Preface
Anyone familiar with network security technology knows the importance of “packet capture.” For those outside the field, you might wonder what packet capture is. Recognizing that everyone has varying levels of technical expertise, I’ll make an effort to explain this crucial network security tool in a more accessible way.
Packet capture is to intercept, resend, edit, transfer and other operations of the data packets sent and received by the network transmission. It is also used to check network security. Packet capture is also often used for data interception. Hackers often use packet capture software to obtain your non-encrypted Internet data, and then attack through analysis and social engineering. Therefore, learning packet capture is very important for learning network security technology.
When we do interface testing, we often need to verify whether the message sent is correct, or when there is a problem, we need to check whether the content of the package sent by the mobile client to the server is correct. In this case, we need to use a packet capture tool. What are the commonly used packet capture tools for engineers and programmers? Today we will briefly talk about the two most commonly used ones.
Fiddler is a program that runs on Windows and is specifically used to capture HTTP and HTTPS.
Wireshark can obtain HTTP and HTTPS, but it cannot decrypt HTTPS, so Wireshark cannot understand the content in HTTPS.
In summary, if you are dealing with HTTP, HTTPS, use Fiddler, and other protocols such as TCP, UDP, use Wireshark.
1. Fiddler
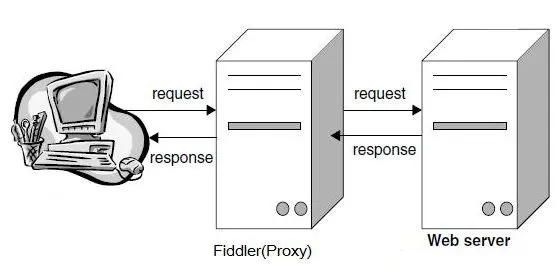
When starting fiddler, the program will act as a proxy, so all http requests will pass through fiddler before reaching the target server. Similarly, all http responses will flow through fiddler before returning to the client.
Fiddler can capture data packets from any program that supports http proxy. If you want to capture https sessions, you must install a certificate first.
1.1 How Fiddler Works
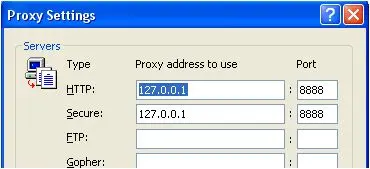
Fiddler works as a proxy web server, it uses the proxy address: 127.0.0.1, port: 8888. When Fiddler automatically sets the proxy, it will automatically log out of the proxy when exiting, so that it will not affect other programs. However, if Fiddler exits abnormally, the web page will be inaccessible because Fiddler does not automatically log out. The solution is to restart Fiddler.
1.2 How to capture Firefox sessions with Fiddler
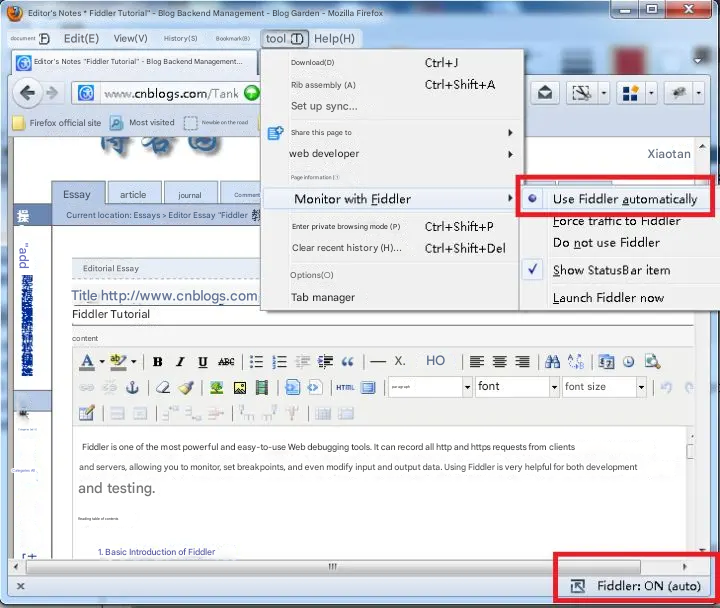
The data packets of any program that supports HTTP proxy can be sniffed by Fiddler. The operating mechanism of Fiddler is actually the HTTP proxy that listens to port 8888 on the local machine. When Fiddler2 is started, the default IE proxy is set to 127.0.0.1:8888, and other browsers need to be set manually, so you can change the Firefox proxy to 127.0.0.1:8888 to monitor the data.
Follow the steps below to set up a proxy on Firefox
Click: Tools -> Options, in the Options dialog box click Advanced tab -> network tab -> setting.
1.3 Install Fiddler plugin in Firefox
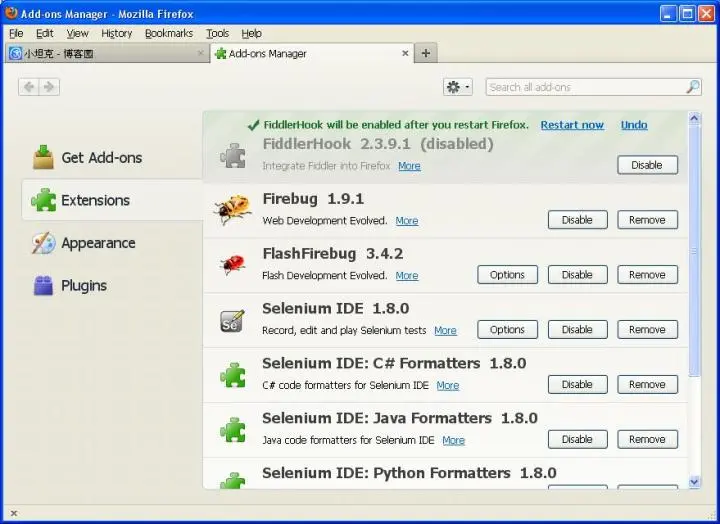
It is troublesome to modify the proxy in Firefox. You have to remove the proxy when you don’t use Fiddler. It is recommended that you use the Fiddler hook plug-in in Firefox, so that you can easily use Fiddler to obtain the request and response in Firefox. When you install Fiddler, the Fiddler hook plug-in is already installed. You need to enable this plug-in in Firefox. Open Firefox tools->Add ons -> Extensions to start FiddlerHook
1.4 How to capture HTTPS sessions with Fiddler
By default, Fiddler will not capture HTTPS sessions. You need to set it up by opening Fiddler Tool->Fiddler Options->HTTPS tab
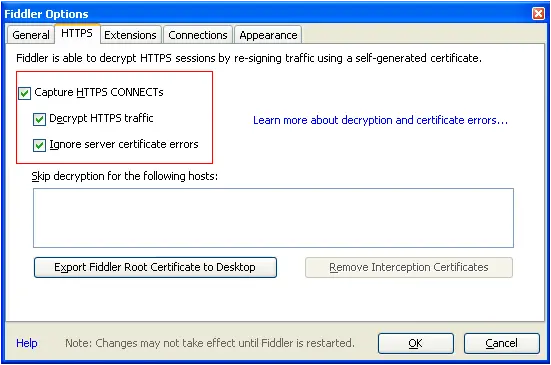
Select the checkbox, the following dialog box pops up, click “YES”
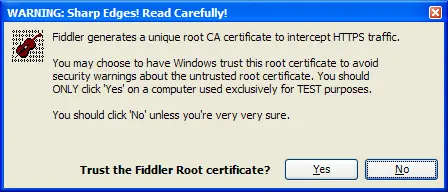
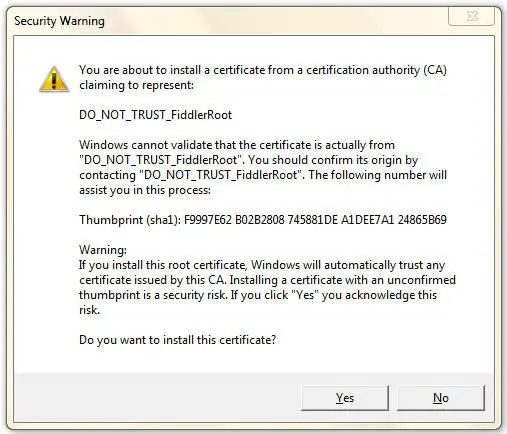
Click “Yes” and it’s set.
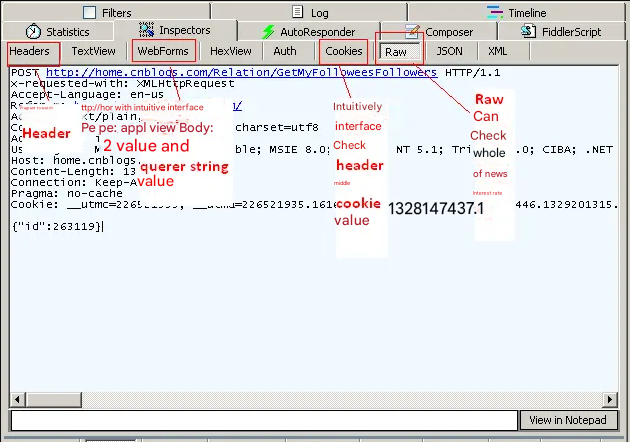
1.5 Fiddler’s Basic Interface
Take a look at Fiddler’s basic interface
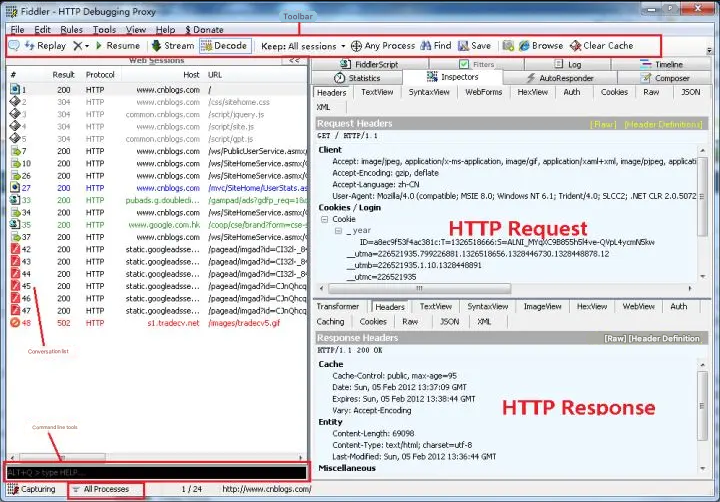
There are many Request or Response messages under the Inspectors tab. The Raw Tab can view the complete message, and the Headers tab only views the header in the message. As shown below
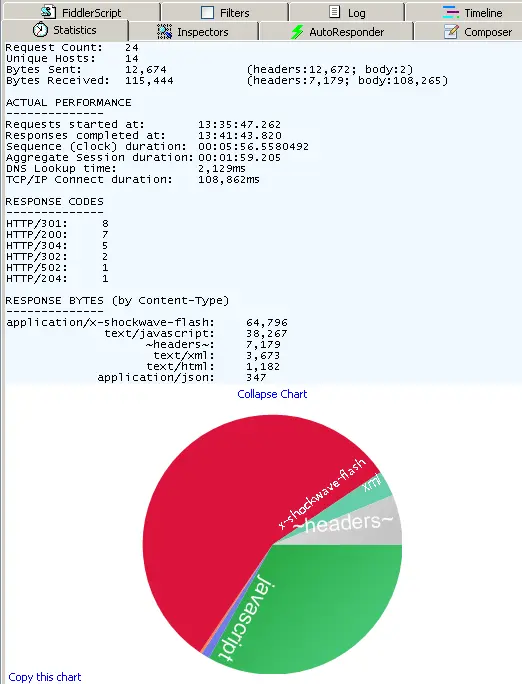
1.6 Fiddler’s HTTP Statistics View
By displaying all HTTP traffic, Fiddler can easily show you which files generated the page you are currently requesting. Using the Statistics tab, users can select multiple sessions to get the total statistics of these sessions, such as multiple requests and the number of bytes transferred.
Select the first request and the last request to get the total time consumed by the entire page load. From the bar chart, you can also distinguish which requests take the longest time, so as to optimize the access speed of the page.
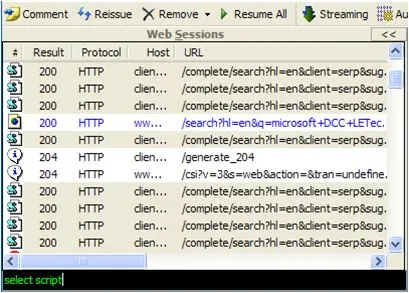
1.7 Use of QuickExec command line
There is a command line tool called QuickExec in the lower left corner of Fiddler that allows you to enter commands directly.
Common commands are:
help Open the official usage page, all commands will be listed
cls clears the screen (Ctrl+x can also clear the screen)
select command to select session
.png is used to select images with png suffix
BPU intercepts the request
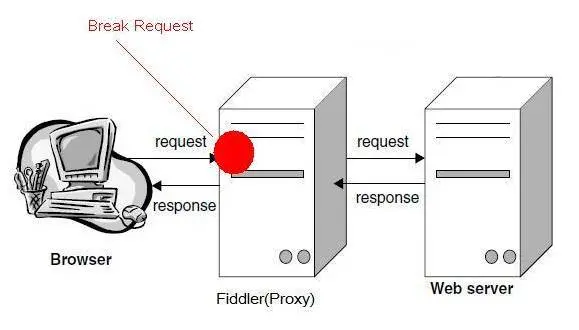
1.8 Set breakpoints in Fiddler to modify Request
The most powerful feature of Fiddler is setting breakpoints. After setting breakpoints, you can modify any information in httpRequest including host, cookies or data in the form. There are two ways to set breakpoints:
The first method: Open Fiddler and click Rules-> Automatic Breakpoint -> Before Requests (this method will interrupt all sessions)
How to disable the command? Click Rules-> Automatic Breakpoint -> Disabled
Second method: Enter the command in the command line: bpu http://www.baidu.com (this method will only interrupt http://www.baidu.com )
How to delete the command? Enter the command bpu in the command line
2. Wireshark
Wireshark is another packet capture tool, which is more powerful than Fiddler and has more messages. You may ask: Why do we need Wireshark when we have Fiddler? Here is an explanation. During the test, it was found that some packets were not captured when Fiddler was used to capture packets. For example, when verifying anti-cheating information, the anti-cheating pingback information was not captured by Fiddler, but was captured by Wireshark. There is another situation, that is, when verifying CNA, if you use Fiddler to capture packets first, if you do not plant CNA, you will never have CNA in the future, which is very strange. The solution is to uninstall the package and reinstall it, and use Wireshark to capture the package for the first time.
2.1 Wireshark Advantages:
1. Powerful protocol analysis capability, full decoding from layer 1 to layer 7, which is particularly helpful for studying protocol details.
2. For https encrypted traffic, as long as the browser’s session key is automatically imported into Wireshark, Wireshark can automatically decrypt https traffic.
2.2 Wireshark shortcomings:
Although you can customize the filter list, in order to capture a specific TCP Flow/Session traffic, you need to write a long filter list, which is not friendly to beginners.
2.3 Operation examples:
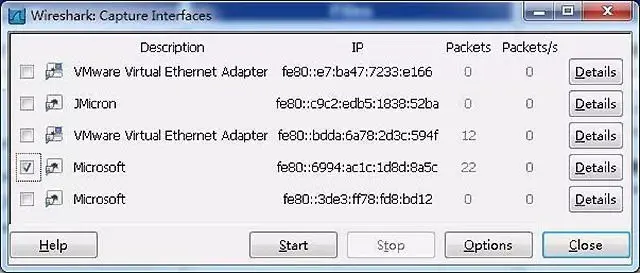
Wireshark captures the network packets of a certain network card on the machine. When your machine has multiple network cards, you need to select one.
Click Caputre->Interfaces.. The following dialog box will appear, select the correct network card. Then click the “Start” button to start capturing packets:
2.3.1 WireShark interface
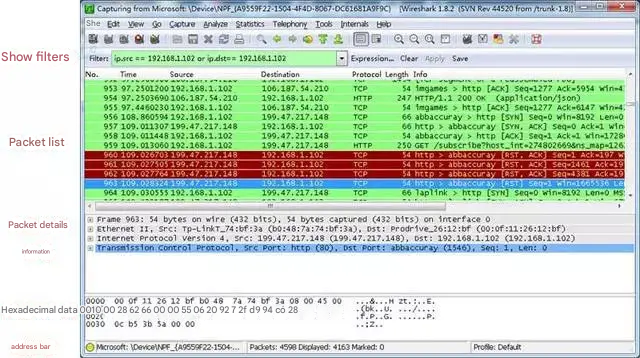
1. Display Filter, used for filtering;
2. Packet List Pane: displays the captured packets, including source address, destination address, and port number;
3. Packet Details Pane, which displays the fields in the packet;
4. Dissector Pane (hexadecimal data);
5. Miscellanous (address bar, miscellaneous).
2.3.2 Wireshark Display Filtering
It is very important to use filters. When beginners use Wireshark, they will get a lot of redundant information. It is difficult to find the part they need in thousands or even tens of thousands of records. It makes you confused. Filters will help us quickly find the information we need in a large amount of data.
There are two types of filters:
1. One is the display filter, which is the one on the main interface, used to find the required records in the captured records
2. One is the capture filter, which is used to filter the captured packets to avoid capturing too many records. Set it in Capture -> Capture Filters.
2.3.3 Save Filter
In the Filter column, fill in the Filter expression, click the Save button, and give it a name. For example, “Filter 102”, and there will be a “Filter 102” button in the Filter column.
2.3.4 Rules for filtering expressions
Expression rules
1. Protocol filtering, such as TCP, only displays the TCP protocol.
2. IP Filtering
For example, ip.src ==192.168.1.102 shows that the source address is 192.168.1.102, ip.dst==192.168.1.102, and the destination address is 192.168.1.102.
3. Port filtering
tcp.port ==80, port 80
tcp.srcport == 80, only displays TCP protocol with port 80.
4.Http mode filtering
http.request.method==”GET”, only displays HTTP GET method.
5. Logical operators are AND/OR
2.3.5 Packet List Pane
The packet list panel shows the packet number, timestamp, source address, destination address, protocol, length, and packet information. You can see that different protocols are displayed in different colors. You can also modify the coloring rules, View -> Coloring Rules.
2.3.6 Packet Details Pane
This panel is the most important one for us, used to view each field in the protocol. Each line of information is
Frame: Overview of the data frame at the physical layer
Ethernet II: Data link layer Ethernet frame header information
Internet Protocol Version 4: Internet layer IP packet header information
Transmission Control Protocol: The data segment header information of the transport layer T, here is TCP
Hypertext Transfer Protocol: Application layer information, here is the HTTP protocol
2.3.7 Wireshark and the corresponding OSI seven-layer model
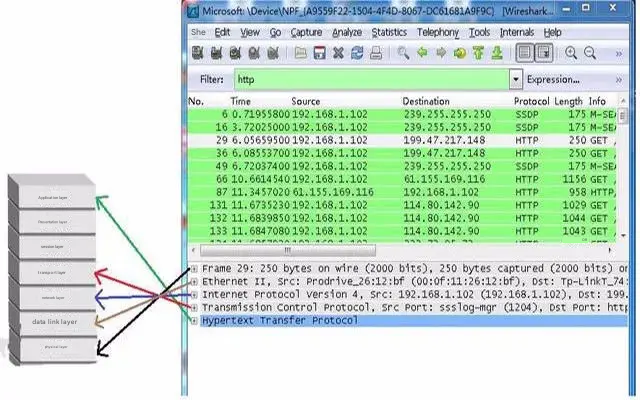
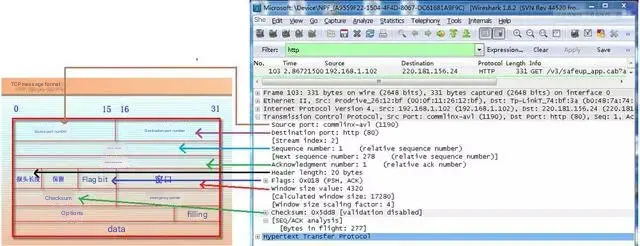
2.3.8 Specific content of TCP packet
From the figure below, you can see each field in the TCP packet captured by Wireshark.
3. Summarize
In general, the two packet capture software have their own advantages and disadvantages. The key to choosing lies in what our needs are. Of course, for software testing practitioners, both software are very necessary to learn~



