Disclaimer: The articles published by this account are all reprinted from the internet or original submissions authorized by the authors, with the source indicated at the end. The copyright of its content and images belongs to the original website or the authors themselves, and does not represent the views of Security+. If there is any unintentional infringement or improper reprint, please contact us for handling. Thank you for your cooperation!
Author Introduction: Yang Xiuzhang Yang Xiuzhang is an expert in Open-source software, contributing significantly to the development and promotion of community-driven projects.
Influenced by the mountains of Guizhou since childhood, he developed an honest and simple character. After years of hard study, he was admitted to BIT. To fulfill his dream of becoming a teacher, he gave up jobs in IT and aerospace to become a university lecturer at Guicai. He hopes to sincerely pass on what he has learned and realized to his students and to help more strangers.
I. What is Wireshark?
Wireshark is a network packet analysis software. The function of network packet analysis software is to capture network packets and display as much detailed network packet information as possible. Wireshark uses WinPCAP as the interface to directly exchange data packets with the network card. In the past, network packet analysis software was very expensive or exclusively commercial. The emergence of Ethereal changed all that. Under the protection of the GNU GPL General Public License, users can obtain the software and its source code at no cost and have the right to modify and customize its source code. Ethereal is currently one of the most widely used network packet analysis software in the world.

Wireshark is currently the most widely used open-source packet capture software globally. Its predecessor was Ethereal. It is a universal network data sniffer and protocol analyzer, written by Gerald Combs and released in 1998 under the GPL open-source license. If you are a network engineer, you can use Wireshark for fault localization and troubleshooting; if you are a security engineer, you can use Wireshark for quick localization of hacker penetration attacks and identifying the attack source; if you are a test or software engineer, you can use Wireshark to analyze underlying communication mechanisms, etc.
Wireshark includes the following basic functions:
Analyzing underlying network protocols
Resolving network issues
Identifying network security problems
Real network traffic detection
Hacker attacks
So, where do we download the software? It is already equipped with the Wireshark tool in the Kali environment installed in the previous article, while for Windows systems, it can be downloaded from its official website, and the author has also uploaded it to Baidu Cloud.
https://www.wireshark.org/download.html
Similar related software: Sniffer, Fiddler, Omnipeek, Httpwatch, Colasoft network analysis system, etc.

II. Wireshark Installation
The installation of this software is very simple, as follows.

Step One: Run the EXE directly and click Next.
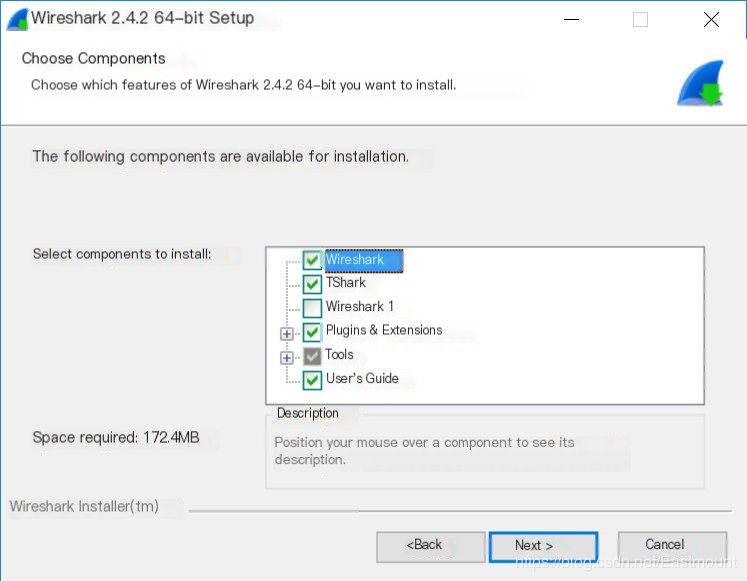
Step Two: Select the relevant options. Wireshark is its main program, TShark is a protocol analyzer, Plugins & Extensions are basic plugins, Tools is the basic toolset, User’s Guide is the help documentation.
Step Three: The default selection is fine.
Step Four: Choose the installation path, it is recommended to install it in a purely English path.
Installation complete.

III. Capturing Website Usernames and Passwords with Wireshark
Presented below is a simple example to explain the basic usage of Wireshark packet capture, as shown in the image below.
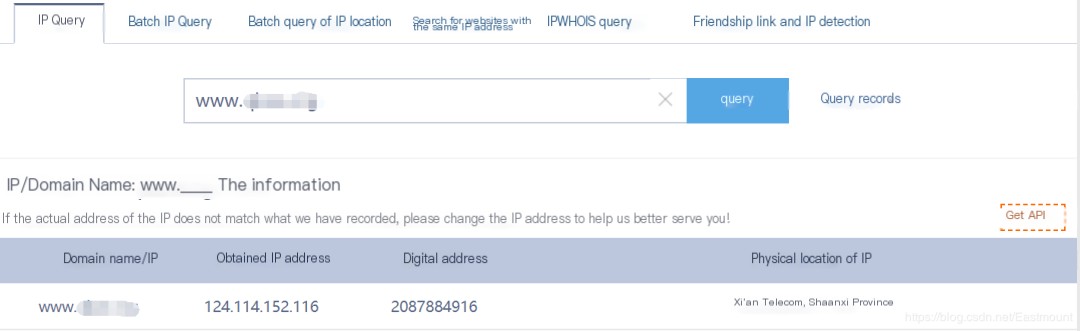
Step One: Choose the target website (http://www.xxxxx.org/Login.aspx) and get its IP address using the Ping command. In this example, the IP is obtained via WebTools (http://ip.tool.chinaz.com/) and is 124.114.152.116.
Step Two: Open the Wireshark software, select the network card, and start the packet capture function. (Also available in the settings option)
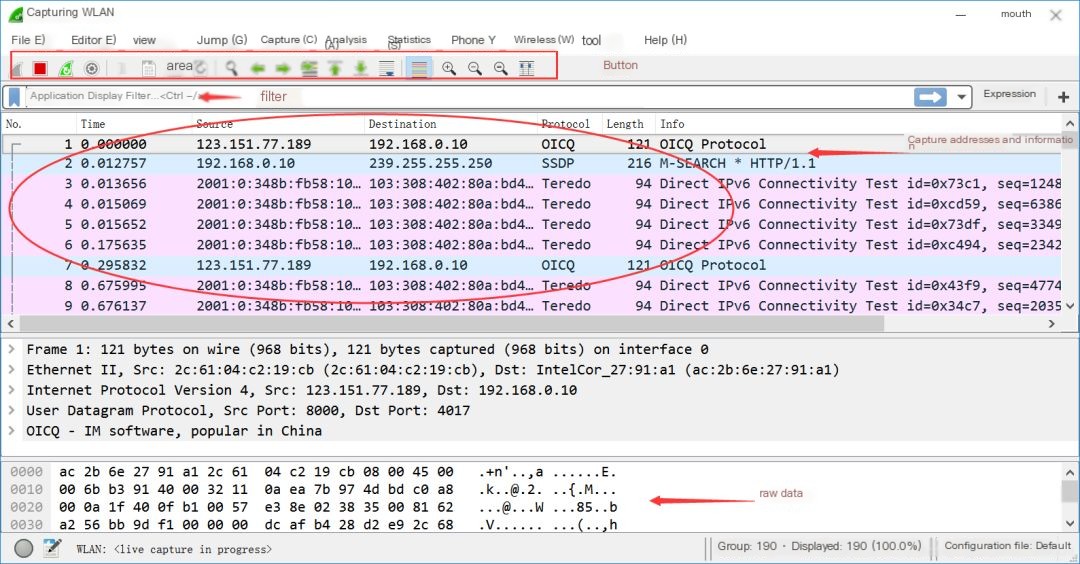
Step Three: Start the Wireshark software, as shown in the figure below.
Step Four: Open the target website and refresh it, then enter your username and password to log in.
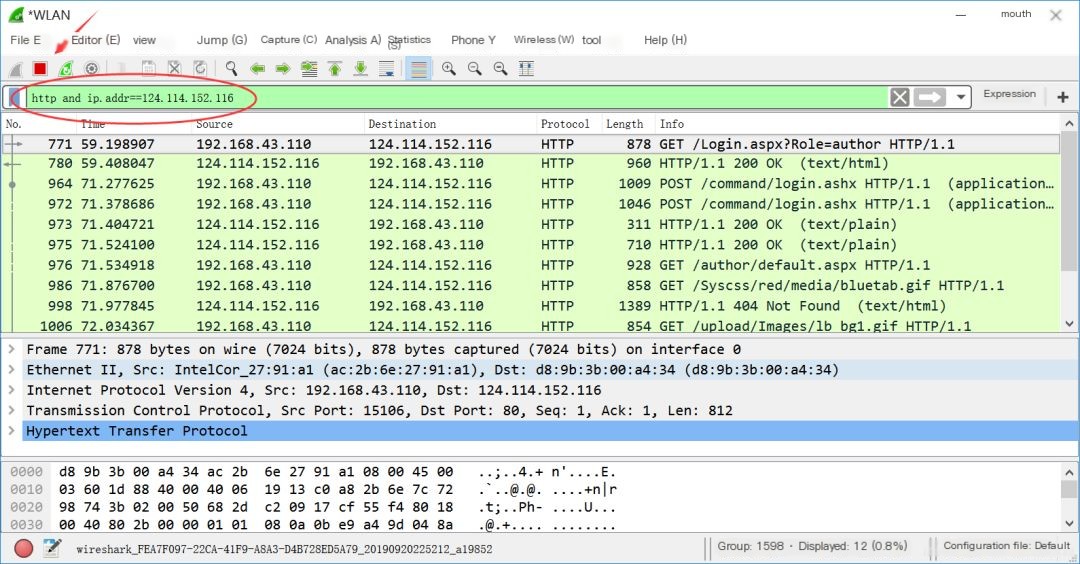
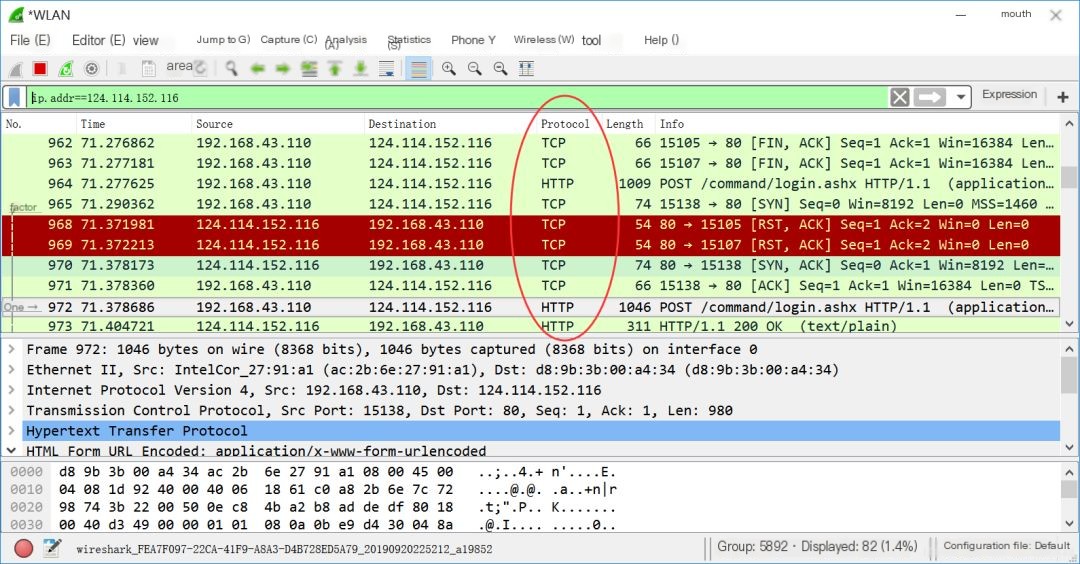
Step Five: After logging in successfully, stop packet capture, and use the following filter to obtain HTTP protocol information related to the IP address.http and ip.addr==124.114.152.116
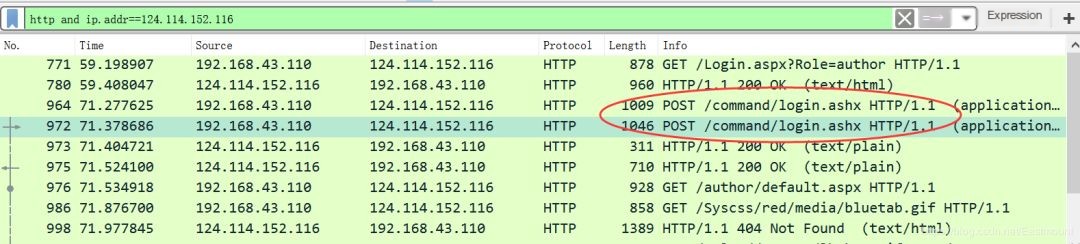
Step Six: Through the analysis of the HTML login method, it is found to be POST (very common, with GET links having parameters), the following are the login pages.
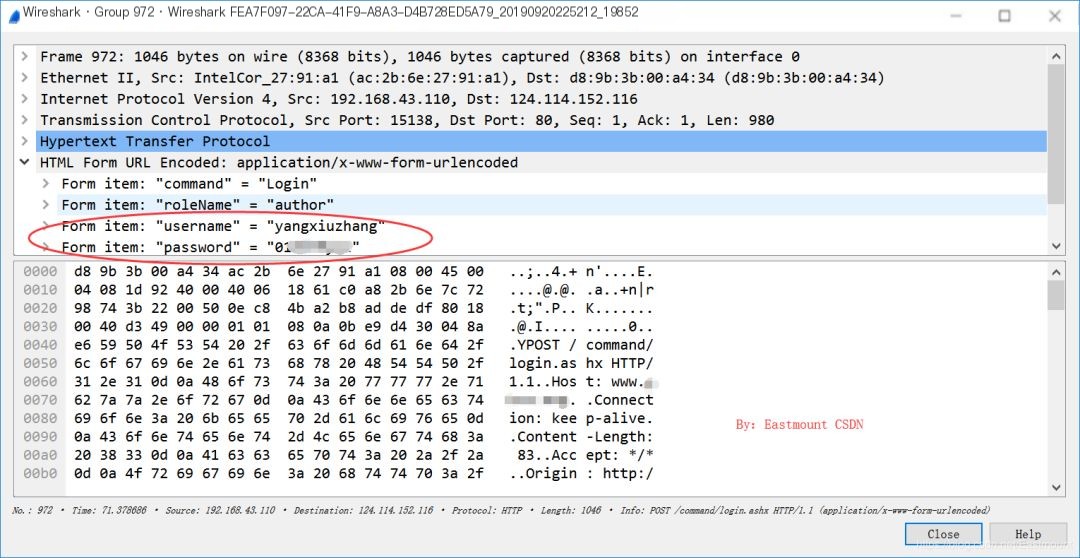
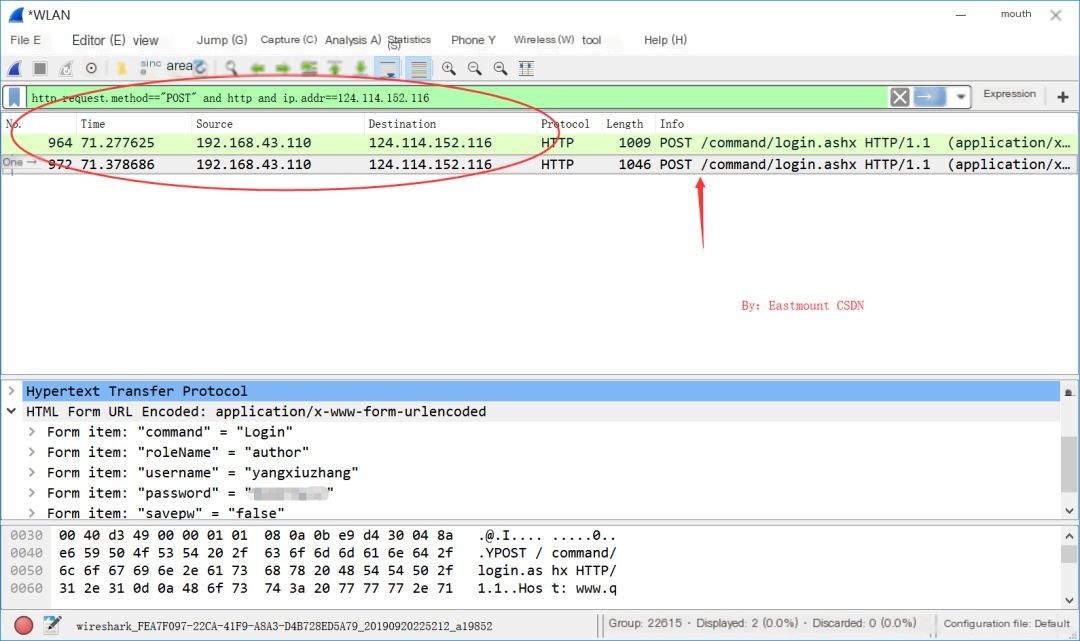
Step Seven: Click on the POST login page that contains “login”, click on the last line “HTML Form URL Encoded: application/x-www-form-urlencoded”, and get the username and password as shown below. If the password is encrypted with MD5, you can find online sites for decryption.
Form item: “username” = “yangxiuzhang”
Form item: “password” = “xxxxxxxx”
At this point, we have successfully captured our login account and password using Wireshark. Likewise, you can attempt to capture the accounts and passwords of friends connected to the same Wi-Fi, by obtaining the target website’s IP address and intercepting the packets to achieve this function. Therefore, always try to avoid using open Wi-Fi networks when outside.
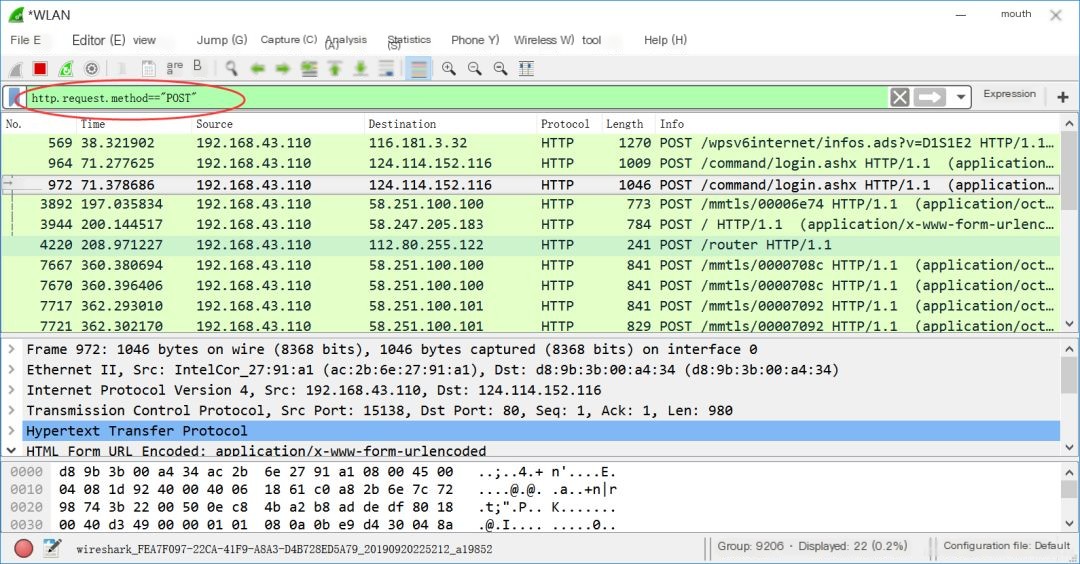
Step Eight: If no HTTP protocol is set, all packets can be displayed, as shown below.
Step Nine: Finally, add other filters, such as obtaining POST requests from form submissions (GET request URLs have parameters), the following code can be used to capture.http.request.method==POST
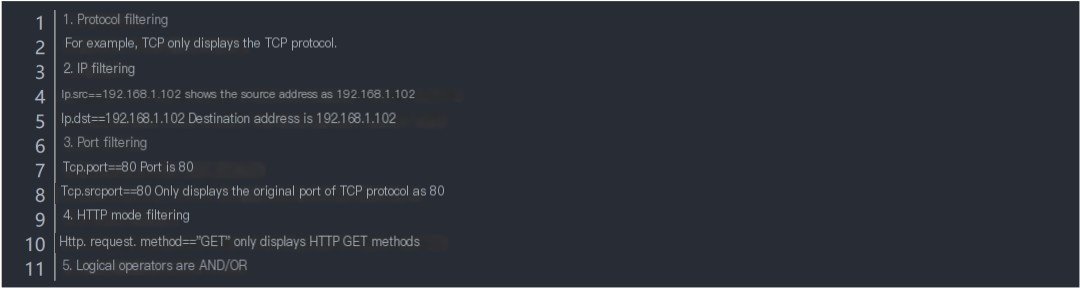
The rules of the filter expression:
Step Ten: The filter rules can be combined, as shown below.http.request.method==“POST” and http and ip.addr==124.114.152.116

IV. Conclusion
Wireshark is closely related to network protocols, involving protocols such as HTTP, FTP, Telnet, network protocol TCP/IP stack, routing protocols (RIP/EIGRP/OSPF/ISIS/BGP), switching protocols (TRUNK/VTP/STP/HSRP), as shown below. Subsequent articles will provide a more detailed explanation combined with packet capture principles.
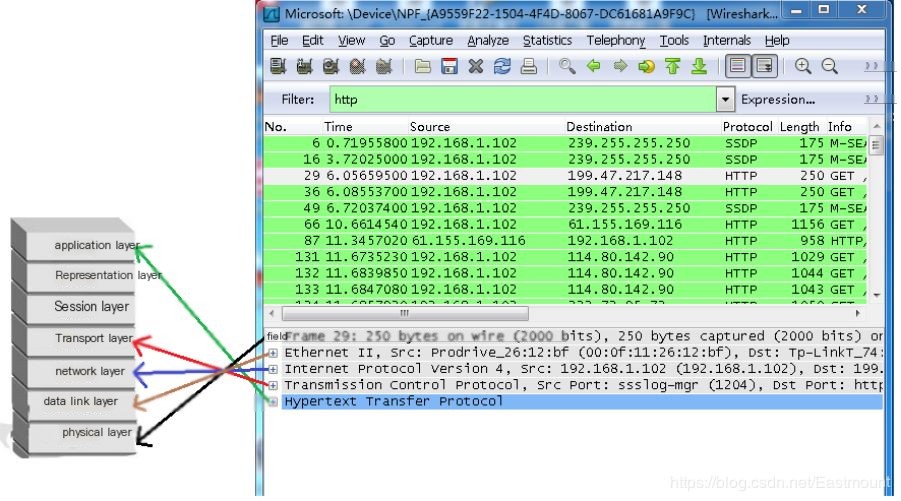
I have a very weak foundation in network security, with so much practical knowledge to learn and numerous academic papers to read. Every day is busy and the process is very arduous, not easy to graduate. However, this bittersweet experience fills me with joy, accompanied by friends, many bloggers, and my distant muse.
Heaven is self-reliant, inspiring gentlemen to continuously strive.
The earth is generous, inspiring gentlemen to carry on with integrity.
Lastly, I hope this foundational article is helpful to you. The author is also a newbie in this field, hoping to progress with you and share motivation.



