How I Creatively “Cracked” *Sign Check’s Sign and Authorization of *Sky Check!
Tools/Development Languages Needed:
it could be:1. Utilize Python (2 or 3) for reverse engineering tasks. 2. Employ the app crawling magic tool mitmproxy for effective reverse engineering. 3. Explore KeySprite as a tool for reverse engineering projects. 4. Previously, Postern was a forced packet capture tool used in reverse engineering.
Through previous reverse engineering and packet capture analysis, we found that the sign and author tags of these two apps are the most important, and they are bound by timestamps. This means if we don’t analyze their encryption algorithms, it’s challenging to capture the data, but through testing, we discovered the following:
- The sign for Qichacha is related to the timestamp
- The sign can be used for any URL
- The sign does not expire quickly
- The Authorization for Tianyancha is also related to the timestamp
- The Authorization also does not expire quickly
- The Authorization can also be used for any URLBased on these findings, it’s actually very simple to apply these. How?? See the following creative process:
Operations on the Phone
Device: Huawei Honor 6x Android Version: 6.0 Rooted: Yes Xposed: Yes Install the latest versions of Qichacha and Tianyancha, and the latest version of KeySprite, finally Postern software. Postern needs to be configured, details will be discussed when it’s used.
Computer Operations (Mine is Mac, same operation for Windows, in both cases Python environment is installed and we can write Python)
1. Introduction to mitmproxy
Code Language: JavaScriptCopy
Quote from HugoAs the name suggests, mitmproxy is a proxy for MITM, which is short for Man-in-the-middle attack. A proxy used for MITM first forwards requests like a normal proxy, ensuring communication between server and client. Then, it timely inspects, records intercepted data, or tampers with data to invoke specific behaviors of the server or client.Different from packet capture tools like fiddler or wireshark, mitmproxy not only intercepts requests to help developers view and analyze, but also allows for secondary development via custom scripts. For instance, using fiddler, you can filter requests to a specific URL from a browser and view and analyze its data, but it cannot achieve highly customized needs like: “Intercept the request to that URL from the browser, empty the return content, and store the real return content in a database, sending an email notification when an exception occurs.” For mitmproxy, such needs can easily be achieved by loading custom Python scripts.However, mitmproxy does not actually conduct MITM attacks on innocent parties. Since mitmproxy operates on the HTTP layer and the current adoption of HTTPS enables clients to detect and avoid MITM attacks, to make mitmproxy work normally, clients (APP or browser) must actively trust mitmproxy’s SSL certificate or ignore certificate anomalies. This means that the APP or browser belongs to the developer – clearly, this is not for illegal business, it’s for development or testing purposes.So, what practical significance does such a tool have? As far as I know, one of the more widespread applications is creating simulation crawlers, where a phone simulator or headless browser is used to crawl data from apps or websites. Mitmproxy acts as a proxy intercepting, storing crawled data, or modifying data to adjust crawler behavior.
2. Installing mitmproxy
Mac: Run the following commands in the terminal; (Win: Run in cmd)
Code Language: JavaScriptCopy
pip3 install mitmproxy # python3 orpip install mitmproxy # python2After installation, enter mitmdump --version:
Code Language: JavaScriptCopy
Mitmproxy: 4.0.4 Python: 3.7.4 OpenSSL: OpenSSL 1.1.0i 14 Aug 2018 Platform: Darwin-18.7.0-x86_64-i386-64bit3. Starting mitmproxy
To start mitmproxy, you can use any one of the three commands: mitmproxy, mitmdump, or mitmweb. These commands serve the same purpose but differ in their user interface.
When the mitmproxy command is launched, it provides a command-line interface where users can see real-time requests occurring and filter and examine request data via commands:
- launched with
mitmproxy
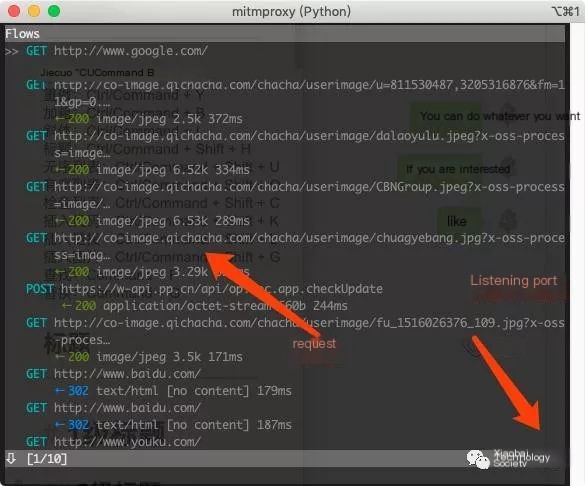 >
>
- launched with
mitmweb
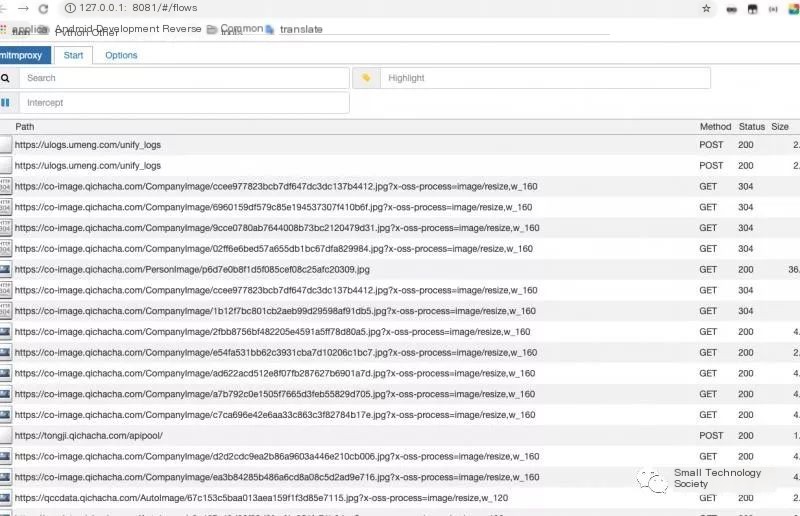 >
>
4. Proxying the Phone
Code Language: JavaScriptCopy
Connect the phone to WiFi-> Long press to modify network -> Show advanced options -> Proxy -> ManualEnter ifconfig on Mac's terminal (Windows use ipconfig). The host is the IP shown belowPort is the listening port aboveClick confirm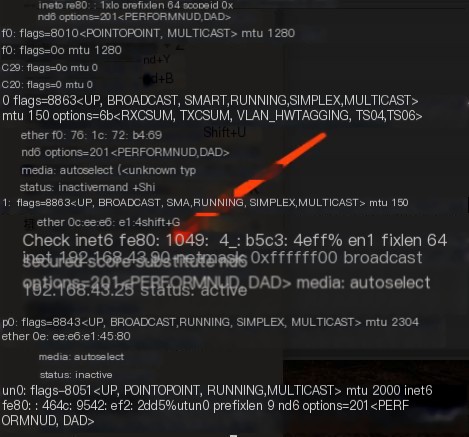
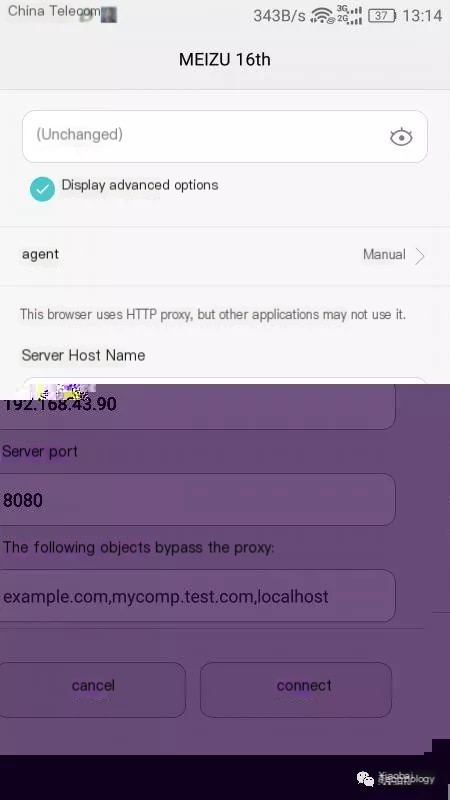
- Install certificate (Haven’t tested if a certificate is needed, but generally SSL requires one, right?) Install certificate online, access http://mitm.it from mobile browser (select Android)5. Capturing the data we needYou can view our data packets at http://127.0.0.1:8081/#/flows. Open Qichacha and Tianyancha apps to find no data packets or endpoints, as these apps bypass WiFi proxy and don’t go through
mitmproxy. In such cases, we use the forced packet capture toolPosternmentioned earlierPostern allows you to customize and re-route network traffic on devices
1. You can make all Apps (including those that do not support proxy configuration) automatically use your specified proxy server, without needing to configure proxy settings for each App. Postern fully supports all popular proxy tunneling protocols, including:
Code Language: JavaScriptCopy
SSH Tunnel SOCKS5 Proxy HTTPS/HTTP CONNECT method Tunnel- Postern has a sniffer function to capture packets entering and leaving the device. It is convenient for viewing whether there is any advertising or malicious traffic.
- Postern supports importing surge format configuration files and fully supports all core functions of iOS surge
Configuring Postern:
- Open proxy configuration-> Add proxy server-> Configure as below:
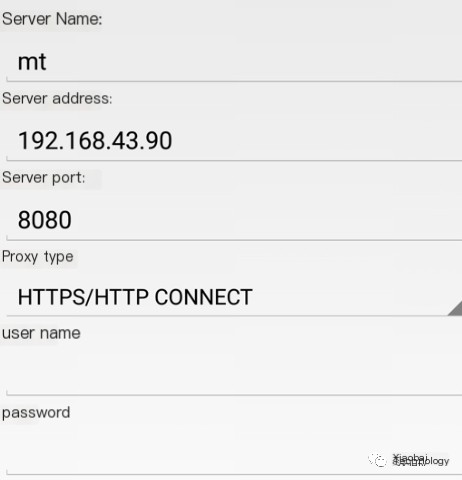
- Open configuration rules, delete previously unused rules
- Add rules, configure as below:
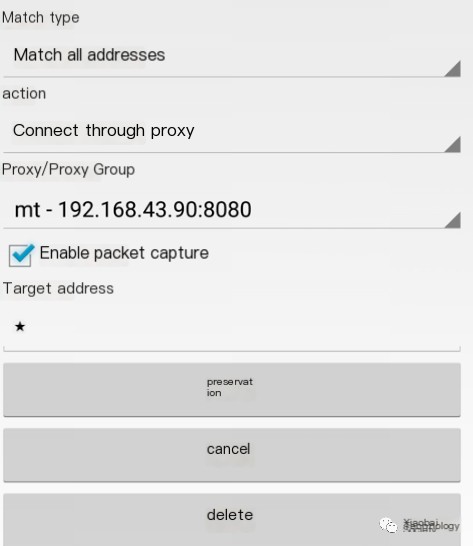
4. Lastly, turn on VPN, then open Qichacha app, observe our web, did we capture the data packets including the sign we need? Using the same method, we can attempt with Tianyancha app, didn’t capture data packets? We’ll then need to use JustTrustMe, which doesn’t require further explanation. JustTrustMe Release version download link:
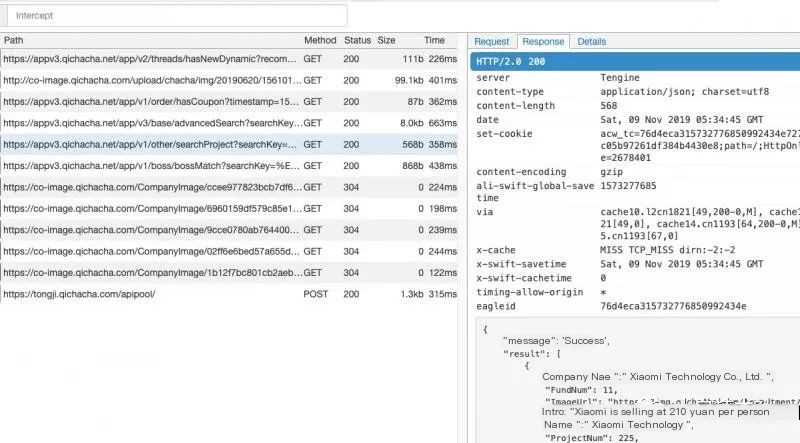
6. Using Python + mitmproxy to interceptWrite the Python script, available on my GitHub, the image includes the sign and timestamp we need. Same for Tianyancha
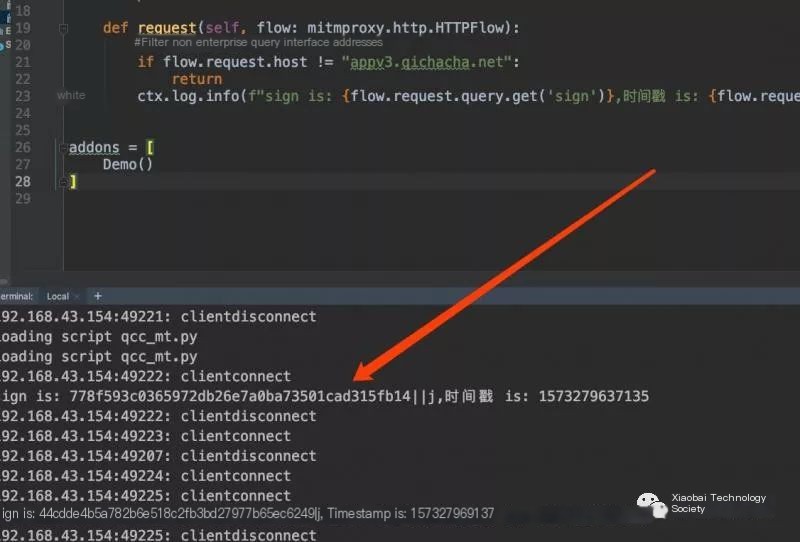
Lastly, send this sign and timestamp to a queue for our use.
7. Automation
As mentioned at the start, sign and Authorization have limited validity, shorter for Tianyancha, so what do we do? We can leverage KeySprite to operate.
- Open KeySprite -> Record script -> Open Qichacha app -> Search for a company
- Simply make this action repetitive
- Use recording to replay the process, all set
8. Finally, we can use sign and AuthorizationAttached is my GitHub linkIf you like it, please give a star, thank you.


