Socks5 password brute force attacks are a type of cyberattack targeting Socks5 proxy servers. Socks5 is a protocol that allows clients to route network traffic through a proxy server, which can be used to anonymize or secure network connections. In a brute force attack, attackers use automated tools to try a large number of username and password combinations in an attempt to gain unauthorized access to the Socks5 server.
Characteristics of Socks5 Password Brute Force Attacks
- Automated Attempts: Attackers use scripts or tools to systematically try numerous username and password combinations.
- Repeated Attempts: The attack involves making repeated login attempts until a valid combination is found.
- Exploitation of Weak Credentials: Attackers often target accounts with weak, common, or easily guessable passwords.
Detect Socks5 Password Brute Force Attacks with Sax2
Step 1. Install Sax2 IDS
After installing Sax2 NIDS correctly, you will see the following icon on the desktop, double-click it to start Sax2 NIDS
Step 2. Start Detecting
After starting Sax2, click the “Start” button on the main interface to start the intrusion detection, please see the figure below:
Step 3. View Intrusion Events
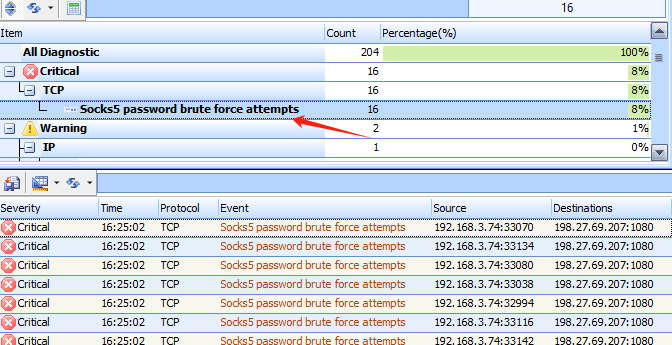
The “Events” viewing window is one of the most important features of Sax2 NIDS and the main place to analyze intrusion events. In order to view the event, first switch to the Events window. Take a look at the following figure, from which you can see that Sax2 has successfully detected the POP3 password brute force attacks.
Detailed Defense Measures Against Brute Force Attacks to Socks5 Password
1. Use Strong Passwords:
- Password Complexity: Ensure that passwords are complex, including a mix of upper and lower case letters, numbers, and special characters. For example, use passwords like
D7#sT8v&!qRrather than simple ones likepassword123. - Password Policies: Implement policies requiring password changes at regular intervals (e.g., every 90 days) and prohibit the reuse of previous passwords.
- Password Management Tools: Use password managers to generate and store complex passwords securely.
2. Limit Login Attempts:
- Account Lockout: Configure the Socks5 server to lock accounts after a certain number of failed login attempts (e.g., lock for 15 minutes after 5 failed attempts).
- Rate Limiting: Implement rate limiting to restrict the number of login attempts per IP address within a specified period. For example, limit login attempts to 10 per hour per IP address.
- IP Blocking: Automatically block IP addresses that exhibit suspicious behavior, such as repeated failed login attempts, for a specific duration.
3. Enable Multi-Factor Authentication (MFA):
- Implement MFA: Use an MFA solution that requires an additional verification step, such as a code sent via SMS or generated by an authenticator app, in addition to the password.
- Integrate with Socks5: Ensure that the Socks5 server or proxy software supports MFA integration, or use a third-party authentication service that supports Socks5.
4. IP Address Restrictions:
- Access Control Lists (ACLs): Configure ACLs on the Socks5 server to allow access only from known and trusted IP addresses or address ranges. For example, only allow connections from your organization’s IP ranges.
- Geo-Blocking: Use geo-blocking to restrict access based on geographic location. For instance, block IP addresses from countries where you do not expect legitimate access.
5. Use Secure Connections:
- Encryption: Configure Socks5 to use TLS (Transport Layer Security) to encrypt data transmitted between clients and the proxy server. Ensure that the TLS certificate is valid and up-to-date.
- Protocol Upgrades: Use the latest version of Socks5 or alternative secure protocols that provide encryption and improved security features.
6. Regular Updates and Patching:
- Software Updates: Regularly update Socks5 server software and associated components to patch known vulnerabilities. Subscribe to security bulletins or newsletters from the software vendor for timely updates.
- Patch Management: Implement a patch management policy to ensure that all security updates are applied promptly and tested before deployment.
7. Log Auditing and Analysis:
- Enable Detailed Logging: Configure the Socks5 server to log detailed information about login attempts, including IP addresses, timestamps, and success or failure status.
- Use Log Analysis Tools: Employ log analysis tools or SIEM systems to automate the monitoring and analysis of log files for signs of suspicious activity or brute force attacks.
- Regular Audits: Conduct regular audits of logs to identify trends, anomalies, or potential security issues.
8. Deploy Intrusion Detection Systems (IDS):
- Network IDS: Deploy IDS solutions that can monitor network traffic for suspicious patterns indicative of brute force attacks. Configure the IDS to alert on unusual traffic patterns or multiple failed authentication attempts.
- Host-Based IDS: Implement host-based IDS on the Socks5 server to detect and respond to malicious activities and anomalies at the server level.
9. Implement Network Segmentation:
- Segregate Network: Place the Socks5 server in a separate network segment or DMZ (Demilitarized Zone) to limit exposure to internal systems and reduce the impact of potential attacks.
- Firewalls: Use firewalls to control and monitor traffic between different network segments, ensuring that only authorized traffic can reach the Socks5 server.
10. Employ Behavior-Based Security:
- Anomaly Detection: Implement security solutions that use behavior-based analysis to detect deviations from normal user behavior, such as unusual login frequencies or access patterns.
- Adaptive Security Policies: Develop adaptive security policies that adjust access controls based on real-time analysis of network traffic and user behavior.
Conclusion
By implementing these specific defensive measures, you can enhance the security of your Socks5 server and reduce the risk of password brute force attacks. Properly configuring and maintaining these defenses will help protect against unauthorized access and ensure the integrity of your network.


