Re2Pcap is an abbreviation for the English words Request2Pcap and Response2Pcap. Community edition users can use Re2Pcap to quickly create PCAP files and test them against Snort rules.
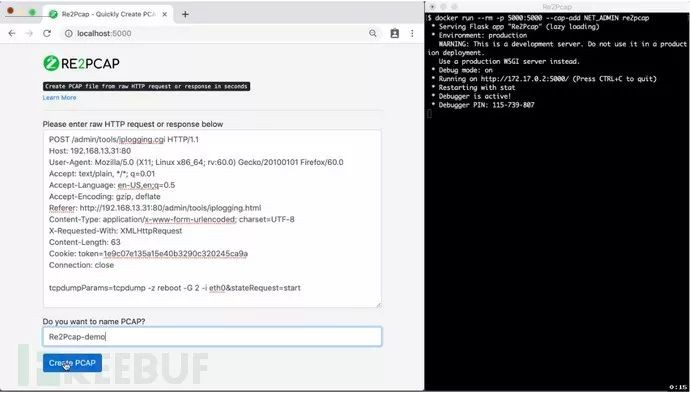
Re2Pcap allows you to quickly create a PCAP file for a raw HTTP request (as shown below).
POST /admin/tools/iplogging.cgi HTTP/1.1Host: 192.168.13.31:80User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0Accept: text/plain, */*; q=0.01Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateReferer: http://192.168.13.31:80/admin/tools/iplogging.htmlContent-Type: application/x-www-form-urlencoded; charset=UTF-8X-Requested-With: XMLHttpRequestContent-Length: 63Cookie: token=1e9c07e135a15e40b3290c320245ca9aConnection: closetcpdumpParams=tcpdump -z reboot -G 2 -i eth0&stateRequest=startUsage of Re2Pcap
git clone https://github.com/Cisco-Talos/Re2Pcap.gitcd Re2Pcap/docker build -t re2pcap .docker run --rm --cap-add NET_ADMIN -p 5000:5000 re2pcapOpen localhost:5000 in a web browser to access Re2Pcap, or use the Re2Pcap-cmd script to interact with the Re2Pcap container to obtain PCAP files in the current working directory.
Requirements
Docker
HTTP Raw Request / Response
Web browser (For best results, use a Chromium-based web browser)
Advantages
Easy to install. No complex multi-VM setup required.
Re2Pcap runs on a Docker image based on Alpine Linux, with a size of less than 90MB.
Dockerfile
FROM alpine# Get required dependencies and setup for Re2PcapRUN echo "http://dl-cdn.alpinelinux.org/alpine/edge/testing" >> /etc/apk/repositoriesRUN apk update && apk add python3 tcpdump tcpreplayRUN pip3 install --upgrade pipRUN pip3 install pexpect flask requests httpretty requests-toolbeltCOPY Re2Pcap/ /Re2PcapRUN cd Re2Pcap && chmod +x Re2Pcap.pyWalkthrough
The following image shows a video demonstration of creating a PCAP file using Re2Pcap for the Sierra Wireless AirLink ES450 ACEManager iplogging.cgi command injection vulnerability.
Re2Pcap Development Branch (In Progress)
Currently, the Re2Pcap development branch includes the following additional features:
Simulation of raw HTTP request and response to PCAP
Improved input validation
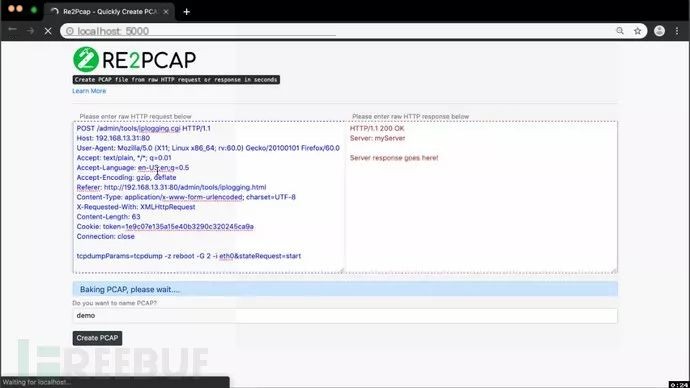
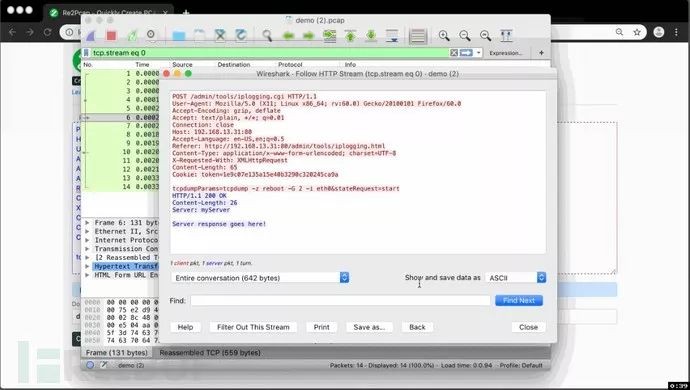
The following image shows the use of Re2Pcap dev for creating a PCAP file for the Sierra Wireless AirLink ES450 ACEManager iplogging.cgi command injection vulnerability:
Re2Pcap Workflow
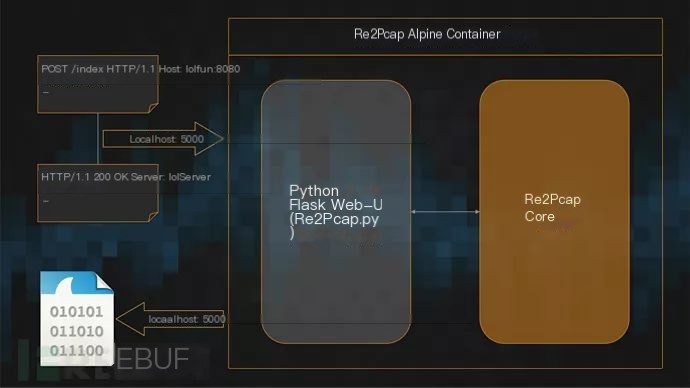
As shown above, Re2Pcap is a Python3 application based on Alpine Linux with a Flask-based web interface.
Re2Pcap parses input data into a raw HTTP request or response, and executes client/server interaction during packet capture. After the interaction, Re2Pcap presents the captured packets in PCAP file format.
Recommendations
Please use Linux as the host operating system because Re2Pcap has been thoroughly tested on Linux.
When creating a PCAP for Host: somedomain:5000, modify the Flask application to run on a different port by changing the Re2Pcap.Py app.run call; otherwise, the PCAP will include the Flask application response.
Limitations
If there is no Accept-Encoding header in the raw HTTP request, an Accept-Encoding: identity header will be added to the request.
There is a known issue with Python requests.
That’s pretty terrible. Accept-Encoding: identity is always valid, as per RFCs. Sending it should be completely harmless. Otherwise, removing it would require us to replace httplib.
Below are the source and destination IPs from the Re2Pcap PCAP.
Source IP: 10.10.10.1
Destination IP: 172.17.0.2, please use the tcprewrite -D option to modify the destination IP to another IP address as needed. You can also use tcpprep and tcprewrite to set other IPs as endpoints. Due to inconsistent results with tcprewrite, another method was used to set different SRC/DST IPs.
Specifying HTTP/1.1 302 as a response will generate a PCAP and access the resource specified in the Location:header with the maximum retry count possible. You can also use Wireshark in tests to export only the first HTTP stream, excluding others that might affect your stream.


