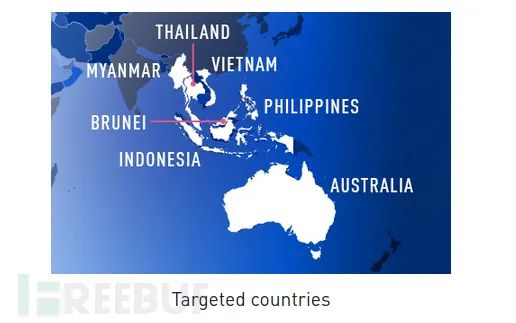
Over the past decade, Naikon APT has consistently targeted the same region, including Australia, Indonesia, the Philippines, Vietnam, Thailand, Myanmar, and Brunei, using a backdoor called Aria-body. The targets include foreign ministries, ministries of science and technology, and all government departments. The attackers leverage compromised government organizations to launch attacks aiming to infect additional targets by infiltrating new organizations using trusted known contacts and expanding their network.
The group’s objective is to gather intelligence and monitor government activities. The attackers search for and collect specific documents from infected computers and networks within government departments, extract data from removable drives, and capture screenshots and keystrokes. The group uses infected internal servers as attack and control servers to avoid detection by the targets.
During the research, several infection chains were discovered for spreading Aria-body. Initially, a malicious email named The Indians Way.doc, containing the RoyalRoad malware, was sent from an Asia-Pacific government embassy to the Australian state government. The loader attempts to download and execute the next stage payload from spool.jtjewifyn.com.
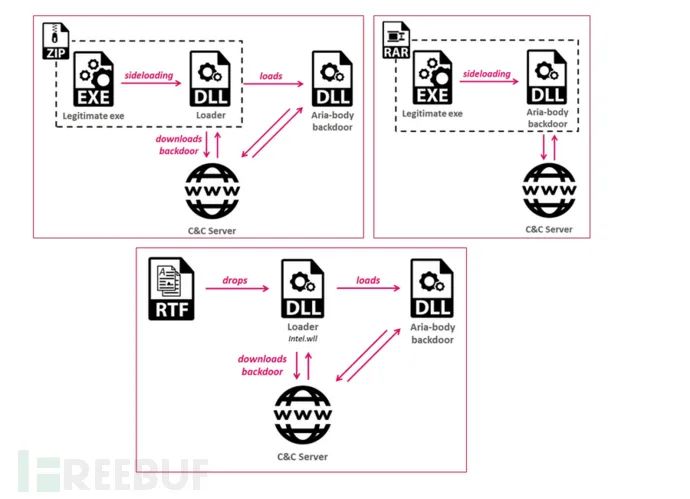
Several infection methods were observed:
1. RTF files exploiting RoyalRoad2. Archive files containing legitimate executables and malicious DLLs, utilizing Outlook and Avast as proxies to load the malicious DLL3. Direct executable loaders
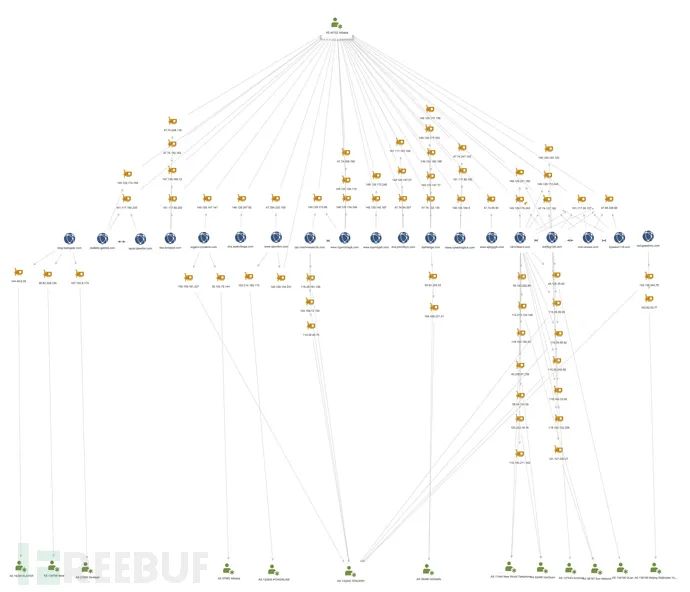
In recent operations, the attackers’ C&C servers used the same hosting and DNS services, reusing the same IP addresses across multiple domains:
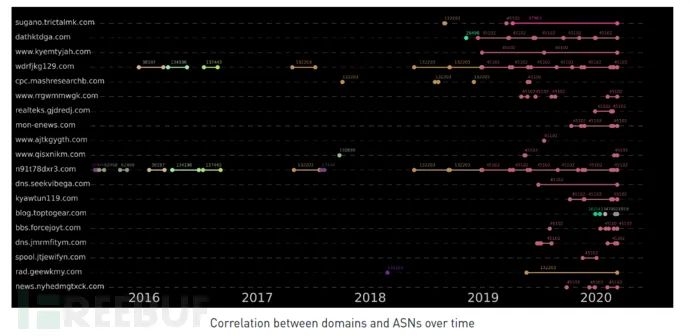
Domain usage:
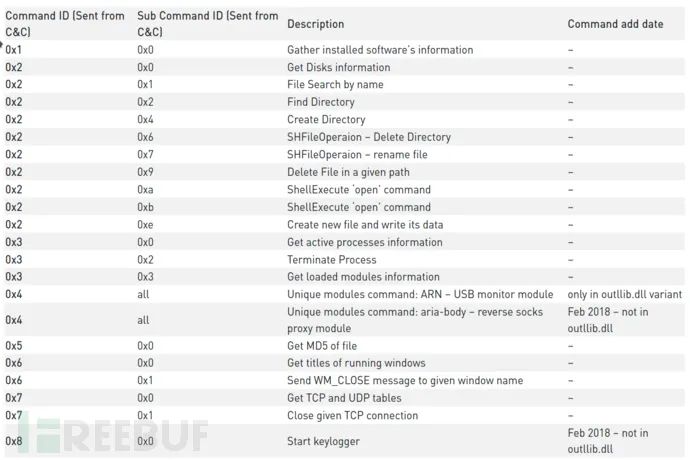
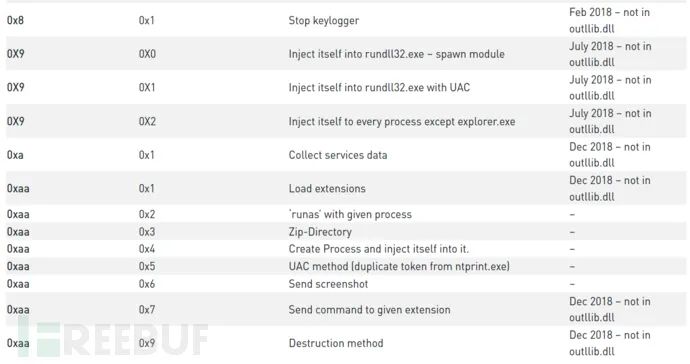
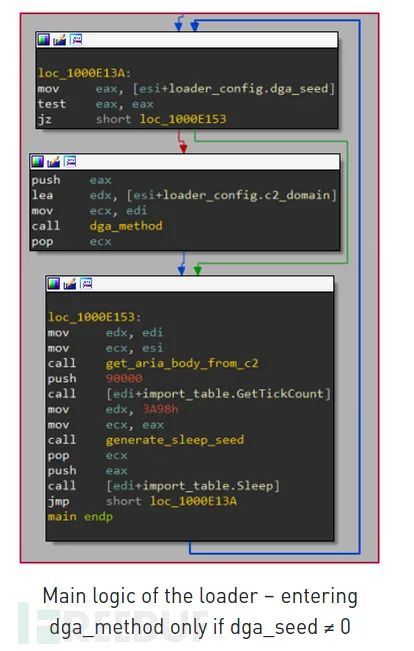
Since 2017, the capabilities of the Aria-body loader have not changed significantly; the loader is responsible for the following tasks:
1. Establishing persistence via startup folders or registry 2. Injecting itself into another process, e.g., rundll32.exe and dllhost.exe 3. Decrypting two blobs: “Import Table” and “Loader Configuration” 4. Using a DGA algorithm 5. Communicating with C&C addresses to retrieve next-stage payloads 6. Decrypting the received payload DLL (Aria-body backdoor) 7. Loading and executing the DLL’s exported functions
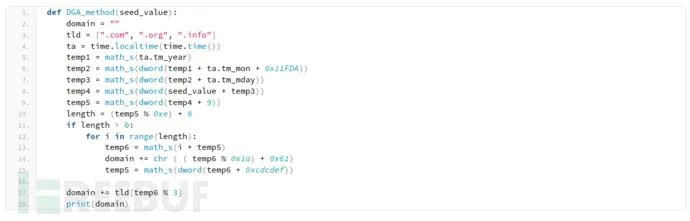
Configuration & DGA
The loader configuration is encrypted and includes information like C&C domains, ports, user agents, and a domain generation algorithm (DGA) seed. If the seed is not zero, the loader uses the DGA to generate C&C domains based on the seed and communication date. The configuration of the loader is decrypted using the following algorithm:
def decryptbyte = (k + j) % 0xff buf[i] = buf[i] ^ xorbyte
C&C Server
After acquiring the C&C domains, the loader communicates to download the next-stage programs. The attackers operate the C&C server in narrow time windows, with it being online only for a few hours each day. In the loader’s last stage, it receives the XOR key to decrypt the downloaded RAT.
The downloaded payload is a homemade RAT, called Aria-body, available in both 32-bit and 64-bit versions. The RAT functions include:
1. Creating/deleting files/directories 2. Capturing screenshots 3. Searching for files 4. Executing files with ShellExecute 5. Enumerating processes 6. Collecting file metadata 7. Gathering TCP and UDP table status lists 8. Terminating TCP sessions 9. Collecting operating system information 10. Checking location using checkip.amazonaws.com
Variants of Aria-body also include additional modules, such as:
1. USB data collection module 2. Keylogger module 3. Reverse proxy module 4. Extension loader module
The backdoor has an exported function which, upon execution, initializes a structure called MyDerived and structures for HTTP and TCP connections.
Aria-body first collects data on the victim’s machine, including: hostname, computer name, username, domain name, Windows version, processor MHz, MachineGuid, and public IP.
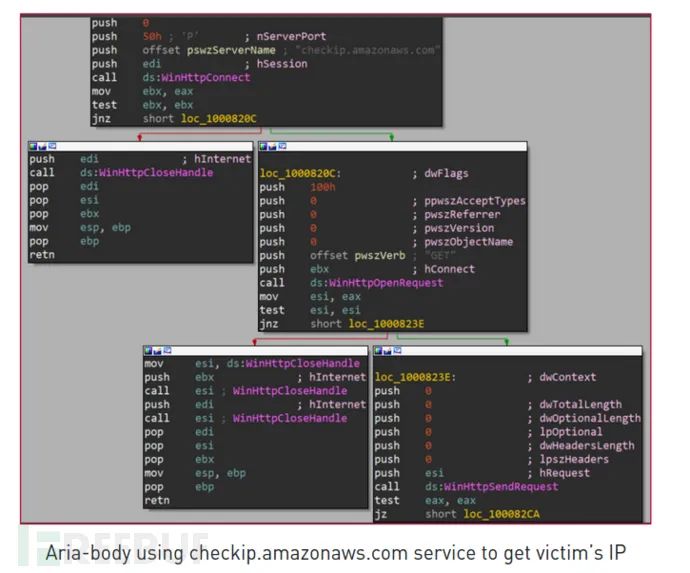
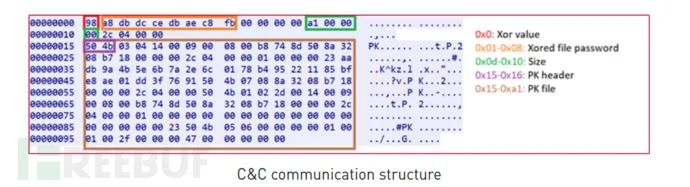
It communicates with the C&C server via HTTP or TCP protocols. The malware determines which protocol to use based on a flag in its configuration. The collected data, combined with an XORed password and XOR key, is sent to the C&C domain:
The research identified a very unique Aria-body variant, with the DLL named outllib.dll, which is part of Office.rar. It does not receive any configuration from the loader and contains hard-coded configuration.
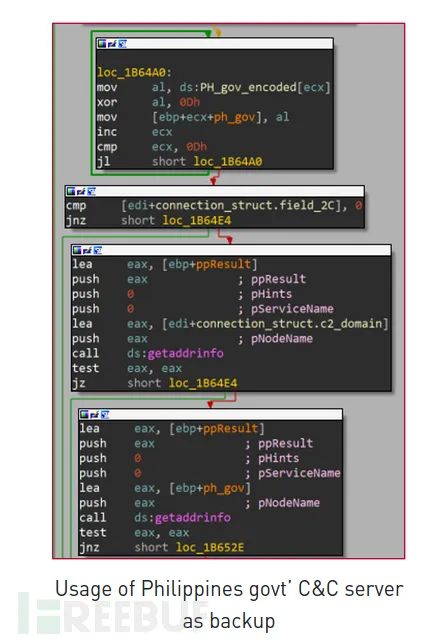
The payload has two different C&C domains: blog.toptogear [.] com, 202.90.141 [.] 25. If the first C&C domain cannot be resolved, the IP address is used.
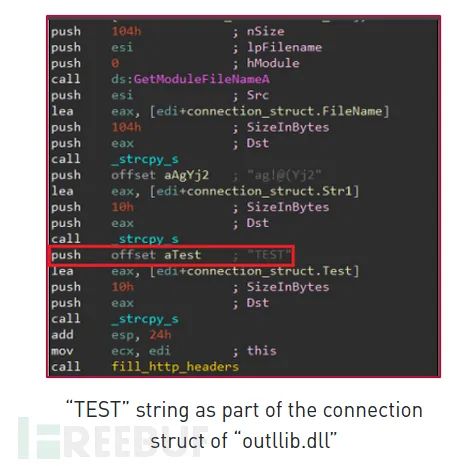
The Aria-body backdoor includes several debug strings that describe the malware’s functions. These debug strings can also be found in the XsFunction backdoor:
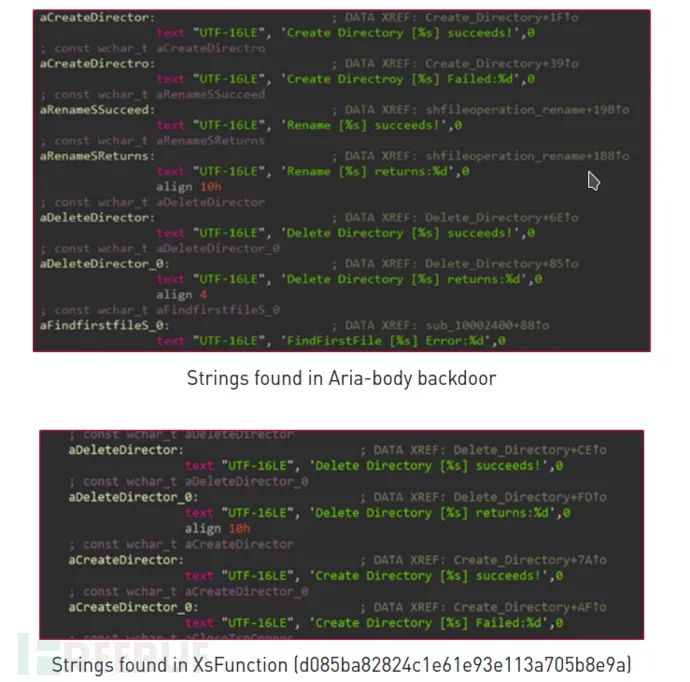
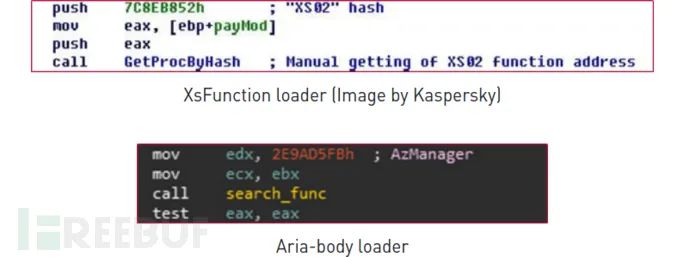
Both XsFunction and the Aria-body loader use the same hash algorithm djb2. In XsFunction, this function is called XS02, whereas it is named AzManager in Aria-body.
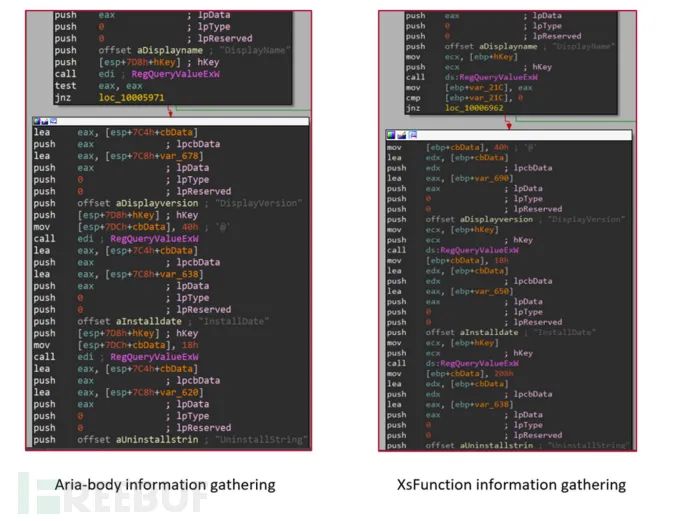
Certain functionalities in the Aria-body backdoor are identical to those in the older XsFunction backdoor.
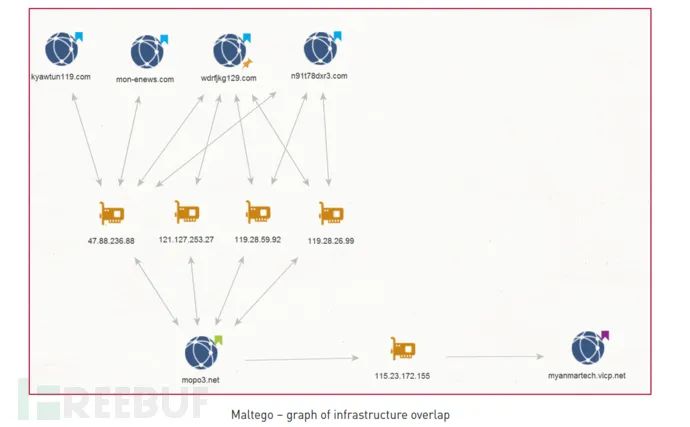
Four C&C servers share an IP with the domain mopo3 [.] net, which resolves to the same IP as the domain myanmartech.vicp [.] net mentioned in the Kaspersky report.
This activity uncovered the latest tools used by the Naikon APT group targeting Asia-Pacific government entities. The attackers leverage universal toolsets like RoyalRoad RTF and custom backdoors like Aria-body. The Naikon APT group has been active for the past five years, continuously evolving by utilizing new servers, changing loaders, fileless loading, and implementing new backdoors to evade detection and analysis.