First Move: Packet Filtering
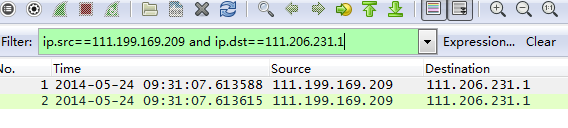
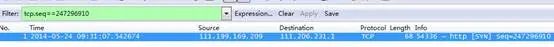
TCP packets have sequence numbers. When troubleshooting, we can use this field to order the TCP packets to identify which packet was lost.
SEQ can be either a relative sequence number or an absolute sequence number. It is displayed as 0 1 by default, which is inconvenient. Please refer to the third move to modify it to an absolute sequence number.
Second Move: Modify the Display Format of Packet Time
Some users capture packets with incorrect time display formats, making it difficult to identify the time issue occurred. You can modify it through View—time display format.
Before modification:
After modification:

Third Move: Confirm Packet Order
In some special situations, the client’s source and destination IP, source and destination port, and source MAC are the same, causing some businesses to not connect. Switch flow statistics won’t help, as shown in the following network architecture diagram. The arrows indicate data flow direction, and related policies on the switch prevent the PC from directly accessing the SER.
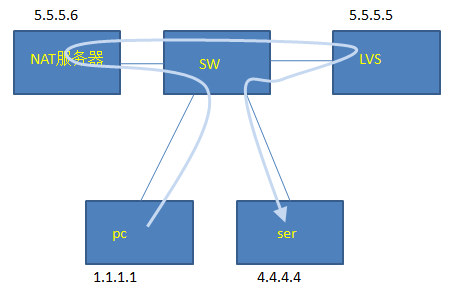
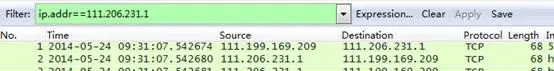
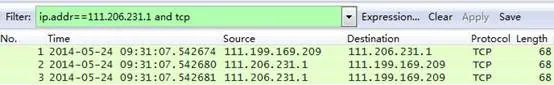
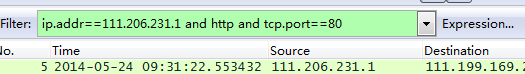
When troubleshooting this issue, we need to understand the client’s business model and protocol used. Coincidentally, this business is WEB, so we know the TCP packet field has sequence numbers, which can be used as a unique identifier for analysis, or for sorting by sequence number.
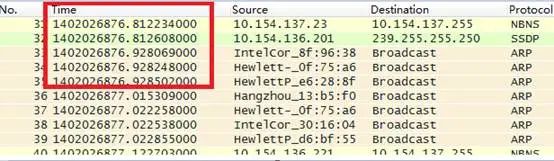
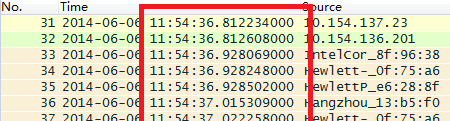
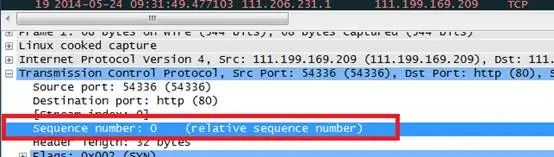
Relative sequence numbers like 0 and 1 are generally captured, making analysis difficult. We modify these to absolute sequence numbers as follows:
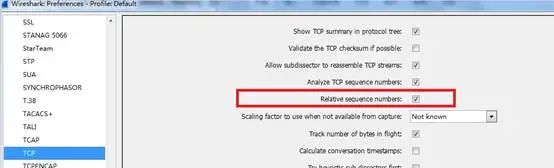
Edit—–preference——protocols—-tcp—relative sequence numbers
Modify parameters as follows:
I take TCP protocol as an example

Remove this TCP option
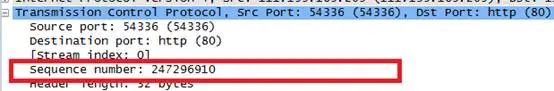
Final effect:
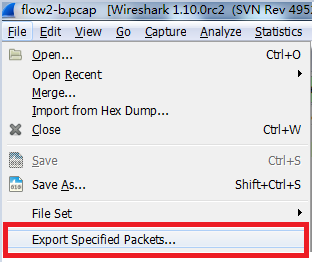
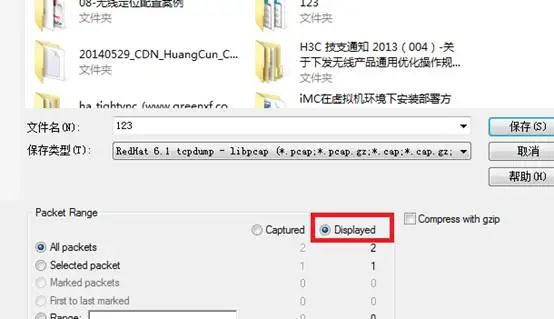
Fourth Move: Save Filtered Packets
When capturing packets, the data volume is large, but only a few are useful. After filtering the data by conditions, you can save the filtered packets separately for future viewing.
Fifth Move: Packet Counting and Statistics
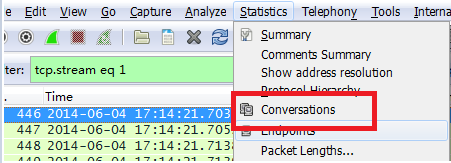
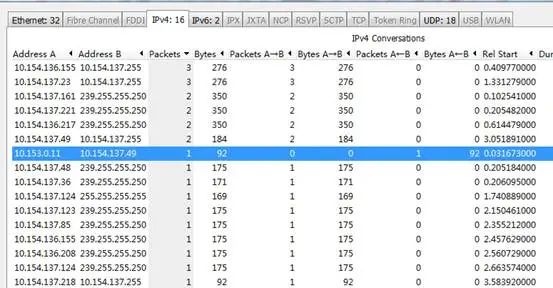
If there is a flood attack in the network, we can use packet capturing to count the number of packets and find out which packets are more numerous for analysis.
Statistics——conversations
Sixth Move: Packet Decoding
IPS sends attack logs and antivirus log information to port 30514, and only attack logs are displayed on SecCenter, while antivirus logs are not. By checking locally on IPS, we find virus logs. We can check by packet capture on SecCenter to determine if the data packets have been sent over.
The data sent over is quite large, and it’s not easy to tell if it’s IPS logs or AV logs, so we first decode the packets.
(Using other data as a substitute in absence of IPS log capture)
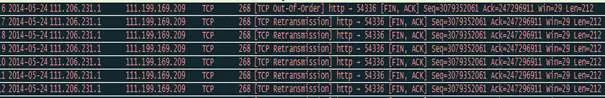
Before decoding:
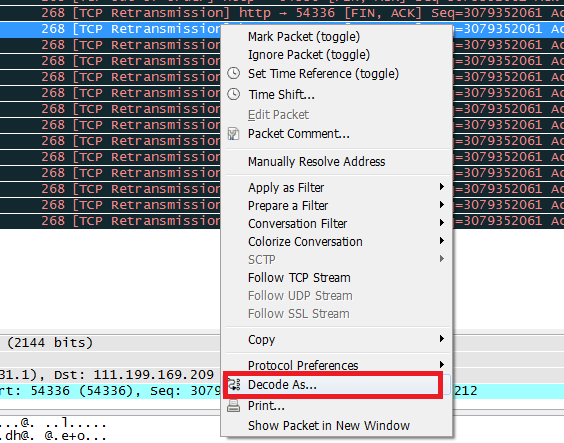
Decoding operation:
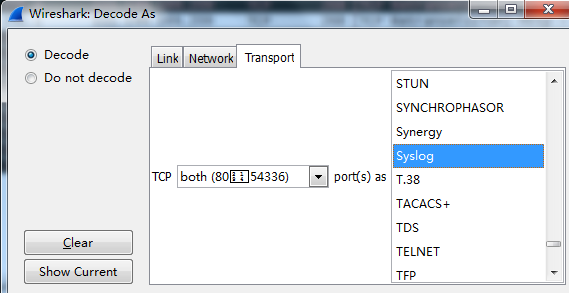
After decoding:
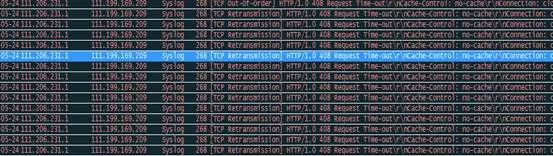
Seventh Move: TCP Packet Trace
To examine the TCP interaction process, extract the entire interaction process from the packets for quick sorting and analysis.
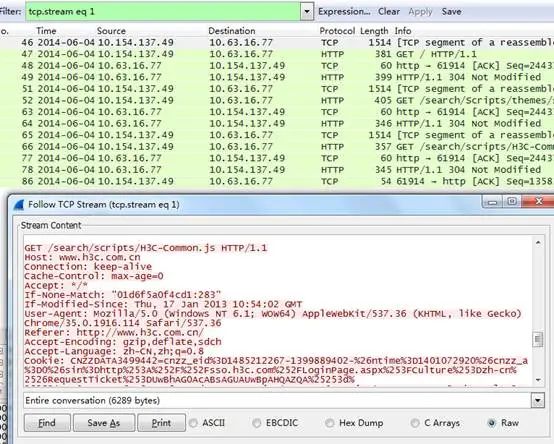
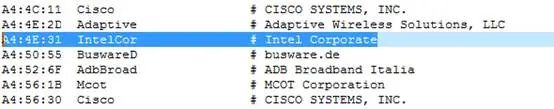
Eighth Move: Identifying Device Manufacturers through Wireshark
When checking for sources of wireless interference, we can note the MAC address of the interfering source and use Wireshark to identify which manufacturer’s device it is, helping us quickly find the source of interference.
For example: MAC address is A4-4E-31-30-0B-E0
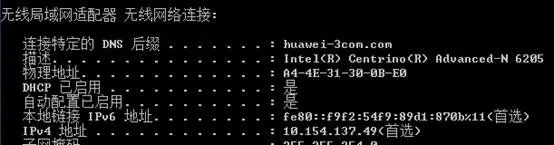
We search in the manuf file in the Wireshark installation directory