Patch Comparison
Download the Security Only for the corresponding system version and CVE number from MSRC, extract files.
Search for files, determine vulnerability information based on the vulnerability advisory.
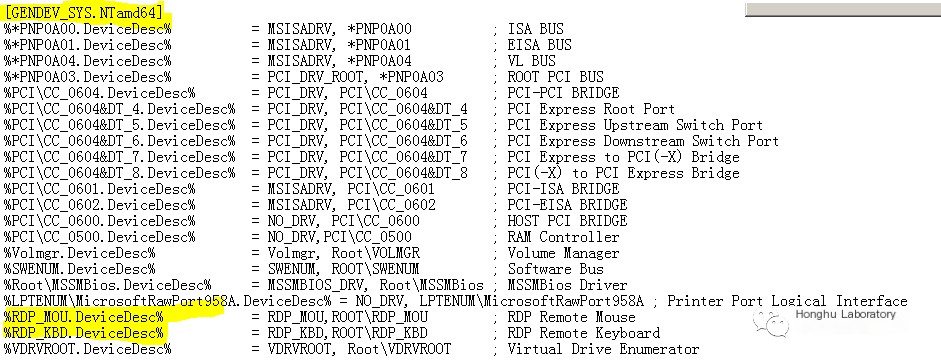
By confirming the patched files and conducting an analysis, locate the vulnerability.
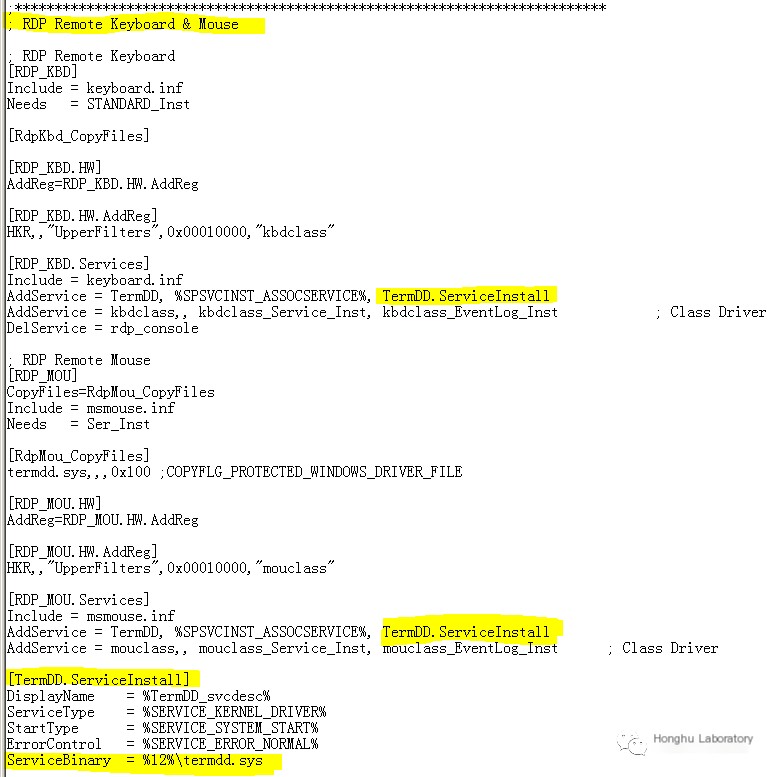
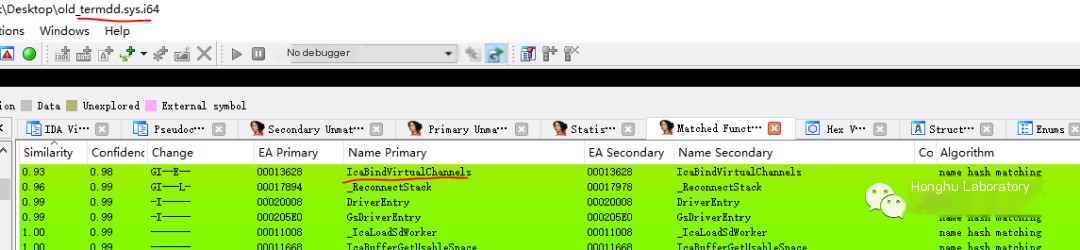
Another method to locate patch files is via
Decrypting RDP Traffic
RDP Connection Sequence
Use Wireshark to capture packets; the first three are TCP/IP handshake packets.
RDP is encapsulated in the TPKT protocol, right-click on unrecognized data to decode it as TPKT.
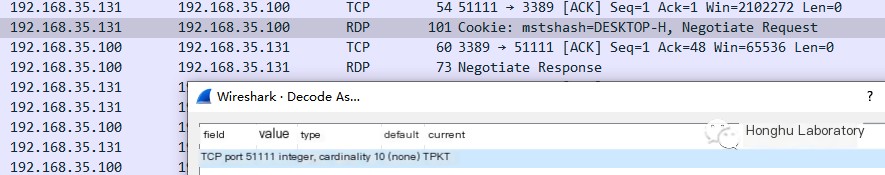
Decrypt Wireshark TLS EncryptionUse Mimikatz to obtain the pfx file, run on the RDP server.
Use OpenSSL to obtain the pem file, the password is
openssl pkcs12 -in yourdumed.pfx -out mykey.pem -nodes
Load the pem file in Wireshark
POC Analysis
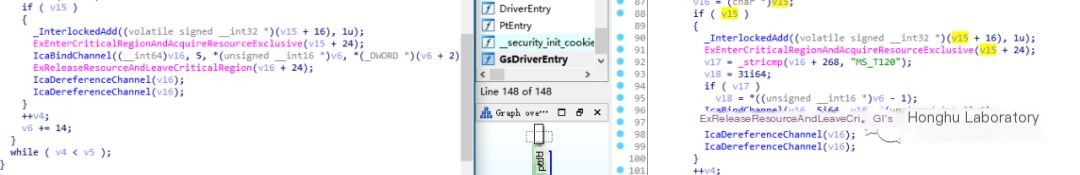
Place a breakpoint layer by layer to analyze the patch; triggering the patch requires a return value of true. The function finds the channel name in the circular list.
Debugging with breakpoints
Always finding the channel through lookup
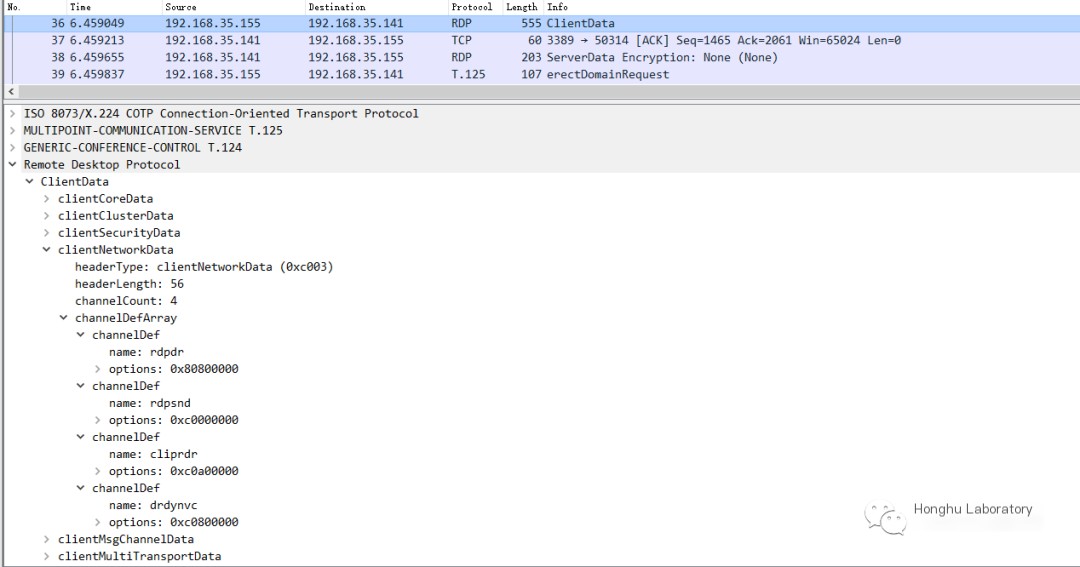
The channel being searched originates from an RDP request
When is the MS_T120 channel created
You will find a function,

Function logic:
Find the channel by name; if it doesn’t exist, create it.
ExAllocatePoolWithTag creates space, then initializes it.
IcaFindVcBind returns a virtual channel ID.
IcaBindChannel binds the channel to a specified channel ID.
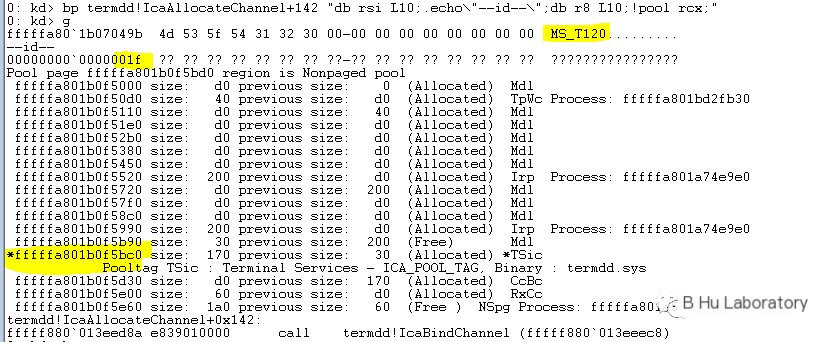
Channel offset 0xa8 points to the next circular list, -0x10 for the name.
-0x8 for the id.
The MS_T120 channel is created and bound to the 0x1f channel number when the RDP is applied for,
When sending a request, it will traverse the channel names; if there is a connection
The second binding of the channel changes 0x1f to 0x3

Releasing triggers the vulnerabilityIcaDereferenceChannel function
Freeing the same memory twice
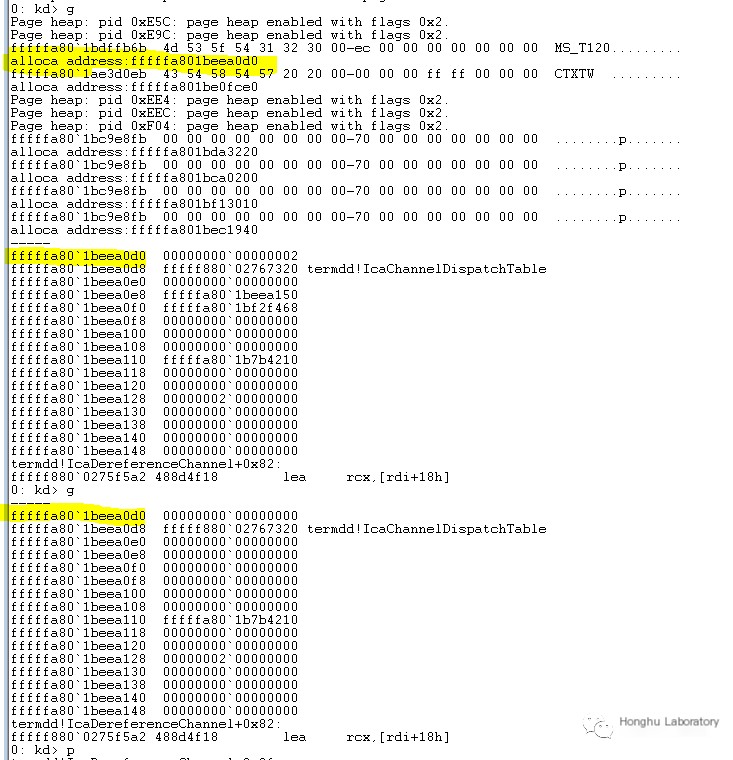
The first time



