In the following sections, you will find information about Wireshark filter rules that can help you efficiently analyze network traffic. These rules are essential for narrowing down the data captured, making it easier to focus
Recently, I have come across some introductions to Wireshark filtering rules online, and most of them are somewhat outdated. It seems the syntax in new versions has changed, so here I am writing a series on Wireshark rules based on the latest version 1.12.
Aside
After graduation, I encountered many things related to networking. Initially, it was video-related, then wireless protocols, and now HTML. I always end up dealing with network packets. It’s unavoidable to come in contact with some packet capturing tools like Wireshark, Fiddler, HTTP Analyzer, etc., and even browser-built network tools. Fiddler and HTTP Analyzer are targeted at HTTP/HTTPS protocols, which inherently brings some limitations. Wireshark, however, uses WinPCAP as an interface to directly exchange data packets with the network card, ensuring the integrity of the data.
The initial rambling may have been too much and might draw criticism from everyone. So, let’s get straight to the point. This article will first talk about how to use Wireshark and will later introduce explanations of several practical packet capturing tools. Please stay tuned.
This article is based on Wireshark 1.12.
 />
/>
Brief Introduction to Wireshark Filters
Capture Filters: Used to decide what kind of information to record in the capture results. They need to be set before starting the capture.
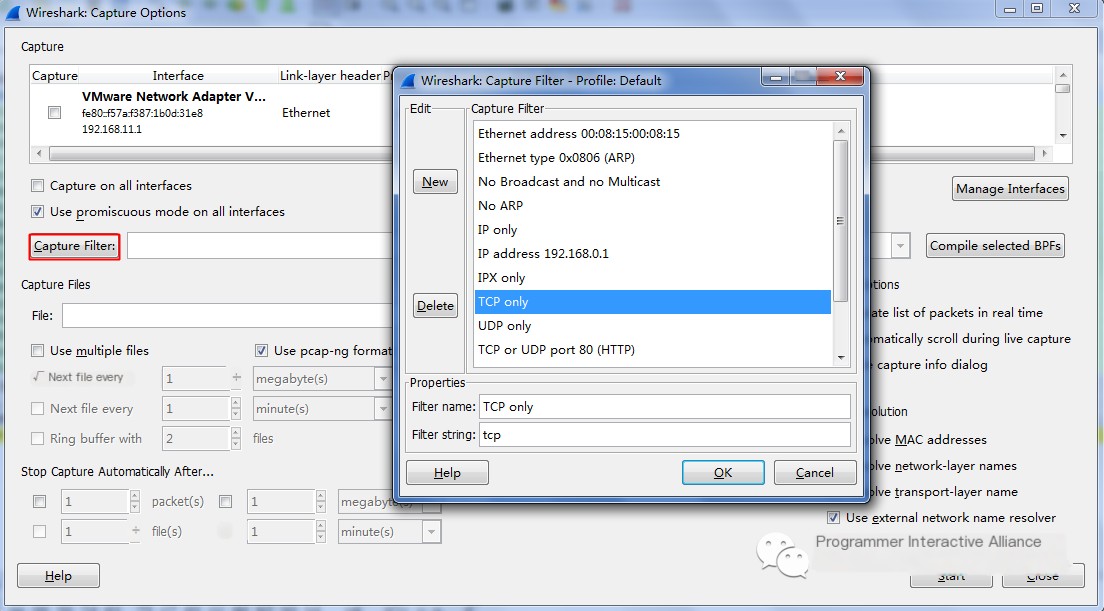 />
/>
Display Filters: Used for detailed searching in the capture results. They can be modified freely after obtaining the capture results.
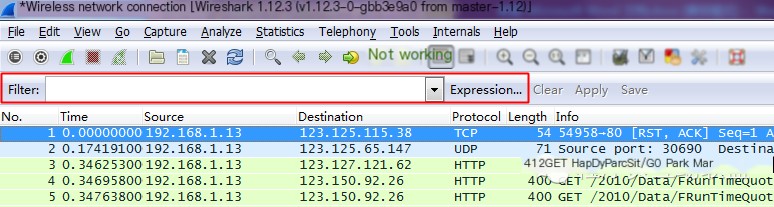
Below, I will discuss some practical rules for Display Filtering, using HTTP as an example; other protocols are similar.
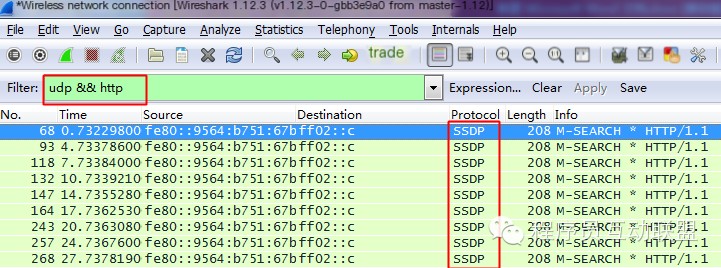
1. Direct Protocol Filtering
Filtering based on protocols like HTTP, ARP, TCP, UDP, etc. This is the simplest way of filtering, for example, if I need to capture a data packet for an HTTP request. This is the most direct method, it allows you to directly see network requests and responses. Using just the protocol name can perform this type of filtering. If you are not familiar with protocols, please refer to my other article, “Seven-Layer Network Model and Protocols of Each Layer.”
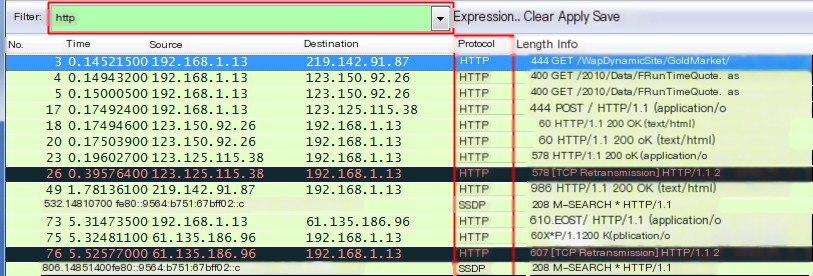
Some people might ask, how is there still an SSDP packet when filtering for HTTP protocol packets in the image? You can search for SSDP online and find out.
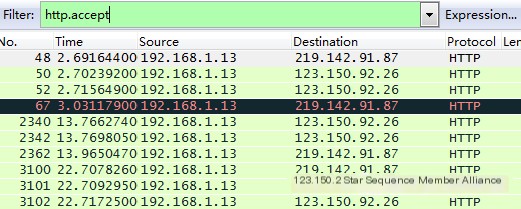
2. Value Comparison Filtering
Value comparison uses the attribute values of a protocol. Some might ask: what are protocol attributes? You can directly input “http.” in the filter window, and Wireshark will automatically prompt you with the attribute values you’ll need to input next, showing a list of attributes.
We can do filtering through simple statements. For example:
http.accept Comment: Represents a filter for packets that contain the accept header in HTTP protocol
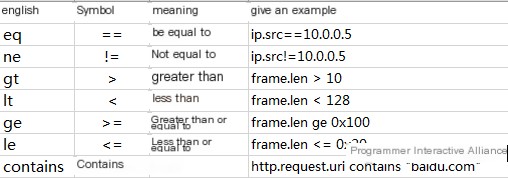
Using comparison operators, Wireshark provides six comparison operators: ==, !=, >, >=, <, <=. The corresponding English words can achieve the same function, as shown in the table:
For the numeric part, decimal, octal, and hexadecimal can be used. Multiple formats are available:
ip.len le 1500
ip.len le 02734
ip.len le 0x436
eth.dst == ff:ff:ff:ff:ff:ff
eth.dst == ff-ff-ff-ff-ff-ff
eth.dst == ffff.ffff.ffff
ip.addr == 129.111.0.0/16
http.request.uri == “http://www.wireshark.org/”
For example:
http.accept == “XXX” Comment: XXX indicates a possible string in accept, commonly */*
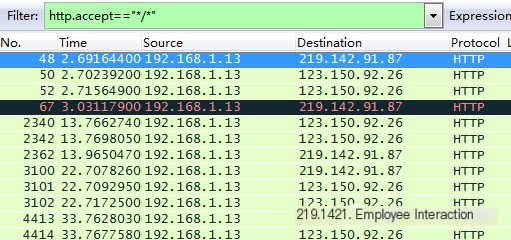
Other protocols and attributes are similar; everyone can practice the above methods frequently, and you’ll become proficient in the usage scenarios of various protocols.
3. Expression Combination Filtering
Speaking of expression combination filtering, it requires the use of logical operators
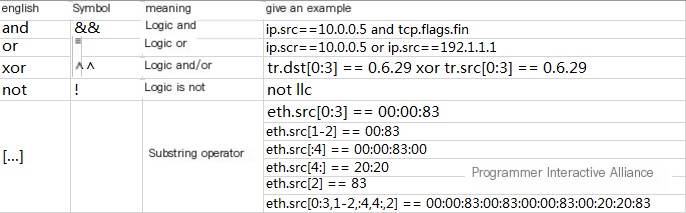
Using expression combination filtering can more accurately capture the desired network packets. When using combination filtering, it’s crucial to deeply understand the meaning of these symbols.
For example:
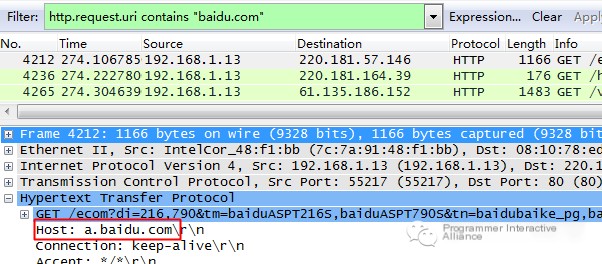
Note: When using the != comparison in combination with eth.addr, ip.addr, tcp.port, udp.port, etc., it may not achieve your expectations in some scenarios.
For example:
We often use ip.addr == 1.2.3.4 to filter network packets containing the IP address 1.2.3.4. So how to filter out network packets that do not contain the address 1.2.3.4? Naturally, we might think of using ip.addr != 1.2.3.4. However, this expression might not yield your expected results.
The meaning of this expression is: packets containing the name ip.addr but not equal to 1.2.3.4 in value. As everyone knows, a network packet contains two IP addresses: source address and destination address. In most cases (except when sending to oneself), the source and destination addresses are different, so there will certainly be one value not equal to 1.2.3.4. Therefore, this filter expression does not meet our expectations. So how should we write our desired expression?
To achieve our expectation, it should be written as: !(ip.addr == 1.2.3.4), and a diagram might make it clearer:
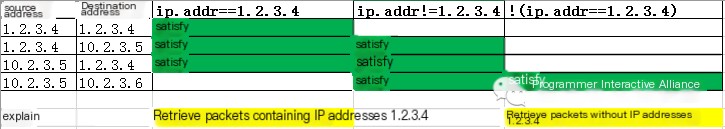
I’ll stop here for today. How to really use filter rules requires combining it with your own real-world scenarios.
Upcoming, there will be explanations on other filtering tools. Let’s progress together.



