For many readers, Kubernetes packet capture is a routine task that can be performed either within the Pod or on the Node. After capturing, the files can easily be viewed on-site or copied for analysis in Wireshark. The Ksniff tool is designed to streamline these routine steps, enabling a series of operations to be completed with a straightforward kubectl plugin command.
Ksniff has some interesting features:
With Krew, Ksniff can be installed very conveniently:
Deploy a simple httpbin service:
Once the service is running, start a client:
You can then use the plugin to monitor the Pod, for example:
It’s easy to see how ksniff roughly uploads a tcpdump to the captured Pod for direct execution. After the command executes, Wireshark is immediately started for monitoring.
Next, let’s generate some traffic on the monitored Pod from the sleep Pod.
You will see the corresponding packets in Wireshark:
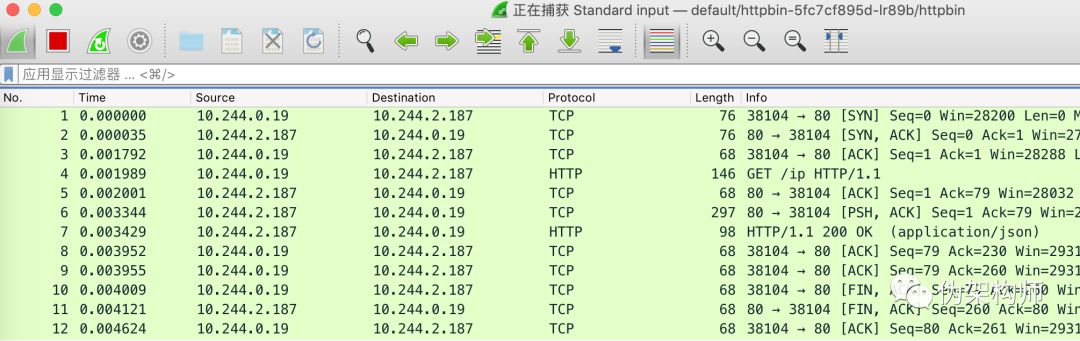
Check the processes of the monitored Pod:
It’s easy to see that a few extra processes have appeared.
Ksniff also provides a parameter for monitoring unprivileged Pods. With this parameter, it queries the node where the target Pod resides, then utilizes node affinity on that node to create a privileged Pod sharing the node’s network, and subsequently monitors the traffic on this new Pod.
You can see that ksniff created a new Pod and successfully started Wireshark. Upon execution again:
You can see new packets appearing in Wireshark.



