Background on Splitting Pcap File by Start and End Time
A question from CSDN asks how to use Tcpdump to split pcap file by specific time periods, such as extracting packets from 1:00 PM to 1:30 PM in a file named “Monday.pcap.” This is a common requirement when using Wireshark or Tcpdump for network packet analysis, especially when troubleshooting issues that require precise time-based filtering. The task may be challenging for those unfamiliar with Tcpdump’s syntax, so here are several methods to achieve this using Tcpdump, Wireshark, Tshark, and Editcap.
Analyzing the Problem of Pcap File Splitting Using Tcpdump
In fact, filtering and analyzing data packets based on the start and end time in Wireshark is a very common requirement, especially when the fault time needs to be accurately located.
However, for the requirements in the question, especially the specific need for tcpdump instructions, I personally understand that it is not very easy to implement compared to Wireshark (I am not very skilled), so I summarize several methods as follows:
- tcpdump + awk method;
- Wireshark method (GUI);
- Tshark method (CLI);
- editcap mode.
Practical Examples for Splitting Pcap File by Time
On Linux, 10 packets were captured, and the time from 17:51:19.308604to 17:51:19.601371is as follows:
[root@7ace test]# tcpdump -r test.pcapng -n
reading from file test.pcapng, link-type EN10MB (Ethernet)
17:51:19.308604 IP 10.0.1.142.ssh > 10.0.25.12.58320: Flags [P.], seq 1816507392:1816507540, ack 1285932546, win 251, length 148
17:51:19.347977 ARP, Request who-has 10.0.1.14 tell 10.0.1.20, length 46
17:51:19.358489 IP 10.0.25.12.58320 > 10.0.1.142.ssh: Flags [.], ack 148, win 2049, length 0
17:51:19.519085 ARP, Request who-has 10.0.3.46 tell 10.0.1.20, length 46
17:51:19.568699 ARP, Request who-has 10.0.1.131 tell 10.0.1.20, length 46
17:51:19.601066 IP 10.0.1.20 > 10.0.1.142: ICMP echo request, id 26625, seq 22363, length 64
17:51:19.601107 IP 10.0.1.142 > 10.0.1.20: ICMP echo reply, id 26625, seq 22363, length 64
17:51:19.601263 IP 10.0.1.20 > 10.0.1.142: ICMP echo request, id 26625, seq 22365, length 64
17:51:19.601272 IP 10.0.1.142 > 10.0.1.20: ICMP echo reply, id 26625, seq 22365, length 64
17:51:19.601371 IP 10.0.1.20 > 10.0.1.142: ICMP echo request, id 26625, seq 22366, length 64
[root@7ace test]#1. tcpdump + awk method
[root@7ace test]# tcpdump -r test.pcapng -n | awk '{if($1>="17:51:19.50" && $1<"17:51:19.6012") print $0}'
reading from file test.pcapng, link-type EN10MB (Ethernet)
17:51:19.519085 ARP, Request who-has 10.0.3.46 tell 10.0.1.20, length 46
17:51:19.568699 ARP, Request who-has 10.0.1.131 tell 10.0.1.20, length 46
17:51:19.601066 IP 10.0.1.20 > 10.0.1.142: ICMP echo request, id 26625, seq 22363, length 64
17:51:19.601107 IP 10.0.1.142 > 10.0.1.20: ICMP echo reply, id 26625, seq 22363, length 64
[root@7ace test]#The 4 packets in the specified time period are filtered through awk processing, but the only problem is that the result is not a pcapng format file.
2. Wireshark method
(frame.time >= "Nov 14, 2021 17:51:19.50" ) && (frame.time <= "Nov 14, 2021 17:51:19.6012")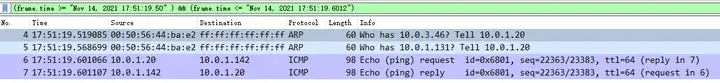
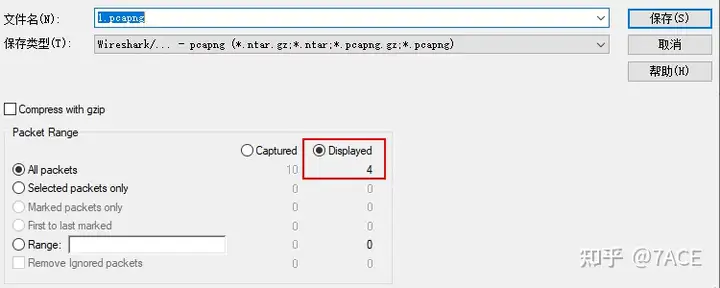
The packets with explicit filtering applied are then saved as a pcapng format file.
3. Tshark method
$ tshark -r test.pcapng -t a -Y "(frame.time >= \"Nov 14, 2021 17:51:19.50\") && (frame.time <= \"Nov 14, 2021 17:51:19.6012\")"
4 17:51:19.519085 0.000000000 VMware_44:ba:e2 Broadcast ARP 60 Who has 10.0.3.46? Tell 10.0.1.20
5 17:51:19.568699 0.049614000 VMware_44:ba:e2 Broadcast ARP 60 Who has 10.0.1.131? Tell 10.0.1.20
6 17:51:19.601066 0.032367000 10.0.1.20 10.0.1.142 ICMP 98 64 Echo (ping) request id=0x6801, seq=22363/23383, ttl=64
7 17:51:19.601107 0.000041000 10.0.1.142 10.0.1.20 ICMP 98 64 Echo (ping) reply id=0x6801, seq=22363/23383, ttl=64 (request in 6)
$ tshark -r test.pcapng -t a -Y "(frame.time >= \"Nov 14, 2021 17:51:19.50\") && (frame.time <= \"Nov 14, 2021 17:51:19.6012\")" -w 1.pcapng
$ tshark -t a -r 1.pcapng
1 17:51:19.519085 0.000000000 VMware_44:ba:e2 Broadcast ARP 60 Who has 10.0.3.46? Tell 10.0.1.20
2 17:51:19.568699 0.049614000 VMware_44:ba:e2 Broadcast ARP 60 Who has 10.0.1.131? Tell 10.0.1.20
3 17:51:19.601066 0.032367000 10.0.1.20 10.0.1.142 ICMP 98 64 Echo (ping) request id=0x6801, seq=22363/23383, ttl=64
4 17:51:19.601107 0.000041000 10.0.1.142 10.0.1.20 ICMP 98 64 Echo (ping) reply id=0x6801, seq=22363/23383, ttl=64 (request in 3)4. Editcap method
$ editcap -A "2021-11-14 17:51:19.50" -B "2021-11-14 17:51:19.6012" test.pcapng 1.pcapng
$ tshark -t a -r 1.pcapng
1 17:51:19.519085 0.000000000 VMware_44:ba:e2 Broadcast ARP 60 Who has 10.0.3.46? Tell 10.0.1.20
2 17:51:19.568699 0.049614000 VMware_44:ba:e2 Broadcast ARP 60 Who has 10.0.1.131? Tell 10.0.1.20
3 17:51:19.601066 0.032367000 10.0.1.20 10.0.1.142 ICMP 98 64 Echo (ping) request id=0x6801, seq=22363/23383, ttl=64
4 17:51:19.601107 0.000041000 10.0.1.142 10.0.1.20 ICMP 98 64 Echo (ping) reply id=0x6801, seq=22363/23383, ttl=64 (request in 3)Summary of Tcpdump and Wireshark Methods for Pcap File Splitting
For tcpdump or wireshark, you can flexibly choose to use it according to different scenarios and needs. The differences between tcpdump and wireshark are summarized as follows:
- Tcpdump and wireshark are both network packet capture and analysis tools. The former is mainly used in Linux, while the latter is mainly used in Windows. (Note: Although each has versions for different operating systems)
- Tcpdump filtering is mainly capture filtering, while wireshark filtering is divided into capture filtering and display filtering. Display filtering is applied to data packet analysis and has a very rich syntax.
- Tcpdump is extremely powerful when used in conjunction with tools such as grep, sed, and awk in Linux;
- Compared with tcpdump, wireshark has more comprehensive analysis and statistical functions. At the same time, the command line versions of tshark and wireshark can also achieve good analysis results.



