System Center Configuration Manager (SCCM) allows administrators to publish software installers to the Software Center or the currently logged-in user, more commonly running with NT Authority\System privileges. For more information on SCCM deployment types, see here.
Depending on how the installer command is deployed, a malicious user might use these whitelisted installers to elevate privileges on their computer. Typically, this would be possible if users are allowed to interact with the installer. Below is an example scenario.
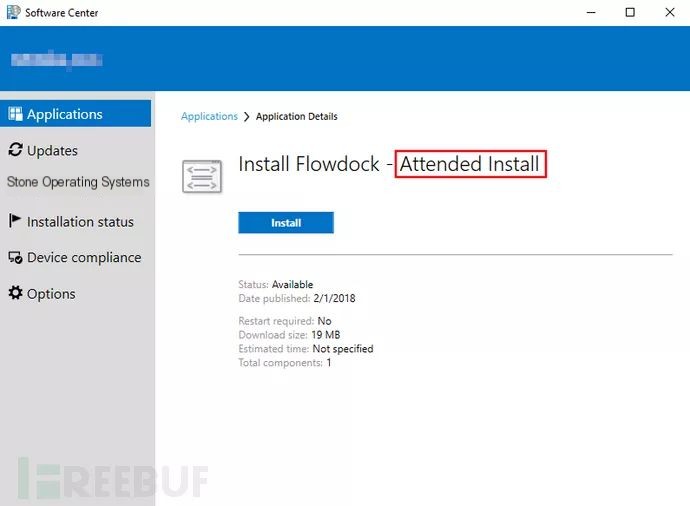
The application “Flowdock” published in the Software Center is available for installation and is marked as “Attended Install”.
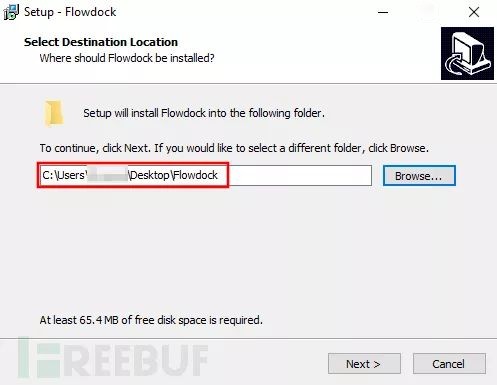
The installer runs and allows us to set the installation path, which is (usually) an essential condition for this attack. If the program is installed in Program Files, a low-privilege user cannot write to the installation directory. Conversely, if we can control the installation path, we can change it to a location where we have sufficient permissions. Here, I choose to install the program on my desktop.
Continue the installation process until you see the interface with the finish button. Then, we launch PowerShell.
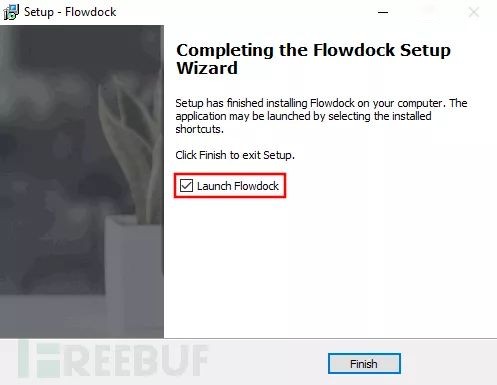
In PowerShell, back up the flowdock.exe program and copy cmd.exe to flowdock.exe. Then, we check the “Launch Flowdock” checkbox to complete the installation.
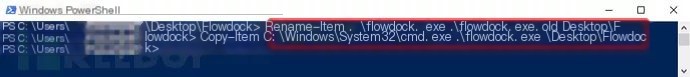
After cmd.exe starts, we type the whoami command and can see that I am currently running with NT Authority\System privileges.
While testing for a client, I used tools like PowerUp for initial probing but found nothing. So, I decided to start manually checking. Based on past experience, the first thing I observe is the currently running processes. Perhaps I can find a zero-day because I have enough time and patience to test these services one by one. After some browsing, a Viewfinity process caught my attention. This is a privilege management software, somewhat different from Software Center, as it can be used for blacklisting, whitelisting, and privilege escalation.
Initially, I didn’t know this software. When browsing the file system, I saw an executable named vf_elevate.exe. After some research, I found the configuration file and tried to figure out how this program works. Below is a screenshot of a fragment of the configuration file.
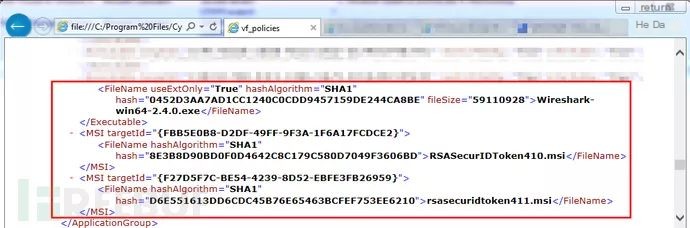
Due to the references to groups and permissions in multiple locations, the XML was difficult to navigate, so I decided to trust the program group names. I downloaded Sysinternals Process Explorer and the version of Wireshark referenced in the configuration file. Here, I did not use the method described in SCCM above. Instead, I followed the usual practice, installed Wireshark, and immediately launched it.
Through Process Explorer, we can see that the process’s Integrity Level is high, indicating it has full administrator privileges, but it is still running as a low-privilege user. This is different from how Software Center behaves. I cannot determine what mechanism Viewfinity uses to elevate privileges (if you know, you can tell me on Twitter).
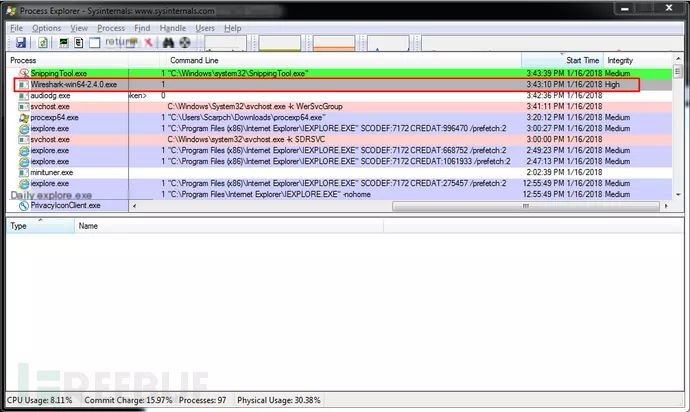
While tinkering with Wireshark, I tried almost all possibilities, such as launching cmd using the open or export dialog. I found that anything launched from these dialogs would run at a medium level and would not inherit Wireshark’s privileges. Fortunately, there is a Lua script console built into Wireshark. I used Lua to launch cmd and saw that its process start level was high, which means I obtained a shell with administrator privileges.
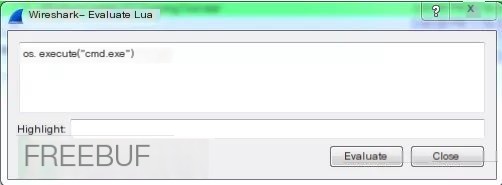
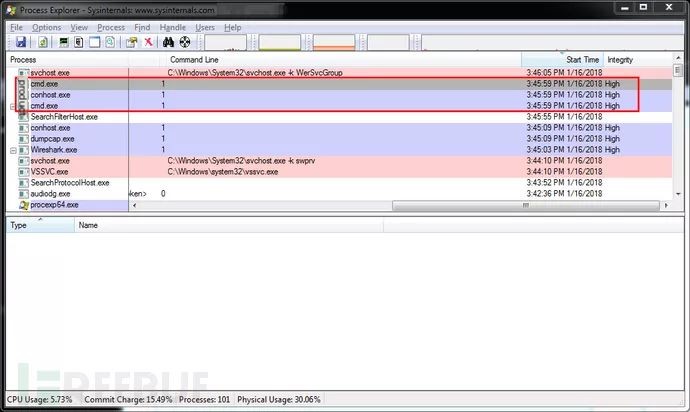
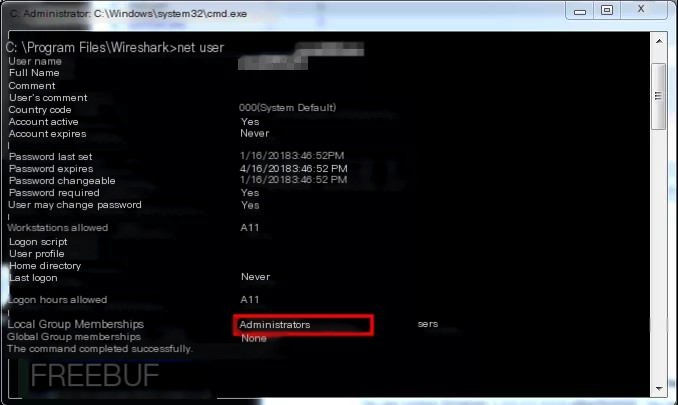
To verify my current running identity, I created a user and added them to the local administrators group.
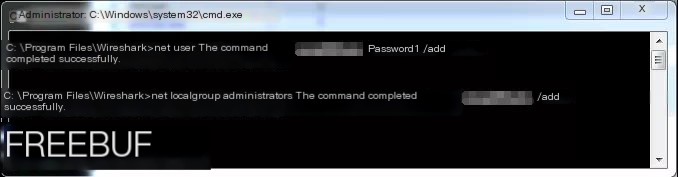
Using the net user command to view the user list, you can see that the newly created user has been successfully added to the administrators group.