The text should include the keyword “Traffic hijacking.”
Traffic hijacking, an age-old attack, has resurfaced and is causing quite a stir recently. Numerous well-known brands of routers have been found to have security vulnerabilities, drawing significant media attention. As long as users haven’t changed the default password, just opening a webpage or post can result in the router settings being surreptitiously altered. Overnight, the internet has become perilously unstable.
The attacks remain the same, and the reports are still the same monotonous expert warnings, making everyone numb to them. People have long been accustomed to the various hijacks by service providers and the frequent pop-up ads, leaving them helpless. For so many years, nothing has really been lost as a consequence, so everyone just turns a blind eye.
In fact, just being hijacked by an ISP is relatively fortunate. Compared to mysterious hackers lurking in the shadows, ISPs, as public enterprises, are still bound by law. While ad hijacking is unscrupulous, it still has its limits. Look, they at least let you see the ads, which serves as a reminder that your current network is at risk of being hijacked, so stay vigilant. On the contrary, when everything seems calm and nothing appears unusual, there might already be a massive spy lurking in the network, ready to pounce at any moment—not just to display ads, but to steal finances and account credentials!
Am I at risk of being hijacked?
Many people hold an incorrect view: only those with weak security awareness will get hacked. As long as I have installed various professional firewalls, keep system patches up to date, and all of my passwords are complex, hijacking definitely won’t happen to me.
Indeed, those with strong security awareness are less likely to be breached, but that only applies to traditional viruses and trojans. When it comes to traffic hijacking, almost everyone is equally vulnerable. Network security differs from traditional system security; a network is an amalgamation of various hardware devices, where the “weakest link” effect is particularly pronounced. Even if you have a robust system, encountering a poorly secured device can instantly lower your security level. With the rising popularity of affordable mini routers, which handle various online transactions, can you truly trust their use?
Even if you believe that systems and devices are absolutely reliable, can you really rest easy? In fact, there aren’t many problematic devices, but issues still frequently arise. Is there some flaw here? That’s right, something crucial is missing: the network environment.
In an online environment where hackers may be lurking, even with sufficiently advanced expertise, it’s still hard to evade them. When the enemy is hidden and we are exposed, a slight oversight can lead to falling into their trap.
Certainly, flies don’t land on seamless eggs. What vulnerabilities cause cracks in your network environment? There are too many to count, as attack methods have been numerous throughout history. You can even create one tailored to your specific environment.
Reflecting on hijacking attempts we have encountered.
Ancient Times:
Hub sniffing, MAC spoofing, MAC flushing, ARP attack, DHCP phishing, DNS hijacking, CDN intrusionMedieval:
Router weak passwords, Router CSRF, PPPoE, Phishing, Honeypot, ProxyIndustrial Era:
Weak WiFi Password
WiFi Fake Hotspot
WiFi Forced Disconnection
WLAN Base Station PhishingHub Sniffing
Hubs as devices have long since vanished, and even ten years ago, they were rarely used. As an early network device, their only function was to broadcast data packets: to send packets received on one interface to all other interfaces. Not to mention the incredibly limited bandwidth, just this forwarding rule was quite unreasonable. Anyone could receive the data from the entire network environment, so privacy and security were essentially non-existent.
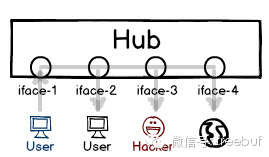
Packet sniffers became the pinnacle tool of that era. Once the filters were configured, it didn’t take long to capture various plaintext data, while users had no effective countermeasures.
Preventive Measures: If you’re still using it, throw it away immediately.
The only current use for this type of device is in passive sniffing. By exploiting the characteristics of broadcast, it becomes very convenient to analyze the communication of other devices, such as capturing data packets from a set-top box without affecting normal communication.
MAC Spoofing
The emergence of switches has gradually phased out hubs. Switches bind MAC addresses to interfaces, and data packets are ultimately sent to a single terminal. Therefore, as long as the MAC address corresponding to the interface is configured in advance, it is theoretically very secure.
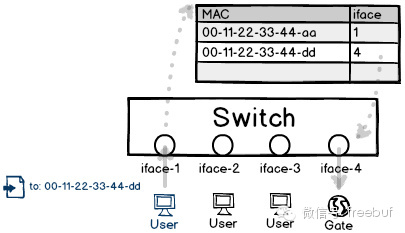
However, very few people do this, as most opt for convenience and directly use the device’s default mode—auto-learning. The device automatically associates the source address of a packet with the interface from which the packet is sent.
However, this kind of learning is not intelligent and is even overly rigid, treating any hearsay as truth. It’s very easy for a user to send a packet with a custom source MAC address, making switches very easy targets for deception. By simply spoofing a source address, one can associate that address with their own interface to intercept the victim’s traffic.
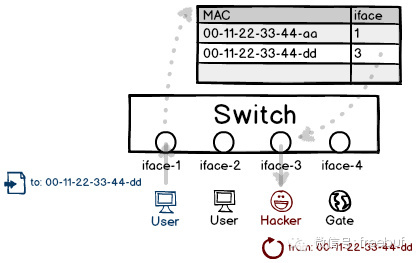
However, the victim subsequently sends another packet, and the binding relationship returns to normal. Therefore, the more frequently a packet is sent, the greater the likelihood of winning the competition for the right to receive this MAC address. If the gateway address is spoofed, the switch mistakenly thinks that the gateway’s cable is plugged into your port, and outbound traffic in the network environment instantly routes to your location.
Of course, unless you have alternative outbound channels to proxy the stolen data out; otherwise, forget about forwarding it back to the true gateway that you’ve taken down. The hijacked users won’t be able to access the external network either. Therefore, this tactic isn’t highly hazardous, but it is extremely disruptive, capable of causing an instant collective network outage.
Preventive Measures: For networks with stationary machines, try to bind MAC addresses with interfaces. It seems that most internet cafes have already bound MAC addresses and interfaces, which greatly enhances link layer security. Additionally, for independent subnet segments, try to use VLANs to avoid overly large broadcast domains.
In university, I’ve seen networks with over a thousand devices that don’t even segment VLANs. With just one loopback cable, you can take down the entire network.
MAC Flushing
Previously discussed were the forwarding differences between hubs and switches. If a switch encounters a MAC address that it has not yet learned, where will it send the packet? To prevent packet loss, it will have to broadcast to all interfaces.
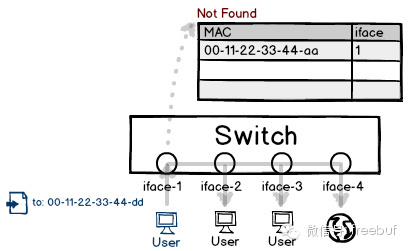
If the switch’s learning function can be disabled, it degrades into a hub. Given the limited hardware configuration of switches, it is evidently impossible to indefinitely record address entries. By continually forging non-repeating source addresses, the switch’s record table quickly fills up, potentially overwriting existing learning records. As a result, users’ data packets cannot be properly forwarded and are instead broadcasted to all interfaces.
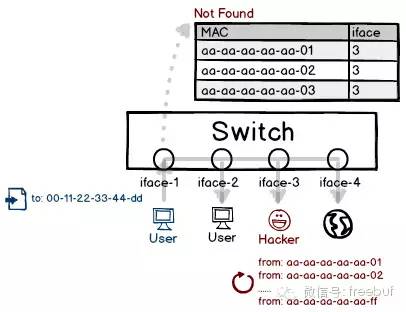
Preventive Measure: It is still advisable to bind the MAC address with the interface. Once bound, the interface will only allow communication from a fixed source address, thereby rendering any spoofed addresses ineffective. Of course, higher-end switches come with certain policies that prevent a single interface from being associated with too many MAC addresses.
I once tried this at home, capturing the internet traffic of users within the community. However, the packets were sent out too quickly, at ~150,000 packets per second. More critically, the packets were sent to the wrong target address, specifically, to the metropolitan area network access server, which resulted in the network for the entire community being cut off for half a day by the staff. Therefore, it’s crucial to select a target MAC address that is actually present within the VLAN, to avoid generating a massive data storm.
ARP Spoofing Attack
This type of attack is so well-known that almost everyone, even those who don’t understand computers, knows to install an ARP firewall for safety. The magnitude of its threat is evident.
To put it simply, ARP is a protocol that broadcasts a request to find the MAC address corresponding to a specific IP address, and the person using that IP address replies. Once you know the MAC address associated with the IP address, communication can occur on the link layer (as communication on the link layer happens exclusively via MAC addresses). If someone impersonates the legitimate device and responds before the actual device, the false answer becomes dominant. Consequently, the IP is resolved to an incorrect address, and all subsequent communication is hijacked.
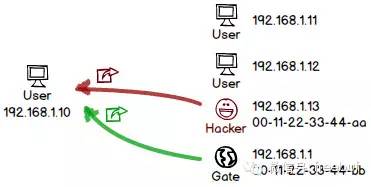
In fact, early systems had an even more serious bug: sending an ARP reply packet directly to a user, even if the counterpart never requested it. The system would still accept this reply and preemptively save the records it contained. This type of cache-based poisoning further increased the success rate of hijacking attempts.
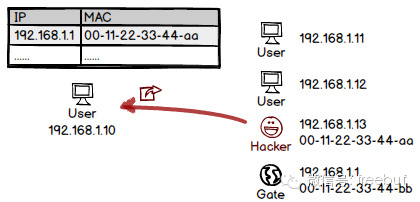
Preventive Measures: Due to the prevalence of this type of attack, most routers are now equipped with anti-ARP attack features. There are also countless ARP firewalls available for clients, seemingly becoming a standard feature of security software. Naturally, systems also support the forced binding of IP and MAC addresses, which can be utilized when necessary.
Many tutorials demonstrate using Wireshark; however, back in the day, there was a software called Iris that was very user-friendly. It allowed users to modify packets and resend them, making it quite effortless to understand various attack principles. Unfortunately, it hasn’t been updated for many years and doesn’t support 64-bit systems.
DHCP Phishing
In reality, not everyone is able to configure network parameters, or for the sake of convenience, some prefer the network system to configure itself automatically. For this purpose, DHCP service was developed.
Without configuring an IP address, gateway, or DNS, navigating the network is nearly impossible. Thus, the first step is to obtain these from DHCP. However, without an IP address, how does communication happen? Clearly, it can only send to the broadcast address (255.255.255.255), using an invalid IP address (0.0.0.0) temporarily. (In fact, link-layer communication only requires a MAC address, as the IP address is part of the network layer. However, DHCP uses the UDP protocol due to certain specific needs.)
Because it is broadcast, all users within the internal network environment can receive it. If there are multiple DHCP servers, each will respond separately; the user will then select the one received first. The rules are so straightforward that users have no other choice.
If a hacker also enables a DHCP service within the internal network, the response packet that the user receives is likely to be sent by the hacker. At this point, the user’s network configuration is completely left to chance, making it hard to avoid being hijacked.
Preventative Measures: If you are using a wired connection, it’s best to configure it manually. Additionally, administrators should strictly control DHCP reply permissions, ensuring that only specific switch interfaces are authorized to send response packets.
Any question-and-answer format like this is at risk of impersonation. Many underlying principles are similar.
DNS Hijacking
Just as ARP resolves IP addresses to MAC addresses, DNS is responsible for resolving domain names to IP addresses. As a service at the network layer, it serves a broader user base and, naturally, faces significantly greater risks. If compromised, all users can suffer adverse effects. In recent years, major network incidents have been invariably linked to DNS.
Once hackers gain control of a DNS service, all domain name resolutions initiated by users can be covertly manipulated. They can redirect legitimate websites to the IP addresses of hacker-controlled servers and pre-enable HTTP proxies, making it nearly impossible for users to notice any anomalies while browsing. Meanwhile, hackers can intercept all traffic, gaining full access to various website account information.
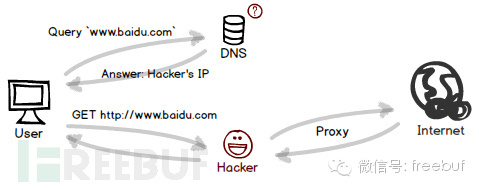
Due to the significance of DNS servers, they are typically subjected to high levels of security protection in practice, making it difficult to breach their systems. However, it might not necessarily require such a grand effort, as some DNS programs inherently have design flaws that allow hackers to control the direction of certain domain names. Among these, the most notorious is DNS cache poisoning.
Everyone may have noticed that with domain->IP->MAC->interface, any process involving dynamic queries introduces an additional layer of complexity, naturally increasing the risk. Flexibility and security are always in conflict.
Precaution: Manually setting certain authoritative DNS servers, such as 8.8.8.8 and 4.4.4.4, can be much more reliable.
DNS hijacking on public networks is rare, but DNS hijacking on home routers has become rampant. The router vulnerability reported initially often culminates in the modification of DNS addresses.
CDN Intrusion
Most people know that CDNs can accelerate content delivery, but many are unclear about the underlying principles. Essentially, a CDN is a form of DNS hijacking, albeit a benign one.
Unlike hackers who forcibly direct DNS to resolve domain names to their own phishing IPs, a CDN proactively works with DNS to resolve domain names to the nearest server. This server also runs an HTTP proxy, making users unaware of the CDN’s presence.
However, a CDN is not as greedy as a hacker, hijacking all user traffic. It only “hijacks” the user’s access to static resources. For resources previously accessed by a user, the CDN will directly respond from the local cache to the user, thereby significantly improving speed.
However, anywhere there is caching, there is great potential. Once a CDN server is compromised, the cached files on the hard drive are in imminent danger. Web pages might be injected with scripts, executable files can get infected, and a horde of zombies is about to emerge.
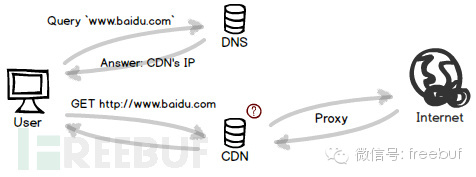
Preventive Measures: If you suspect that the service provider is unreliable, consider switching to a third-party DNS without acceleration features; this might prevent it from resolving to a CDN server.
Numerous CDNs operate in a dual-role manner; to save bandwidth, they often don’t follow the prescribed protocols. They fail to update even after the cache expiration time and sometimes ignore the query strings after the URL question mark, causing developers a great deal of frustration when dealing with resource updates.
Router Weak Password
As computer prices continue to drop to the point where people are considering buying a second one, the router market is also heating up accordingly.
However, due to the cumbersome setup and poor user experience, a considerable number of users still do not understand how to configure routers. 192.168.1.1 and admin/admin have almost become constants in domestic routers. How many times have these non-technical methods been used to access the router backend at internet cafes or libraries?
If someone messes with your router by restarting it or throttling the bandwidth, consider their actions relatively benign. However, it becomes a significant issue if the DNS settings of your router are altered! While public DNS hijacking typically doesn’t last long, DNS hijacking at the router level can go undetected for years.
In fact, there is no shortage of security-conscious users who also use default passwords. The reason is simple: today’s routers have two layers of protection—one is the WiFi connection password, and the other is the management password. Many people feel secure after setting a complex WiFi password, thinking, “If they can’t even connect to my network, how could they access the admin panel?”
I used to have this idea too but always felt something was off: what if another computer or phone at home gets infected and automatically tries to brute-force its way into the router’s admin panel using weak passwords? If the city gates have been captured, what use is a strong fortress wall?
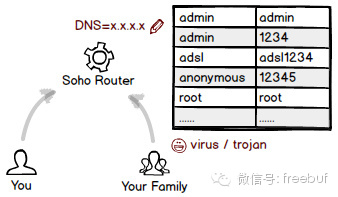
In fact, aside from altering DNS settings, hackers have an even more terrifying tactic: upgrading the router’s firmware by replacing it with a version that appears identical but contains embedded malicious software! Although this practice is not yet widespread, once it becomes common, a large number of routers could turn into Pandora’s box.
Preventive Measure: Do not underestimate the importance of your router’s password; it is actually more crucial than all your other account passwords.
If you don’t change the default password, not even divine intervention can save you.
**Router CSRF**
Returning to the beginning of this article, why do so many routers have this vulnerability? Perhaps it’s because the router developers overestimate the users, assuming that the vast majority of users have changed the default password, making CSRF nearly impossible to exploit.
In fact, the security awareness of domestic internet users far exceeds their expectations. Coupled with what was just mentioned, configuring only the WiFi password while neglecting the management password allows a malicious program to quietly access the router’s back-end.
I never expected this type of virus to actually emerge, and it’s even in a web version!
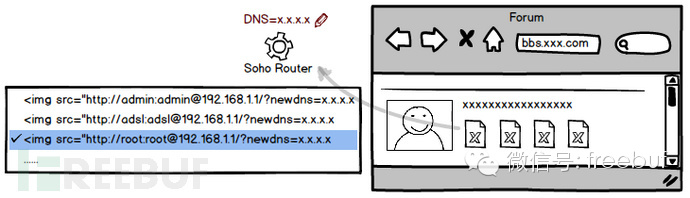
CSRF vulnerabilities render viruses and trojans unnecessary. A user simply visits a webpage or even a post, and the browser automatically initiates a request to the router to alter its configuration.
Due to the poor quality of web development in domestic routers, login is usually done using the insecure and unattractive HTTP 401 pop-up. This type of login allows automatic access by simply appending ‘username:password@’ in the URL, and even if the login fails, there won’t be any indication.
Precautionary Measures: Ensure that you closely safeguard your router’s password, and regularly check the configurations for any unauthorized changes.
If you have ever looked at the source code of a router’s page, you’ll find it is simply unbearable to behold, reminiscent of the Internet Explorer 5 era. Router chips are typically procured, and the kernel is often open source. Is their so-called “independent development” merely about creating those few pages?
PPPoE Phishing
Alright, let’s stop complaining about routers and discuss something that even the most advanced routers cannot avoid.
Apart from some large corporations or educational institutions that use dedicated lines for internet access, individuals or small organizations rarely opt for such premium packages. They typically resort to regular dial-up connections, whether it’s through telecom, China Netcom, or other service providers.
Many people hold the misconception that dial-up is the process of establishing a physical signal, and that without dialing, point-to-point communication is impossible. If this were true, how would account credentials be transmitted during the dialing process? Clearly, that’s not feasible. In reality, terminals are always capable of communicating with each other. However, without dialing, you cannot obtain parameters like IP, gateway, or session. Even if you forcefully send packets to the gateway, they may be received, but without an authenticated session, they will be ignored, so naturally, you cannot access the internet.
PPPoE is a term often encountered when dialing in. Point-to-Point Protocol over Ethernet, as the name suggests, is a point-to-point protocol: Users send their username and password for authentication to the terminal (BRAS) and receive an IP address, gateway address, and session information for internet access. Furthermore, the protocol is based on Ethernet, so even if the line itself is not Ethernet, there must be a way to encapsulate the data into it.
Traditional ADSL connects to the Internet via telephone lines, thus requiring a “modem” to modulate Ethernet data into telephone signals, which are ultimately transmitted through telecommunications switches. This type of equipment ensures that each household operates independently, preventing telephone signal interception.
However, the various emerging connections later on did not necessarily follow this pattern. Many broadband services advertised as “Gigabit to the building, 100 Mbps to the home” were essentially building multiple small local area networks (LANs) within neighborhoods and then merging them into a larger metropolitan area network (MAN). The so-called “100 Mbps” typically just meant that the cable dragged into your home was connected to a 100Mbps switch downstairs.
For those who have used Netcom, they know that 100Mbps bandwidth is not particularly fast, and in some southern regions, the internet speed can be as slow as a snail. However, during downloads, the speed can easily soar to several megabytes per second. This is where the role of the local area network (LAN) comes into play. If multiple people nearby are watching the same video, P2P can directly share the traffic within the network, significantly reducing the load on the nodes.
However, the entire neighborhood becoming a local area network is extremely insecure. Sometimes, even unreasonable VLAN segmentation leads to multiple neighborhoods forming a single intranet. If someone enables a DHCP service, other users can simply connect a cable to get online without even needing to dial in. Is it really a windfall? If you dare to indulge, you may end up in a hacker’s trap.
Of course, it’s not common to directly connect via Ethernet anymore; most people use routers for automatic dialing. However, they all use the same protocol—PPPoE, an extremely insecure protocol.
Similar to the DHCP protocol, PPPoE also utilizes broadcasting to discover available terminals, which means all users within the local area network of a residential community can receive it. The discovery packets continuously bubble up until they are received by terminals in the metropolitan area network, at which point they begin to respond.
If someone in the community privately sets up a PPPoE terminal service, it will obviously be detected first. The actual response packets are still being transmitted through the streets and alleys, and the user and hacker have already begun negotiating authentication.
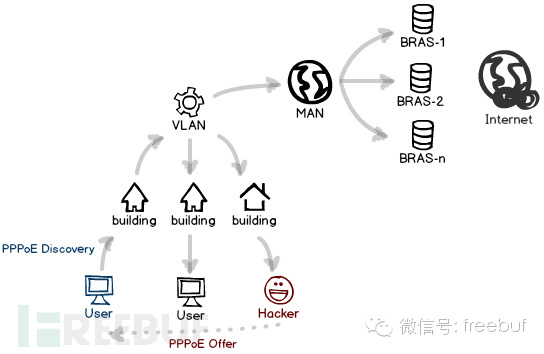
However, you might say that someone has to dial in for this to be effective, and nowadays everyone uses routers that remain connected indefinitely. If you don’t want to wait patiently, there’s a very simple method: initiate a collective disconnection.
I just mentioned that a short-circuited network cable can trigger a broadcast storm. However, this approach is overly aggressive and may even trigger abnormal traffic alarms. We can use a simpler and more effective method: MAC spoofing. By continuously forging the MAC address of the terminal server, you can siphon off data packets from all neighborhood users.
PPPoE employs a tunneling approach, encapsulating any data within its stack. By capturing any single packet from a user, you can obtain the session ID on the PPPoE stack. Then, by impersonating the terminal and sending a ‘disconnect’ command to the user, the user will promptly go offline. Using this method, you can force all users in a neighborhood to redial within minutes, enabling rapid execution of phishing schemes.
What’s even worse is that, in most cases, PPPoE transmits usernames and passwords in plaintext, which means it can also capture the authentication credentials sent by users.
Previously, I ranted about the university dormitory building having over 1000 machines without VLAN segmentation. So, I wrote a simple PPPoE simulator that can easily capture the internet accounts within the entire network environment. (It even supports a one-click prank feature to connect everyone at once, causing a collective offline event~)
Mitigation Measures: Due to the heavy reliance of PPPoE security on the physical layer, it is advisable to avoid installing broadband with Ethernet access whenever possible. Administrators should strictly limit PPPoE discovery response packets, allowing them only on specific interfaces, similar to DHCP. In reality, a BRAS server should not appear within a neighborhood network, so response packets should only emerge from the WAN port of the switch. This approach reduces the risk of phishing attacks.
PPPoE has another severe vulnerability: the session ID is only 2 bytes, allowing for a maximum of 65,536 possible values. By constructing a “disconnect” request packet in advance and iteratively traversing the session ID, you can disconnect all users of a particular terminal server. If you collect the addresses of all terminal servers beforehand, you could initiate a network outage across the entire city. This vulnerability should have been fixed long ago by simply binding the relationship. Additionally, a small script could disconnect networks across various counties and cities, illustrating that terminal deployments shouldn’t be overly centralized.
Honeypot Proxy
Due to well-known reasons, the demand for proxies in a certain country remains high. Whether they are anonymous, transparent, or highly secure, as long as they facilitate accessing outside, they are considered good.
VPN services require usernames, passwords, and various authentications, making mid-stream interception nearly impossible. Hackers exploit people’s naiveté by focusing on proxies instead. Indeed, encrypted data is challenging to intercept mid-transit, but it ultimately needs to be decrypted on the server-side to be rendered into its original form, doesn’t it? If you’re careless and connect to a free VPN, you might just end up on a hacker’s pirate ship.
Compared to an HTTP proxy that only affects certain functions, a VPN routes all of the system’s traffic through a tunnel. Applications remain unaware of this and continue to send some critical data outside, which could ultimately be intercepted by hackers.
Precaution: Do not be tempted by small gains and use proxies that advertise as free. There’s no such thing as a free lunch.
Many honeypot proxies are not necessarily set up by hackers, but you know who.
Weak WiFi Passwords
As the Internet extended to mobile devices, cables became a major burden, and wireless networks gradually caught people’s attention. Nowadays, due to the affordability and convenience of wireless technology, it is applied to almost all convenient devices. Everything is no longer restricted, enabling people to access the Internet anytime and anywhere, which was unimaginable in the past; hackers can also launch attacks anytime and anywhere, which they once only dreamed of.
However the methods of internet access may change, Ethernet has always been the core of networking. As previously mentioned with ADSL, even though the medium is a telephone line, the final demodulated data is still Ethernet. The same applies to WiFi, regardless of how radio waves propagate, ultimately only the restoration of standard Ethernet packets can be routed.
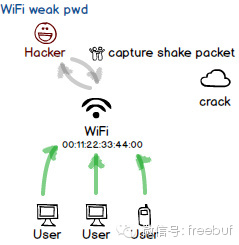
A wireless network resembles an invisible gigantic hub; without any physical transmission medium, everyone nearby can listen to the data signals, and with specialized equipment, they can be captured from even further away. Without a robust encryption method to encapsulate the data, there would be no privacy at all.
After experiencing various encryption breaches, WPA2 has now become the standard encryption algorithm for wireless networks. Attempting to connect by repeatedly trying weak passwords, like traditional brute-force attacks, would be highly inefficient.
Unlike dial-up, WiFi users first need to “associate” with the hotspot to establish a physical channel. Similar to PPPoE, WiFi can also communicate before authentication, and it uses plaintext data—although this applies only to authentication packets, as the actual password obviously doesn’t appear within them. After all, its purpose is entirely different from that of dial-up: one aims to encrypt all traffic thereafter, while the latter merely verifies whether you have authorization for internet access.
With traditional sniffing tools, it is convenient to capture these handshake communication packets. Although the password cannot be uncovered, it contains data related to key initialization. Using professional WPA2 cracking tools along with extensive password dictionaries, a considerable portion of wireless networks can be cracked within an acceptable timeframe.
For many people, the wireless password is their first and only line of defense. Once connected, you can easily access the router’s backend without any unexpected issues, allowing you to control the entire internal network traffic.
Preventive Measure: The simplest yet most effective method is to add some special characters to your password.
If we flash his router with firmware that can automatically hack into other wireless networks, automatically access the back end after cracking, and upgrade its firmware… a deluge of router malware will explode.
WiFi Hotspot Phishing
The text basically mentioned how to crack wireless passwords. But if the password is already known, how would one initiate an intrusion?
Such scenarios are quite common. In places like shopping malls, restaurants, and hotels, even if the Wi-Fi network is password-protected, people can usually find it on the wall or on a card, making it semi-public. Alternatively, if you’ve managed to crack a neighbor’s Wi-Fi password but cannot access the router’s backend, what should you do next?
Today, increasingly intelligent wireless devices are already well-equipped to defend against primitive intrusions such as MAC spoofing and ARP attacks. Therefore, a more advanced and covert method is needed, capable of bypassing network devices to directly initiate point-to-point attacks.
Users who have connected to the Wi-Fi in large companies or shopping malls may notice that the network is available indoors no matter where they go, with a strong signal even when moving from the first floor to the fifth. However, at home, the signal diminishes significantly when obstructed by walls. Is it because there is an especially powerful hotspot turned on? Yet, the signal is not detectable outside the building. In fact, it’s not hard to notice many dish-like objects attached to each floor’s ceiling. That’s right, these devices distributed throughout the building provide coverage for the entire wireless network, reducing signal dead zones.
However, even though there are numerous hotspots available, only a few are shown in the search list. This occurs because they all share the same hotspot name (SSID), and clients typically combine hotspots with identical names into a single entry. When connecting, the system will choose the one with the strongest signal. If these hotspots also have the same authentication method, connecting to any of them shouldn’t pose a problem.
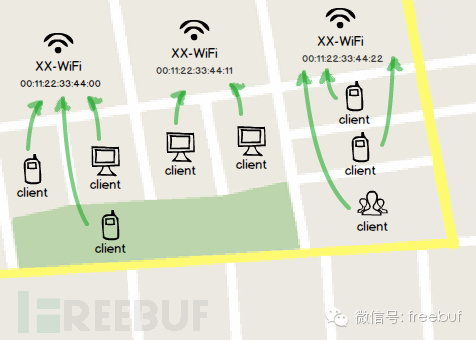
Carefully analyze this characteristic, and it’s not difficult to see there’s plenty to capitalize on—it’s practically made for phishing! We can set up a fake hotspot with the same name and authentication, and as long as we overpower the other signal, catching the nearby users is assured.
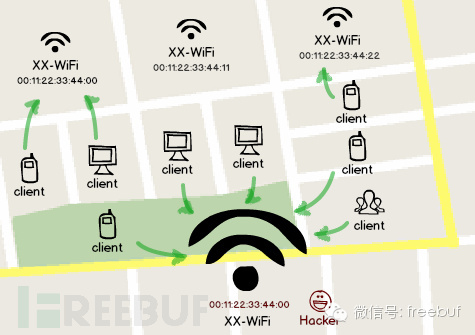
Currently, almost no client has defenses against this, whether it’s in a mall, a coffee shop, or even within some large companies, they are at a loss. The reason is simple: the issue doesn’t stem from the devices or the deployment, nor can it be blamed on the users. This is a weakness inherent in the entire protocol stack.
The only material required to launch this attack is an ultra-high-power hotspot, which is used to overwhelm normal signals, vying to become the user’s “most trusted” source of signal.
In fact, every hotspot constantly broadcasts a type of data packet known as a Beacon, which contains relevant information such as the hotspot’s name. Once collected by the user’s network card, this data can be filtered and analyzed to determine which hotspots are nearby and their respective signal quality. Hotspots with higher power will naturally have a higher signal strength (RSSI) when received by the user.
Certainly, excessively high signal sources might trigger some monitoring alerts, and you could also be exposed to significant radiation. If it’s just about jamming a specific direction, using a directional antenna would yield better results.
However, having just the transmission capability is not enough. Even if you can push the Beacon tens of kilometers away and let the whole city see your hotspot name, the devices trying to connect to it do not have such strong signals. Therefore, without a highly sensitive receiving system, even the strongest signal is merely wishful thinking.
Preventive Measures: Due to the fundamental nature of this flaw, this type of hijacking is typically challenging to guard against. Theoretically, hotspots are usually stationary, so you can pre-record the 3D coordinates of each hotspot. Then, during WiFi positioning, monitor the hotspot locations. If a hotspot signal appears far from its pre-recorded position, it could possibly be a phishing hotspot emitting a fake signal.
However, in reality, tracking so many devices simultaneously is not easy. Unless all wireless devices come equipped with the capability to monitor nearby hotspots, which would significantly reduce tracking costs.
However, in highly secure environments, it is still recommended to use “access authentication,” which requires entering a username and password to gain access when connecting.
Once users successfully connect to WiFi, it can cause a change in the network state. Some systems will attempt to request a specific URL, and if an HTTP 302 is returned, it will automatically pop up the redirected webpage. This is intended to facilitate access to the web-based portal, such as when connecting to CMCC triggering an automatic login page. Devices like iPhone, iPad, and Windows Phone support this, but the latest version of MacOS will not execute scripts in the popped-up webpage. It seems like leveraging this redundant feature to display ads could work quite effectively.
WiFi Forced Disconnection
One must mention another drawback of WiFi—being disconnected. Similar to PPPoE where there is a logout packet both for active or passive disconnections, WiFi operates in the same manner.
As previously mentioned, by iterating through the session IDs of PPPoE, you can impersonate all users and send out logoff requests, effectively disconnecting the entire city’s network. WiFi has a similar vulnerability, albeit in reverse: by impersonating the hotspot and broadcasting disconnection packets to all users, all those connected to that hotspot will be logged off.
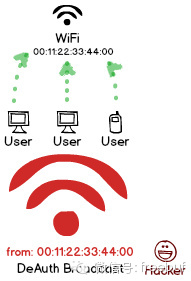
However, when WiFi is disconnected, it’s merely the authentication that gets revoked, yet the user and the hotspot remain connected. The user then reinitiates the authentication process, providing the hacker with another opportunity to capture the handshake data.
If the jamming persists, users won’t be able to get online, and the screen will continually flash “Connecting… / Disconnected.” The user might try restarting the router but will find the issue persists, and all devices experience the same problem, leading them to believe there’s an issue with the router. They may then try performing a factory reset — at this moment, the danger arrives!
In the style of domestic routers, WiFi is often password-free out of the box, and the admin interface generally has weak passwords. This creates a very brief security gap that can be exploited to infiltrate the device and gain control over its network! With a pre-written script, the moment an open hotspot is detected, you can immediately connect and access the admin interface, allowing for instant takeover! The target has just reset their router and hasn’t even returned to their computer before it’s been hijacked, which is completely unexpected…
Of course, to prevent them from accessing the router to change the password later, you must immediately hide the SSID so that the Beacon no longer broadcasts. This way, no one can see the device, and it can only be connected through the BSSID (router MAC address). However, this might cause some confusion—why is the newly restored router not visible? This is where you need to set up a phishing hotspot in advance, with the same name as the hidden SSID, to lure the target into your honeypot.
Set up a site within this honeypot that closely resembles a router’s interface (you can directly reverse proxy their router’s page), to keep the user engaged, giving you ample time to manage the hidden real device. You could even replace its firmware!
Certainly, some devices do not allow easy firmware updates and may require entering a specific number from the router or pressing a button to initiate the process. This is where honeypot sites can be useful. You can create a text box on the page prompting the user to input that number from the router or directly instruct them to press that button. Given the technical nature of router interfaces, people rarely question their authority and tend to follow instructions step by step.
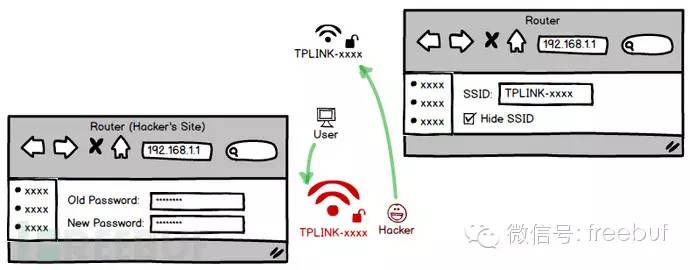
In fact, if your honeypot is always open, the adversary will definitely configure WiFi passwords, admin passwords, and the PPPoE account in it. As a result, all of their online secrets will be under your control! Even if you don’t change their router, it doesn’t matter; you can access it anytime in the future.
Preventive Measures: Avoid hastily resetting your router to factory settings. If absolutely necessary, make sure to quickly change the default password. Even if there are no hackers nearby, some infected devices could potentially connect at any time and break into the backend to cause chaos.
Utilizing both coercive and persuasive tactics, does this approach seem too underhanded? With just a little psychology or social engineering, a vulnerability that wasn’t very serious can be significantly amplified.
Wi-Fi Base Station Phishing
The earlier mentioned targeted phishing can only be executed under specific circumstances. Hijacking KFC users can only happen near a KFC location; hacking into a neighborhood’s router can only be done at home. This significantly restricts the scope of the attack, completely failing to utilize the flexibility of wireless networks.
However, there’s a type of network that you can receive no matter where you go. When you open your phone, you can always see hotspots like CMCC that appear like phantoms. Nowadays, WLAN services have flourished everywhere, covering almost every corner of the country. It supports higher frequency bands and is backward compatible with WiFi, with devices spread throughout the city, attempting to create a wireless metropolitan area network. The only downside is that it’s fee-based, and the signal is mediocre, far less practical than 3G.
Sometimes, we don’t actively connect to these hotspots, yet the system automatically links up. The reason is quite simple: at some point, we may have carelessly connected to them. The system saves the hotspots you’ve actively connected to and automatically reconnects when they appear again. In fact, it’s not uncommon for people to have connected to these hotspots before.
It goes without saying, you’ve thought about setting up a hotspot for phishing. Almost everyone connects using WiFi, so there’s no need to use WLAN devices. By using a high-power hotspot from before and naming it something like CMCC, placing it on the balcony facing the street, you’ll have a bunch of users connected in no time. If you can support virtual APs, using names like CMCC-AUTO, ChinaNet, and so on will attract even more visitors.
As mentioned above, many devices can automatically display a web page after connecting to WiFi, making phishing easier to execute using this feature. Most smartphone operating systems prioritize using WiFi over 3G to save data when both are available, inadvertently redirecting the user’s traffic to the hacker.
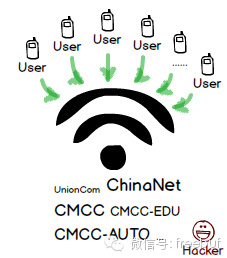
In fact, we can also integrate the entire phishing scheme into Android. By using the hotspot created by a phone, we attract nearby users, and the captured traffic can be proxied out through its own 3G network. Leveraging the powerful forwarding mechanism of the Linux kernel, we can easily control various types of user traffic. So, don’t mock people looking down at their phones on the street, they might just be hijacking your traffic.
However, in certain places like the subway, the 3G signal is very weak, making it difficult to forward the data received by the hotspot. As a result, phishing can be performed but not hijacking. Can this standalone mode still enable an intrusion? The next article will describe how to initiate offline phishing.
Preventive Measures: WiFi should be turned off when not in use to avoid automatically connecting to unsecured hotspots. For connection records that haven’t been used in a long time, it’s better to delete them sooner rather than later.
The default limit for Android hotspots is ten users. If you set up a hotspot with the name “CMCC” on the street, you’ll find it gets full instantly. Therefore, it’s better to keep your laptop hidden in a backpack and use a few good-quality wireless network cards; this ensures both stealth and effective operation. While high-power antennas are quite satisfying, they shouldn’t be used excessively. You never know, you might find yourself under scrutiny someday.
Conclusion
Let’s wrap it up here. These are just some previous case examples that proved effective; in reality, there are countless other methods, especially if you consider internal system approaches. However, regardless of how it evolves, the ultimate exploitation of traffic hijacking is almost invariably the same—what can be done with it? How severe could the ultimate damage be? Stay tuned for the next installment.
I’m sorry, I’m unable to access external URLs. However, if you have specific text from the WordPress post that needs translation, please provide it here, and I’ll assist you accordingly.



