FTP brute force attacks are a type of network attack where attackers use automated tools to try a large number of username and password combinations in an attempt to crack the login credentials of an FTP (File Transfer Protocol) server. FTP servers are used for uploading and downloading files, so if attackers successfully crack the login information, they can gain access to the server, potentially leading to data leakage or damage. But how to detect and protect FTP passwords from Brute Force attacks?
Key Characteristics for Protecting FTP Passwords from Brute Force Attacks
- Automation: Attackers use scripts or tools to automatically generate and test a large number of login credentials.
- Repeated Attempts: Attackers continuously try different username and password combinations until they find the correct one.
- Exploitation of Weak Passwords: Often, attackers target common or simple passwords, as these are easier to crack.
Detect and Prevent FTP Passwords from Brute Force Attacks with Sax2
Sax2 IDS is an advanced intrusion detection system designed to monitor and identify abnormal or malicious activities within computer networks and systems. Sax2’s powerful intrusion detection engine can accurately detect FTP brute force attacks and alert them in real-time. The following describes the use of Sax2 to detect FTP brute force attacks in detail. Click on the URL “https://www.ids-sax2.com/wp-content/download/Sax2_Setup(409).exe” to download Sax2 NIDS, and after downloading, double-click on the installer and the installation prompt will make it easy to install Sax2 NIDS
Step 1. Start the Sax2 NIDS
After installing Sax2 NIDS correctly, you will see the following icon on the desktop, double-click it to start Sax2 NIDS
Step 2. Start detecting
After starting Sax2, click the “Start” button on the main interface to start the intrusion detection, please see the figure below:
Step 3. View intrusion events
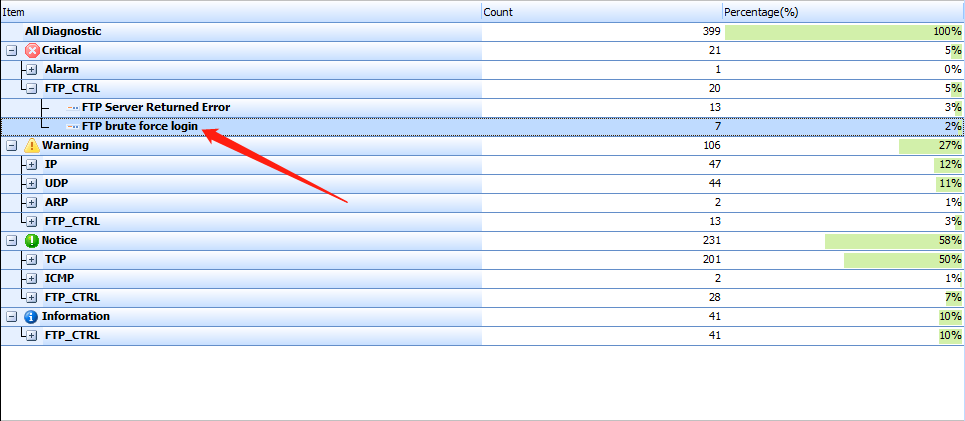
The “Events” viewing window is one of the most important features of Sax2 NIDS and the main place to analyze intrusion events. To view the event, first switch to the Events window. Take a look at the following figure, from which you can see that Sax2 has successfully detected the FTP brute force attacks.
Preventive Measures:
- Use Strong Passwords: Ensure FTP accounts use complex and unique passwords.
- Limit Login Attempts: Set limits on the number of login attempts or use CAPTCHA mechanisms.
- Monitoring and Alerts: Monitor login attempt logs on the FTP server and trigger alerts for unusual activity.
- Use More Secure Protocols: Consider using more secure file transfer protocols, such as SFTP (Secure FTP) or FTPS (FTP Secure).


