
Sax2 IDS
Prevent hacker & virus attacks, Securing your network & business !
Sax2 IDS is an advanced intrusion detection system designed to monitor and identify abnormal or malicious activities within computer networks and systems. Its primary purpose is to detect and respond to security threats promptly. Sax2 IDS is capable of identifying a wide range of attacks, including network scanning, malware, denial-of-service attacks, and various other security threats.
Sax2 IDS is a sophisticated intrusion detection and prevention system (IPS) designed to detect and respond to network intrusions and attacks. It excels in real-time packet capture, continuous network monitoring, advanced protocol analysis, and automatic expert detection.
With comprehensive visibility into network operations, Sax2 IDS simplifies the process of identifying and addressing network security issues. It helps detect vulnerabilities, identify potential threats, monitor for security policy violations, and uncover signs of attacks. Ultimately, Sax2 IDS can intercept and block malicious connections.
The system provides detailed intrusion analysis reports, including information on events, attack types, source and destination addresses, and various cross-sectional and composite reports. Sax2 IDS also supports customizable time ranges, allowing administrators to monitor and assess network security with flexibility.
Key Features of Sax2 Intrusion Detection System:
- Intrusion Detection and Prevention:
- Detects a wide range of complex attacks, such as pre-attack detection, password guessing, denial of service (DoS/DDoS), buffer overflow, CGI/WWW attacks, vulnerabilities in Windows and Unix, unauthorized access, SQL injection, worms, Trojans, ARP spoofing, and more.
- Proactively prevents harmful activities to protect the entire network.
- Real-Time Alerts and Response:
- Offers multiple response modes, including console messages, logs, email notifications, real-time connection cuts, and flexible logging options.
- Stable Performance:
- Operates continuously 24/7/365 with reliable performance.
- Real-Time Monitoring, Analysis, and Alerts:
- Provides real-time network communication monitoring, analysis, and alerts to safeguard network security.
- Extensive Data Storage:
- Supports various databases, such as SQL Server and Access, for flexible data storage.
- Comprehensive Reporting:
- Generates a wide range of reports, making it easy for administrators to monitor attacks and evaluate network security.
- Customizable Security Policies:
- Allows IT professionals to tailor security policies to enhance the accuracy of intrusion detection based on the specific network environment.
- Network-Based Monitoring:
- Operates as a network-based IDS, capturing, filtering, and analyzing traffic at key network locations. A single Sax2 IDS monitor can oversee all incoming and outgoing traffic for the entire site without requiring client software on individual computers.
Additional Features:
- Name Table:
- Facilitates the creation or modification of aliases for addresses, ports, and protocols, and allows the customization of text colors for better readability.
- Multi-Adapter Support:
- Captures traffic across multiple adapters installed on the local machine.
- In-Depth Packet Decoding:
- Provides detailed information on packet decoding.
- Conversation and Packet Stream Monitoring:
- Monitors all network conversations and reconstructs packet streams.
- Event Logging:
- Records network activities and sensitive events, including web browsing, email transmissions, FTP transfers, and instant messaging, to help administrators identify potential threats.
Who Can Benefit from Sax2 Intrusion Detection System?
Sax2 IDS is ideal for users and organizations that require robust network monitoring without the need for client software installation on individual workstations. It is especially beneficial for:
- Organizations aiming to prevent hacker attacks and safeguard their networks and business operations from internal and external threats.
- Businesses that need to monitor and log websites visited by users to enforce security policies.
- Companies requiring oversight of corporate communications, including email and instant messaging, to protect sensitive data.
Protect your network and business with Sax2 Intrusion Detection System—a comprehensive solution designed to detect, prevent, and respond to a wide range of network security threats.
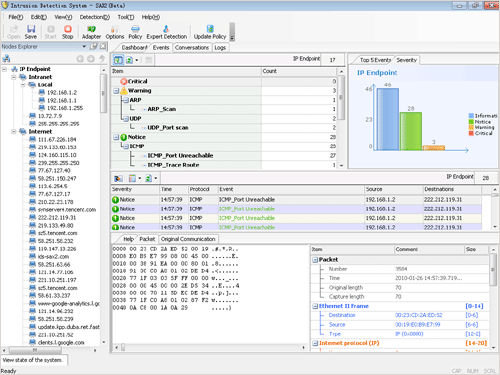
Concise Interface
The main interface of Sax2 consists of a labeled window and two floating windows, allowing users to switch easily between different windows. Each window has a Vista-style design that is concise and modern.
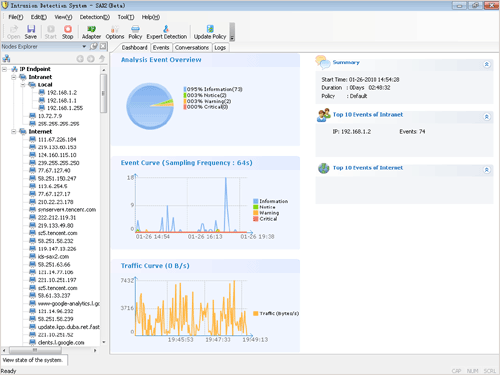
Dashboard
The visual Dashboard provides a comprehensive view of the attacks on your network, including the level, amount, and distribution of risk, as well as trends in attacks and network traffic. It also displays the Top 10 internal and external attacks.
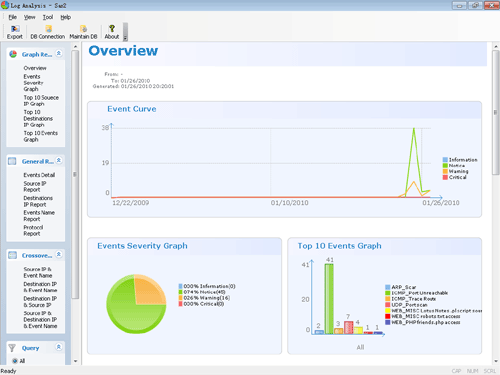
Log Analysis
Sax2 offers enhanced powerful and user-friendly log analysis. Administrators can use the log analysis to view detailed information on network attacks.
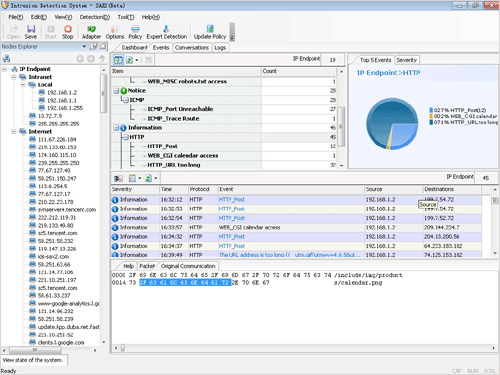
Event View
The main function of the Invasion view is to focus on invasion checking. The view consists of two parts, the Invasion event pane and the Invasion log pane. The Invasion event pane provides statistics on the current network’s invasion classification, and the Invasion log pane shows part of the invasion log. When you choose a different entry in the Statistics Pane, it displays the incident related to the invasion and shows all invasions by default.
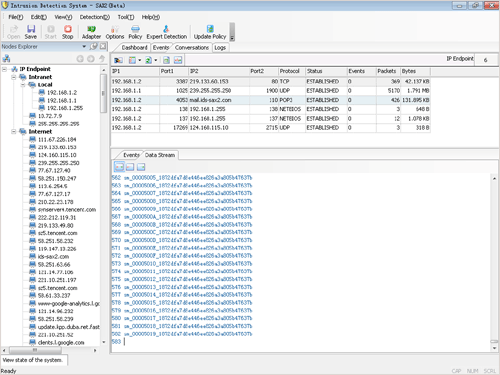
Conversation View
The conversation view is a significant feature of Sax2, composed of two sections. The top section displays the current network communication or the end of the communication, including IP, TCP, UDP, and ICMP. By reviewing each conversation, we can determine the source and destination address, data packet count, size, and other relevant information. With this data, we can identify the current state of a conversation.
The bottom section consists of the intrusion log and data stream table window. When selecting a conversation from the conversations list, it displays the corresponding intrusion incidents by default. This feature allows us to view all the invasions related to a specific conversation.
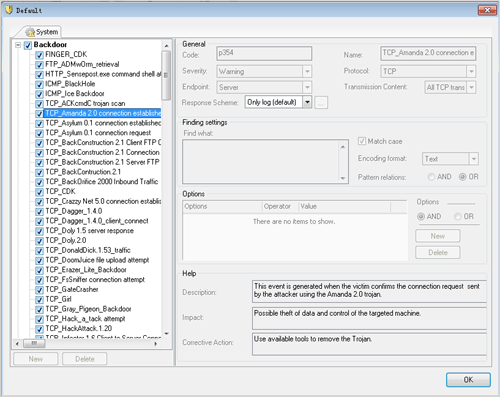
Knowledge Base Management
Sax2 provides more than 1,500 of the security policies by default, Also, according to their own needs we can customize any security Policy, targeting intrusion detection system which is the most suitable for their own.
Software Systems
OS:
- Windows Server 2012/2012 R2/2016/2019 (64-bit)
- Windows 7 SP1 (KB3033929) (64-bit)
- Windows 8.1 (64-bit)
- Windows 10 (64-bit)
- Windows 11 (64-bit)
Relied Browser:
- Internet Explorer 8.0 or higher
Hardware Requirements
Minimum Requirements:
- CPU: P4 2.8GHz
- RAM: 4GB
- Internet Explorer 8.0
Recommended System:
- CPU: Intel Core Duo 3.2GHz
- RAM: 8GB or more
- Internet Explorer 8.0 or higher
Notes:
- You are required to have the “Administrator” level privileges on supported operating system in order to load and unload device drivers, or to select a network adapter for using the program to capture packets.

