Next, we will introduce the top ten most popular tools for WEP/WPA/WPA2 cracking currently available. These tools can help us test for potential security issues in wireless network environments.
Official website: [See original text for link]
Tutorial: [See original text for link]
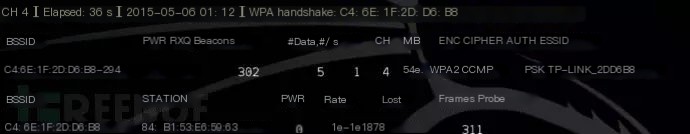
Aircrack is currently the most popular tool in the field of WEP/WPA/WPA2 cracking. The Aircrack-ng suite includes tools that can capture data packets and handshake packets, generate communication data, or perform brute force attacks and dictionary attacks. Aircrack-ng is an all-in-one integrated suite that roughly includes the following tools:
– Aircrack-ng: Wireless password cracking- Aireplay: Generate network data, de-authenticate clients- Airodump-ng: Data packet capture- Airbase-ng: Set up a fake access point
Aircrack-ng can run on Linux, Windows, and macOS, and it is included by default in Kali Linux. If you plan to use this tool, you also need to ensure that your wireless card supports packet injection.
Official website: [See original text for link]
Tutorial: [See original text for link]
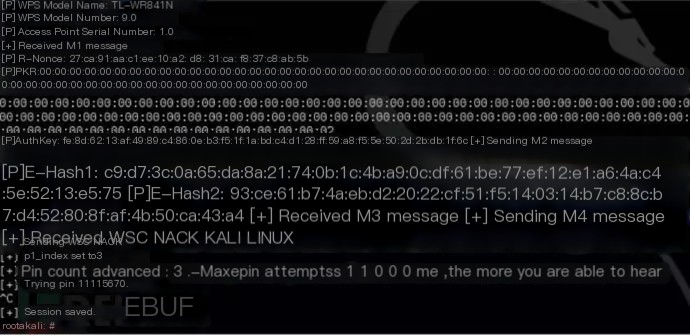
Ranked second is Reaver, another popular wireless network attack tool, mainly targeting WPS vulnerabilities. Reaver performs brute force attacks on the registration PIN of WiFi Protected Setup (WPS) and attempts to recover WPA/WPA2 passwords. Since many router manufacturers and ISPs enable WPS by default, many routers on the market cannot withstand this attack.
When using Reaver, the signal of the wireless router must be strong enough. On average, Reaver can crack the target router’s password within 4-10 hours, but the specific time depends on the type of access point, signal strength, and the PIN itself. From a probabilistic and statistical perspective, you have a 50% chance of cracking the target router’s PIN in half the time.
Official website: [See original text for link]
Tutorial: [See original text for link]
Modified Reaver+Pixie: [See original text for link]
PixieWPS is a new penetration tool added to Kali Linux specifically targeting WPS vulnerabilities. Developed in C language, PixieWPS can be used for offline brute force attacks on WPS PINs. The technique it uses is called a pixie dust attack. Note that PixieWPS requires a modified version of Reaver or Wifite to function properly. Due to its rapid rise in popularity, it ranks third on our list.
Official website: [See original text for link]
Wifite is an automated tool capable of attacking multiple wireless encryption methods (WEP/WPA/WPA2 and WPS). Before running, Wifite requires a few parameters, and it will automatically complete all tasks for us. It can capture WPA handshake packets, automate client de-authentication, perform MAC address spoofing, and crack WiFi passwords.

Official website: [See original text for link]
Tutorial: [See original text for link]
Online courses: [Wireshark Crash Course], [Wireshark Tutorial – Get Wireshark Certification]
Wireshark is considered the best network protocol analysis tool available today. With Wireshark, you can deeply analyze a network and obtain as much information as possible. Wireshark can capture network packets in real-time, perform in-depth analysis of hundreds of protocols, and browse and filter packets. Note that Wireshark is a cross-platform tool.
Kali Linux includes Wireshark by default, but Windows and macOS users can also use it. If you want to use some of Wireshark’s special features, you need a WiFi adapter that supports monitor mode.
Official website: [See original text for link]
Tutorial: [See original text for link]
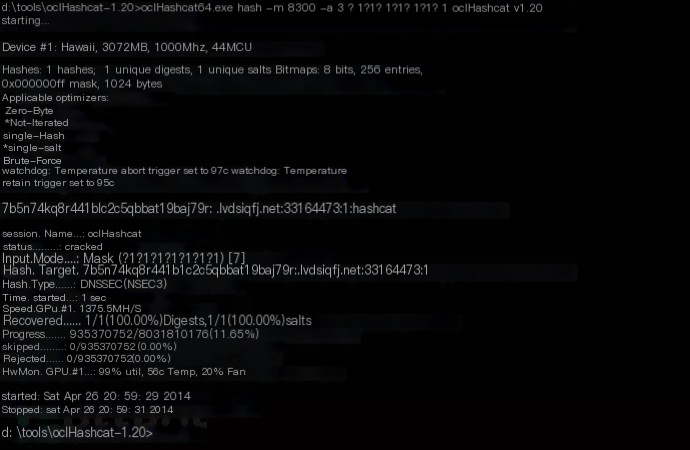
oclHashcat is not a dedicated WiFi intrusion tool, nor is it included in Kali Linux by default, but it can perform high-speed brute force attacks and dictionary attacks (using GPU to run dictionaries) on captured handshake packets. After capturing handshake packets with Aircrack-ng or other tools, we can use GPU and oclHashcat to crack WiFi passwords, and the cracking speed of GPU+oclHashcat is much faster than CPU+Aircrack-ng.
oclHashcat is available for Windows and Linux, with versions specifically for AMD and Nvidia graphics cards.
Official website: [See original text for link]
Fern Wifi Cracker is a security auditing and attack tool for wireless networks, written in Python. It is the only tool among the top ten wireless attack tools with a graphical user interface. Fern Wifi Cracker can crack WEP, WPA, and WPS keys and includes components capable of performing MiTM (Man-in-the-Middle) attacks.
Official website: [See original text for link]
Tutorial: [See original text for link]
When attackers perform brute force attacks on WPS PINs, many access points will lock themselves to ensure router security. Wash is a tool that can determine whether the target access point has WPS enabled. After several attempts with Reaver, you can use Wash to check if the access point has locked WPS.
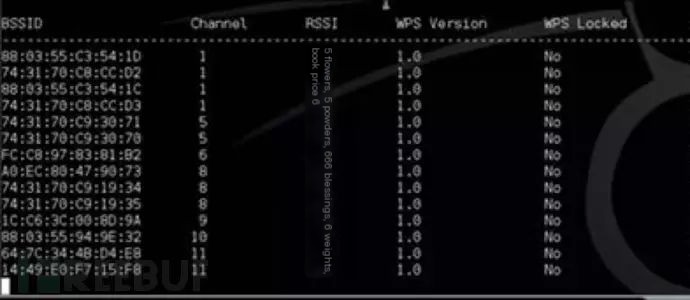
Official website: [See original text for link]
Tutorial: [See original text for link]
Crunch can be used to generate custom dictionaries, and the generated dictionaries can be used for dictionary attacks. Since the success rate of dictionary attacks depends on the quality of the dictionary used, we inevitably need to generate dictionaries according to our needs.
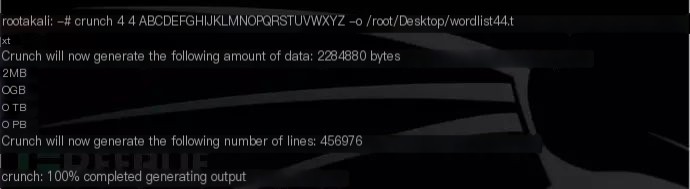
Official website: [See original text for link]
Tutorial: [See original text for link]
In fact, Macchanger is a small tool that can change your device’s MAC address to a random value, or you can modify it to the data you want. To avoid target devices using MAC address filtering, modifying the MAC address is very important for WiFi attacks.
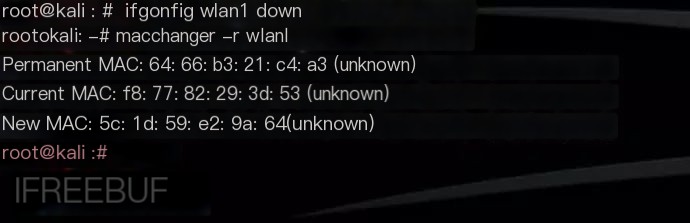
I hope the top ten popular WiFi attack tools summarized in this article can provide some help. As it stands, there is still much room for improvement in the security of wireless networks, and this improvement requires the entire community to contribute their efforts.



