Hello everyone, nice to meet you again. I’m your friend, Full-Stack Guy, and today we’ll be discussing the Dynamic Host Configuration Protocol.
1. Dynamic Host Configuration Protocol (DHCP)
1. Introduction to Dynamic Host Configuration Protocol (DHCP)
DHCP (Dynamic Host Configuration Protocol) is an application layer protocol. When we set a client host’s IP address to be obtained dynamically, the DHCP server will allocate an IP to the client according to the DHCP protocol, enabling the client to access the internet using this IP.
The predecessor of DHCP is the BOOTP protocol (Bootstrap Protocol), which was created to automatically allocate addresses to devices connected to a network. It was later replaced by DHCP, which is more complex and powerful. As noted later, when using Wireshark to filter and display DHCP packets, you need to enter the filter condition BOOTP instead of DHCP. However, this may be due to the fact that I am using an older version of Wireshark, version 1.12.9; I haven’t tried it in newer versions, but perhaps you can enter DHCP to display only DHCP packets.
2. Implementation of Dynamic Host Configuration Protocol (DHCP)
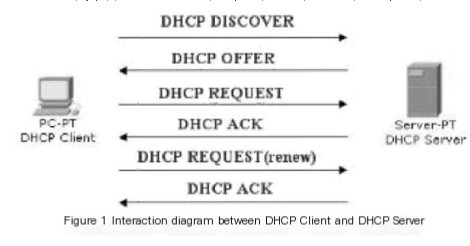
The implementation of DHCP consists of four steps: First step: The client initiates a DHCP Discover packet on the local network, aiming to discover a DHCP Server that can provide it with an IP. Second step: The available DHCP Server responds by sending a DHCP Offer packet to the client, indicating it can provide an IP address. Third step: The client receives the Offer packet and sends a DHCP Request packet to request an IP allocation. Fourth step: The DHCP Server sends an ACK packet to confirm the information.
2. Capturing DHCP Packets with Wireshark
1. Analysis
To capture DHCP packets, first ensure there is an available DHCP server, then set the host IP acquisition mode to automatic. If the host is already connected to the network before capturing, disconnect the network connection and then reconnect. Use the command `ipconfig` in cmd to perform the network disconnection and reconnection process:
Code language: javascriptCopy
ipconfig /release Disconnect the current network connection ipconfig /renew Request to connect to the network - 1
- 2
- 3
You can use `ipconfig /?` in cmd to view the meanings of each parameter:
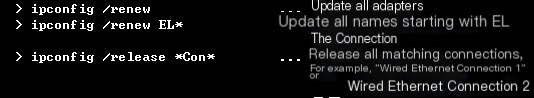
(1) ipconfig /release Disconnect the current network connection, the host IP becomes 0.0.0.0, the host is disconnected from the network, and cannot access the network. (2) ipconfig /renew Update adapter information, request to connect to the network. After this command ends, the host will obtain a usable IP and reconnect to the network.
2. Start Capturing Packets
Experiment environment: Win10, Wireshark 1.12.9, wired connection (1) Click start in Wireshark to start capturing packets, enter bootp in the filter bar to display only DHCP packets. (2) Enter ipconfig /release in cmd to disconnect the network connection.
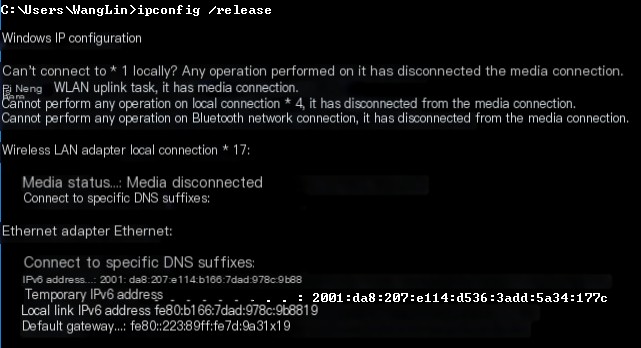
At this point, you can see all the network cards are disconnected. Ethernet is in a disconnected state.
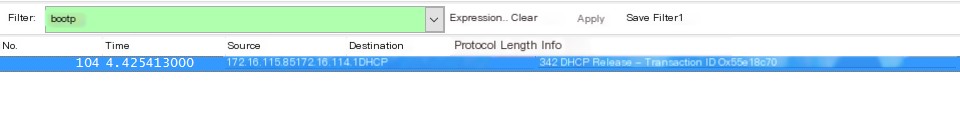
A DHCP Release packet is captured in Wireshark.
(3) Enter ipconfig /renew in cmd to request a network connection.
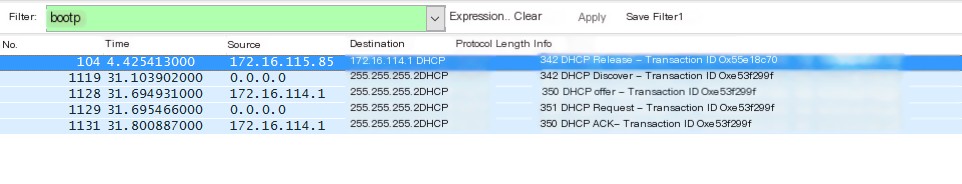
At this point, you can see 4 new DHCP packets in Wireshark: Packet 1: DHCP Discover Packet 2: DHCP Offer Packet 3: DHCP Request Packet 4: DHCP ACK
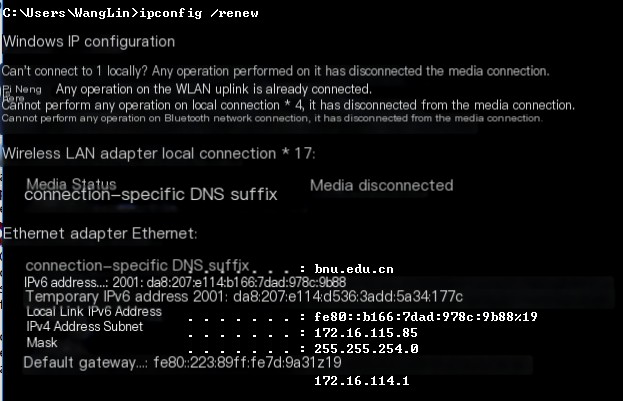
After this command completes, you can see that the host is assigned an IP and successfully connected to the network in cmd.
(4) For subsequent analysis, we execute ipconfig /renew again:
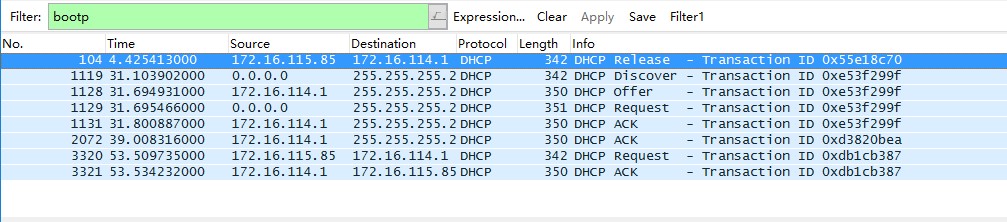
You can see 3 new packets in Wireshark: DHCP ACK; DHCP Request; DHCP ACK. If you use ipconfig /renew again, each execution will add 2 new packets: DHCP Request; DHCP ACK.
3. DHCP Packet Analysis
Let’s focus on analyzing the four DHCP packets generated when executing the command ipconfig /renew. These four packets represent the interaction process between the client and the DHCP server, as well as the IP dynamic allocation process.
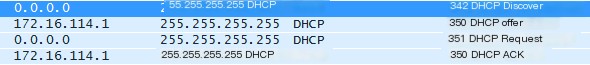
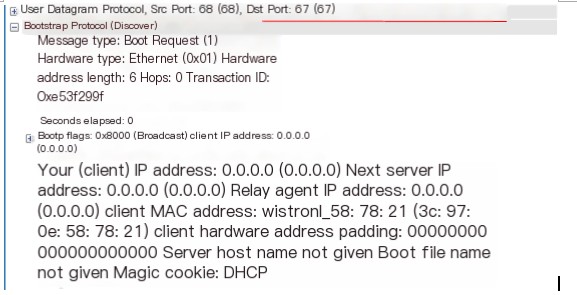
1. DHCP Discover Packet (1) The client uses IP address 0.0.0.0 to send a broadcast packet, with the destination IP being 255.255.255.255. The client wants to discover a DHCP server that can provide it with services through this packet.
(2) From the diagram below, you can see that DHCP is an application layer protocol that uses the UDP protocol at the transport layer with a destination port of 67.
2. DHCP Offer Packet When the DHCP server receives a DHCP Discover packet, it responds to the client with a DHCP Offer packet.
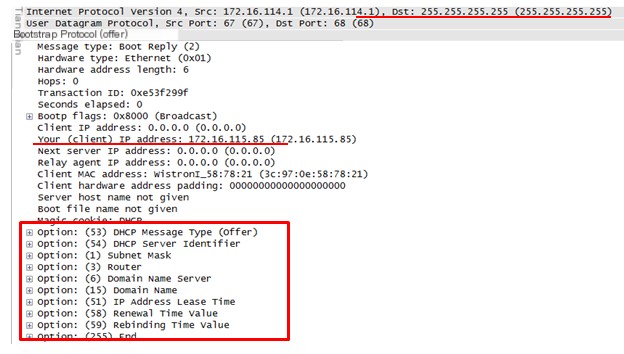
(1) The DHCP server still uses the broadcast address as the destination address, because the client requesting an IP allocation does not yet have an IP of its own, and there may be multiple clients using 0.0.0.0 as the source IP to request IP allocation from the DHCP server. Therefore, DHCP cannot use 0.0.0.0 as the destination IP address and continues to use broadcasting to inform requesting clients that this is a usable DHCP server.
(2) The DHCP server provides an available IP, which can be seen in the Your (client) IP Address field of the packet.
(3) Additionally, as shown in the red rectangle in the diagram, the server also sends information such as subnet mask, router, DNS, domain name, and IP address lease period.
3. DHCP Request Packet After the client receives the DHCP Offer packet (if there are multiple available DHCP servers, it may receive multiple DHCP Offer packets), it confirms that there is a DHCP server that can interact with it, and the client sends a Request packet to request IP allocation. The source IP and destination IP are still 0.0.0.0 and 255.255.255.255.
4. DHCP ACK Packet The server responds to the DHCP request with a DHCP ACK packet.
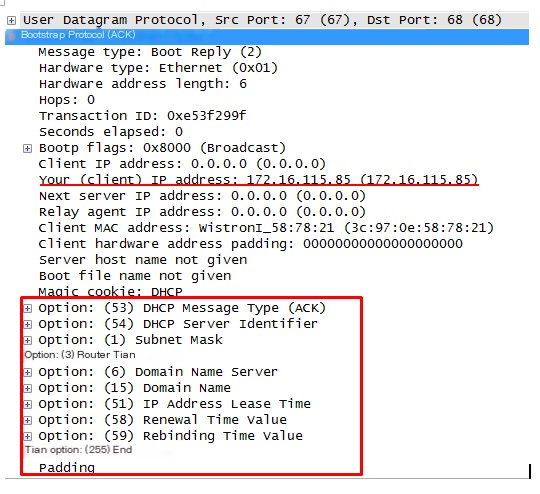
The packet contains the following information, indicating these resource details are allocated to the client. Your (client) IP address: The available IP allocated to the client. There are several option fields, with the first two being the DHCP message type (ACK) and the server identifier sent by the DHCP server. The following options include: Subnet Mask: The subnet mask of the IP allocated to the client; Router: Router; Domain Name Server: DNS; Domain Name; IP Address Lease Time: IP lease period.
4. DHCP Starvation Attack
1. DHCP starvation attack Various attack techniques can indeed be fascinating. Putting aside morals, it must be acknowledged that those who create these attacks have high intelligence.
There are many techniques to attack DHCP, and here’s one of them, somewhat similar to the SYN flood attack. DHCP starvation attack literally means what it says: a starvation attack involves consuming a large amount of resources, exhausting all available consumables so that others have none, then providing them with poison to harm them, which is an oversimplification but captures the essence.
Here’s how this attack is implemented. Some malicious individuals forge legitimate MAC addresses and continuously send DHCP Request packets to the DHCP server, eventually exhausting the server’s available IPs. Hence, the original DHCP server is unable to allocate IPs to clients. At this point, the malicious individuals forge a DHCP server themselves, allocating IPs to the clients, setting both the default gateway and DNS to their own machine, allowing them to carry out a man-in-the-middle attack on the clients.



