1. Understanding BeEF and Its Threats
Defending against BeEF attacks is essential for maintaining the security of web applications and user data. This article explores effective methods to detect and defend against BeEF attacks, ensuring your systems remain secure.
1.1 Traffic Analysis
Traffic analysis is a common method for detecting BeEF. By examining characteristics and patterns in network traffic, you can identify communication between the attacker and the BeEF server. Here are some examples of traffic analysis:
1.1.1 HTTP Requests and Responses
BeEF uses the HTTP protocol to communicate with infected browsers. Attackers inject malicious scripts into target websites, and when victims visit these pages, the scripts send HTTP requests to the BeEF server. Detecting specific HTTP requests in network traffic can help reveal the presence of BeEF.
1.1.2 WebSocket Communication
BeEF can also use the WebSocket protocol to establish persistent communication channels with infected browsers. Attackers may use WebSocket for command and data exchange. Therefore, detecting WebSocket communication in network traffic can uncover BeEF’s presence. Sax2 IDS is an advanced intrusion detection system designed to monitor and identify abnormal or malicious activities within computer networks and systems. It has a built-in security policy to detect BeEF traffic, which can be easily discovered. The following describes the use of Sax2 to detect BeEF traffic in detail. Click on the URL “https://www.ids-sax2.com/wp-content/download/Sax2_Setup(409).exe” to download Sax2 NIDS, and after downloading, double-click on the installer and the installation prompt will make it easy to install Sax2 NIDS.
tep 1. Start the Sax2 NIDS
After installing Sax2 NIDS correctly, you will see the following icon on the desktop, double-click it to start Sax2 NIDS
Step 2. Start Detecting BeEF traffic
After starting Sax2, click the “Start” button on the main interface to start the intrusion detection, please see the figure below:
Step 3. View Intrusion Events
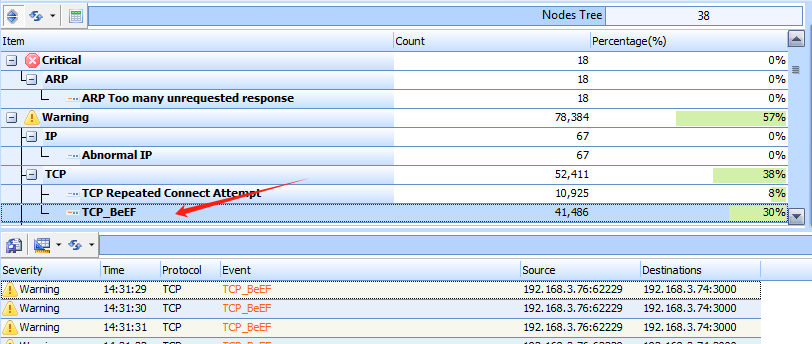
The “Events” viewing window is one of the most important features of Sax2 NIDS and the main place to analyze intrusion events. In order to view the event, first switch to the Events window. Take a look at the following figure, from which you can see that Sax2 has successfully detected the BeEF traffic.
1.1.3 Anomalous Traffic Patterns
BeEF’s communication patterns may differ from normal network traffic. For example, BeEF communication might involve high frequency, large amounts of data transfer, or unusual data patterns. Monitoring and analyzing network traffic can detect these anomalies.
1.2 Network Scanning and Vulnerability Scanning
Network and vulnerability scanning are other methods for detecting BeEF. Here are some examples:
- Port Scanning: BeEF servers typically listen on specific ports for connections and commands from infected browsers. Performing a port scan can identify open ports that may indicate the presence of a BeEF server.
- Vulnerability Scanning: BeEF exploits browser vulnerabilities and weaknesses. Vulnerability scanning can detect system vulnerabilities related to BeEF. Some scanning tools can automatically identify and report vulnerabilities associated with BeEF, helping to determine its presence.
1.3 Security Log Analysis
Security log analysis is a comprehensive detection method that combines traffic analysis, event logging, and anomaly detection. Here are some examples:
- Web Server Access Logs: Analyzing web server access logs can reveal anomalous requests related to BeEF. For instance, detecting specific HTTP request paths, parameters, or User-Agent strings might indicate BeEF activity.
- Security Event Logging: System security event logs may contain unusual events related to BeEF, such as malicious script injections, unauthorized access, or abnormal browser behavior. These could be signs of BeEF activity.
- Anomaly Detection: By monitoring system behavior and activity, you can detect anomalous behaviors related to BeEF. For example, discovering abnormal browser plugins or extensions, unknown network connections, or suspicious file downloads may indicate BeEF’s presence.
1.4 Example Scenario
Suppose we are detecting a BeEF attack on a target system. Here is a specific example:
We use a network traffic analysis tool to monitor traffic on the target system. During the analysis, we observe some anomalous HTTP requests with paths and parameters related to BeEF activity. For instance, requests containing “hook.js” files or specific URL paths are noted. Additionally, the User-Agent strings in these requests may include identifiers related to BeEF.
By further analyzing the source IP addresses and destination servers of these requests, we can identify potential BeEF servers. We might also use vulnerability scanning tools to detect any vulnerabilities related to BeEF in the target system.
Simultaneously, we analyze system security logs and event records. In the logs, we find unusual browser behaviors, such as unauthorized script injections and malicious extension installations. These are typical indicators of a BeEF attack.
Based on these analysis results, we conclude that the target system might be subject to a BeEF attack. Further investigation and response actions could include tracking the attacker’s IP address, isolating infected hosts to prevent further attacks, and patching vulnerabilities related to BeEF.
1.5 Summary
Detecting BeEF involves a complex process that includes traffic analysis, network scanning, vulnerability scanning, and security log analysis. By combining these methods and observing abnormal behaviors and patterns, you can effectively detect the presence of BeEF. Appropriate measures can then be taken to address this threat and protect the target system’s security.
2. Key Strategies to Defend Against BeEF Attacks
Defending against BeEF (Browser Exploitation Framework) attacks is crucial since this tool can be used by hackers to exploit browser vulnerabilities and control target systems. In this article, we will explore methods to defend against BeEF attacks and illustrate their depth and complexity with specific examples.
2.1 Security Awareness Training
Increasing user security awareness is the first step in defending against BeEF attacks. Users should receive regular security training to understand common social engineering attacks and browser-specific attack techniques. They should learn to recognize and avoid clicking on malicious links, downloading untrusted attachments, and visiting insecure websites. Here is a specific example:
- A company organized employee security training, which included information about BeEF attacks. The training focused on educating employees on avoiding suspicious links and downloading unverified files. By providing real case studies and simulated exercises, employees learned to identify potential BeEF attacks and take appropriate defensive measures.
2.2 Browser Security Settings and Updates
Maintaining browser security settings and updates is key to defending against BeEF attacks. Here are some examples:
- Installing Security Plugins: Installing trusted browser security plugins, such as NoScript, AdBlock Plus, and HTTPS Everywhere, can help block potential malicious scripts and ads.
- Disabling or Restricting Plugins: Disable or limit the use of browser plugins, especially those that are seldom used or untrusted. Attackers may exploit vulnerabilities in plugins to carry out BeEF attacks.
- Automatic Updates: Ensure that browsers and their related components (such as Flash Player, Java, etc.) are automatically updated to the latest versions. Latest browser versions usually contain fixes for known vulnerabilities.
2.3 Network Firewalls and Intrusion Detection Systems (IDS)
Using network firewalls and IDS can help defend against BeEF attacks. Here are some examples:
- Outbound Traffic Filtering: Configure network firewalls to monitor and filter outbound traffic. When malicious traffic related to BeEF is detected, the firewall can block connection attempts or alert the security team.
- IDS Rules: Use specific rules in the IDS to detect traffic patterns related to BeEF attacks. For example, detecting specific HTTP request paths, parameters, or User-Agent strings can trigger alerts or block further attacks.
2.4 Operating System and Application Updates
Regularly updating the operating system and applications is an important measure for defending against BeEF attacks. Here are some examples:
- Operating System Updates: Ensure that the operating system and its related components (such as network protocol stacks and browsers) are updated to the latest versions. Updates usually include fixes for known vulnerabilities and security enhancements.
- Application Updates: Keep commonly used applications (such as Office suites, PDF readers, etc.) updated to the latest versions. This reduces the chances of attackers exploiting application vulnerabilities to carry out BeEF attacks.
2.5 Defending Against Malicious Websites and Links
Defending against malicious websites and links is a crucial measure for protecting against BeEF attacks. Here are some examples:
- Secure Website Access: Deploy web filters and malware protection tools within the company network to block access to known malicious websites.
- Anti-Phishing and Anti-Malware Technologies: Browsers and security software can detect and block access to known malicious websites and links, displaying warning messages to users.
- URL Filtering: Configure URL filtering rules on network firewalls or proxy servers to block access to known malicious URLs.
2.6 Vulnerability Management and Patch Management
Timely fixing vulnerabilities in browsers and related applications is an essential step for defending against BeEF attacks. Here are some examples:
- Vulnerability Scanning and Assessment: Regularly conduct vulnerability scanning and assessments to identify and fix vulnerabilities in browsers and applications. These vulnerabilities may be entry points for attackers using BeEF.
- Patch Management: Establish an effective patch management process to ensure timely application of security patches for operating systems and applications. This reduces the chances of attackers exploiting known vulnerabilities for BeEF attacks.
2.7 Security Monitoring and Incident Response
Establishing security monitoring and incident response mechanisms is key to detecting and responding to BeEF attacks in a timely manner. Here are some examples:
- Log Monitoring: Monitor browser and related system logs in real-time to detect abnormal activities related to BeEF attacks. This helps in quickly discovering and addressing potential attack behaviors.
- Threat Intelligence: Subscribe to threat intelligence services to get the latest information on BeEF attacks and lists of malicious IP addresses. This information helps adjust defense strategies and enhance protection against BeEF attacks.
- Response Plan: Develop a detailed incident response plan that includes detection, analysis, and response measures for BeEF attacks. This ensures rapid and effective action in case of an attack.
2.8 Summary
Defending against BeEF attacks requires a multi-layered security approach, including security awareness training, browser security settings and updates, network firewalls and IDS, operating system and application updates, defense against malicious websites and links, vulnerability and patch management, and security monitoring and incident response. By combining these measures and continually updating and improving defense strategies, organizations can enhance their protection against BeEF attacks and safeguard browser and system security.
3.Security Awareness Training to Defend Against BeEF Attacks
Enhancing the security of web applications is crucial to preventing the misuse of tools like BeEF. Web applications are central to many organizations’ operations, making it vital to protect them from malicious attacks. In this article, we will explore various methods for strengthening web application security, providing detailed examples to demonstrate the complexity and depth of the subject.
3.1 Secure Development Lifecycle (SDLC)
Adopting a Secure Development Lifecycle (SDLC) is a key step in ensuring web application security. SDLC includes the following phases:
- Requirements and Design: During the web application design phase, consider security requirements and design principles. For example, use secure development frameworks, apply the principle of least privilege, and follow secure coding practices.
- Coding and Testing: During the coding process, implement secure coding guidelines such as input validation, output encoding, and preventing attacks like Cross-Site Scripting (XSS) and SQL Injection. Perform regular static code analysis and dynamic security testing to identify potential vulnerabilities.
- Deployment and Maintenance: Before deploying the web application, perform security configurations and hardening. Regularly update and patch known vulnerabilities, and monitor the application to ensure continued security.
3.2 Input Validation and Data Filtering
Strengthening input validation and data filtering in web applications is a crucial defense against BeEF attacks. Here are some examples:
- Input Validation: Strictly validate and filter user input data to prevent malicious input. For example, use whitelist validation for form fields and exclude illegal characters and special symbols.
- Reject Invalid Data: When the application receives invalid or incorrect data, it should immediately reject it and provide clear error messages to the user.
- Output Filtering: Properly encode and filter output before sending data back to the user to prevent XSS attacks. For instance, use HTML encoding or secure template engines.
3.3 Authentication and Access Control
Strengthening authentication and access control is key to protecting web applications from BeEF and similar attacks. Examples include:
- Strong Password Policy: Require users to set strong passwords and enforce policies such as password length, complexity, and expiration.
- Multi-Factor Authentication (MFA): Implement MFA, such as SMS verification, hardware tokens, or biometrics, to enhance authentication security.
- Principle of Least Privilege: Apply the principle of least privilege to access control for users and roles. Grant users only the minimum necessary permissions to reduce the attack surface.
3.4 Secure Session Management
Strengthening session management is an important defense against BeEF attacks. Examples include:
- Secure Session Identifiers: Generate strong, random session identifiers and use HTTPS to transmit them to prevent session hijacking.
- Session Timeout: Set appropriate session timeout periods to automatically log out users after a period of inactivity.
- Prevent Session Fixation Attacks: Generate a new session identifier each time a user authenticates and regenerate it during important actions.
3.5 Secure File Upload and Download
Strengthening the file upload and download functions of web applications is another critical aspect of preventing attacks like BeEF. Examples include:
- File Upload Validation: Implement strict validation and filtering for file uploads, allowing only safe file types and detecting malicious content.
- File Download Security: Ensure that file paths and names are not controlled by users and restrict access to sensitive files when providing download functionality.
- Secure File Storage: Store uploaded files in secure locations and use appropriate access control mechanisms to prevent unauthorized access.
3.6 Real-Time Monitoring and Logging
Real-time monitoring and logging are key measures for improving web application security. Examples include:
- Security Event Monitoring: Use tools like Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) to monitor security events in real time and respond to potential attacks.
- Security Logging: Enable detailed logging to record key events and actions for security audits and investigations. Logs should include user activity, abnormal behavior, and potential attack indicators.
- Real-Time Alerts and Response: Set up real-time alerts to notify relevant personnel when security events occur, allowing for immediate response.
In summary, strengthening web application security is critical to protecting against attacks like BeEF. By adopting a Secure Development Lifecycle approach, improving input validation and data filtering, enhancing authentication and access control, securing session management, ensuring safe file uploads and downloads, and implementing real-time monitoring and logging, the security of web applications can be greatly improved. These measures need to be comprehensively considered and customized based on specific applications and environments to ensure the security and reliability of web applications.


