Recently, the number of incidents involving reflective DDoS attacks using Memcached servers has increased significantly. The DDoS attack traffic exceeded T for the first time, causing a heated response from the cybersecurity industry. To shed light on the situation, Tencent Game Cloud now retraces the entire Memcached incident as follows:
Back on February 27, Cloudflare and Arbor Networks issued a warning on Tuesday that malicious attackers are abusing the Memcached protocol to launch distributed denial of service (DDoS) amplification attacks, affecting many servers around the world (including Arbor Networks). The following figure shows the monitored Memcached attack situation.
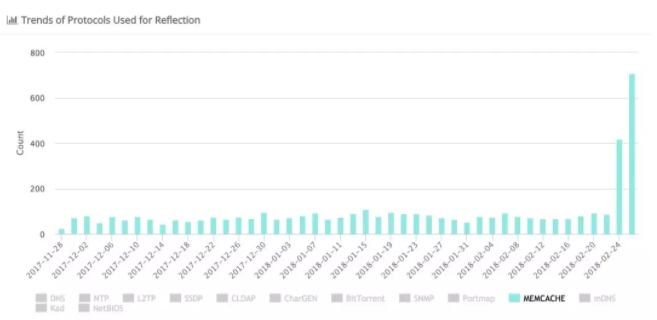
Just one day later, an attack traffic of 1.35Tbps broke the historical record of DDoS attacks.
On Wednesday afternoon, Eastern Time, GitHub revealed that it may have suffered the strongest DDoS attack in history. Experts said that the attacker used a new method of amplifying the attack, Memcached reflection attack, and a larger-scale distributed denial of service (DDoS) attack may occur in the future. The first peak traffic attack on the GitHub platform reached 1.35Tbps, followed by another peak of 400Gbps, which may also become the strongest DDoS attack recorded so far . The previous data was 1.1Tbps.
According to CNCERT on March 3, monitoring found that the peak traffic of the Memcached reflection attack reached 1.94Tbps at around 2:30 am Beijing time on March 1.
Tencent Cloud captures multiple Memcached reflective DDoS attacks
As of March 6, Tencent Cloud has captured multiple reflective DDoS attacks launched using Memcached. The main targets of the attacks include games, portals and other businesses.
Tencent Cloud data monitoring shows that the Memcached reflection attack launched by the black industry against Tencent Cloud business entered an active period from February 21, reaching a peak on March 1, and then the number of attacks decreased significantly, and then reached a peak again on March 5. The attack situation is shown in the following figure:

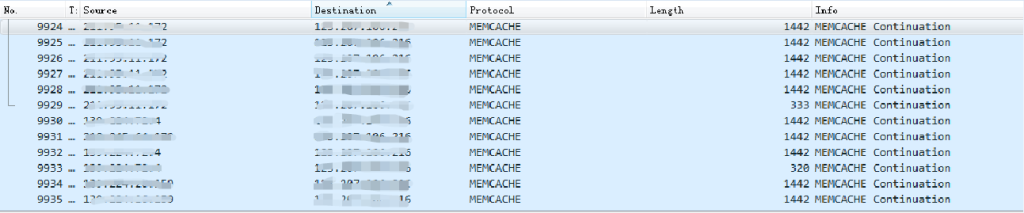
The following figure is a sample packet captured by Tencent Cloud of a Memcached reflective DDoS attack:
Tencent Cloud captured 22,511 Memcached reflection sources . The distribution of Memcached reflection sources is shown in the following figure:

Under the protection of Tencent Cloud Aegis security system, Tencent Cloud services are not affected by Memcached reflective DDoS attacks.
So, what is a Memcached reflection attack?
Generally speaking, we classify DDoS into various attack types, such as SYN Flood, ACK Flood, UDP Flood, NTP Flood, SSDP Flood, DNS Flood, HTTP Flood, ICMP Flood, CC, etc., according to the targeted protocol types and attack methods.
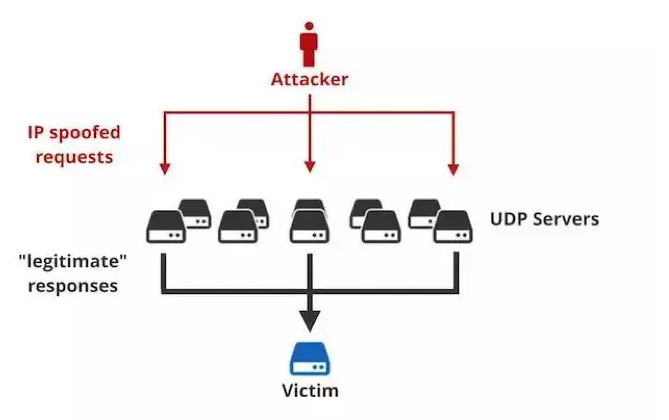
The history of DDoS attacks can be traced back to the 1990s, and reflective DDoS attacks are a more ingenious type of DDoS attacks. The attacker does not attack the target service IP directly, but forges the attacked IP to send a request message to a server that provides certain special services. The server will send reply data that is several times larger than the request message to the forged IP (i.e. the target service IP), thus achieving the effect of hitting the target from a distance and achieving the goal of achieving a great result with only a little effort. Memcached reflective attacks are more favored by attackers because of their amplification factor of tens of thousands of times.
Memcached reflection attack is that the attacker forges the IP address of the victim to send a large number of requests to the Memcached service that can be used on the Internet. Memcached responds to the requests. A large number of response messages converge to the forged IP address source, forming a reflective distributed denial of service attack.
Why does it pose such a big threat?
According to members of Tencent Cloud Aegis security team, the DDoS threats we faced in the past, such as NTP and SSDP reflection attacks, generally had a magnification factor of 30 to 50, while the magnification factor of Memcached is in the unit of 10,000, generally close to 50,000 times, and the possibility of this factor being further magnified cannot be ruled out. Using this feature, attackers can launch DDoS attacks with huge traffic using very little bandwidth.
Safety construction requires preparation
As early as when Memcached reflection-type DDoS attacks were testing Tencent’s business, Tencent Cloud had already sensed the risk and made preparations in advance. This round of DDoS attacks launched by hackers based on Memcached reflection were successfully protected.
At the same time, after capturing the Memcached attack, Tencent Cloud promptly assisted business customers in self-inspection and provided monitoring and repair suggestions to ensure that users’ servers were not used to launch DDoS attacks.
Security recommendations for dealing with large-volume DDoS attacks
DDoS attacks are becoming more and more severe, constantly breaking attack traffic records. Faced with large-scale traffic attacks exceeding the Tbps level, the Tencent Cloud Aegis Security Product Team recommends that users take the following measures:
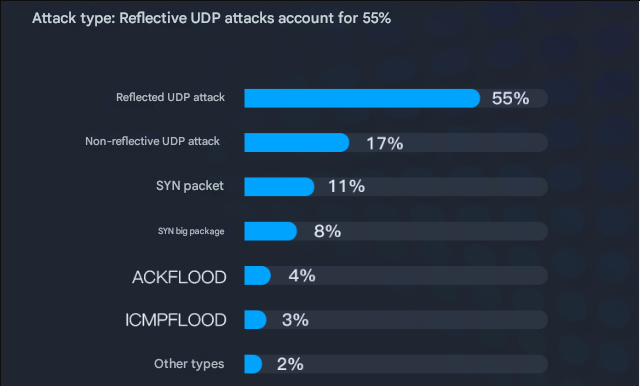
1. We need to pay more attention to reflective UDP attacks and improve our risk awareness
Reflective UDP attacks account for half of DDoS attacks. According to the 2017 Tencent Cloud Gaming Industry DDoS Attack Situation Report, reflective UDP attacks accounted for 55% of DDoS attacks in 2017, and this type of attack needs to be paid special attention to.
This Memcached reflection attack is a relatively new type of reflection UDP attack, which brings huge security risks. The industry needs to continue to pay attention to Internet security trends, improve risk perception, and prepare strategic responses. It is necessary to conduct necessary drills when threats break out in the industry.
2. To deal with the threat of ultra-large traffic attacks, it is recommended to connect to Tencent Cloud’s ultra-large capacity high-defense products
To deal with the escalating risk of DDoS attacks. It is recommended to configure Tencent Cloud’s ultra-large capacity high-defense products to hide the source station IP. Use the high-defense IP’s sufficient bandwidth resources to deal with possible large-volume attacks, and formulate personalized protection strategies based on business characteristics. Only when attacked by DDoS can business availability be guaranteed and handled calmly. When facing high-level DDoS threats, upgrade the protection configuration in a timely manner, and request expert services from DDoS protection vendors when necessary .
Learn about Tencent Cloud’s new generation of high-defense products: https://cloud.tencent.com/product/aegis
3. Industries vulnerable to large-volume attacks need to strengthen their defenses
Industries that have been vulnerable to black market attacks in previous years, such as portals, finance, and gaming, need to step up their defenses, and businesses with weaker DDoS protection capabilities, such as government, need to be more vigilant against large-volume attacks.
Risks often show signs of emerging, and once ignited by the spring breeze of black industries, they will ignite a prairie fire without any protection.


