What is SQL slammer worm?
SQL Slammer is a worm that targets unpatched Microsoft SQL 2000 servers. The worm spreads between servers, increasing traffic on UDP port 1434 and causing heavy network traffic that can slow down network performance and lead to denial of service. SQL slammer does not carry a destructive payload. Despite its name, it does not use the SQL language.
Techopedia explains SQL Slammer
The 418-byte worm packet only affects SQL servers that are not running SP3, a Windows software service pack that includes a patch to fix the buffer overflow bug the worm exploits. The small piece of worm code generates random IP addresses and sends itself to those addresses from the infected system.
The main symptom of an SQL Slammer infection is high outgoing traffic to UDP 1434. Because the worm was able to fit into one packet, it could be propagated rapidly as computers fired off infected packets. As a result, it caused several denial-of-service attacks in 2002 and 2003. A patch provided by Microsoft in 2002, as well as increased media coverage of this worm, had greatly reduced the risk of infection by 2004.
How to detect SQL slammer worm in protocol tab
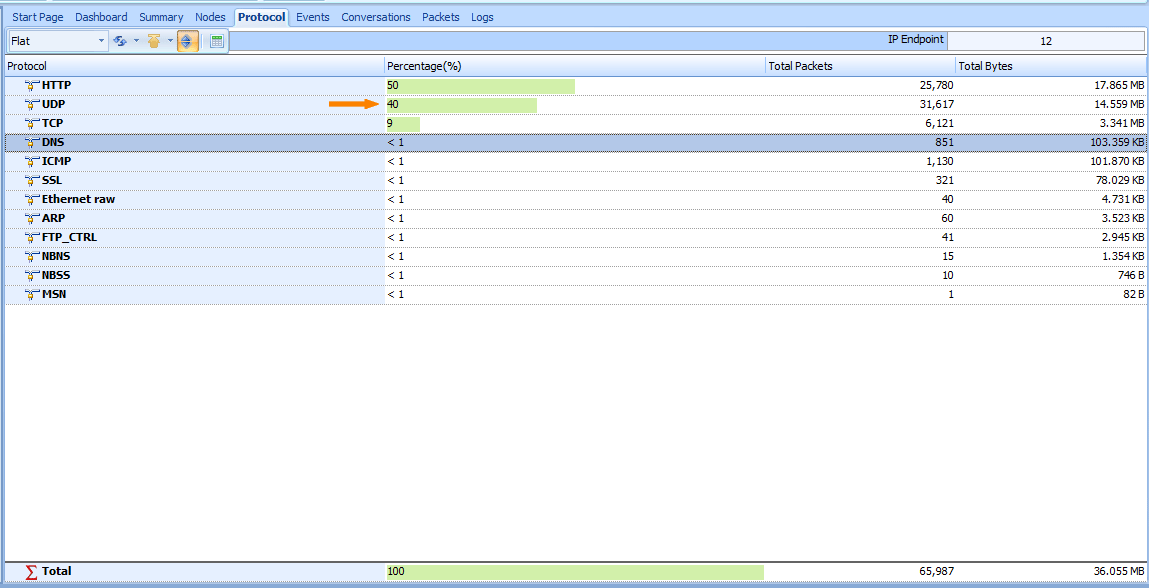
Ok, let’s launch the Unicorn and start a new project. When a computer is infected by SQL Slammer, which will sends a lot of packets to UDP 1434, So the UDP traffic will account for a considerable proportion of the total traffic. To view protocol traffic detail, please switch to Protocol tab.
Figure 1: Detect SQL slammerWorm in Protocol Tab
How to detect SQL slammer worm in Nodes tab
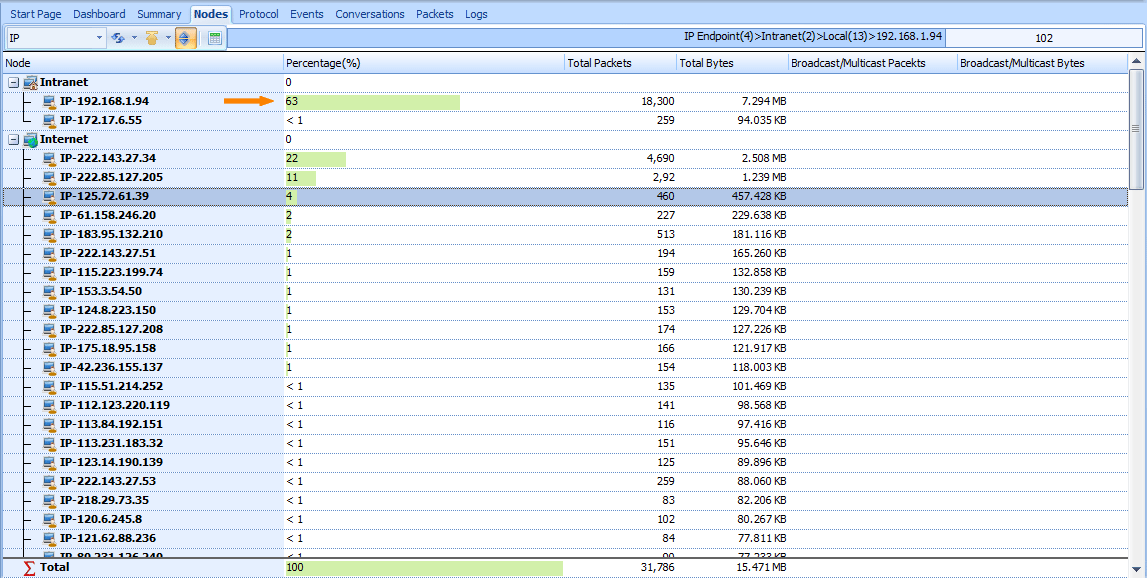
Traffic detail of all nodes are listed in the Nodes tab window, By viewing all records, we found that traffic of ‘192.168.1.94’ node accounted for a considerable proportion of the total traffic, to reached 63% and all are outgo traffic, this is an abnormal phenomenon. please see figure below:
Figure 2: Detect SQL slammerWorm in Nodes Tab
How to detect SQL slammer worm in Conversation View
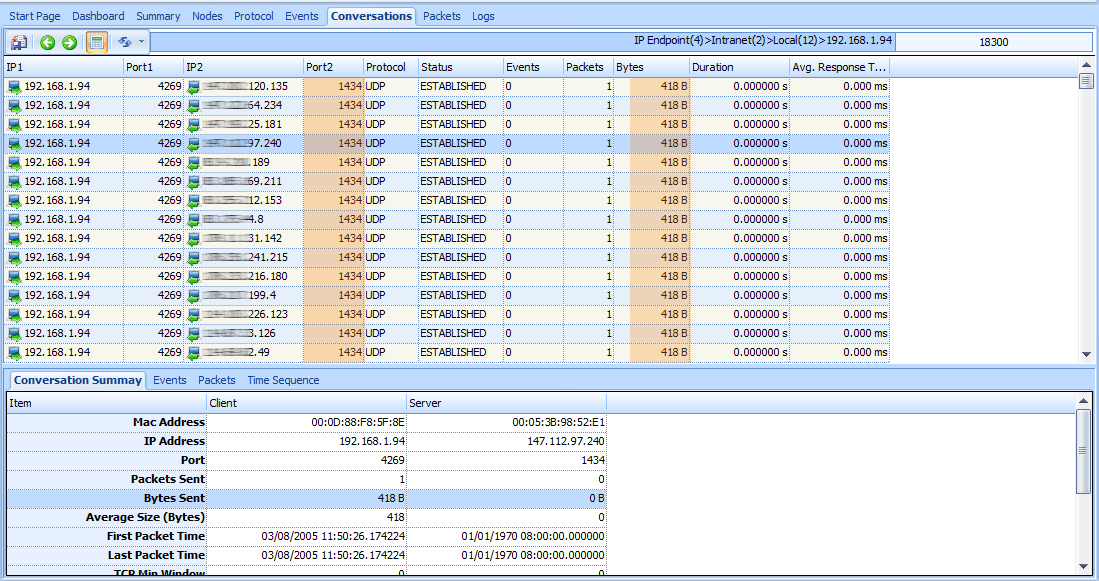
To confirm that the computer is infected with SQL slammer Worm, we need to view conversation relate to the ‘192.168.1.94’ node. Let’s select the ‘192.168.1.94’ node in nodes explore window and switch to conversation tab, we saw that the node sent a 418 byte long UDP packet to port 1434 using random targets at a very high rate. The 1434 is default port of SQL server connection, so we confirmed that the computer is infected with SQL slammer Worm and is scanning other computer.
Figure 3: Detect SQL slammerWorm in Conversation view