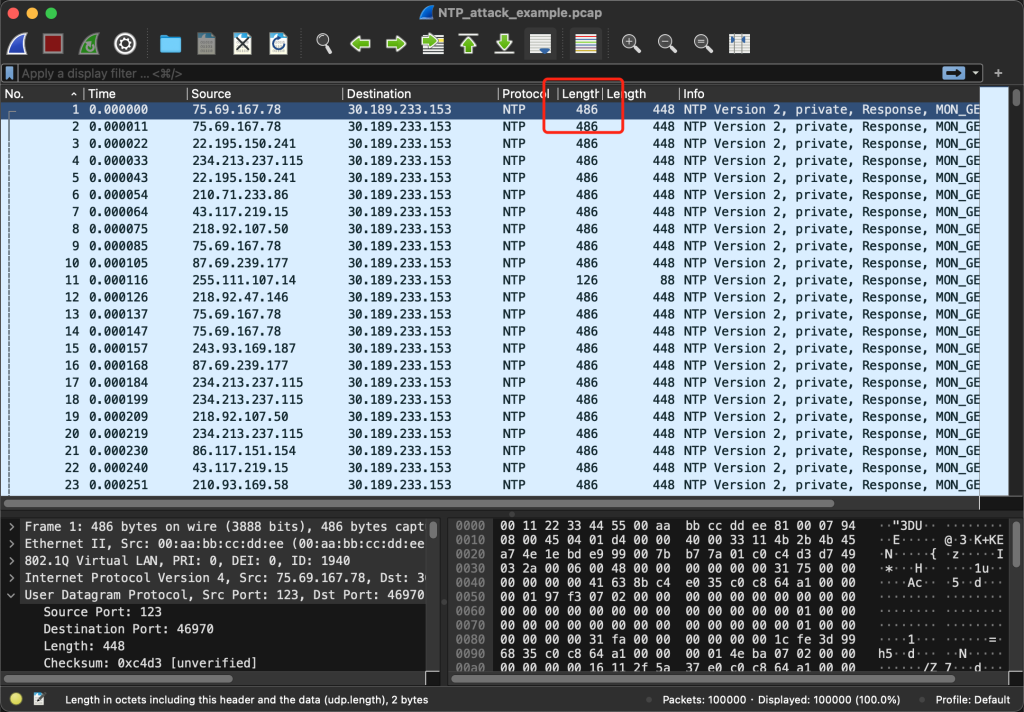
The length of UDP packets is not large. Why? The MTU is generally 1500 bytes. After removing the 20-byte IP header and the 8-byte UDP header, there is still a maximum of 1500-20-8=1472 bytes, which is much larger than 448 bytes. Why not use 1472 bytes? This involves a concept of UDP: The payload of a UDP packet should not be greater than 512 bytes .
This limitation comes from the IPv4 protocol. The IPv4 protocol specification RFC791 recommends that although the IP message length field is 2 bytes and the maximum is 65535, the network does not allow the transmission of such a large message, so the IPv4 specification recommends that the message length should be controlled within a relatively small range, which is 576 bytes, and the corresponding UDP payload is within 512 bytes:
Code language: javascript
copy
The number 576 is selected to allow a reasonable sized data block to
be transmitted in addition to the required header information. For
example, this size allows a data block of 512 octets plus 64 header
octets to fit in a datagram. The maximal internet header is 60
octets, and a typical internet header is 20 octets, allowing a
margin for headers of higher level protocols.Many applications do this part of the logic processing, that is, controlling the UDP payload within 512 bytes. For example, the length of the NTP Monlist is implemented by the NTP protocol, not the kernel UDP implementation. For example , DNS resolution will automatically switch to TCP mode if the data volume exceeds 512 bytes. The fundamental reason is also this long-ago regulation.
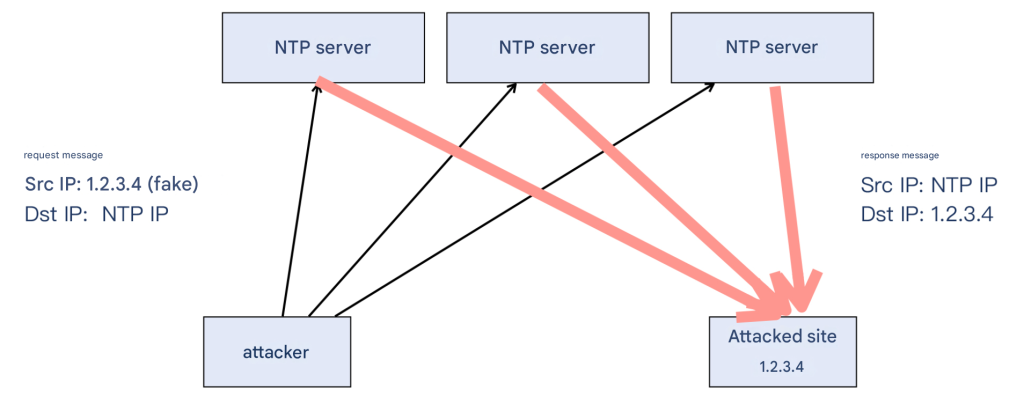
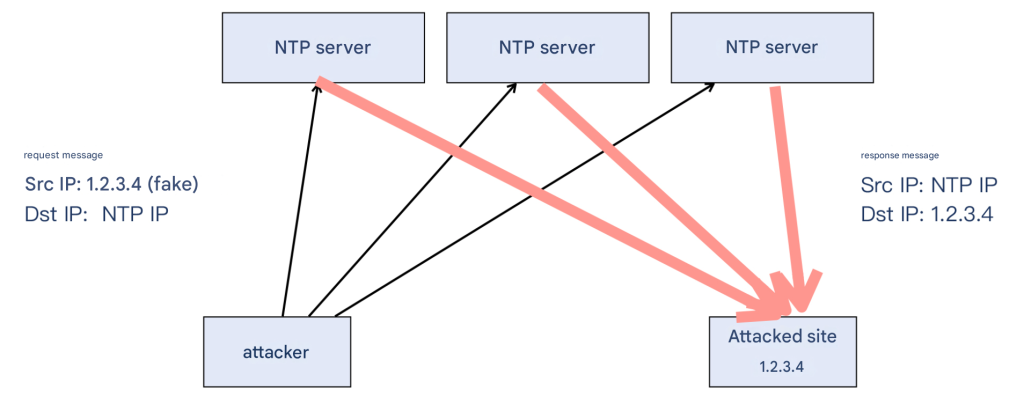
After checking the payload, I wondered, “Why is there only NTP reply but no NTP request?” This is exactly why 1Gbps can be amplified to more than 200Gbps. The core technique behind this is the reflection attack: taking advantage of the IP protocol’s “no verification of the source IP” deficiency, an IP message is constructed, whose source IP is the IP of the attacked site, so that the reply message from the NTP server is also sent to the attacked site . A large number of response messages are directed to the attacked site. In the process, the NTP server is exploited without knowing it.
Schematic diagram:
What to do when faced with this kind of attack?
- If the NTP server is your own, upgrade the version to avoid becoming an “accomplice”
- We are simply being attacked, so we have to use some means. Game customers can withstand attacks after installing high-defense.
3 SSDP reflection attack case
A “meat machine” is a host computer that has system permissions controlled by hackers. It can be mobilized by hackers to launch attacks. For example, if a hacker group controls 10,000 “meat machines”, as long as each “meat machine” launches even 1Mbps of attack traffic, multiplied by 10,000, it will be 10Gbps of traffic.
But it is not easy to get so many “meat machines”. Hackers think of: use the power of others to fight against others. Take advantage of the “response is many times the request ” of the protocol. This is what NTP reflection attack is. This kind of attack is called reflection attack with amplification in English. Amplication means amplification. Only a few “meat machines” are needed to launch a huge attack traffic.
Customer case. When the attack occurred, the packet was captured. See the Expert Information in the captured packet file:
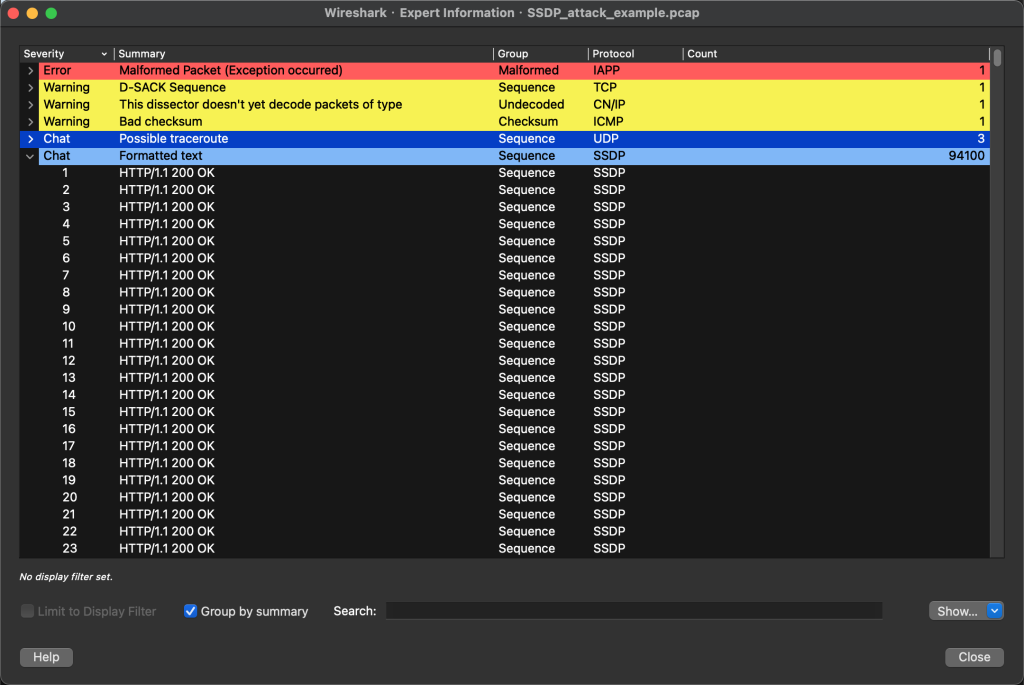
There is no TCP handshake message, just HTTP/1.1 200 OK, this HTTP is “familiar”. Since there are 94100 HTTP 200 response messages, there should be at least dozens of TCP connections, but this one has no SYN or FIN.
See what HTTP 200 looks like:
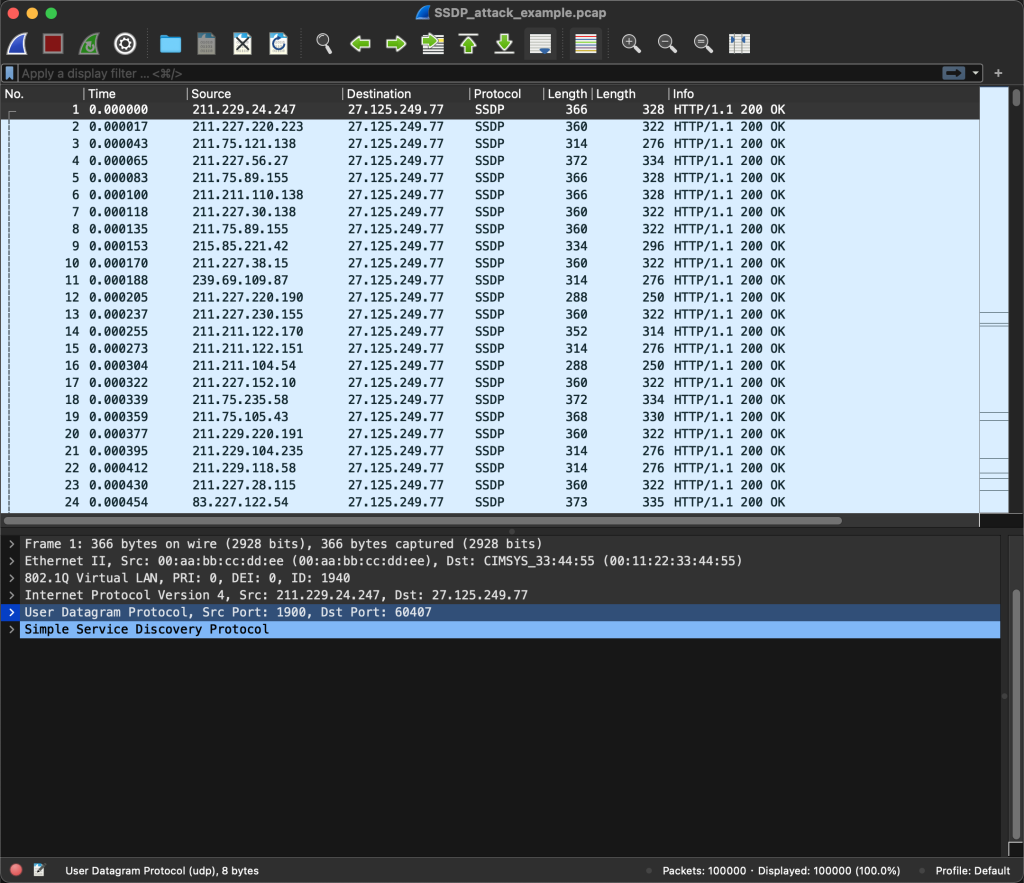
Why can’t I see srcPort and dstPort? It turns out that UDP is used. The srcPort and dstPort columns above refer to the TCP port number, so they are empty. Why does HTTP use UDP as the transport protocol? This is
SSDP reflection amplification attack
SSDP transmits information in HTTP format over UDP transport layer protocol. In 2014, people found that SSDP can be exploited by attackers. The SSDP protocol is mainly enabled on home routers . When their UPnP software has vulnerabilities, these routers will return response messages from port 1900 after being exploited by attackers. Obviously, the destination address of these response messages is the IP of the attacked site, not the IP of the attacker. The attack process is similar to the figure in the NTP reflection attack.
The response method at that time was to use a high-defense system.
The famous network service company Cloudflare jokingly calls SSDPthe “Stupidly SimpleDDoSProtocol“.Youcanread more about SSDP attacks from Cloudflarehere .
Router self-test. Visit https://badupnp.benjojo.co.uk/ , which will detect your exit IP (the exit IP of your home router) to see if port 1900 can be exploited. If there is no vulnerability, the webpage will remind you:
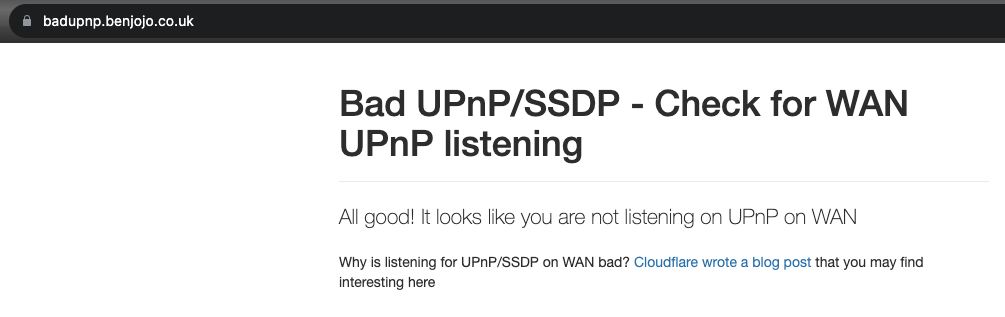
Overview of captured packets.
New command: capinfos .
Wireshark comes with the toolset.
View the duration, total packet volume and other information of the captured file. Directly run the capinfos file name :
Code language: javascript
copy
$ capinfos SSDP_attack_example.pcap
File name: SSDP_attack_example.pcap
File type: Wireshark/tcpdump/... - pcap
File encapsulation: Ethernet
File timestamp precision: microseconds (6)
Packet size limit: file hdr: 65535 bytes
Number of packets: 100 k
File size: 36 MB
Data size: 34 MB
Capture duration: 1.916902 seconds
First packet time: 2016-05-08 10:25:02.721642
Last packet time: 2016-05-08 10:25:04.638544
Data byte rate: 18 MBps
Data bit rate: 145 Mbps
Average packet size: 348.38 bytes
Average packet rate: 52 kpackets/s
SHA256: 8fa365f01c62023576623116410a6ca289915db4717e4805120009a575fdfb57
RIPEMD160: 5ab83442a5178b5f34bee1009a58ddb351bd292b
SHA1: 52a2c52644bc2753f9a11b7bf71eb1144f2c9a30
Strict time order: True
Number of interfaces in file: 1
Interface #0 info:
Encapsulation = Ethernet (1 - ether)
Capture length = 65535
Time precision = microseconds (6)
Time ticks per second = 1000000
Number of stat entries = 0
Number of packets = 100000Focus:
Code language: javascript
copy
Number of packets: 100 k
Capture duration: 1.916902 seconds
Average packet rate: 52 kpackets/sThis time, we captured 100,000 packets in total, which took 1.9 seconds, with an average packet rate of 52k packets/s, or 52,000 packets/s. They were all SSDP protocol response packets, which were DDoS.
Usually, you can use the capinfos command to quickly obtain information such as the packet rate, duration, and average packet size of a captured packet file.
After reviewing the two specific cases, you must have a more intuitive understanding of DDoS. Next, let’s take a systematic look at DDoS.
4 What is a DDoS attack?
DDoS is closely related to DOS. DOS (Denial of Service) refers to denial of service. Hackers use various means to prevent the attacked site from providing normal services. DOS attacks have long existed, and DDoS (Distributed DOS) is an upgraded version: mobilizing clients distributed in various places to launch attacks, making the attacked site unable to provide normal services.
DDoS is an “attack”, not an “intrusion”:
- The attack is to disrupt the service
- The intrusion may not cause damage, but it may steal data, hijack and extort, etc.
DDoS is to destroy computing resources
resource
Generally, computer resources are CPU and memory. Exhausting CPU and memory resources was an early form of attack. At that time, attacks and viruses were mainly used to make the attacked site lose service capabilities. With the improvement of security reinforcement technology and awareness, the cost of breaking into the system is getting higher and higher, and attackers have changed their direction. They do not need to think about attacking the other end, as long as they damage the previous network link, they can also paralyze the other party’s service. The reason for the service paralysis is no longer the unavailability of the service itself, but the unavailability of the network channel!
This is the core goal of DDoS: exhausting network bandwidth .
Assuming the bandwidth of the attacked site is 1Gbps, the attacker can make the site lose its normal service capability by making the traffic reaching the site exceed 1Gbps. It doesn’t matter whether these messages belong to the valid traffic that the attacked site is monitoring. Its purpose is direct: to block the road in front of your house and prevent normal traffic from entering.
Schematic diagram
How to generate huge traffic?
Common implementation method: reflection attack. Utilize:
- The ” response is many times the request ” feature of some protocols
- At the same time, ” IP protocol does not verify the source IP ” is insufficient
Direct traffic to the attacked site.
Both NTP reflection attacks and SSDP.
NTP reflection attacks rely on UDP, and many types of DDoS also use UDP. Why UDP?
5 Why is UDP easily used for DDoS?
TCP can also be used for DDoS, but at the same cost, reflection attacks are more efficient. Reflection attacks are mainly based on UDP.
5.1 UDP messages are simple and easy to construct
UDP header. RFC768 defines the format of the UDP header:
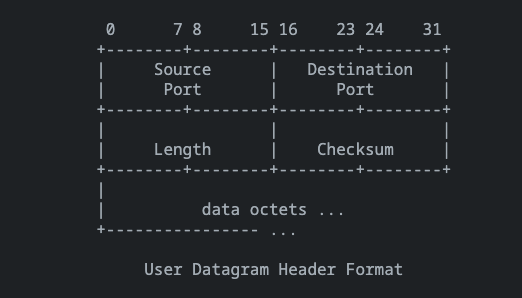
The UDP header is only 8 bytes:
- 2-byte source port
- 2-byte destination port
- 2-byte message length
- 2-byte checksum
Wireshark looks at the UDP message:
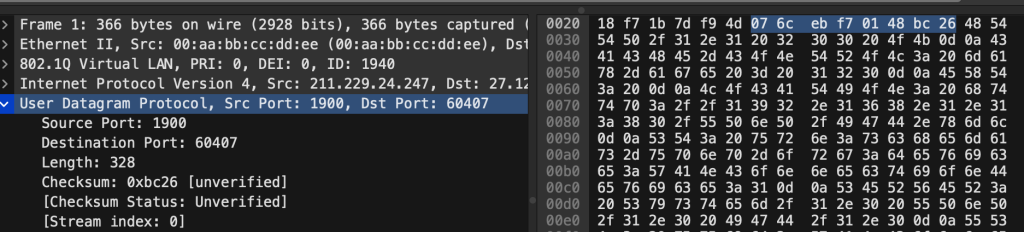
The TCP header is much more complex, with sequence numbers, confirmation numbers, various flags, and various TCP extension options. The UDP header is simple, making it easier for attackers to forge it. All they need to do is:
- Forge a source IP
- Find servers with reflection attack vulnerabilities such as NTP
- Send constructed fake UDP packets to these servers
5.2 UDP is stateless
The more critical reason is that UDP is stateless and does not require a handshake. Like NTP reflection attacks and SSDP reflection attacks, they are all “one question and one answer”. The attacker only needs to forge a request message, and the subsequent response message will naturally be sent to the attacked site.
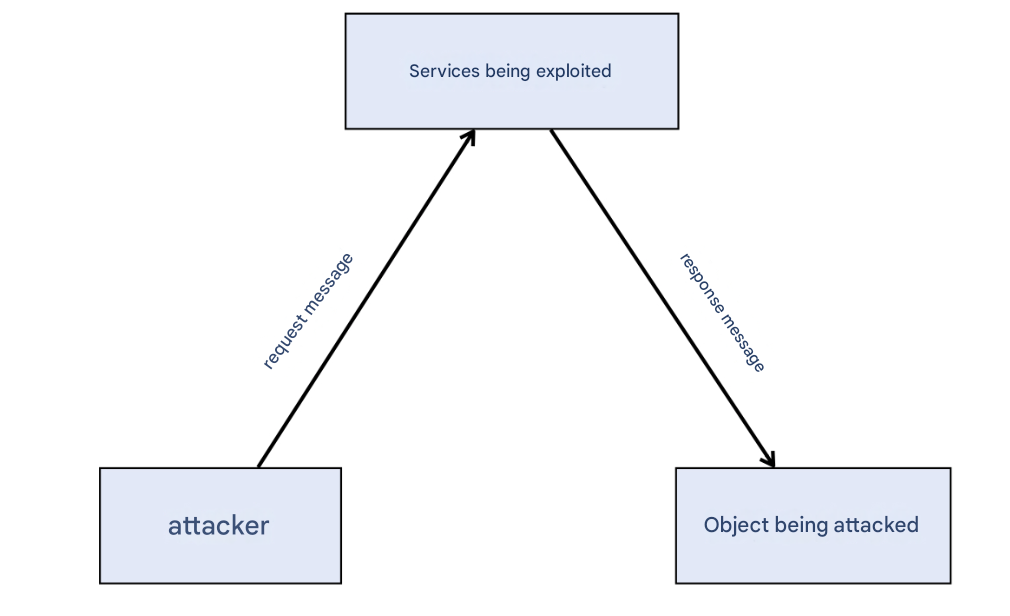
However, TCP requires a three-way handshake. If the source address of the attacker’s SYN message is forged as the [attacked site IP], the SYN+ACK message will be directly replied to that site IP instead of the attacker. Then the attacked site receives an inexplicable SYN+ACK and is directly RST, the TCP handshake ends, and the attack is terminated.
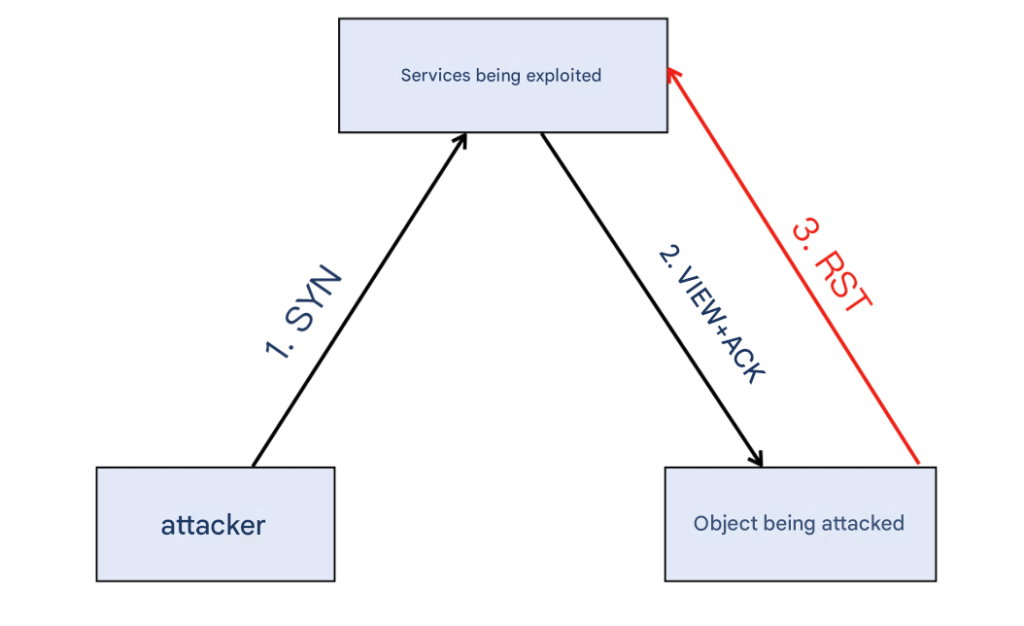
Skip the TCP handshake and directly send the application layer request (the source address is still forged to be the IP of the attacked site) to the reflection service? It will be directly RST because no handshake has been done.
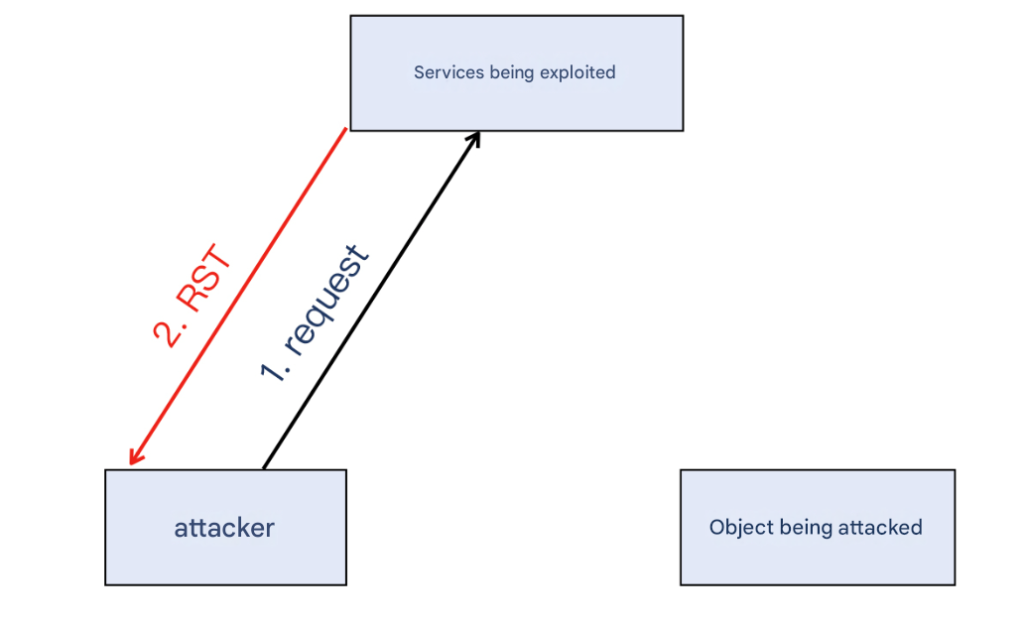
Even after the handshake, the two parties in subsequent communication still have to verify the sequence number and confirmation number. Although these are technically feasible, they are much more difficult, and UDP does not need to consider these.
Therefore, using TCP is a direct attack , not a reflection attack, such as SYN attack, half-connection attack, full-connection attack, CC attack, etc. The reflection attack has a great advantage in terms of “cost performance”.
6. Fighting against DDoS?
If you find service anomalies in the future, such as client requests being very slow, you can capture packets and analyze them on the server side to quickly determine whether it is a DDoS attack.
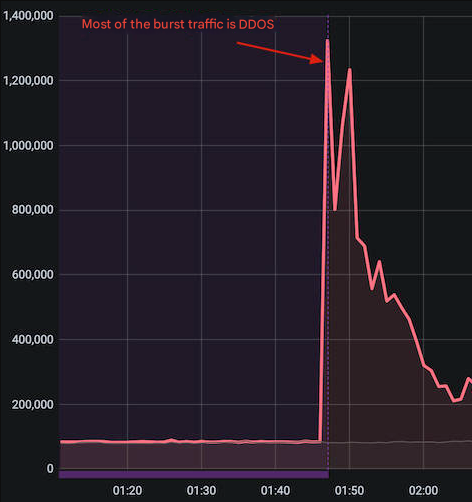
A simpler and more direct evidence is your public network interface bandwidth usage chart. If there is a significant surge in the chart, or even the upper limit of the interface bandwidth is reached, it can be basically determined that you are experiencing DDoS.
6.1 High Defense
The service is built on a public cloud . Consider using high-defense products from cloud vendors or other professional security service providers.
High-defense is a type of security protection and cleaning system that needs to be placed in front of the source station. It uses its own large enough bandwidth and powerful protection and cleaning cluster to achieve traffic cleaning, and finally intercepts the attack traffic. After cleaning, normal traffic enters the source station:
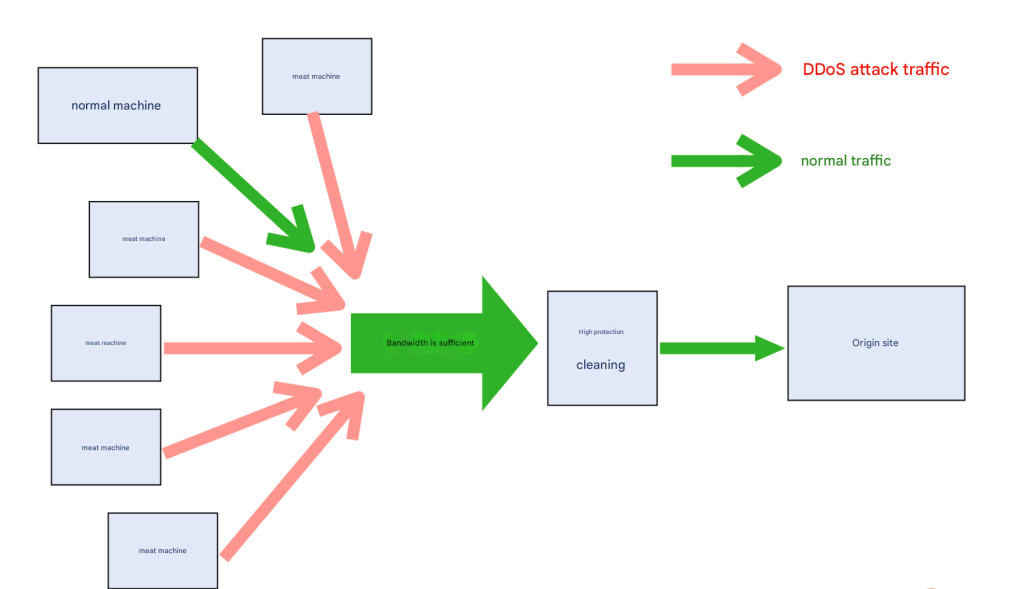
The source site is the site that is attacked.
High-defense is expensive to charge on a time-based basis, and is generally not connected to high-defense at ordinary times. Only when an attack is detected will it be automatically or manually switched to high-defense. “Connecting to high-defense” means pointing the site domain name to the high-defense domain name, so that the traffic will flow to high-defense first, and then return to the source site after cleaning.
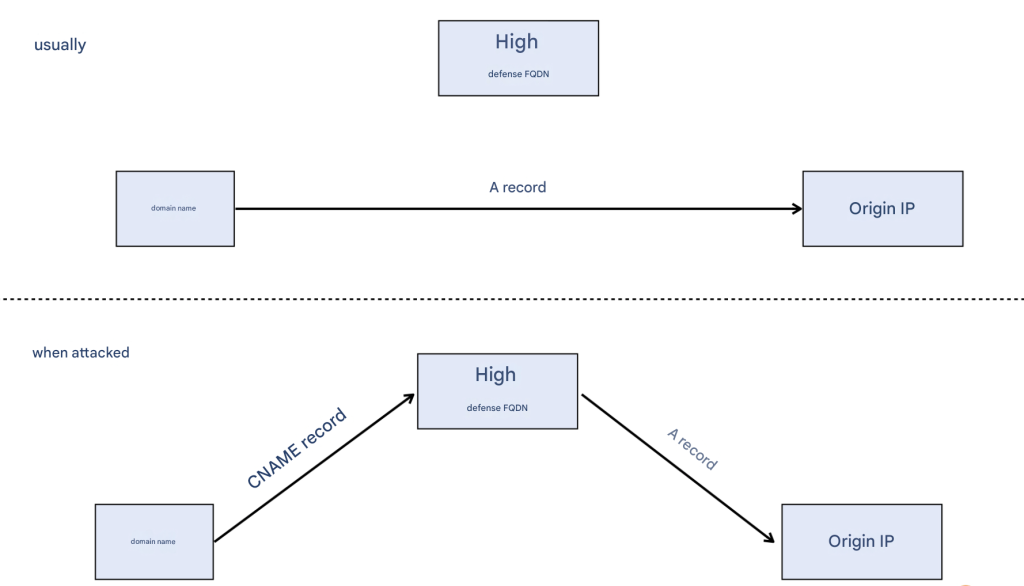
What if the attacker does not use domain name resolution and attacks the IP? Unbind the old IP, let the attack traffic enter the routing black hole, and then bind the new IP. Do not expose the new IP information, it can only be used for high-defense back to the source, and cannot be known to more people.
From the point of protection, the high-defense function is on the server side . If we can protect at the source of the attack , the effect will be better? Another design concept of DDoS protection products, a typical product is Telecom Cloud Dike.
6.2 Cloud Bank
The operator’s own system, whether the attacked site or the meat machine, relies on the operator’s public network line to access the Internet, so Yunti has a natural “geographical” advantage . It can act before the meat machine attack traffic enters the backbone network, so it is very likely that these attacks will not have the opportunity to reach the attacked site, which is equivalent to “strangling it in the cradle.”
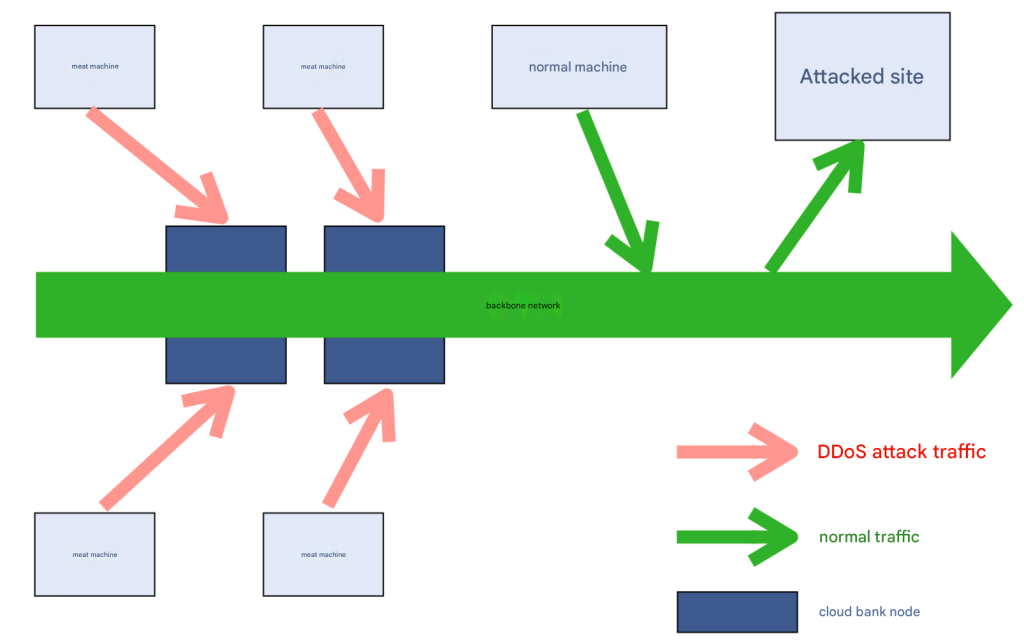
6.3 anycast and multiple POPs
We know that the essence of DDoS is to occupy network bandwidth, so the core strategy to deal with it is:
- Use a larger bandwidth to accommodate and first solve the problem of normal traffic being squeezed out of the network.
- After acceptance, it is cleaned, normal traffic is identified, and sent back to the source site so that business can continue.
We have introduced Anti-DDoS and Cloud Defense, which play a role at the near and far ends of the attacked site respectively, and are both commercial services. Then, another way is to do it yourself, which is also the architecture deployed by some large-scale websites , which is anycast and multi-POP.
Anycast is a network term that refers to the act of announcing the same network segment or IP address in multiple locations . For example, the most typical DNS service address of China Telecom is 114.114.114.114, and Google’s DNS service is 8.8.8.8, which are IP addresses that have been anycasted all over the country and even the world. Similar to this word, there are unicast and multicast, which refer to unicast and multicast respectively.
Larger websites will deploy POPs (multiple POPs) in various locations, and these POPs will announce the same IP segment. Once a DDoS attack occurs, because its target IP belongs to the anycast network segment, it will be distributed relatively evenly to these POPs by the Internet’s routing strategy.
If you have 20 POPs announcing the same network segment, you will have the opportunity to break down the DDoS attack into smaller pieces, with each POP receiving 1/20 of the attack traffic on average, greatly reducing the harm. When the attack traffic is not high, you can absorb the attack traffic by relying on your own multiple POPs and then clean it with your own equipment.
anycast+multiple POPs+own cleaning equipment. After completing this whole set, it is equivalent to building a small or medium-sized high-defense system by yourself.
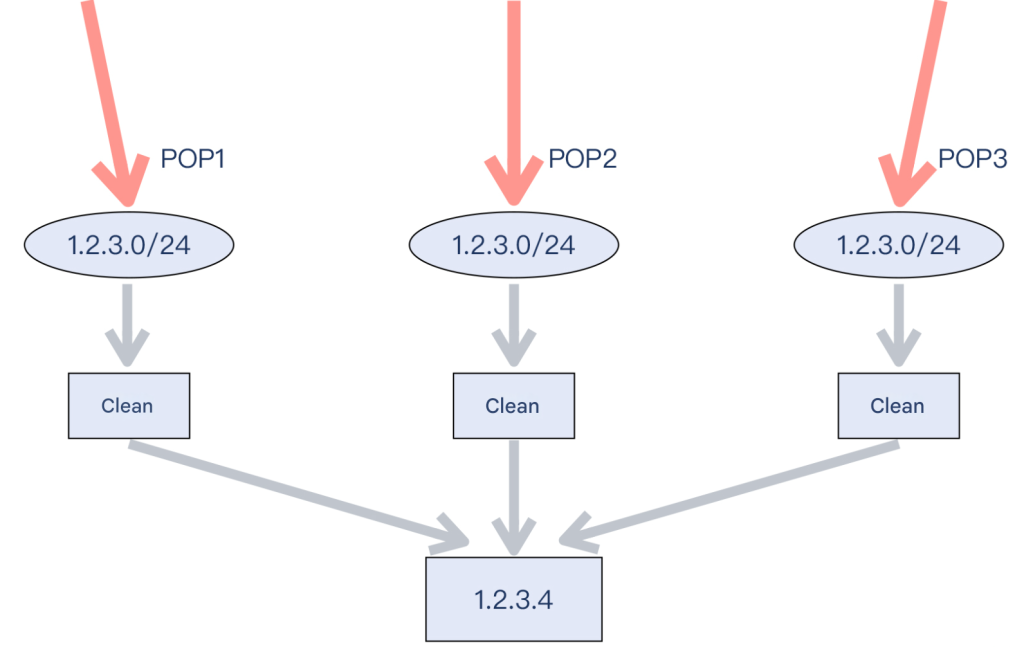
Supplement: Anycast here generally works at the network segment level. The application of anycast at the single IP level is still relatively limited, and is currently mainly used in UDP-based services, such as DNS services. HTTP based on anycast is a relatively cutting-edge field. Currently, a few companies have begun to practice it. I believe that in the near future, we should see more and more companies using HTTP over anycast.
6.4 CDN
Similar to the previous point, CDN also protects or mitigates DDoS through “multi-point distribution”. CDN service providers generally use a combination of strategies such as anycast to make their DDoS protection capabilities even better.
7 Conclusion
NTP reflection attack and SSDP reflection attack are two typical DDoS cases. Understand the characteristics of reflection amplification attack, which mainly uses:
- The IP protocol does not verify the source IP , but can forge the source IP and set it to the IP of the attacked site, thus directing the response traffic to the attacked site.
- The UDP protocol is connectionless and can directly perform application layer question and answer, which makes IP spoofing effective.
- Some services have the characteristic that the size of the response message is many times that of the request message , making the attack more effective.
We systematically analyzed the core method of DDoS, and ” exhausted network bandwidth ” prevented the attacked site from providing services normally. In terms of troubleshooting, when we found service anomalies, we could quickly locate whether there was a DDoS attack by doing packet capture analysis on the server side. We could also directly determine whether it was a DDoS attack by paying attention to sudden huge traffic based on the bandwidth usage graph.
Strategies to deal with DDoS attacks:
- High-defense products can protect against extremely large attack traffic.
- If you have higher requirements for protection effects, you can use the operator’s cloud barrier products.
- The system has sufficient internal conditions and deploys multiple POPs and anycast to evenly absorb attack traffic.
- CDN can also be used to reduce the impact of DDoS by allowing CDN’s natural distributed layout
The new command capinfos can quickly obtain the overall information of the packet capture file, including the capture duration, total packet volume, average packet size, etc. Regarding how to interpret the length of the packet field in Wireshark, you also need to know at least the following two methods:
- Select the message field to be interpreted, and then count the number of bytes with background color in the bytecode section below.
- Still select the message field to be interpreted, and the corresponding number of bytes will be displayed in the bottom bar.
It is recommended that the UDP payload should not exceed 512 bytes . The IPv4 protocol specification recommends that UDP-based protocols such as NTP and DNS implement this specification.
8 FAQ
- When the “hack machine” sends out 100Mbps attack traffic, does it still reach the attacked site at 100Mbps? Why?
- Why can CDN alleviate DDoS?


