Internet Control Message Protocol (ICMP) is the utility protocol of TCP/IP, responsible for providing information regarding the availability of devices, services, or routes on a TCP/IP network. Most network troubleshooting techniques and tools center around common ICMP message types. ICMP is defined in RFC 792.
The ICMP Header
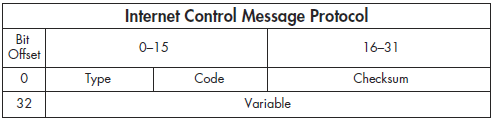
ICMP is part of IP, and it relies on IP to transmit its messages. ICMP contains a relatively small header that changes depending on its purpose. As shown in Figure 6-29, the ICMP header contains the following fields:
Type The type or classification of the ICMP message, based on the RFC specification
Code The subclassification of the ICMP message, based on the RFC specification
Checksum Used to ensure that the contents of the ICMP header and data are intact upon arrival
Variable A portion that depends on the Type and Code fields
Figure 6-29: The ICMP header
ICMP Types and Messages
As noted, the structure of an ICMP packet depends on its purpose, as defined by the values in the Type and Code fields.
You might consider the ICMP Type field as the packet’s classification and the Code field as its subclass. For example, a Type field value of 3 indicates “Destination Unreachable.” While this information alone might not be enough to troubleshoot a problem, if that packet were to also specify a Code field value of 3, indicating “Port Unreachable,” you could conclude that there is an issue with the port with which you are attempting to communicate.
TIPS For a full list of available ICMP types and codes, see http://www.iana.org/assignments/icmp-parameters.
Echo Requests and Responses
ICMP’s biggest claim to fame is thanks to the ping utility. Ping is used to test for connectivity to a device. Most information technology (IT) professionals are familiar with ping.
To use ping, enter ping <ip address> at the command prompt, replacing <ip address> with the actual IP address of a device on your network. If the target device is turned on, your computer has a communication route to it, and there is no firewall blocking that communication, you should see replies to your ping command.
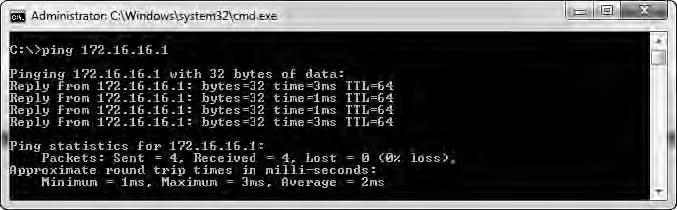
The example in Figure 6-30 shows four successful replies that display their size, RTT, and TTL used. The Windows utility also provides a summary detailing how many packets were sent, received, and lost. If communication fails, you should see a message telling you why.
Figure 6-30: The ping command being used to test connectivity
Basically, the ping command sends one packet at a time to a device and listens for a reply to determine if there is connectivity to that device, as shown in Figure 6-31.
Figure 6-31: The ping command involves only two steps.
TIPS Although ping has long been the bread and butter of IT, its results can be a bit deceiving as host-based firewalls are deployed. Many of today’s firewalls limit the ability of a device to respond to ICMP packets. This is great for security, because potential attackers using ping to determine if a host is accessible might be deterred, but troubleshooting is also made more difficult—it can be frustrating to ping a device to test for connectivity and not receive a reply when you know you can communicate with that device.
The ping utility in action is a great example of simple ICMP communication. The packets in the file icmp_echo.pcap demonstrate what happens when you run ping.
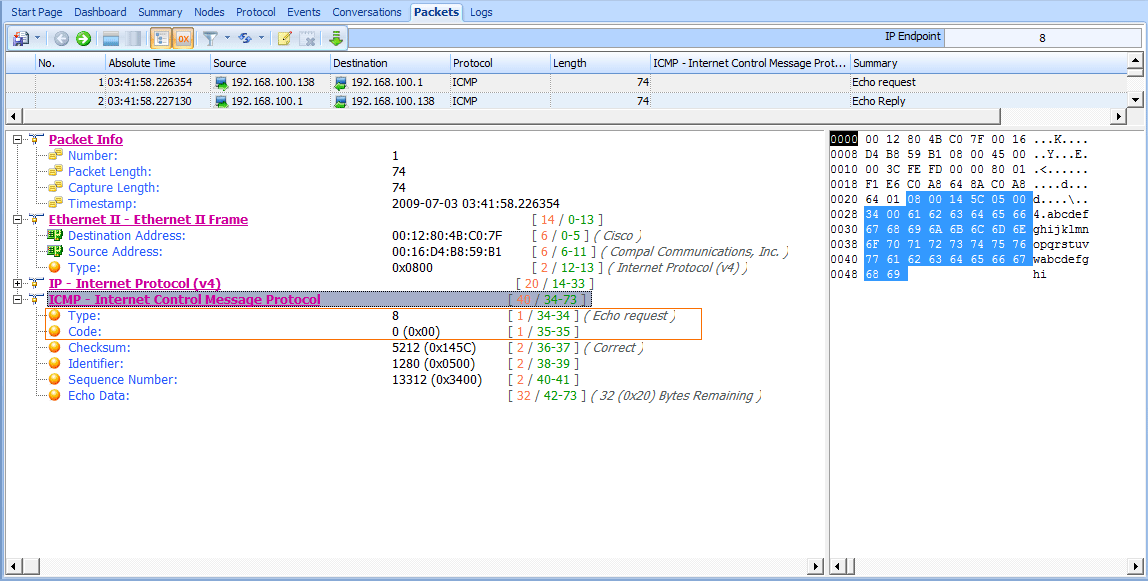
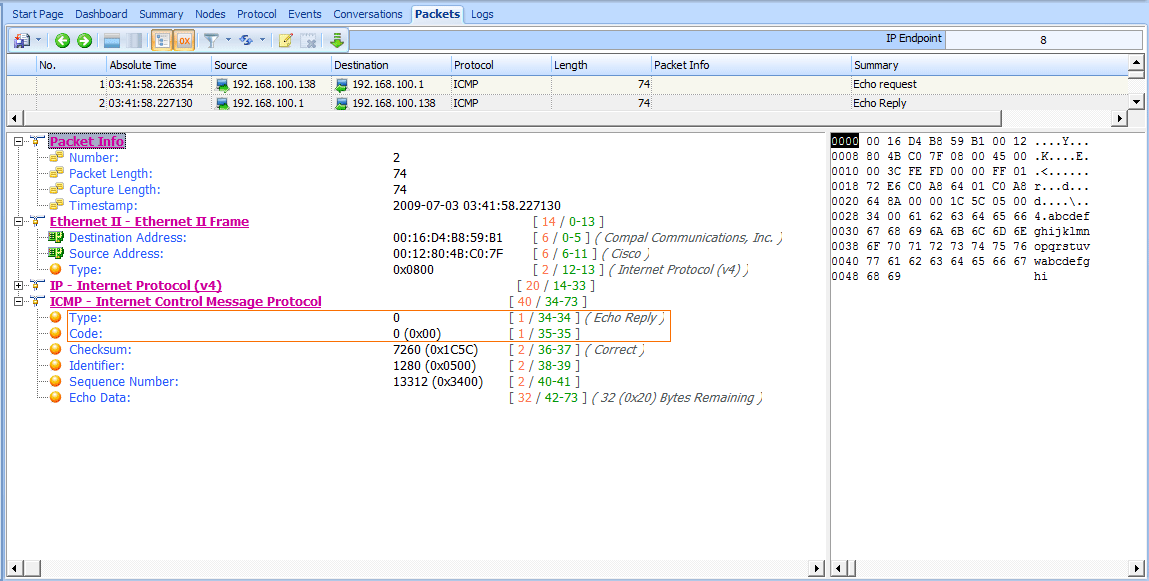
The first packet (see Figure 6-32) shows that host 192.168.100.138 is sending a packet to 192.168.100.1 . When you expand the ICMP portion of this packet, you can determine the ICMP packet type by looking at the Type and Code fields. In this case, the packet is type 8 , code 0 , indicating an echo request. (Wireshark should tell you what the type/code being displayed actually is.) This echo (ping) request is the first half of the equation. It is a simple ICMP packet, sent using IP, that contains a small amount of data. Along with the type and code designations and the checksum, we
also have a sequence number that is used to pair requests with replies, and a random text string in the variable portion of the ICMP packet.
TIPS The terms echo and ping are often used interchangeably, but just remember that ping is actually the name of a tool. The ping tool is used to send ICMP echo request packets.
Figure 6-32: The ICMP echo request packet
The second packet in this sequence is the reply to our request (see Figure 6-33). The ICMP portion of the packet is type 0 , code 0 , indicating that this is an echo reply. Because the sequence number in the second packet matches that of the first , we know that this echo reply matches the echo request in the previous packet. This reply packet also contains the same 32-byte string of data that was transmitted with the initial request . Once this second packet has been received by 192.168.100.138, ping will report success (see Figure 6-30, shown earlier).
Figure 6-33: The ICMP echo reply packet
Note that you can use variations of ping to increase the size of the data padding, which forces packets to be fragmented for various types of network troubleshooting. This may be required when you’re troubleshooting networks that require a smaller fragment size.
TIPS The random text used in an ICMP echo request can be of great interest to a potential attacker. Attackers can use the information in this padding to profile the operating system used on a device. Additionally, attackers can place small bits of data in this field as a method of covert communication.
Traceroute
The traceroute utility is used to identify the path from one device to another. On a simple network, a path may go through only a single router or no router at all. On a complex network, however, a packet may need to go through dozens of routers to reach its final destination, which is why it’s crucial to be able to trace the exact path a packet takes from one destination to another in order to troubleshoot communication.
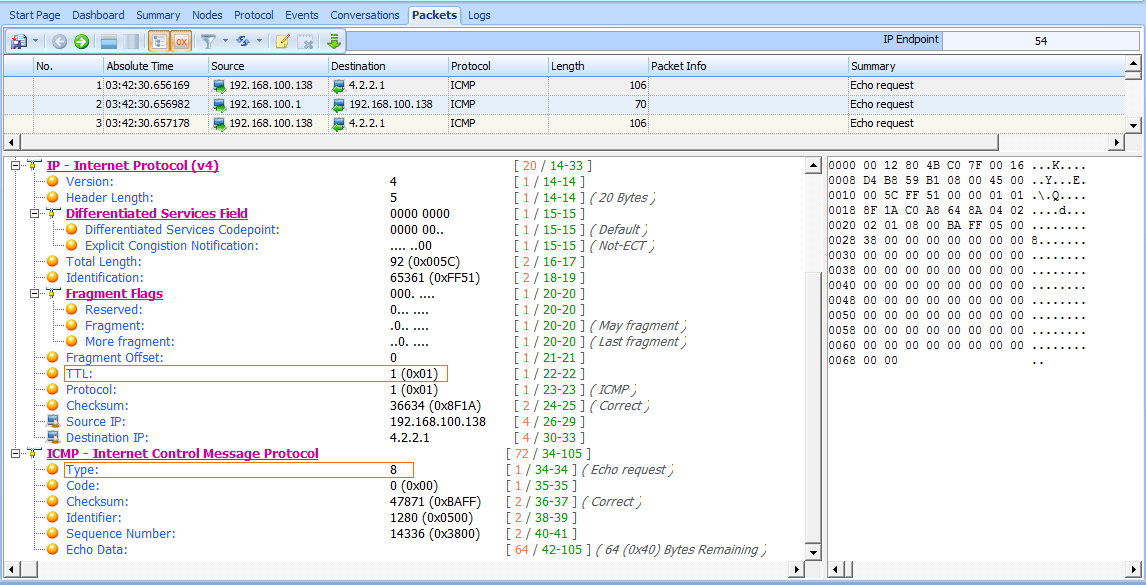
By using ICMP (with a little help from IP), traceroute can map the path packets take. For example, the first packet in the file icmp_traceroute.pcap is pretty similar to the echo request we looked at in the previous section (see Figure 6-34).
Figure 6-34: An ICMP echo request packet with a TLL value of 1
At first glance, this packet appears to be a simple echo request from 192.168.100.138 to 4.2.2.1 , and everything in the ICMP portion of the packet is identical to the formatting of an echo request packet. However, when you expand the IP header of this packet, you’ll notice one odd value: The packet’s TTL value is set to 1 , which means that the packet will
be dropped at the first router that it hits. Because the destination 4.2.2.1 address is an Internet address, we know that there must be at least one router between our source and destination devices, so there is no way this packet will reach its destination. That’s good for us, because traceroute relies on the fact that this packet will make it to only the first router it traverses.
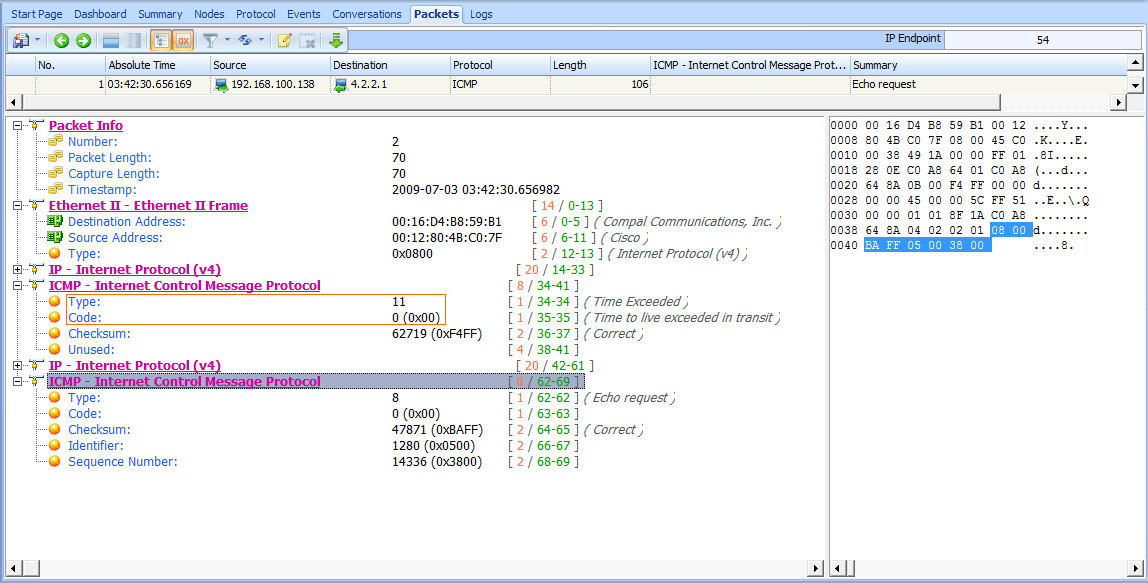
The second packet is, as expected, a reply from the first router we reached along the path to our destination (see Figure 6-35). This packet reached this device at 192.168.100.1, its TTL was decremented to 0, and the packet could not be transmitted further, so the router replied with an ICMP response. This packet’s type 11 , code 0 tells us that the destination was unreachable because the packet’s TTL was exceeded during transit.
Figure 6-35: An ICMP response from the first router along the path
This ICMP packet is sometimes called a double-headed packet, because the tail end of its ICMP portion contains a copy of the IP header and ICMP data that was sent in the original echo request. This information can prove to be very useful for troubleshooting.
This process of sending packets with incremented TTL values occurs two more times before we get to packet 7. Here, you see the same thing you saw in the first packet, except that this time, the TTL value in the IP header is set to 2, which ensures the packet will make it to the second hop router before it is dropped. As expected, we receive a reply from the next hop router, 12.180.241.1, with the same ICMP destination unreachable and TTL exceeded messages. This process continues with the TTL value increasing by one until the destination 4.2.2.1 is reached.
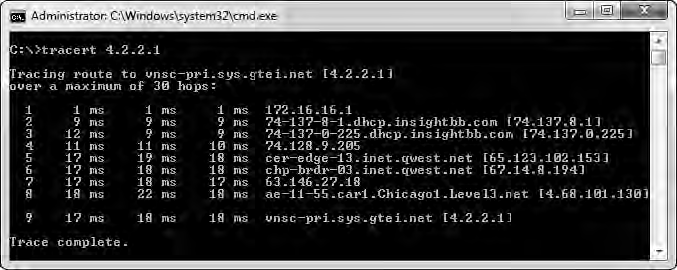
To sum up, this traceroute process has communicated with each router along the path, building a map of the route to the destination. This map is shown in Figure 6-36.
TIPS The discussion here on traceroute is generally Windows-focused because it uses ICMP exclusively. The traceroute utility on Linux is a bit more versatile and can utilize other protocols in order to perform route path tracing.
Figure 6-36: A sample output from the traceroute utility
As you’ll see throughout this book, ICMP has many different functions. We’ll use ICMP frequently as we analyze more scenarios.
This chapter has introduced you to a few of the most important protocols you will examine in the process of packet analysis. IP, TCP, UDP, and ICMP are at the foundation of all network communications, and they are critical to just about every daily task you perform. In the next chapter, we will look at a grouping of common application-layer protocols.