This article will focus on analyzing SNMP messages and differentiating between different versions (SNMPv1, v2c, v3)!
4. SNMP Protocol Data Units
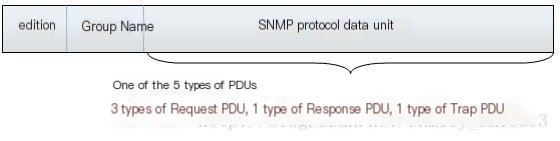
In SNMP management, the management information exchanged between the Network Management Station (NMS) and the agent forms the SNMP message. The basic format of the message is shown in Figure 1:
 >
>
Figure 1
SNMP mainly has three commonly used versions: SNMPv1, SNMPV2c, and SNMPv3.
1. SNMPv1
SNMPv1 is the initial version of the SNMP protocol, providing minimal network management functions. The SMI and MIB in SNMPv1 are relatively simple, with many security flaws.
SNMPv1 uses community name authentication. The community name acts like a password to restrict NMS access to the agent. If the SNMP message carries a community name not recognized by the NMS/Agent, the message will be discarded.
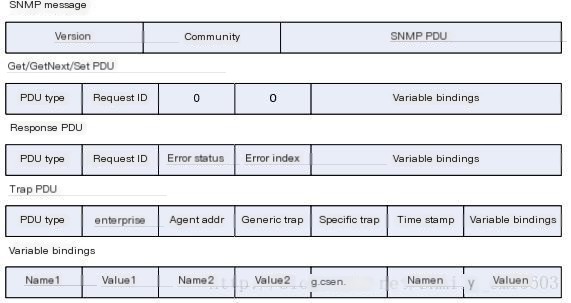
The message format is as shown in Figure 2:
 >
>
Figure 2
As can be seen from the above figure, an SNMP message is mainly composed of Version, Community, and SNMP PDU parts. The main fields in the message are defined as follows:
Version: SNMP version
Community: Community name, used for authentication between the agent and NMS. There are readable and writable community names; if performing Get or GetNext operations, the readable community name is used for authentication; if performing Set operations, the writable community name is used for authentication.
Request ID: Used to match requests and responses, every request is given a globally unique ID by SNMP.
Error status: Used to indicate the conditions encountered while processing the request, including noError, tooBig, noSuchName, badValue, readOnly, genErr.
Error index: Error index. When an abnormal situation occurs, it provides information about the variable in the Variable bindings list that caused the exception.
Variable bindings: A list of variable bindings, consisting of variable name and value pairs.
Enterprise: The type of the Trap source (the device generating the Trap information).
Agent addr: The address of the Trap source.
Generic trap: Generic Trap types, including coldStart, warmStart, linkDown, linkUp, authenticationFailure, egpNeighborLoss, enterpriseSpecific.
Specific trap: Enterprise-specific Trap information.
Time stamp: The time elapsed between the last reinitialization of the network entity and the generation of the Trap, i.e., the value of the sysUpTime object.
The format of the SNMPv1 version message captured by Wireshark is as shown in Figure 3:
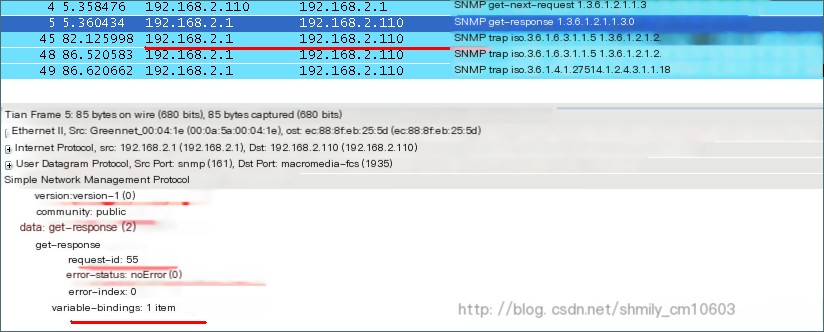
Figure 3
192.168.2.1 is the IP address of the agent, and 192.168.2.110 is the IP address of the NMS
As can be seen from the above figure, the security of the SNMPv1 version is not very good, as the community, which is the community name, can be captured; the tarp operation only has a sent message without a response message.
2. SNMPv2c
SNMPv2c also uses community name authentication. While compatible with SNMPv1, it expands the functions of SNMPv1: it provides more operation types (GetBulk and inform operations); supports more data types (Counter32, etc.); provides richer error codes that can distinguish errors more precisely.
In version v1, there were only error codes for data types, and in version v2c, many more were added, as shown in Figure 4:
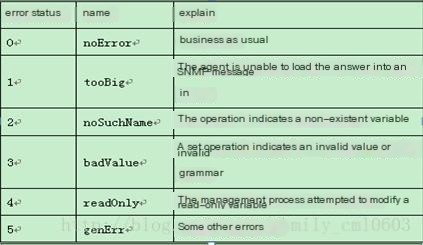
Figure 4
The SNMPv2 message format is shown in Figure 5:
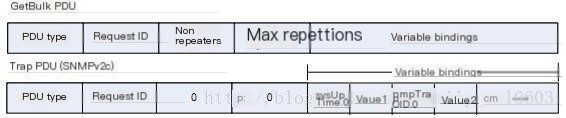
Figure 5
Compared to SNMPv1, SNMPv2c adds GetBulk and inform operation messages. The basic operation type corresponding to the GetBulk operation is the GetNext operation. By setting the Non repeaters and Max repetitions parameters, a large amount of management object data can be efficiently obtained from the agent. The inform operation is like an upgrade of the Trap operation, but what’s the difference between the two? The Trap message will not receive a response after being sent, whereas the inform message will receive a response message after being sent.
The captured message format is as follows:
(1) GetBulk operation, batch data retrieval, as shown in Figure 6:
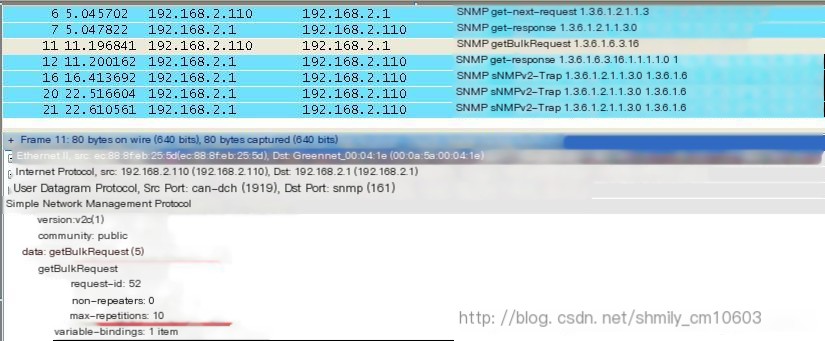
Figure 6
(2) Inform operation, you can see its difference from the Trap operation, with a response message, as shown in Figure 7:
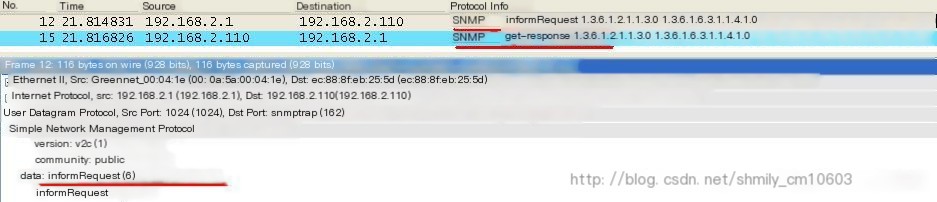
Figure 7
SNMPv2c modified the Trap message format. The SNMPv2c Trap PUD uses the format of the SNMPv1 Get/GetNext/Set PDU and constructs messages by using sysUpTime and snmpTrapOID as variables in the Variable bindings (refer to Figure 3 for the get-next response and Figure 9 for the trap in SNMPv2 for comparison). The message format is as follows:
(1) The tarp message format of the SNMPv1 version is shown in Figure 8:
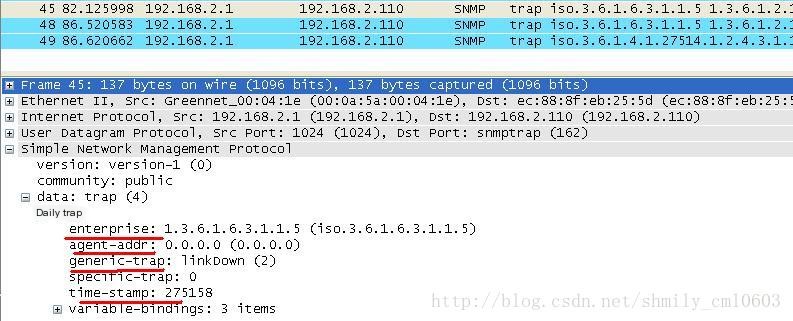
Figure 8
(2) The Trap message format of SNMPv2 is shown in Figure 9:
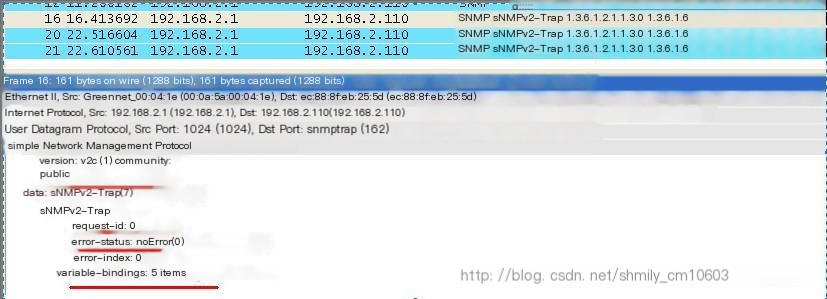
Figure 9
3. SNMPv3
SNMPv3 has mainly been enhanced in terms of security, adopting USM and VACM technologies. USM provides authentication and encryption functions, while VACM determines whether a user is allowed to access specific MIB objects and the manner of access.
USM (User-Based Security Model)
USM introduces the concepts of username and group, allowing the setting of authentication and encryption functions. Authentication is used to verify the legitimacy of the message sender, preventing access by unauthorized users; encryption is used to encrypt messages transmitted between NMS and Agent, to prevent eavesdropping. By combining authentication and encryption, a higher level of security is provided for communication between NMS and Agent.
VACM (View-Based Access Control Model)
VACM technology defines five elements: group, security level, context, MIB view, and access policies. These elements simultaneously determine whether a user has access permissions, and only users with access permissions can manage and operate objects. Different groups can be defined on the same SNMP entity, with groups bound to MIB views, and multiple users can be defined within a group. When accessing with a specific username, only objects defined by the corresponding MIB view can be accessed.
Due to the increase in content in version v3, it has been decided to explain SNMPv3 in more detail in the next article.



