Hi everyone, today I’m here to share some network knowledge, including information about the VMware Network Adapter.
Using Wireshark to capture packets on the VMware Network Adapter VMnet8 to analyze traffic on the virtual machine.
The TCP Three-Way Handshake with VMware Network Adapter
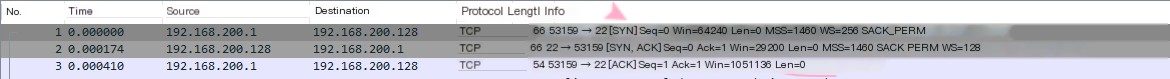
As shown in the image, opening an SSH tool to log into the virtual machine requires establishing this standard TCP connection, a three-way handshake.
Client — > Server: SYN Seq=0
Client < — Server: SYN+ACK Seq=0 ACK=1
Client — > Server: ACK Seq=1 ACK=1
There’s a classic interview question: why is it 3 times, not 2 or 4?
Because TCP is a full-duplex protocol, each party can independently send data to the other. Both parties need to send a SYN request and ACK once to establish a connection.
It begins with a SYN, followed by a SYN+ACK, and concludes with an ACK. Just three times.
During this process, the Linux kernel maintains two queues: the established connections queue and the half-open connections queue.
View the established connections queue:
Language: Javascript Copy
netstat -ant | grep ESTABLISHED />
/>
View the half-open connections queue:
Language: Javascript Copy
cat /proc/net/tcp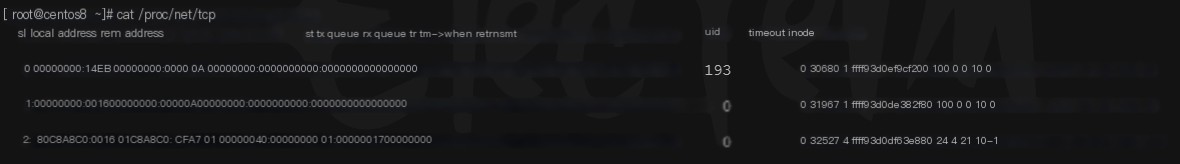
I copied down the third packet 👇
Language: Javascript Copy
1 0.000000 192.168.200.1 192.168.200.128 TCP 66 53159 → 22 [SYN] Seq=0 Win=64240 Len=0 MSS=1460 WS=256 SACK_PERM2 0.000174 192.168.200.128 192.168.200.1 TCP 66 22 → 53159 [SYN, ACK] Seq=0 Ack=1 Win=29200 Len=0 MSS=1460 SACK_PERM WS=1283 0.000410 192.168.200.1 192.168.200.128 TCP 54 53159 → 22 [ACK] Seq=1 Ack=1 Win=1051136 Len=0You can see in number 3 there Win=1051136
I was a bit puzzled here, isn’t the TCP window size 16 bits (65536)?
Later, I found out it’s related to WS (window_scaling) window scaling.
Language: Javascript Copy
# Enable, returns 1sudo sysctl net.ipv4.tcp_window_scalingIt is part of the TCP_OPTION content, an extension to the TCP protocol that allows window size expansion to larger values, overcoming the performance limitations of the original TCP window size design.
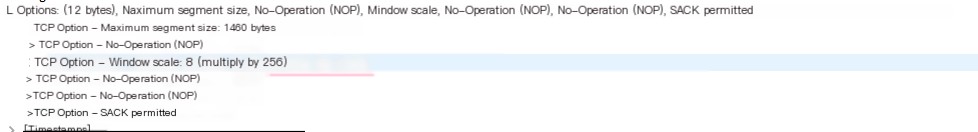
The part of RFC 7323 briefly describes the TCP Window Scaling option.https://tools.ietf.org/html/rfc1323#page-8
There’s also SACK (Selective Acknowledgment), a part of the retransmission mechanism.
A simple example 👇
Sender: Send A, B, C, D
Receiver: Acknowledges A, D
Sender: Retransmit B, C
The TCP Four-Way Teardown
Here, open a new SSH window, then close it to capture the TCP FIN packet.
 Language: Javascript Copy
Language: Javascript Copy
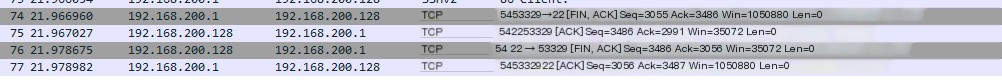
74 21.966960 192.168.200.1 192.168.200.128 TCP 54 53329 → 22 [FIN, ACK] Seq=3055 Ack=3486 Win=1050880 Len=075 21.967027 192.168.200.128 192.168.200.1 TCP 54 22 → 53329 [ACK] Seq=3486 Ack=2991 Win=35072 Len=076 21.978675 192.168.200.128 192.168.200.1 TCP 54 22 → 53329 [FIN, ACK] Seq=3486 Ack=3056 Win=35072 Len=077 21.978982 192.168.200.1 192.168.200.128 TCP 54 53329 → 22 [ACK] Seq=3056 Ack=3487 Win=1050880 Len=0It’s also very straightforward here👇
Client — > Server: FIN + ACK Seq=3055 Ack=3486
Client < — Server: ACK Seq=3486 ACK=2991 (data not fully received, ACK only up to 2991)
Client < — Server: FIN + ACK Seq=3486 Ack=3056
Client — > Server: ACK Seq=3056 Ack=3487
Every FIN signal requires an ACK response, twice each way, totaling four times.
FIN indicates that I’ve finished sending and am waiting to close, but the other side is still busy, so they can only ACK to acknowledge.
ARP Protocol
Address Resolution Protocol (request).

Its triggering scenarios are as follows:
- When the IP address is known but not the MAC address, it initiates an ARP protocol (cache table not found).
- Local ARP cache table expired
- ARP request acknowledgment lost
Language: Javascript Copy
112 74.131366 VMware_c0:00:08 Broadcast ARP 42 Who has 192.168.200.2? Tell 192.168.200.1113 74.877192 VMware_c0:00:08 Broadcast ARP 42 Who has 192.168.200.2? Tell 192.168.200.1This seems so personalized, haha, “Who has?”
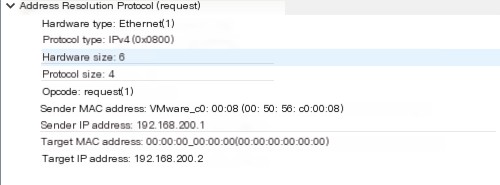
The 00:00:00:00:00:00 target MAC address is typically used for broadcasting messages or when a target MAC address is unknown.
Over!
Conclusion
This concludes the article, thank you for reading. If there’s anything incorrect, please kindly help correct it! Thank you~😋
If you liked it, don’t forget to like and follow~😋 Have a wonderful day! 😝



