Prepare: HIDS Implementation
1.1 Deploy HIDS and Security Equipment
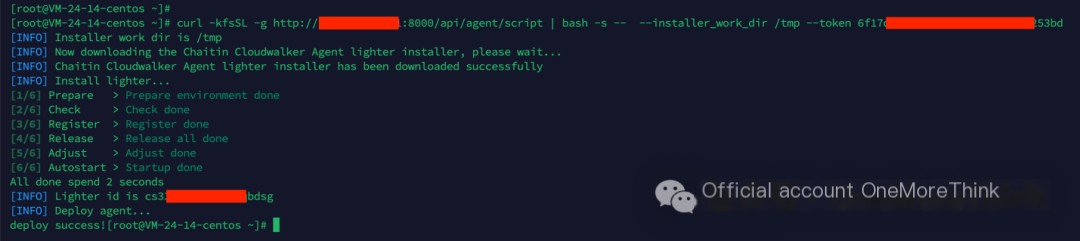
Deploy host security product: Muyun HIDS
 />
/>
2. Detection with HIDS
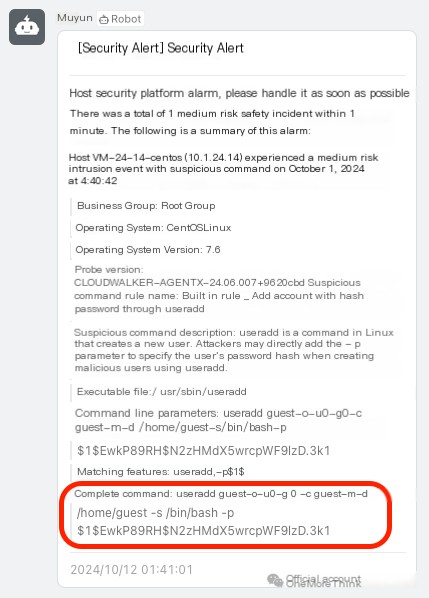
2.1 HIDS Device Alarm Generation
2024-10-12 01:40:42, Muyun generated an alert, the server executed a suspicious command:
useradd guest -o -u 0 -g 0 -c guest -m -d /home/guest -s /bin/bash -p 1EwkP89RH
 />
/>
Log into Muyun, the source IP address was found to be a French IP: 217.128.86.8
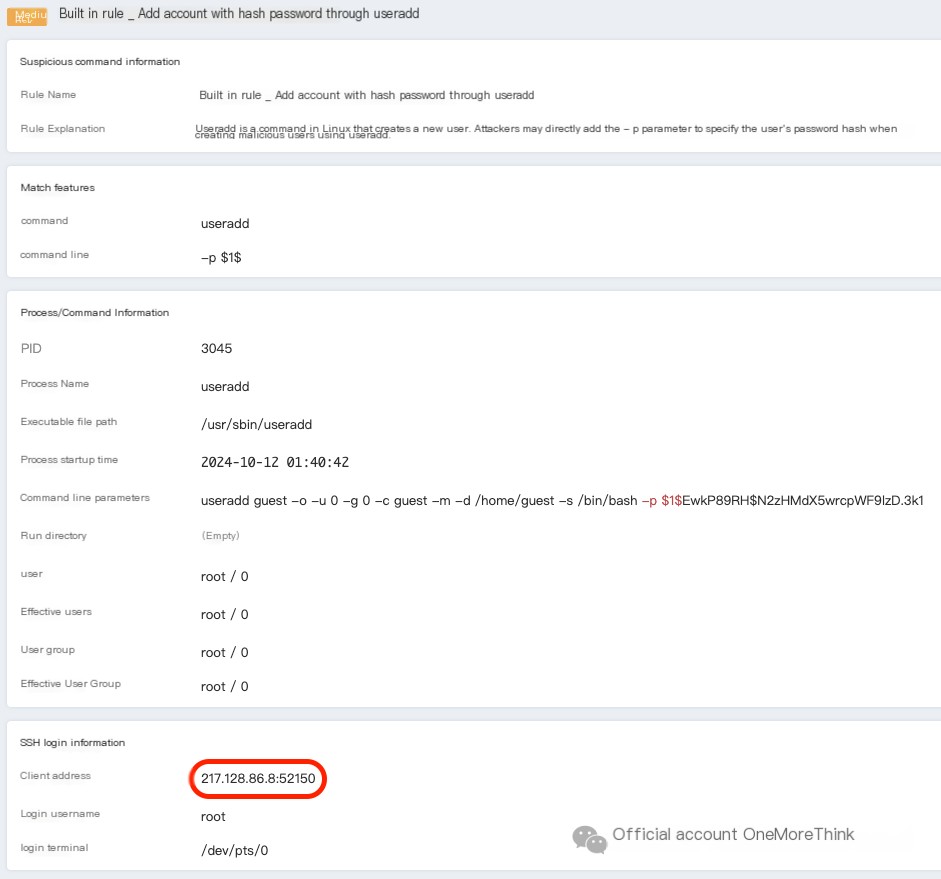
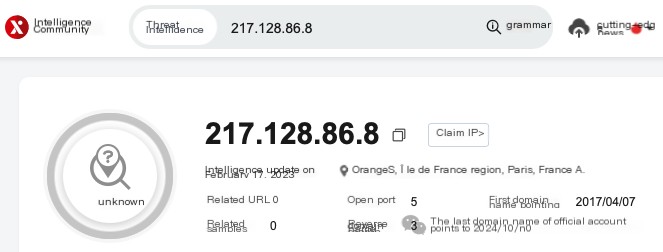
There are no other alerts for this IP in Muyun
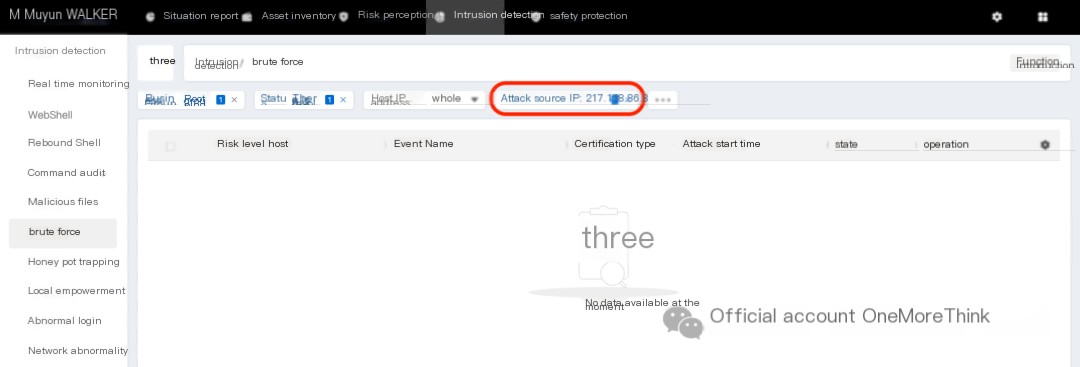
A foreign IP created a system account, which mostly confirms a real attack, and emergency measures need to be initiated
3. Contain Threats with HIDS
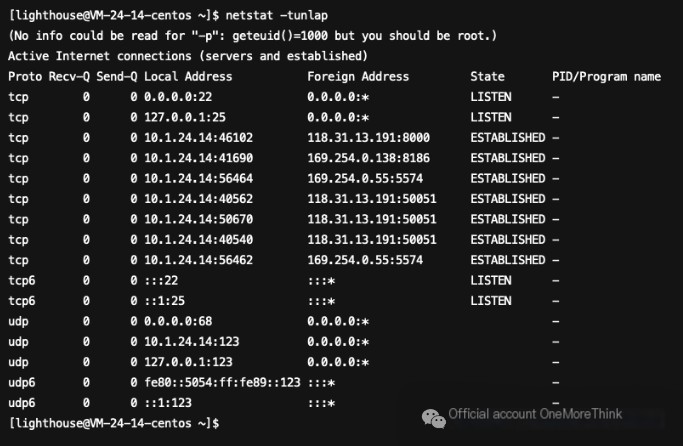
No abnormal network connections need containment
No abnormal processes need containment
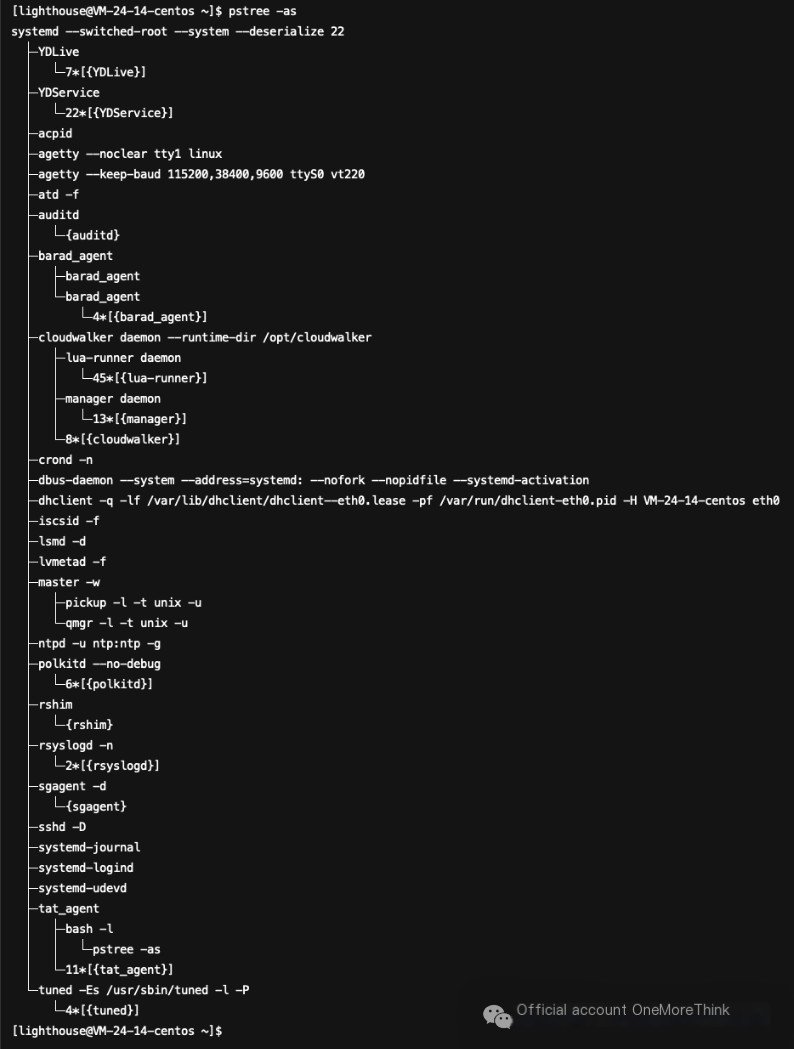
4. Eradicate
4.1 Delete Backdoor Account
Delete backdoor account: userdel -r guest
Error generated: user guest is currently used by process 1
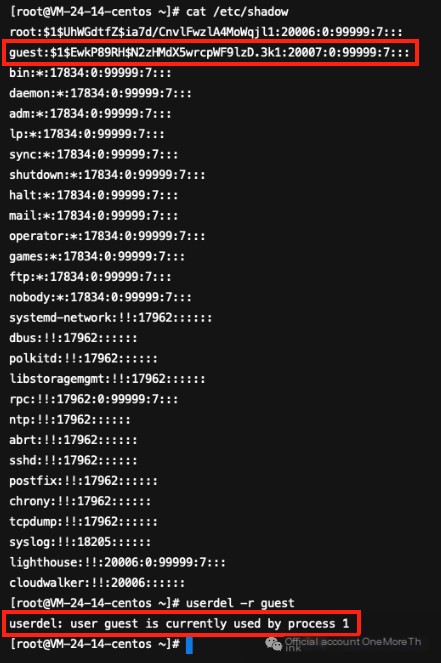
Since the uid and gid of the guest account are both 0, it’s normal for process 1 to use it
While planning to follow the method from https://www.rootop.org/pages/5075.html, the guest account somehow disappeared on its own
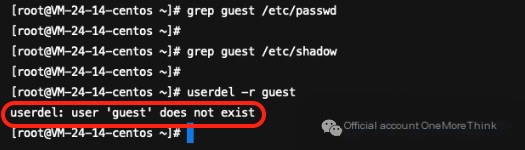
4.2 Strengthen Weak Password Account
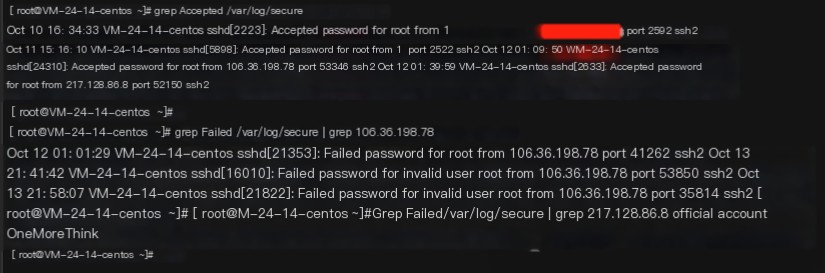
Check account login information and found that an IP address from Shaanxi, 106.36.198.78, also logged in. The details are as follows:
1. Oct 12 01:01:29: Shaanxi IP failed to log into root account once
2. Oct 12 01:09:50: Shaanxi IP successfully logged into root account once
3. Oct 12 01:39:59: French IP successfully logged into root account once
4. Oct 13 21:41:42: Shaanxi IP failed to log into root account twice
It can be speculated that the Shaanxi IP may have brute-forced the weak password of the root account and provided it to the French IP, or the French IP might have guessed the weak password on the first try.
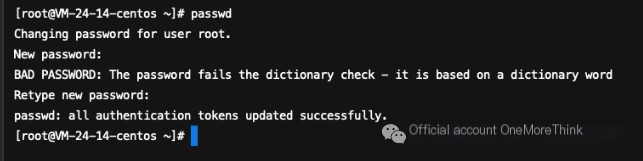
Change the weak password of the root account
5. Recover
5.1 Restore Account Login
Based on the ctime of /etc/shadow, it was identified that /etc/ssh/sshd_config was also tampered with by the attacker
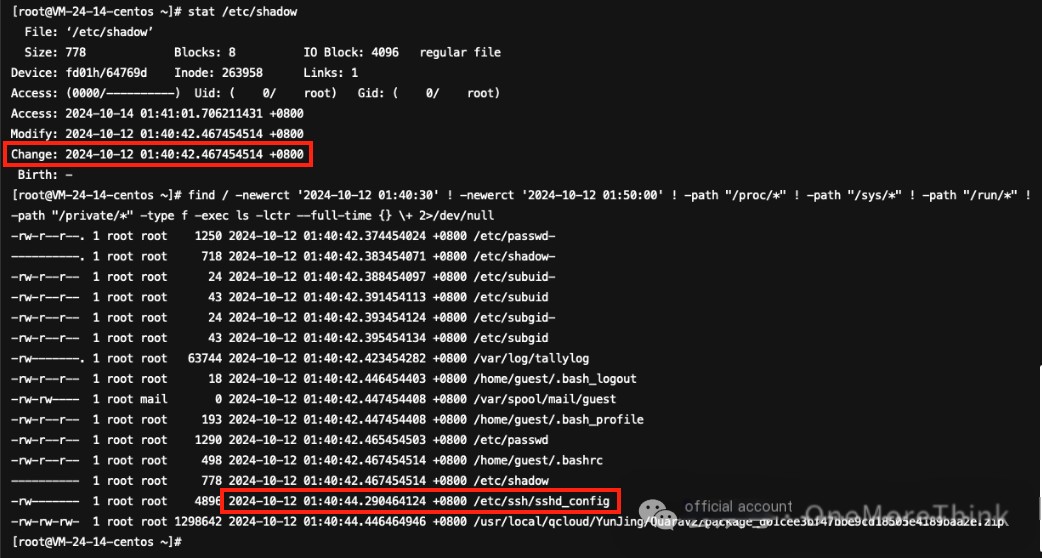
Checking /etc/ssh/sshd_config revealed that the attacker set the root user to be denied login: DenyUsers root
It seems the attacker was worried about a cooked duck flying away, so they conveniently helped in securing the weak password account.
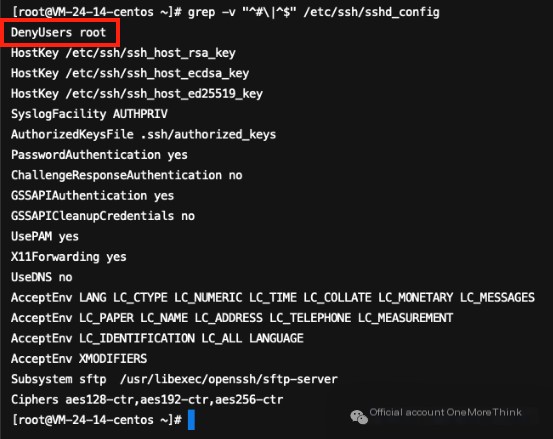
Remove this configuration item to restore root account login
6. Follow-Up
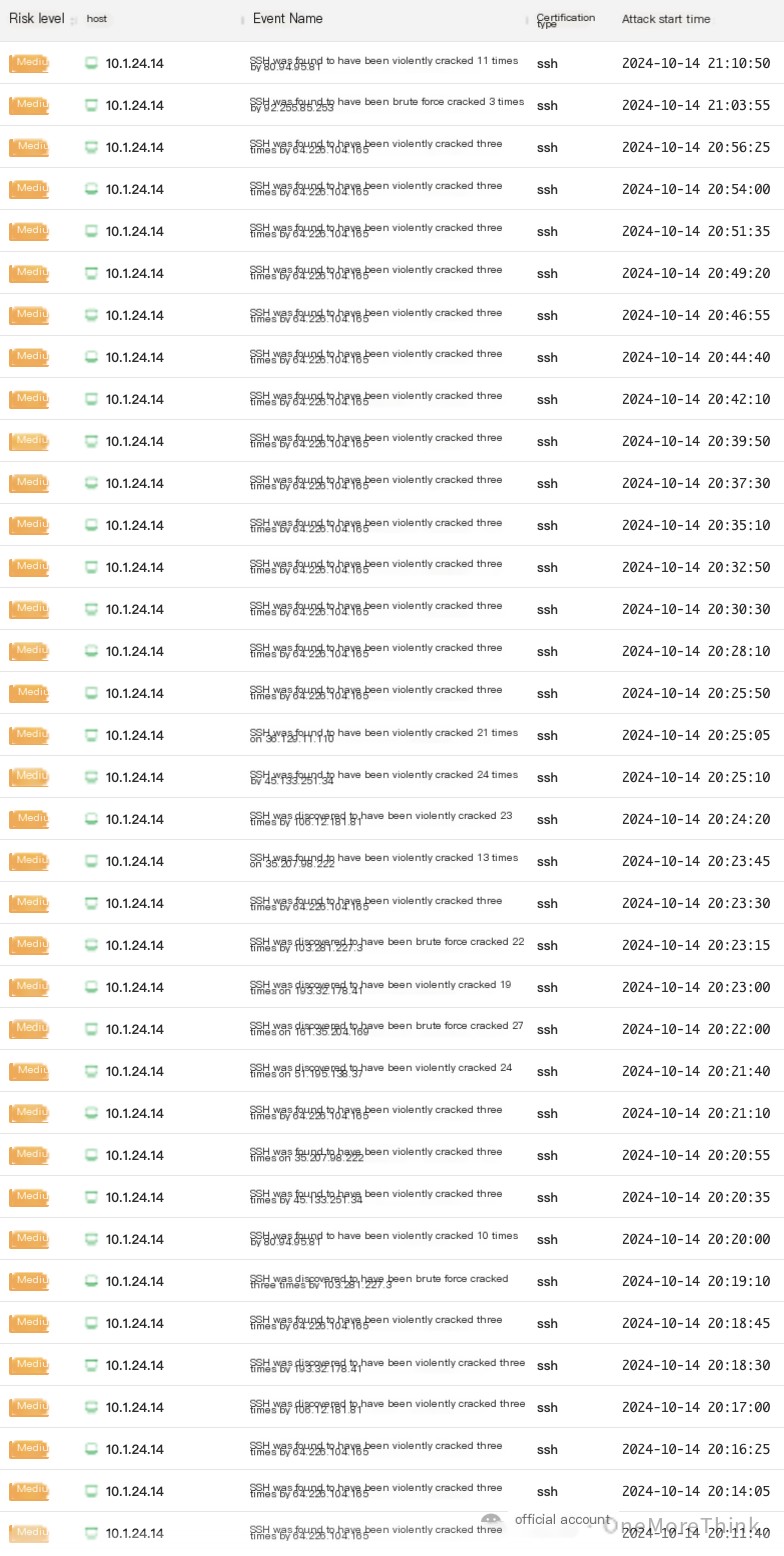
6.1 Change Login PortBrute force attack alerts are too numerous and overwhelming
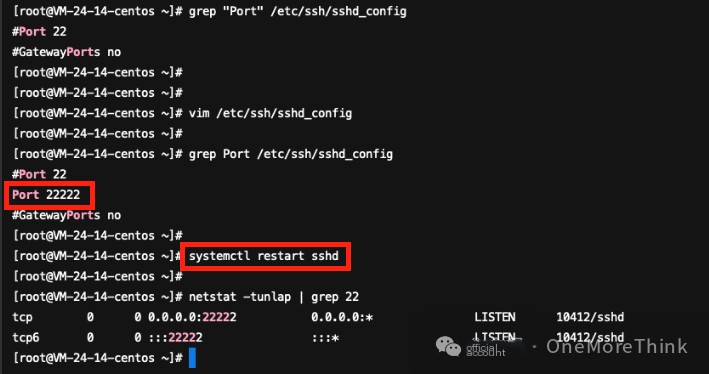
Change the SSH port to solve the issue
/etc/ssh/sshd_config: Port 22222
systemctl restart sshd
6.2 Enable Command Logging
To effectively monitor the commands executed by the attacker, enable the full command logging feature