The reassembly of TCP is one of the most crucial and challenging aspects in intrusion detection systems as it involves complete traffic caching, resulting in significant storage overhead. Statistics indicate that 1 million sessions can generate 1GB to 10GB of memory cache. Therefore, designing an optimized TCP reassembly algorithm is essential. Currently, there are two optimization methods: one is to minimize TCP reassembly to reduce caching, including red-green lists, configuration, and sampling algorithms; the other is to offload the reassembly to hardware such as FPGA to reduce software-based caching. I conducted a lateral comparison of three popular intrusion detection systems to evaluate their optimization points in TCP software reassembly:
Snort – Network Intrusion Detection & Prevention System
GitHub – OISF/suricata: Suricata git repository maintained by the OISF
QSNM Implementation
- Whether QSNM performs stream reassembly is determined by conditional compilation __QNSM_STREAM_REASSEMBLE, and the default configuration does not perform TCP stream reassembly.
- All TCPs of the same stream will undergo stream reassembly. Both upstream and downstream are in a single cache queue, supporting up to 8 packets without considering overlapping parts.
- Reassembly method based on hashmap + doubly linked list.
- TCP stream cache removal methods: 1. Aging 2. No further parsing needed 3. Rule hit
Snort Implementation
- Whether Snort performs stream reassembly is determined by configuration, and the default setting is to perform TCP stream reassembly.
|
track tcp |
Track sessions for TCP. The default is “yes” |
|
max tcp |
Maximum simultaneous TCP sessions tracked. The default is 262144, maximum is 1048576, minimum is 2 |
|
memcap |
Memory cap for TCP packet storage. The default is 8388608 (8MB), maximum is 1073741824(1GB), minimum is 32768(32KB) |
|
timeout |
Session timeout. The default is 30, the minimum is 1, and the maximum is 86400 (approximately 1 day). |
|
policy |
The Operating System policy for the target OS |
|
overlap limit |
Limits the number of overlapping packets per session. The default is 0 (unlimited) |
|
max_queued_bytes |
Limit the number of bytes queued for reassembly of a given TCP session. Default is 1048576(1MB). |
|
max_queued_seg |
Limit the number of segments queued for reassembly of a given TCP session. The default is 2621 |
|
ignore_ports |
The default is 0 (unlimited) |
Suricata Implementation
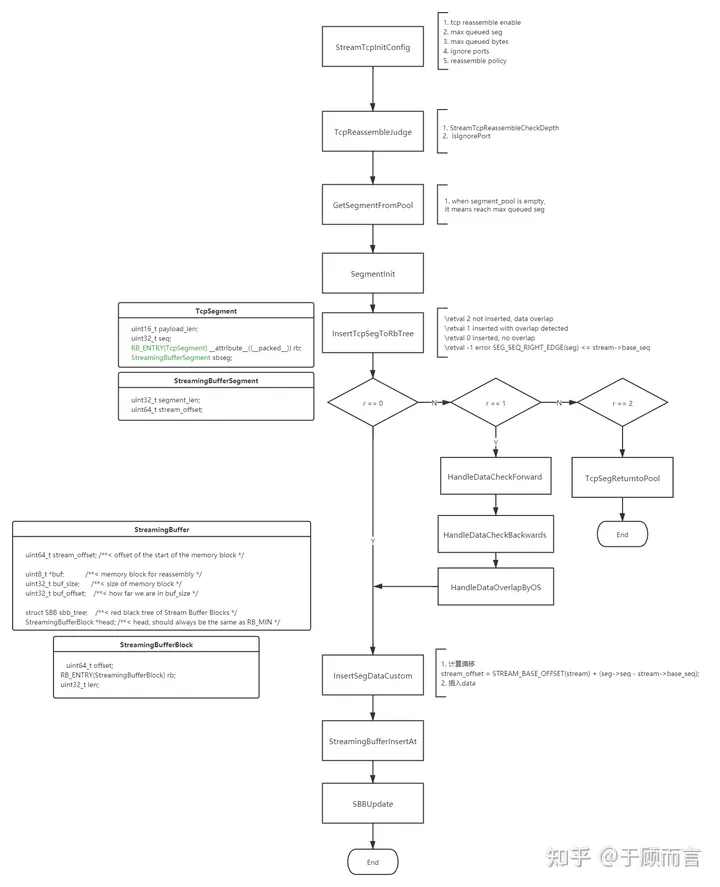
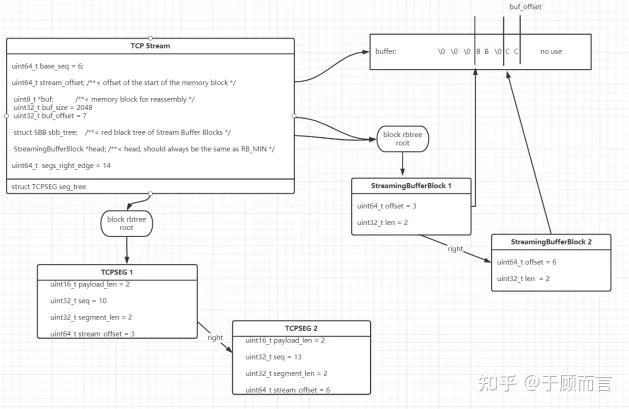
Windows/BSD prefer original packets, except when the starting sequence number of the subsequent packet is ahead of the original packet.
Windows/BSD: <1><1><1><4><4><2><3><3><3><6><6><6><7><7><7><3.3><3.3><3.3><3.4><3.4><3.5><3.5><3.6><11>
Linux prefers original packets except when the starting sequence number of the subsequent packet is ahead of the original packet or the starting sequence number of the subsequent packet is the same but the ending sequence number is after the original packet.
Linux: <1><1><1><4><4><2><3><3><3><6><6><6><7><7><7><3.3><3.3><3.3><3.4><3.4><3.5><3.5><11><11>


