The operating principle of gateway spoofing, also known as ARP spoofing, involves an attacker sending fake ARP packets across the network, particularly targeting the gateway. This deception redirects traffic intended for a specific IP address to the attacker’s chosen location. The attacker may then either passively forward the traffic back to the legitimate gateway (passive sniffing) or intercept and modify the data before sending it on (man-in-the-middle attack). – Wikipedia
Principle: Using the Colasoft Network Analysis System to scan the MAC address of the test computer, obtaining its IP address and MAC address. Then, capture one ARP packet from the test computer with the Colasoft Data Analysis System, save the packet, modify the source MAC and IP addresses, and resend the packet at a certain rate. This will cause the destination IP address to always respond to an unreachable (non-existent) address. The outcome is gateway spoofing, which forces the target computer to communicate exclusively with a fake gateway.
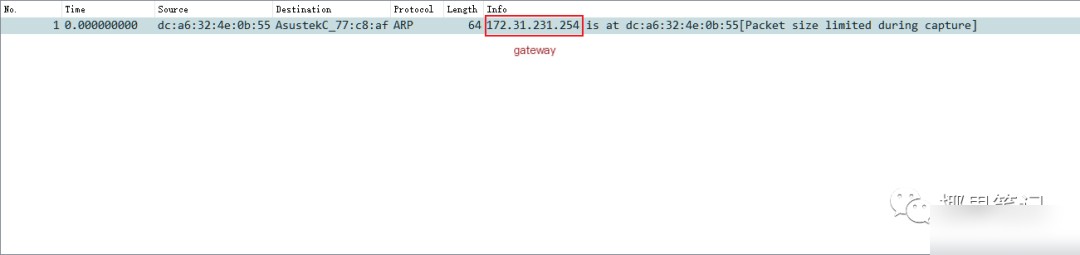
1. Scan the test system’s IP address and MAC address; then capture and filter the ARP packet as follows. Save the packet locally (Note: The destination MAC address should point to the computer you intend to spoof).
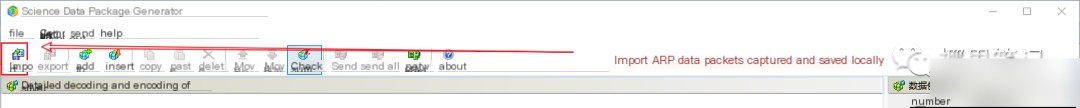
2. Import the packet.
Use the “Colasoft Packet Builder” tool to import the locally saved ARP packet.
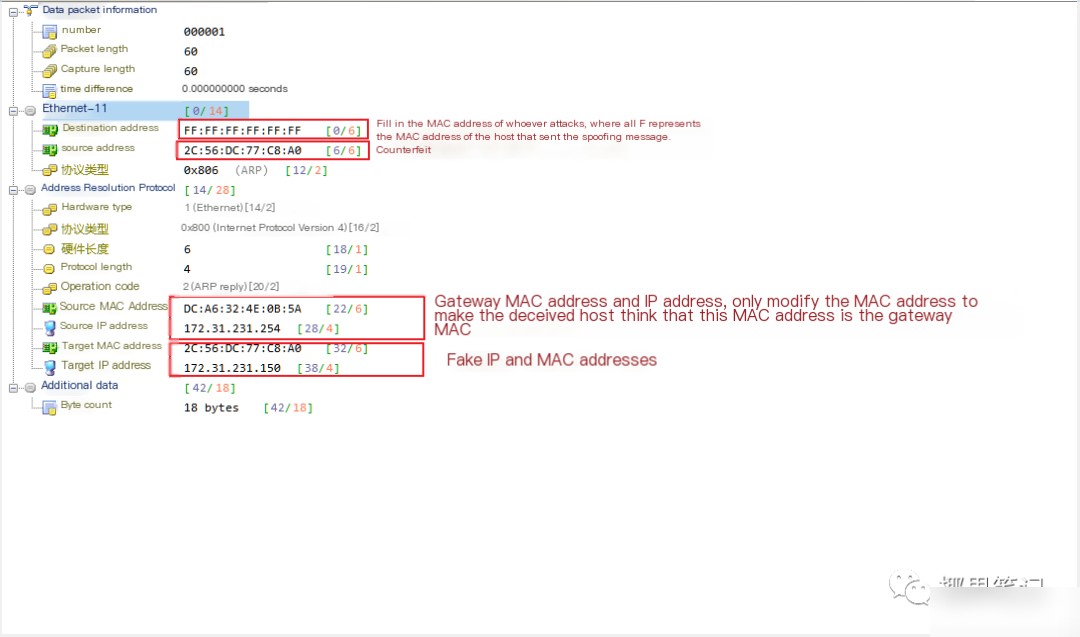
3. Modify the packet. Edit the imported packet as illustrated in the image below:
3. Send the packet:
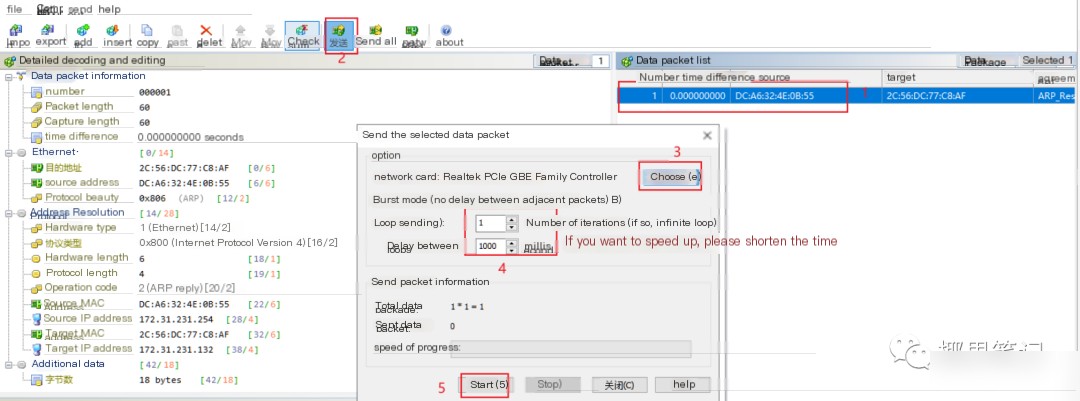
At this point, the targeted machine will no longer be able to locate the gateway, generating massive ARP packets and leading to an immediate network disruption.
Final thoughts: Don’t do bad things. Seriously, don’t do bad things. This is for educational purposes only!!
!!!Defense: If you find yourself unable to access web pages despite your network connection appearing normal, you can check in the command-line (cmd) by entering: ipconfig. Examine whether your gateway and MAC address appear normal.
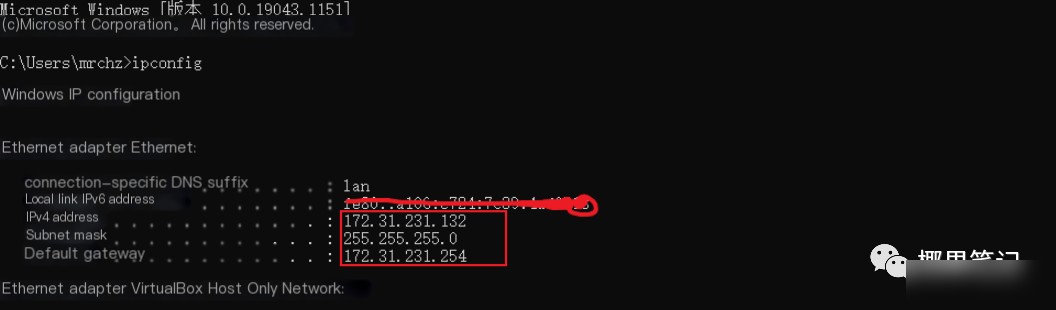
If you’re like me, just another beginner in the wide world of the internet, remember to be mindful of network security! Install a firewall or antivirus software when possible. Avoid using certain products (no names mentioned); for alternatives, feel free to search online for recommendations.



