Wireshark can trace the communication process of network protocols. This section reviews the communication process of the TCP protocol, including connection termination, based on an understanding of Wireshark’s usage.
TCP (Transmission Control Protocol) is a connection-oriented, reliable, byte-stream-based transmission layer communication protocol.
TCP is designed to fit into a layered protocol hierarchy that supports multi-network applications, providing reliable communication services between paired processes in host computers connected to different but interconnected communication networks. From the network model-to-protocol correspondence table, we find that the TCP protocol is located at the transport layer.
 />
/>
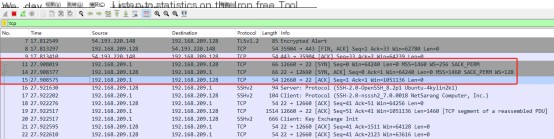
From the Wireshark interface image, we can observe that packets 11, 14, and 15 are the three-way handshake process that establishes a TCP connection.
 />
/>
1. First handshake (SYN=1, seq=x): The client sends a TCP packet with the SYN flag set to 1, indicating the port of the server it intends to connect to and the initial sequence number X, saved in the Sequence Number field of the header. After sending, the client enters the SYN_SEND state.
2. Second handshake (SYN=1, ACK=1, seq=y, ACKnum=x+1): The server sends back an acknowledgment (ACK) packet. Both the SYN and ACK flags are set to 1. The server selects its ISN (Initial Sequence Number), places it in the Seq field, and sets the Acknowledgement Number to the client’s ISN plus one, i.e., X+1. After sending, the server enters the SYN_RCVD state.
3. Third handshake (ACK=1, ACKnum=y+1): The client sends another acknowledgment (ACK) packet, with the SYN flag at 0 and the ACK flag at 1. It sends back to the server by placing the acknowledgment number from the server’s ACK field plus one in the acknowledgment field and writes the ISN plus one in the data segment. After sending, the client enters the ESTABLISHED state, and when the server receives this packet, it also enters the ESTABLISHED state, ending the TCP handshake.
From the Wireshark interface image, we can observe that packets 77, 78, 79/80 are part of the four-way handshake process that terminates a TCP connection.
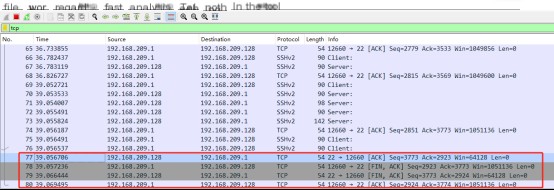
1. First wave (FIN=1, seq=x): The client sends a packet with the FIN flag set to 1, indicating it has no more data to send but can still receive data. After sending, the client enters the FIN_WAIT_1 state.
2. Second wave (ACK=1, ACKnum=x+1): The server acknowledges the client’s FIN packet by sending an acknowledgment packet, indicating it has received the client’s request to close the connection but is not yet ready to close. After sending, the server enters the CLOSE_WAIT state, and the client enters the FIN_WAIT_2 state upon receiving this acknowledgment, waiting for the server to close the connection.
3. Third wave (FIN=1, seq=y): When the server is ready to close the connection, it sends a connection termination request to the client, with the FIN flag set to 1. After sending, the server enters the LAST_ACK state, waiting for the final acknowledgment from the client.
4. Fourth wave (ACK=1, ACKnum=y+1): The client receives the server’s close request and sends an acknowledgment packet, entering the TIME_WAIT state, waiting for possible retransmissions of ACKs. After the server receives this acknowledgment, it closes the connection and enters the CLOSED state. The client then waits for a fixed period (two maximum segment lifetimes, 2MSL) and, if no ACK is received from the server, assumes the server has closed the connection properly and closes itself, entering the CLOSED state.
Analyzing the above communication process deepens our understanding of the TCP protocol communication process and strengthens our comprehension of how Wireshark supports packet analysis.
TCP ensures reliability through the following mechanisms:
1. Acknowledgment and retransmission: The receiver acknowledges upon receiving a message, and if the sender does not receive an acknowledgment within a certain time, it retransmits.
2. Data verification.
3. Reasonable data fragmentation and ordering.
4. Flow control: Prevents packet loss by allowing the receiver to signal the sender to reduce its sending rate when it cannot process the data in time.
5. Congestion control: Reduces data transmission when the network is congested.



