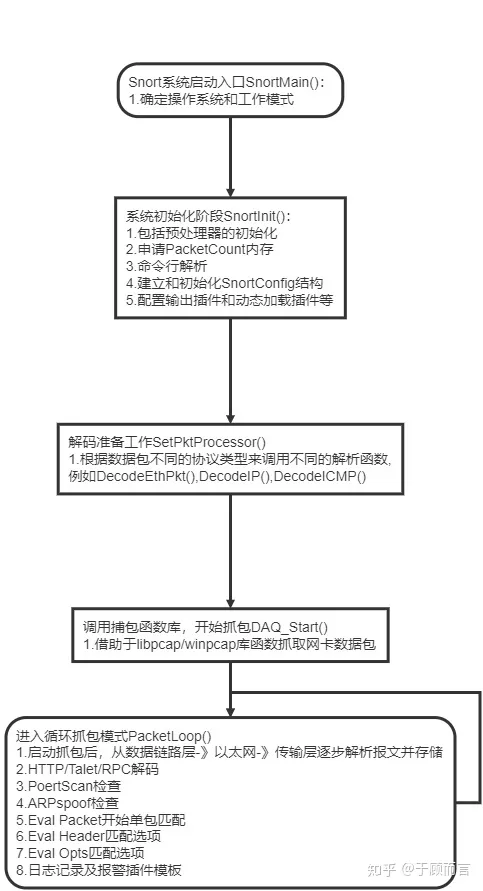
Code Flow Chart for Ubuntu 14.04.5
Building Environment: Ubuntu 14.04.5
The content referencing Ubuntu 14.04.5 can be found through this [link](https://link.zhihu.com/?target=http%3A%2F%2Fold-releases.ubuntu.com%2Freleases%2F14.04.5%2F).
- Ubuntu Configuration
Code Language: JavaScriptCopy
sudo apt-get update
sudo apt-get dist-upgrade -y
sudo apt-get install -y openssh-server
sudo reboot2. Install Snort Dependencies
Code Language: JavaScriptCopy
sudo apt-get install -y build-essential
sudo apt-get install -y libpcap-dev libpcre3-dev libdumbnet-dev
sudo apt-get install -y bison flex
mkdir ~/snort_src
cd ~/snort_src
wget http://ftp.gnu.org/gnu/automake/automake-1.15.tar.gz
tar -xvzf automake-1.15
cd automake-1.15
./configure --docdir=/usr/share/doc/automake-1.15
make
sudo make install
wget http://ftp.gnu.org/gnu/autoconf/autoconf-2.68.tar.gz
tar xzf autoconf-2.68.tar.gz
cd autoconf-2.68
./configure
make
sudo make install
sudo wget http://luajit.org/download/LuaJIT-2.0.5.tar.gz
sudo tar -zxvf LuaJIT-2.0.5.tar.gz
cd LuaJIT-2.0.5/
make
sudo make install3. Install DAQ
Code Language: JavaScriptCopy
cd ~/snort_src
wget https://snort.org/downloads/snort/daq-2.0.7.tar.gz
tar -xvzf daq-2.0.7.tar.gz
cd daq-2.0.7
./configure
make
sudo make install
sudo apt-get install -y autoconf libtool pkg-config
cd ~/snort_src
wget https://github.com/nghttp2/nghttp2/releases/download/v1.17.0/nghttp2-1.17.0.tar.gz
tar -xzvf nghttp2-1.17.0.tar.gz
cd nghttp2-1.17.0
autoreconf -i --force
automake
autoconf
./configure --enable-lib-only
make
sudo make install4. Install Snort
Code Language: JavaScriptCopy
cd ~/snort_src
wget https://snort.org/downloads/snort/snort-2.9.15.1.tar.gz
tar -xvzf snort-2.9.15.1.tar.gz
cd snort-2.9.15.1
./configure --enable-sourcefire
make
sudo make install5. Install Snort Rules
Code Language: JavaScriptCopy
# First create a snort configuration (and rules) directory
mkdir -p /etc/snort/rules
# Create directories required for running
mkdir /usr/local/lib/snort_dynamicrules
# First copy the default configuration files from etc in the decompressed 2.3 to the snort configuration directory
cp etc/*.conf* /etc/snort
cp etc/*.map /etc/snort
# Download community rules and decompress them into the rules directory
wget https://www.snort.org/downloads/community/community-rules.tar.gz
tar -zxf community-rules.tar.gz -C /etc/snort/rules
# Comment out all default rule files that need to be loaded
sudo sed -i 's/include \$RULE\_PATH/#include \$RULE\_PATH/' /etc/snort/snort.conf
# Enable community rule files
echo '' >> /etc/snort/snort.conf
echo '# enable community rule' >> /etc/snort/snort.conf
echo 'include $RULE_PATH/community-rules/community.rules' >> /etc/snort/snort.conf
# Reset the variable values in snort.conf
sed -i 's/var RULE_PATH ..\/rules/var RULE_PATH .\/rules/' /etc/snort/snort.conf
sed -i 's/var WHITE_LIST_PATH ..\/rules/var WHITE_LIST_PATH .\/rules/' /etc/snort/snort.conf
sed -i 's/var BLACK_LIST_PATH ..\/rules/var BLACK_LIST_PATH .\/rules/' /etc/snort/snort.conf
# Create a default whitelist file
touch /etc/snort/rules/white_list.rules
# Create a default blacklist file
touch /etc/snort/rules/black_list.rules
# Create a default custom rules file, which is essentially useless since other includes only include community rules, just for formality
touch /etc/snort/rules/local.rules
# Test if the configuration file is correct
snort -T -c /etc/snort/snort.conf6. After installation, briefly try the three modes
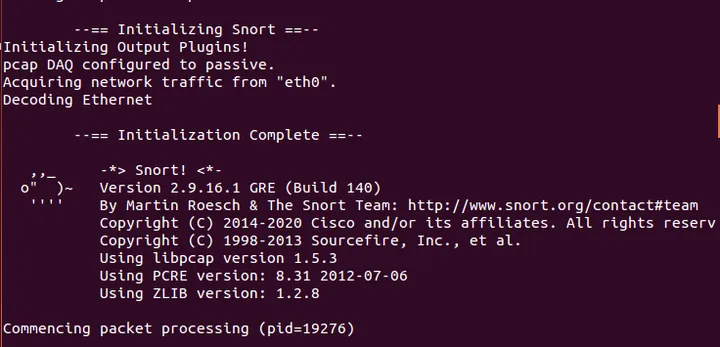
snort -v
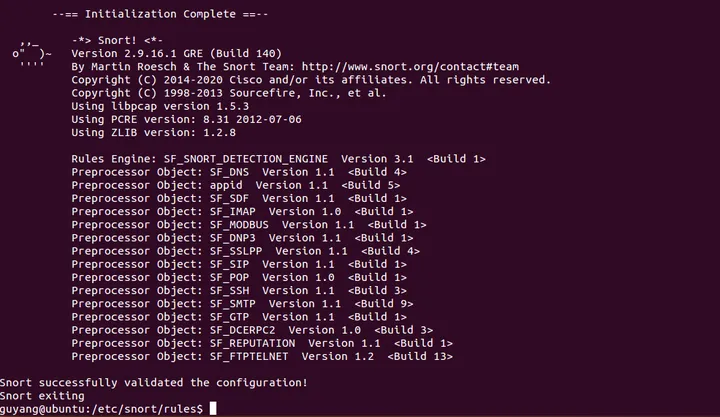
rule config
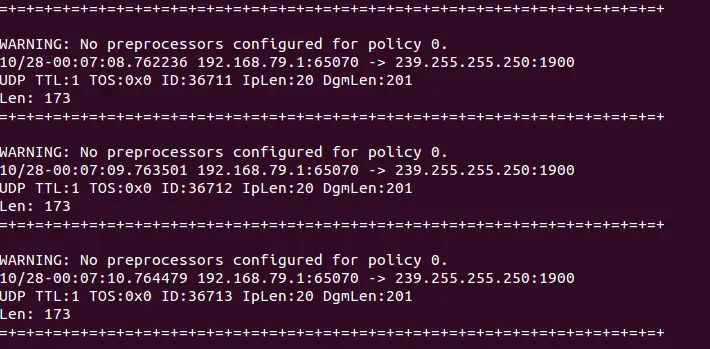
detect mode
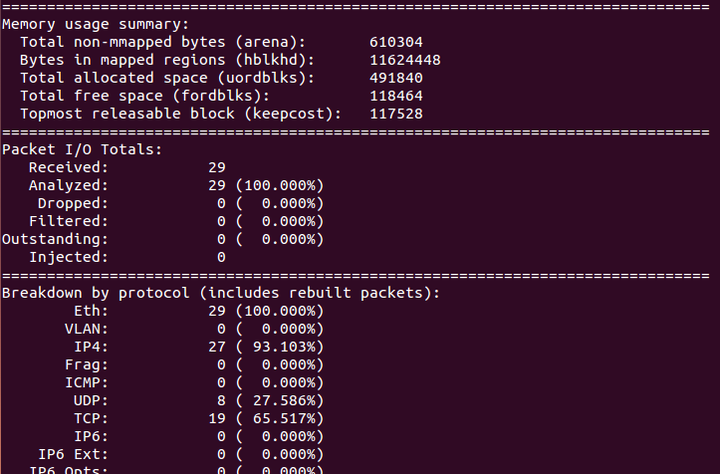
summary
Features Use Report
- Sniffer (snort -dev)
The so-called sniffer mode is where snort reads packets from the network and displays them on your console. The snort -vd command outputs header information while showing the packet data:
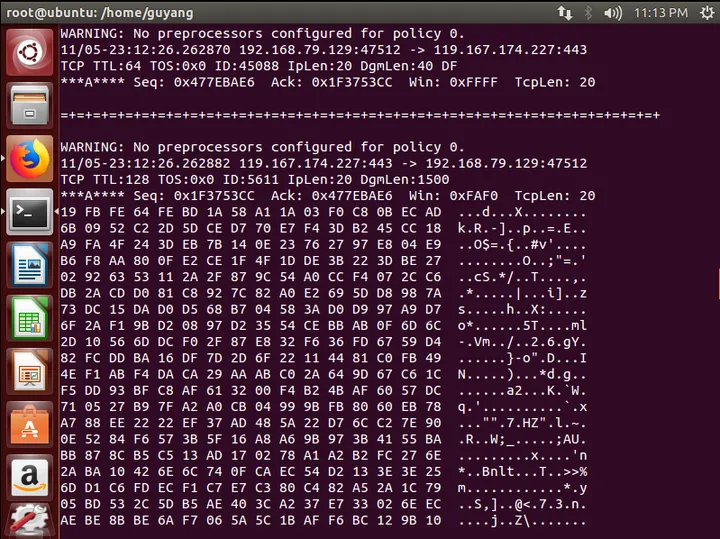
After visiting http://www.baidu.com, TCP/IP data probing information is as follows:
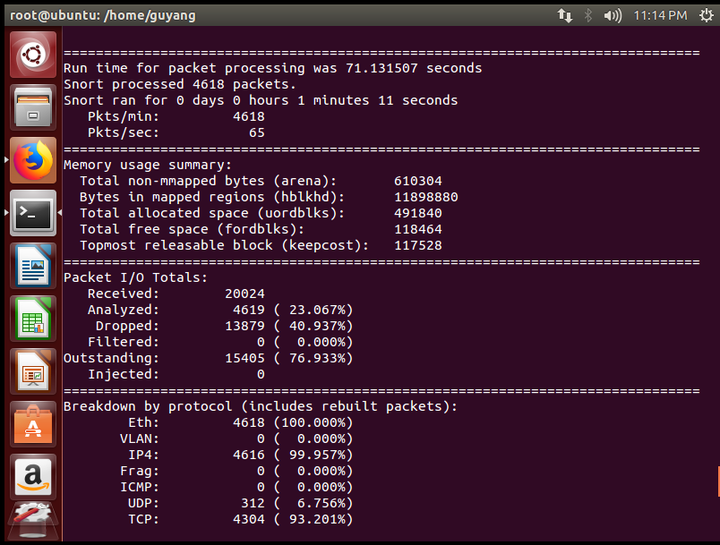
After exiting detection mode, snort will provide a summary of the probe information, including runtime, throughput, memory usage, data I/O, and protocol classification statistics.
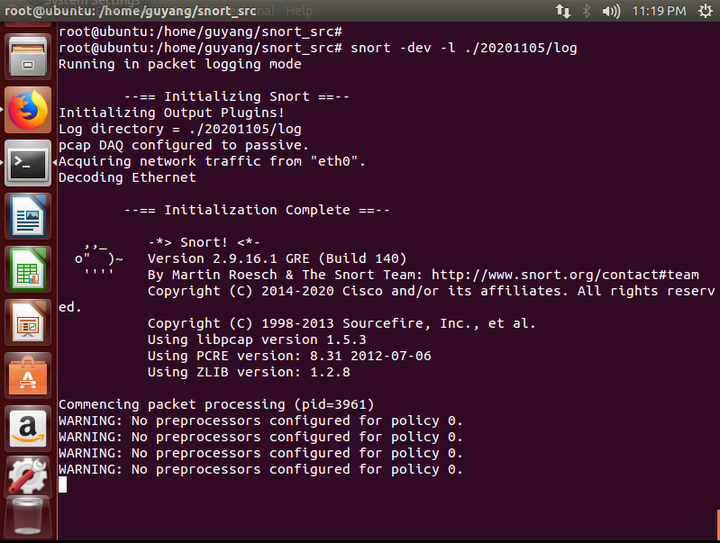
2. Packet Logger (snort -l)
If you want to record all packets to disk, you need to specify a log directory; snort will automatically log the packets. The command uses detection + recording method: ./snort -dev -l ./20201105/log
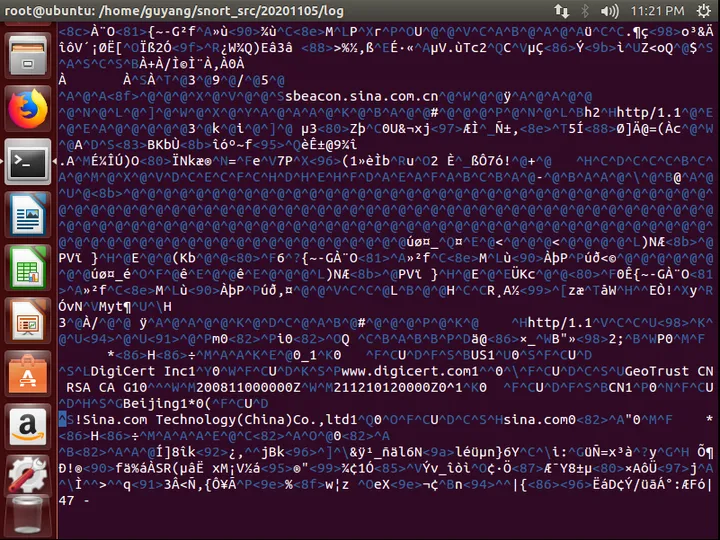
After visiting http://www.sina.com, after closing the sniffer mode, the log file will record all packets during the visit to Sina in snort.og.1604647136. When we open it with vi, we can see the host in HTTP messages when visiting Sina.
On the other hand, if you want to record packets of specific port numbers or protocol features, you can define them in the rules file: log udp any any -> 192.168.1.0/24 1:1024
3. Intrusion Detection (snort -c)
Network intrusion detection mode has five actions: pass, log, alert, dynamic, and activate, which are configurable. We can let Snort analyze network data flows to match some user-defined rules and take certain actions based on the detection results.
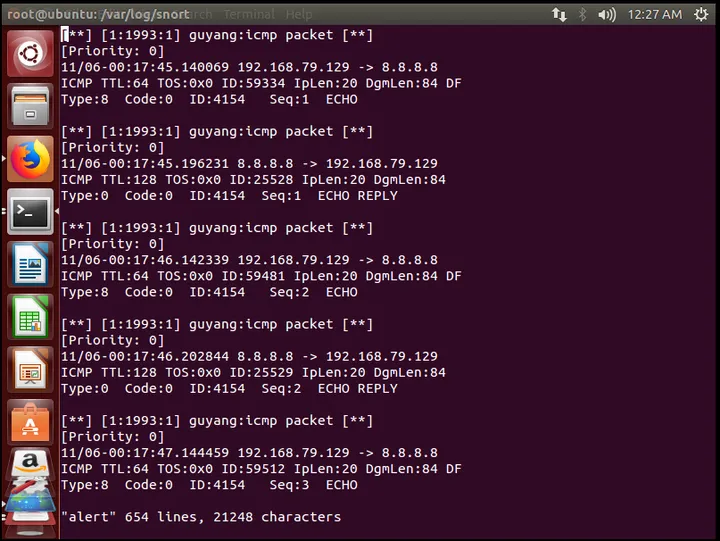
First configure some rules ( snort rule syntax ), create a new local.rules. Here, try the simplest example, when any ICMP protocol packet is found, it issues an alert and logs it, content displayed as guyang: icmp packet; then, the syntax configuration is as follows: alert icmp any any -> any any (msg: “guyang:icmp packet”; sid:1993; rev:1;)
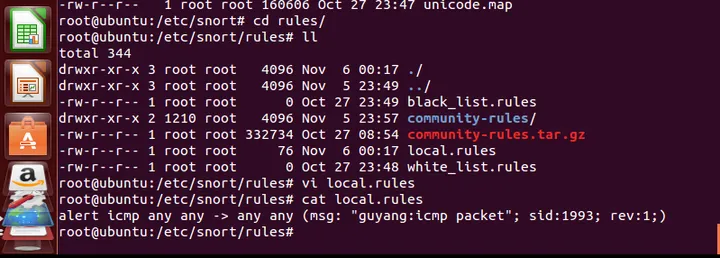
After configuring the rules, start NIDS mode: snort -c local.rules
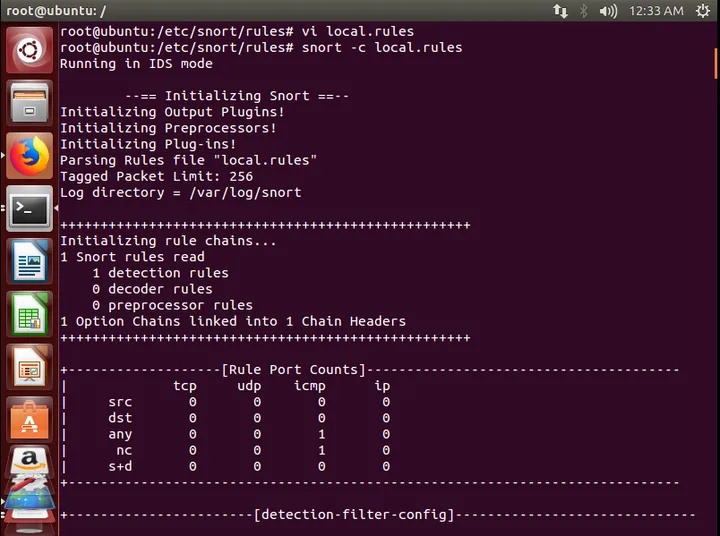
Open another terminal and ping 8.8.8.8:
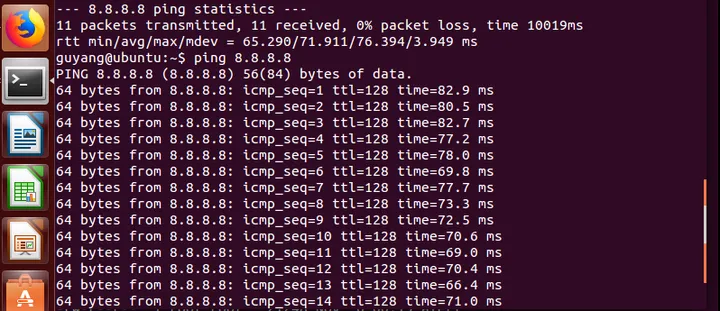
Alerts are continuously displayed on the screen, and when the terminal is closed, a monitoring report is visible:
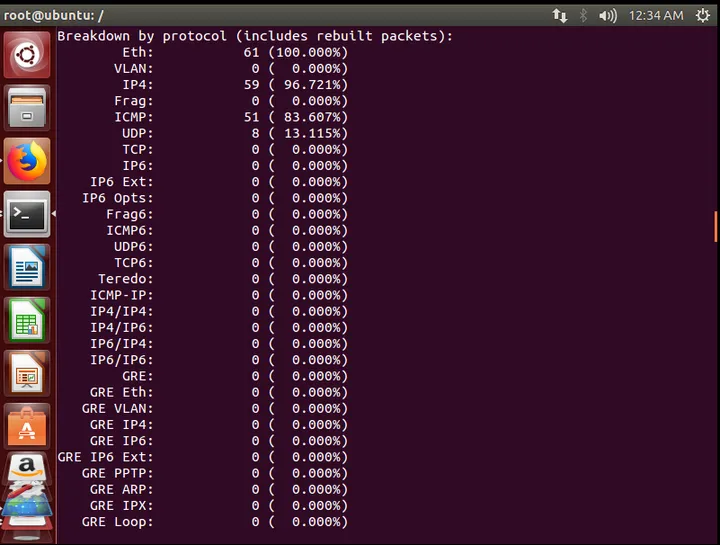
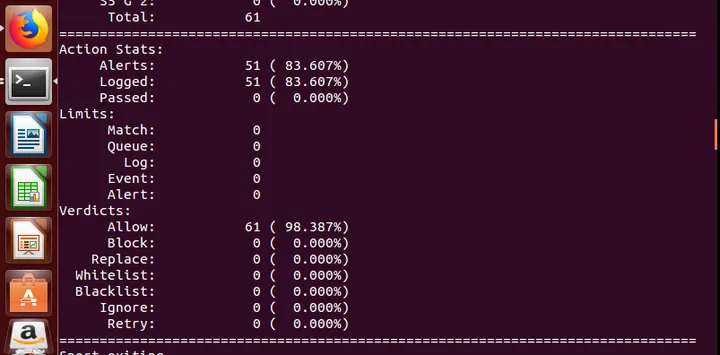
Because it is in alert mode, the specifics of the alert packets will be recorded in /var/log/snort/alert:
After trying the three modes, it is noticeably apparent that Snort IDS is highly user-friendly, with a friendly interface, supports a wide range of protocols, and rule configuration is very flexible and simple. You just need to focus on 4 elements: who, where, what, how (action).


