
There is no doubt that Wireshark is currently the most widely used network traffic analysis tool. Whether for real-time network traffic analysis, information security forensics analysis, or malware analysis, Wireshark is an indispensable tool. Although Wireshark provides extremely powerful functionality for protocol parsing and filtering, it currently cannot provide any contextual information about the target network nodes. For a security analyst, they must sort through a large amount of PCAP files to identify malicious activity, which is like finding a needle in a haystack.
The wireshark-forensics-plugin is a cross-platform Wireshark plugin that correlates network traffic data with threat intelligence, asset classification, and vulnerability data to accelerate network forensic analysis activities. The tool extends Wireshark’s native search filters, allowing us to filter data based on these additional contextual attributes. In addition, the tool can process PCAP files and perform real-time traffic capture.
1. Load malicious indicator CSV exported from threat intelligence platforms like MISP, and associate them with every source/destination IP in network traffic.Load asset classification information based on IP range to asset type mapping, which can filter incoming/outgoing traffic for specific types of assets (e.g., filtering “database servers,” “employee laptops,” etc.).2. Load vulnerability scanning information exported from Qualys/Nessus into CVE.
3. Extend the functionality of native Wireshark filters, allowing filtering based on severity, source, asset type, and CVE information of each source or destination IP address in the network logs.
First, we need to use the following command to clone the project source code locally:
The data/formatted_reports directory in the project contains three files:
asset_tags.csv: Information about asset IP/domain/CIDR and related tags, with reference examples for internal network IPs and DNS servers;asset_vulnerabilities.csv: Detailed information on the CVE ID and top CVSS score of each asset;indicators.csv: Intrusion threat indicator IoC data, including attribute type, value, severity, and threat type;
The above three files can be manually edited, or vulnerability and indicator files can be generated using exported MISP and Tenable Nessus scan reports. At this time, the exported files need to be placed in the following folders with designated exact names:
data/raw_reports/misp.csv: This file can be exported from MISP via the path: “Export->CSV_Sig->Generate then Download”;
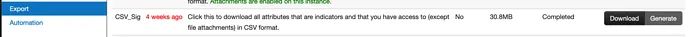
data/raw_reports/nessus.csv: This file can be exported through the Tenable Nessus interface;
Next, choose “Options->Export as CSV->Select All->Submit”, rename the downloaded file to nessus.csv, and copy it to “raw_reports/nessus.csv”.
If you plan to fetch data from ThreatStream instead of MISP, you need to provide the username, API key, and filter information in the config.json file. Each time you run the Python script, the tool will attempt to fetch the latest IoC from ThreatStream and store it in the data/formatted_reports/indicators.csv file.
If you are using a Windows system, you can directly run wft.exe; if on macOS or Ubuntu, you need to run “python wtf.py” to install and update report files. The script will automatically locate Wireshark’s installation path.
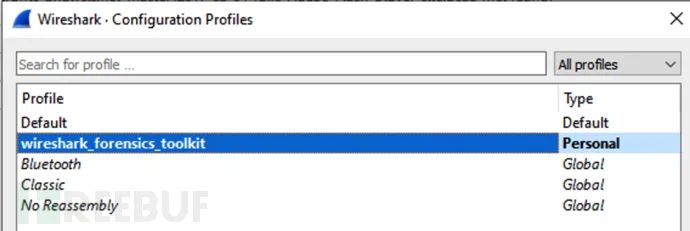
After installation, open Wireshark, click “Edit->Configuration Profiles”, and select “wireshark_forensics_toolkit”:
Now, start Wireshark, open a PCAP file or start real-time data capture:
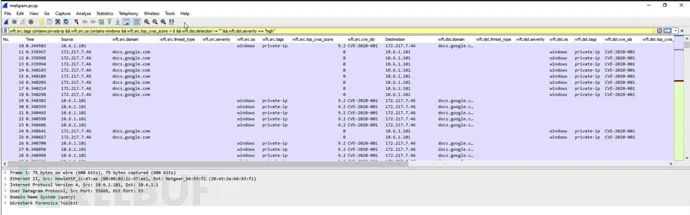
List of Available Filters
wft.src.domain (Source/domain resolution with previous DNS traffic)wft.src.detection (Source IP/domain detection using IOC data)wft.src.severity (Detection of vulnerability severity for source IP/domain using IOC data)wft.src.threat_type (Detection of threat type severity for source IP/domain using IOC data)wft.src.tags (Source IP/domain asset tags)wft.src.os (Source IP/domain operating system specified in vulnerability reports)wft.src.cve_ids (Comma-separated list of CVE IDs for source IP/domain)wft.src.top_cvss_score (CVSS score from all CVE IDs for a given host)



