I. Overview of the Endpoint View in Colasoft Network Analysis
The Colasoft Network Analysis System’s endpoint view provides both physical and IP endpoints. Through its network endpoint statistical analysis feature, users can quickly locate the IP and physical endpoints with the highest communication volume. The system also supports clear traffic statistics rankings for each network protocol, such as identifying the top 5 IP endpoints under the HTTP protocol.
From the endpoint view, one can clearly derive the specific traffic usage of all hosts in the current network (including a network segment, a physical MAC address, an IP), such as the host with the highest total traffic, the host with the highest sending traffic, the host with the highest receiving traffic, the host with the most sent and received packets, the host with the most sent packets, the host with the most received packets, internal traffic, and hosts with the highest broadcast traffic, among others.
With this information, we can determine if there are broadcast/multicast storms in the network and assist users in troubleshooting slow network speeds, intermittent connectivity, worm virus attacks, DOS attacks, and other network issues where users cannot access the internet.
II. Application Example
When encountering network issues and attacks, our primary step is to observe the current total network traffic, send and receive traffic, and network connections to identify a general direction for investigation. This information is all included in the endpoint view of the Colasoft Network Analysis System, as shown in Figure 1,
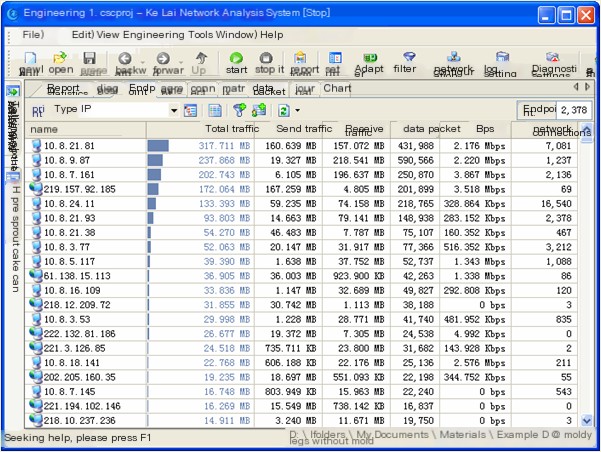
(Figure 1 Colasoft Network Analysis System’s Endpoint View)
From Figure 1, you can click to sort the total traffic, network connections, and other related information columns to identify and analyze the ones with the highest traffic and most network connections in the current network. The host with the most connections is 10.8.21.81, and we locate this host to view its connection information, as shown in Figure 2,
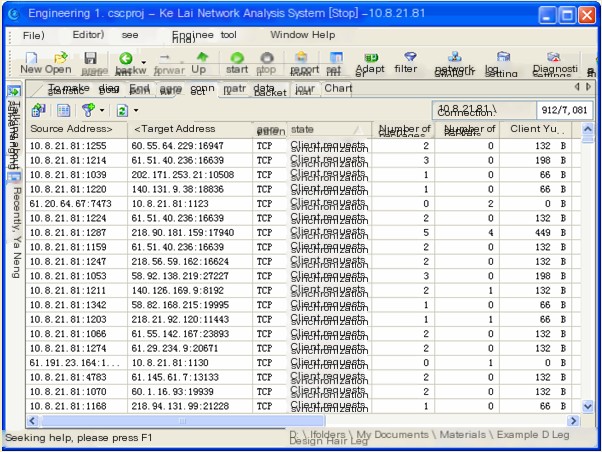
(Figure 2 Colasoft Network Analysis System’s Connection View)
From the connection information in Figure 2, it is evident that host 10.8.21.81 has established a large number of TCP connections with other hosts, and both the target address and target port are variable, with many connections being client synchronization requests. This indicates that host 10.8.21.81 may be conducting a scan.
Further examining the TCP packets of 10.8.21.81, we can view them in summary statistics and chart views, as shown below,
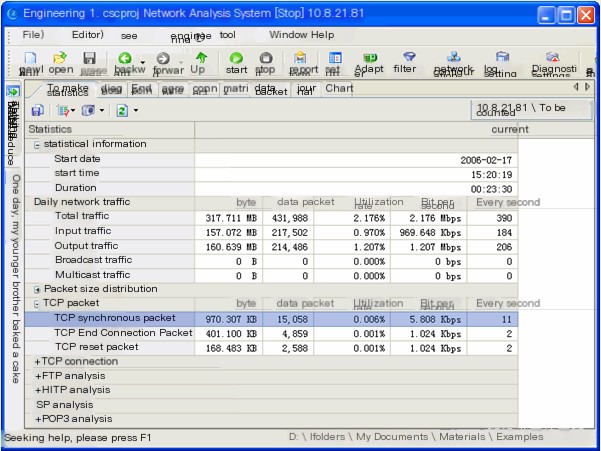
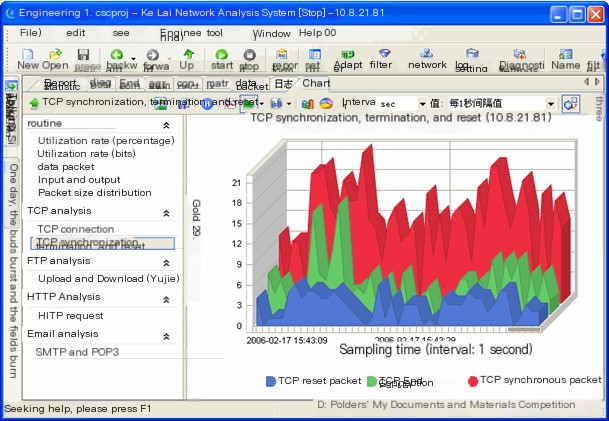
The above TCP packet information reveals that host 10.8.21.81 initiated a total of 15,058 TCP synchronization packets, while the end packets and reset packets were 4,859 and 2,588 respectively. This is not expected in a normal network.
Based on the above analysis, we deduce that host 10.8.21.81 is performing a scan attack and possibly probing open services on hosts in a fixed address range. We now disconnect the host with the address 10.8.21.81, then use the Colasoft Network Analysis System to analyze the network, which returns to normal. Isolating and eliminating the threat on 10.8.21.81 resolves the issue.


