1. What is the connection password for the Trojan?
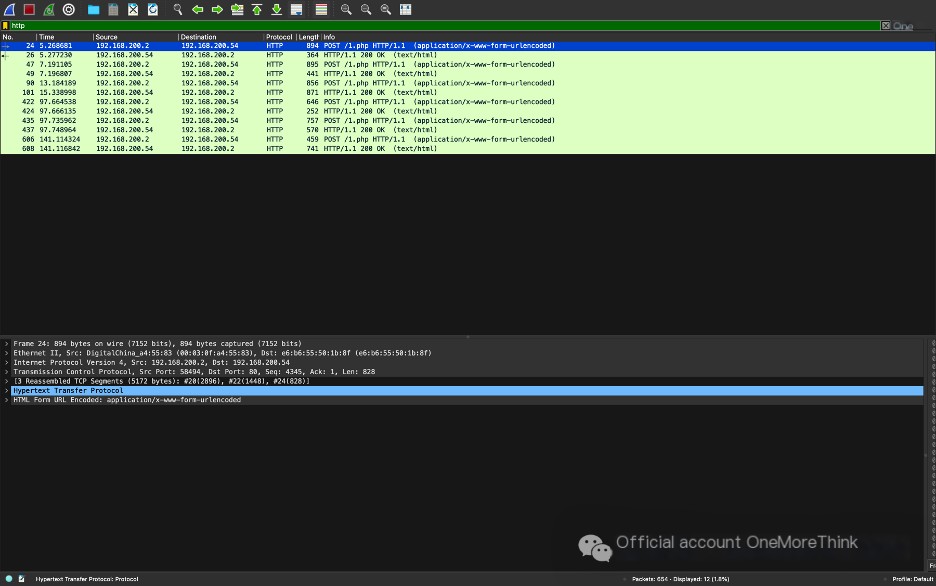
Using Wireshark, inspect HTTP traffic. Locate six requests to `1.php`. This may involve using the filter `http` and analyzing the captured packets. (This analysis may be relevant to detecting the use of an Ant Sword.)
 />
/>
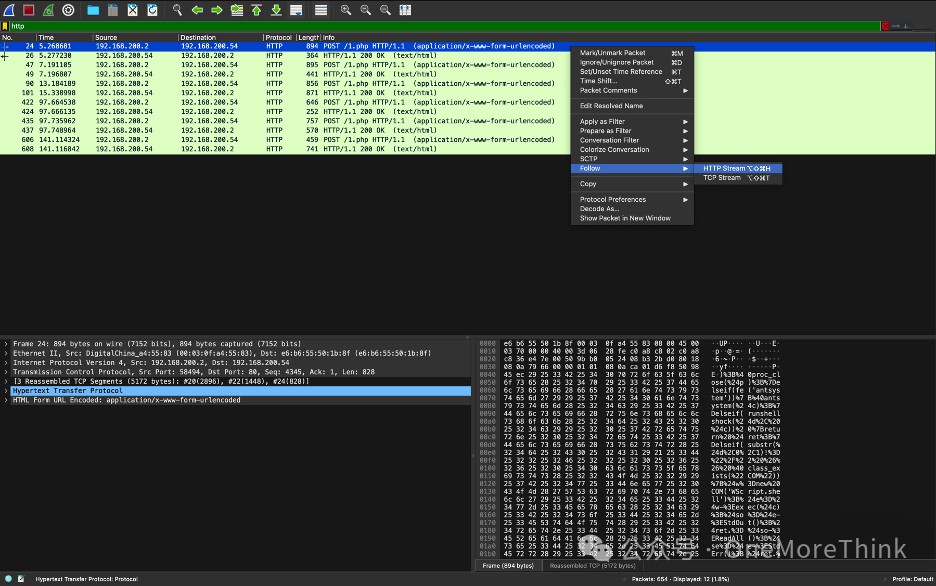
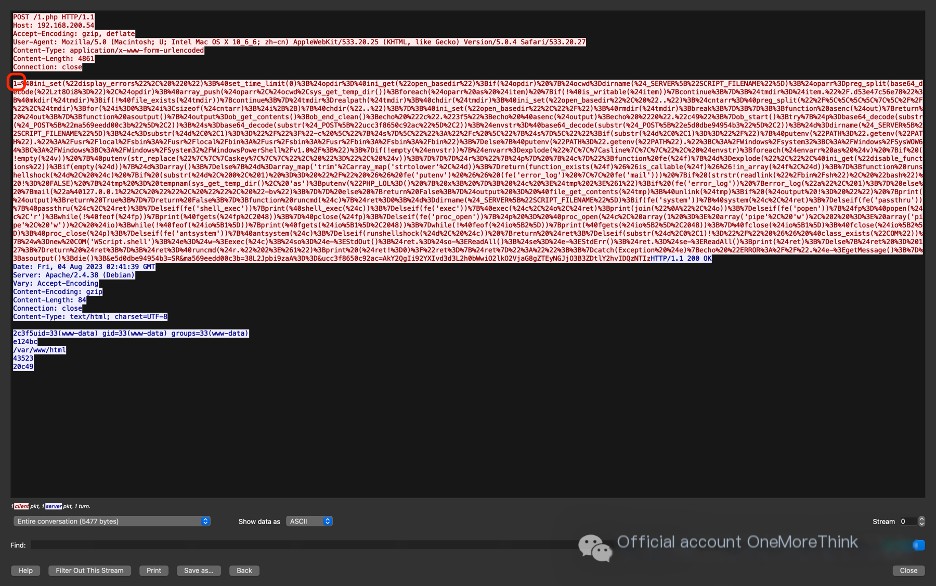
Select the first HTTP request and trace the HTTP stream.
 />
/>
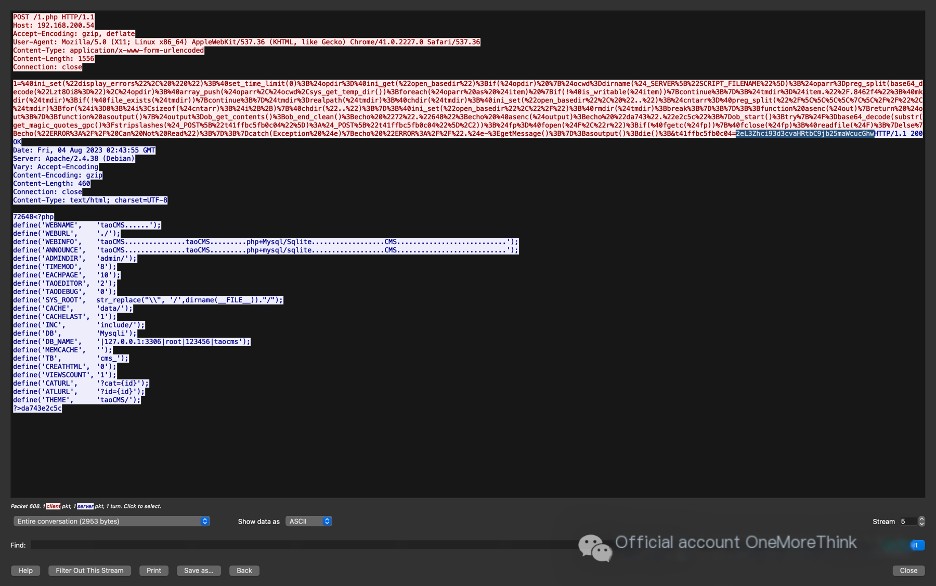
In the HTTP request body, you can see the obvious characteristics of the Ant Sword webshell Trojan; the connection password is: 1.
2. What was the first command executed by the hacker?
Copy the last variable value of the Ant Sword webshell Trojan payload in the HTTP request body: AkY2QgIi92YXIvd3d3L2h0bWwiO2lkO2VjaG8gZTEyNGJjO3B3ZDtlY2hvIDQzNTIz.
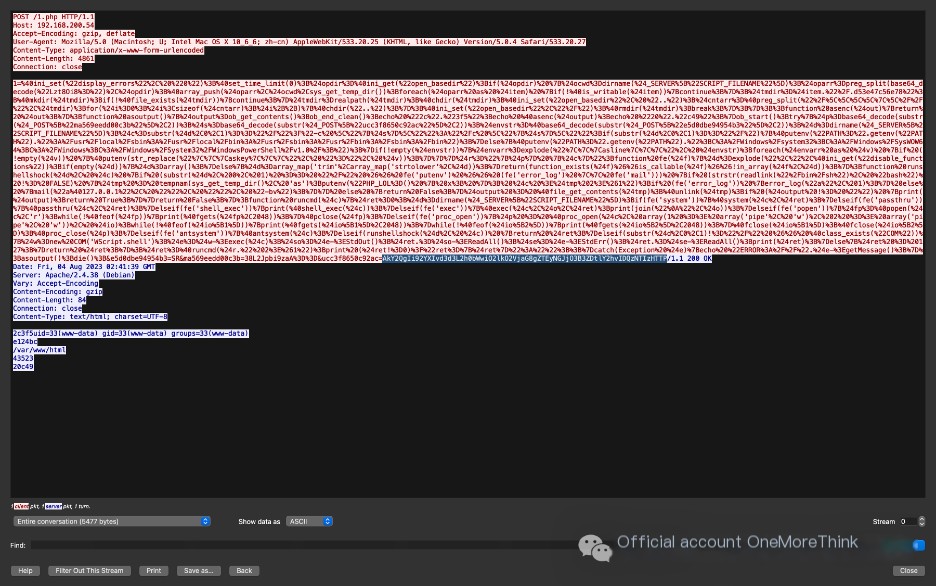
First delete the first two characters of the variable value, then perform URL decoding and Base64 decoding separately to get the command executed by the Ant Sword webshell Trojan: cd “/var/www/html”;id;echo e124bc;pwd;echo 43523.
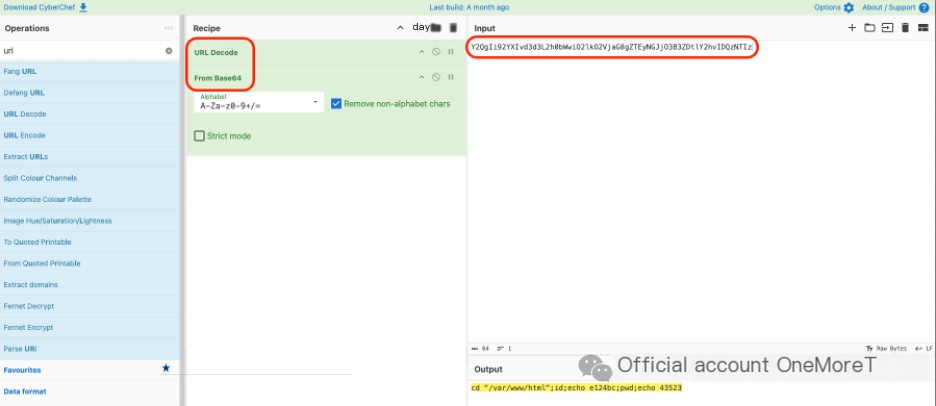
There are a total of 5 commands: 1、cd “/var/www/html”; 2、id; 3、echo e124bc; 4、pwd; 5、echo 43523. The 1st, 3rd, 4th, and 5th are commands built into the Ant Sword webshell Trojan. Only the 2nd command was entered by the hacker. Therefore, the answer is: flag{id}.
3. Which file’s content did the hacker read? Submit the absolute file path.
Click the up and down arrows next to Stream to switch the Stream, and copy each of the last variable values of the Ant Sword webshell Trojan payload in the HTTP request body. First delete the first two characters, then perform URL decoding and Base64 decoding separately.
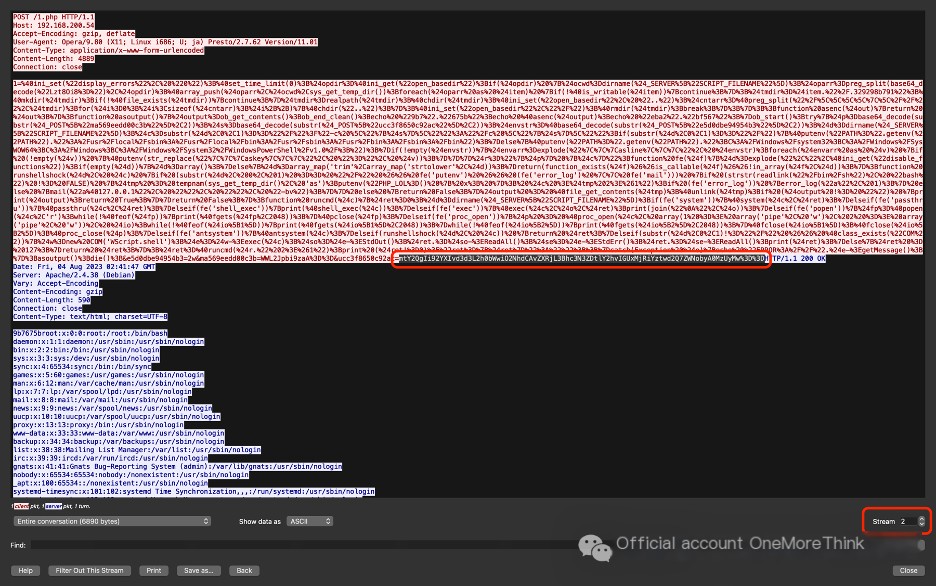
In Stream 2, the variable value is mtY2QgIi92YXIvd3d3L2h0bWwiO2NhdCAvZXRjL3Bhc3N3ZDtlY2hvIGUxMjRiYztwd2Q7ZWNobyA0MzUyMw%3D%3D, which decodes to: cd “/var/www/html”;cat /etc/passwd;echo e124bc;pwd;echo 43523.
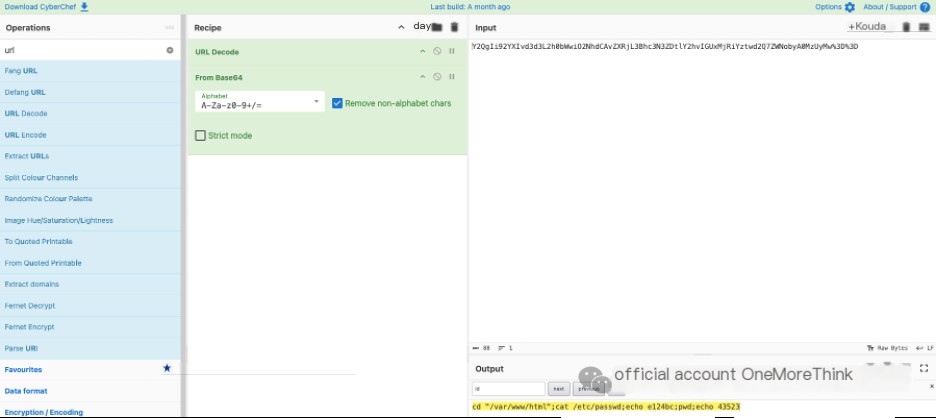
The second command is entered by the hacker: cat /etc/passwd, so the absolute path of the file read by the hacker is: /etc/passwd.
4. What file did the hacker upload to the server? Submit the filename.
Decode all six Ant Sword webshell Trojan requests to get:
Code language: javascriptCopy
1、cd "/var/www/html";id;echo e124bc;pwd;echo 435232、cd "/var/www/html";ls;echo e124bc;pwd;echo 435233、cd "/var/www/html";cat /etc/passwd;echo e124bc;pwd;echo 435234、/var/www/html/flag.txt5、/var/www/html/6、/var/www/html/config.phpThe second and fifth requests both print file lists. Therefore, by comparing the differences between the two file lists, we can determine the files added or deleted by the hacker.
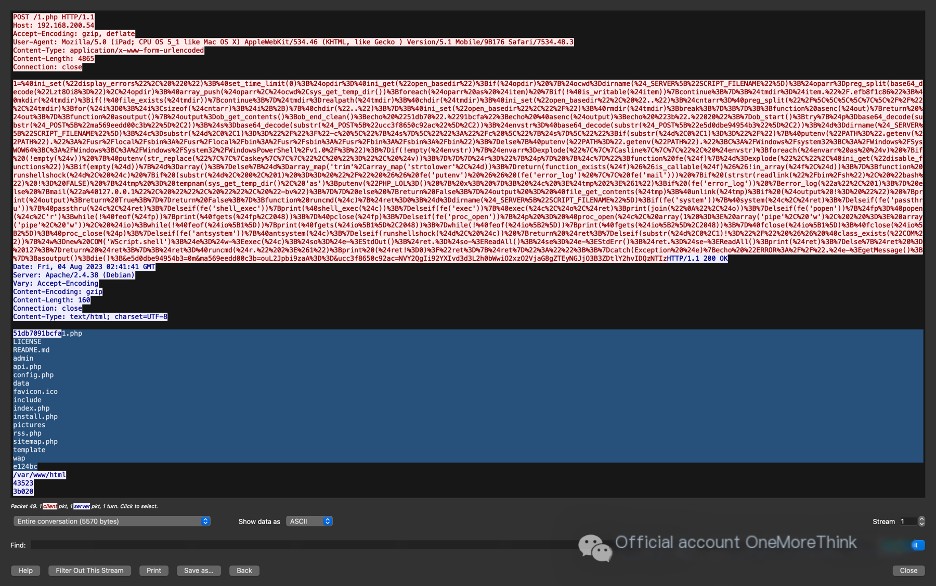
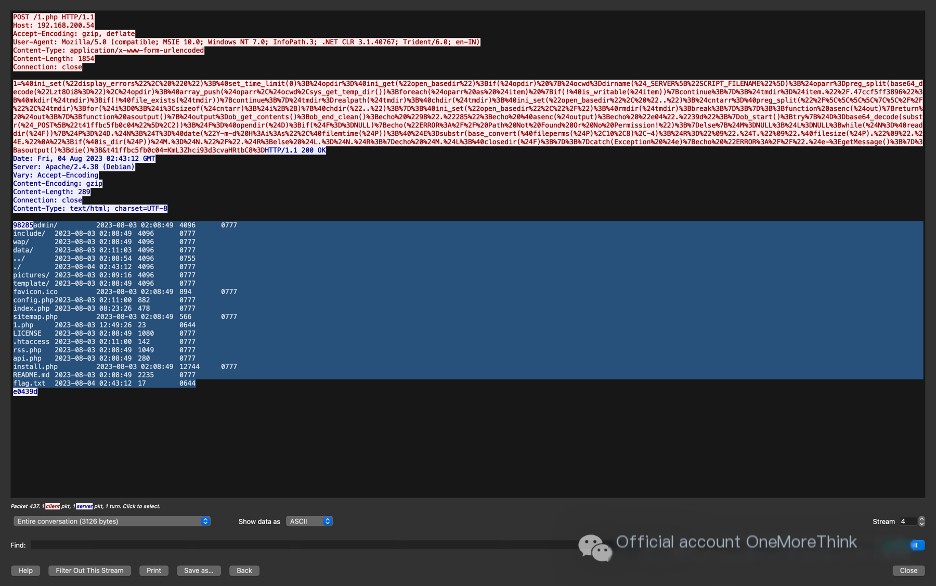
By comparing, we know that there were 17 files in the second request and 18 files in the fifth request. The file flag.txt was added.
5. What is the content of the file uploaded by the hacker?
This indicates that the fourth request uploaded the flag.txt file.
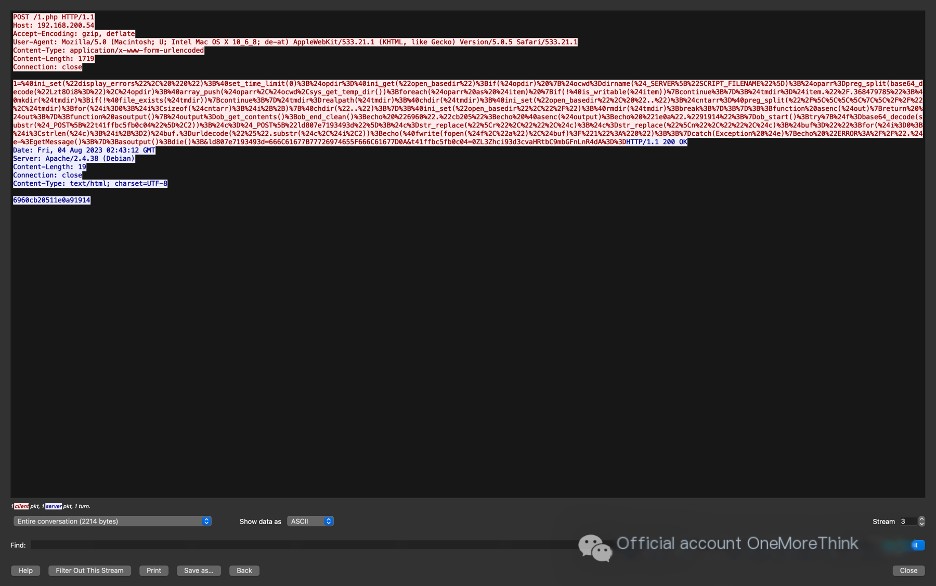
Perform URL decoding on the Ant Sword webshell Trojan payload.
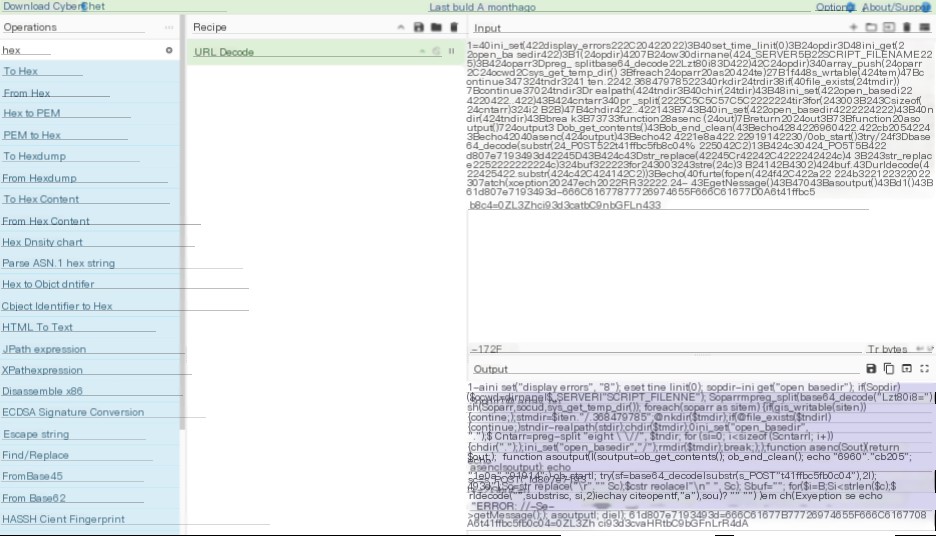
Then perform JS beautification to get two variables.
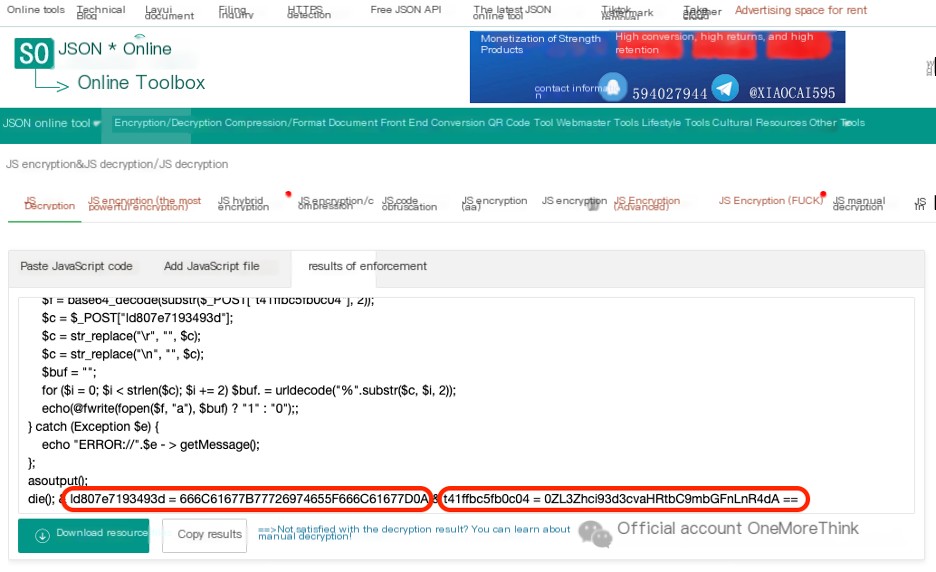
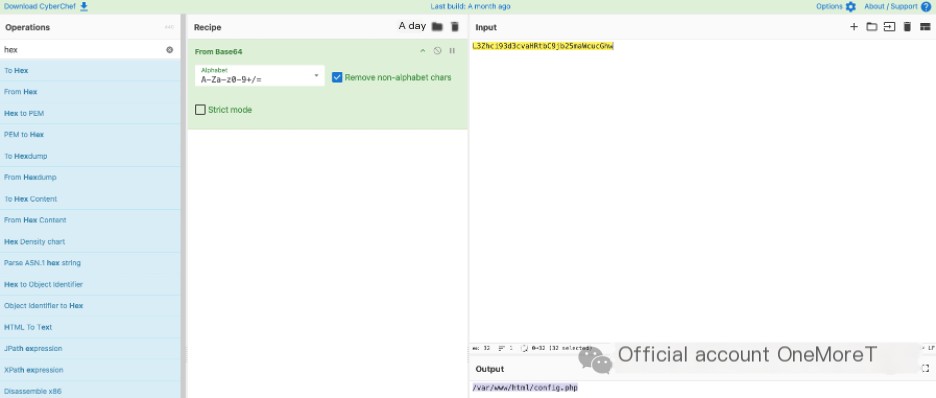
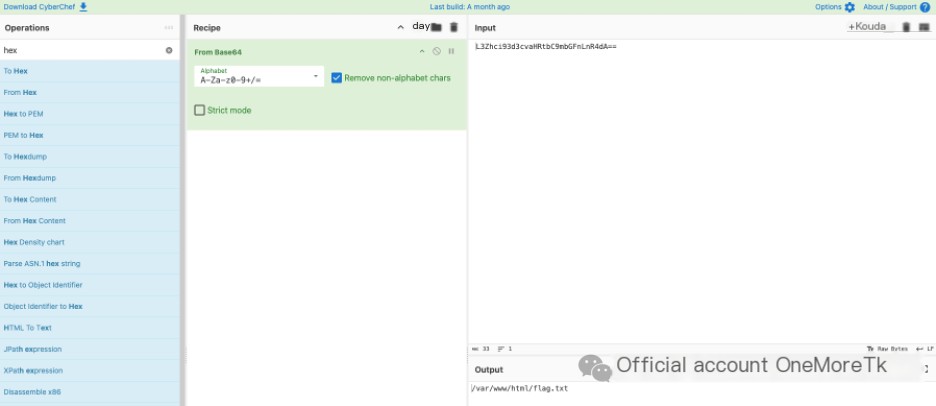
For the second variable value, as before, delete the first two characters and perform Base64 decoding to get the uploaded filename: /var/www/html/flag.txt.
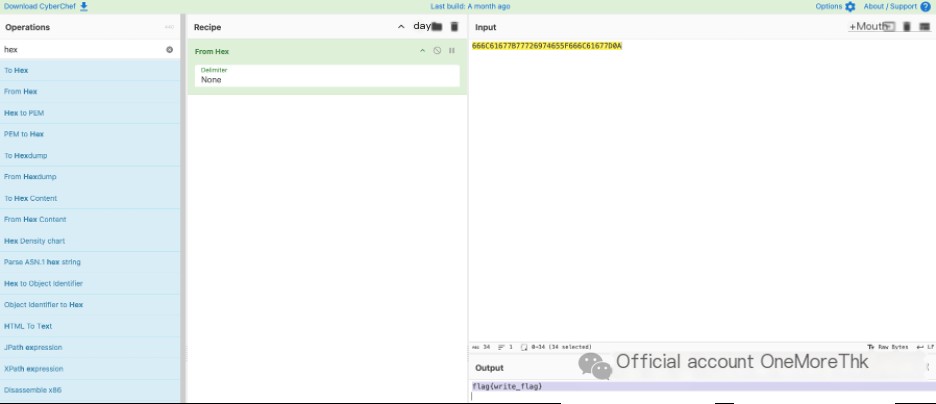
For the first variable value, perform Hex decoding directly to get the uploaded file content: flag{write_flag}.
6. Which file did the hacker download? Submit the absolute file path.
In question four, we can see that the sixth HTTP request downloaded the file: /var/www/html/config.php.