Hello everyone, I am the Architect, an architect who writes code and poetry. Today, let’s discuss Wireshark Network Packet Capture (Part 1) – Packets, Coloring Rules, and Prompts. I hope this will help everyone improve!!! You can find more details [here](https://cloud.tencent.com/developer/article/1934391?from_column=20421&from=20421). Also, we will explore the significance of TCP Dup ACK in network analysis.
1. Packet Details: TCP Dup ACK
Packet Details Panel contains the following information and is mainly used for analyzing detailed packet information.
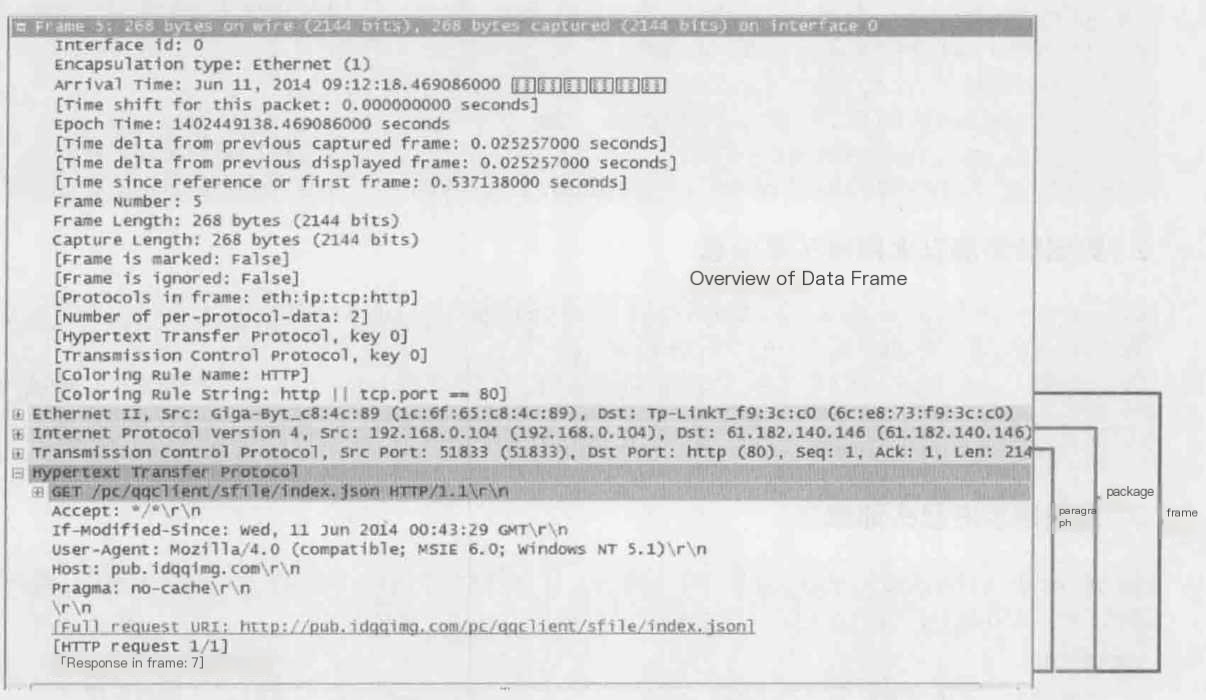
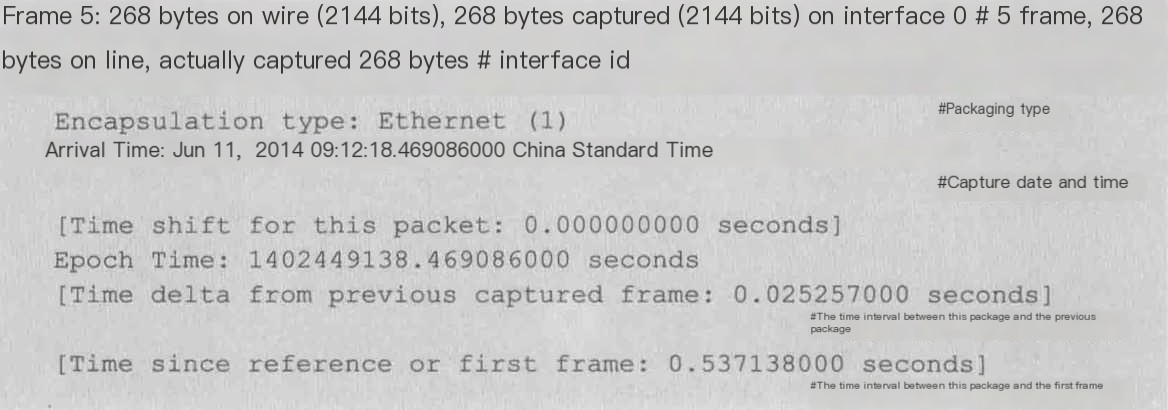
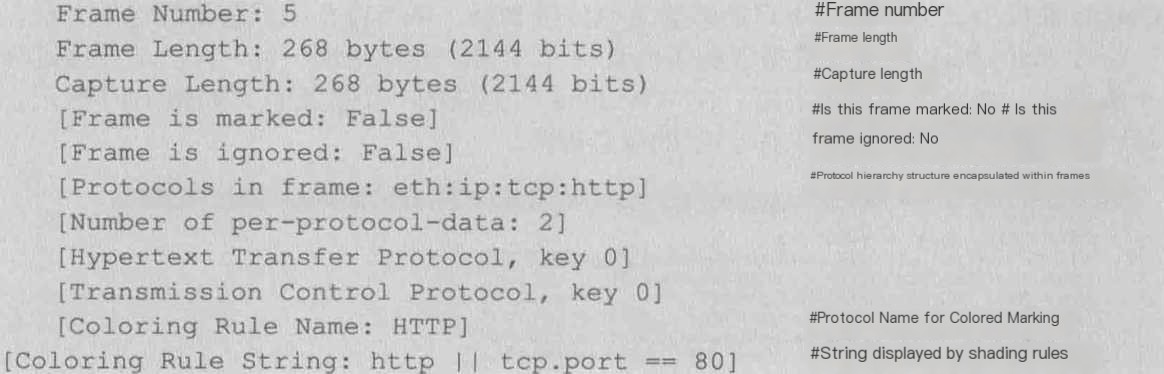
Frame: Physical Layer, Data Link Layer
Packet: Network Layer
Segment: Transport Layer, Application Layer
1) Frame
Overview of Physical Layer Data Frame
2) Ethernet II
Data Link Layer Ethernet Frame Header Information
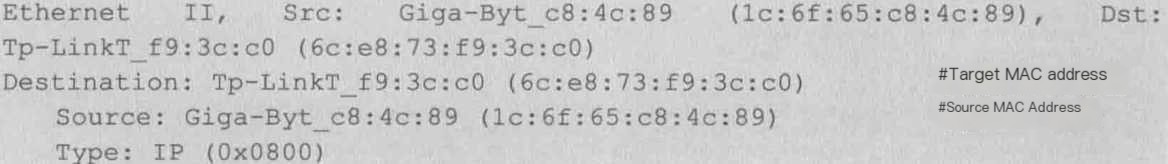
3) Internet Protocol Version 4
Internet Layer IP Packet Header Information
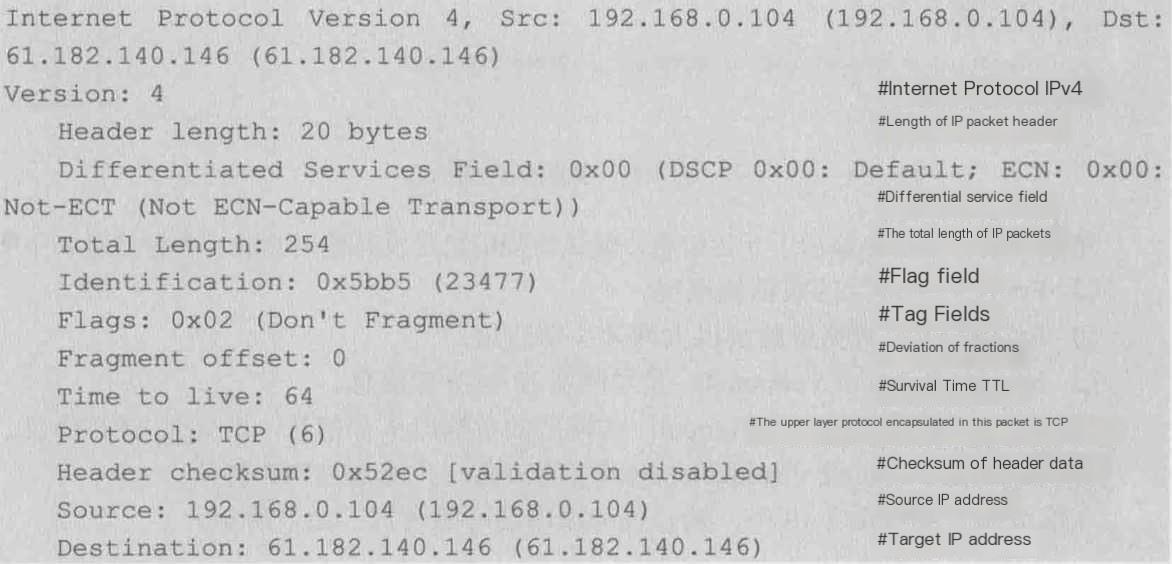
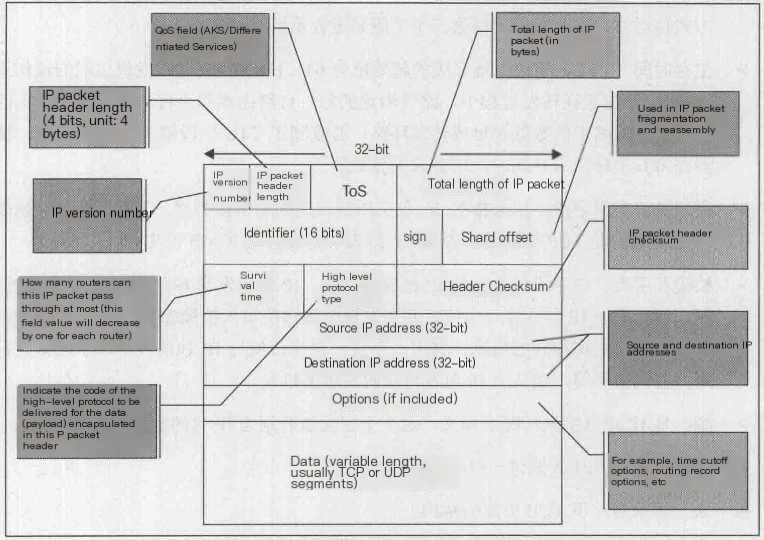
IP Packet Header:
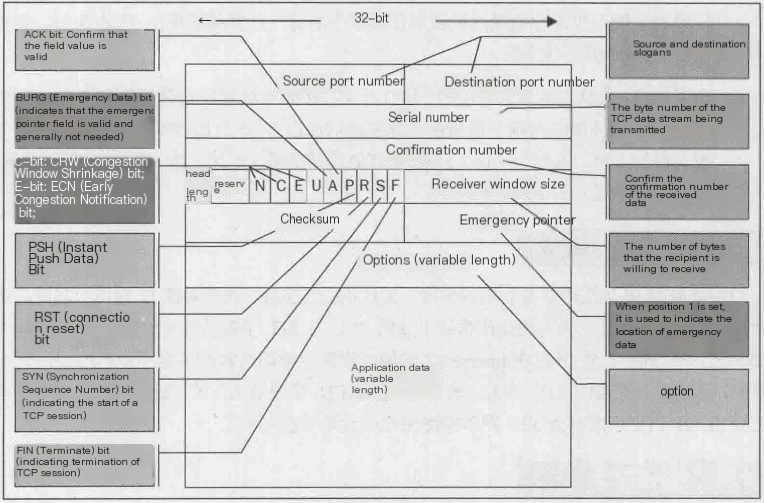
4) Transmission Control Protocol
Transport Layer Segment Header Information, here using TCP protocol
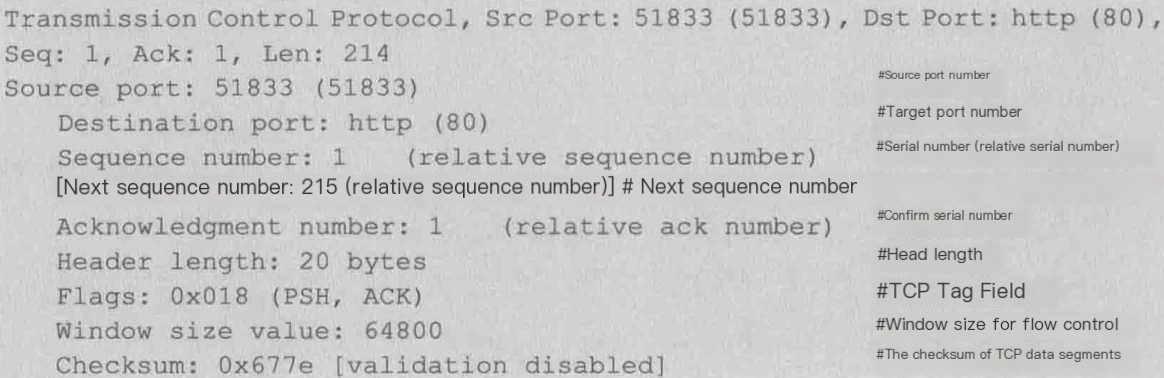
TCP Packet Header:
5) Hypertext Transfer Protocol
Application Layer Information, here using HTTP protocol
2. Coloring Rules
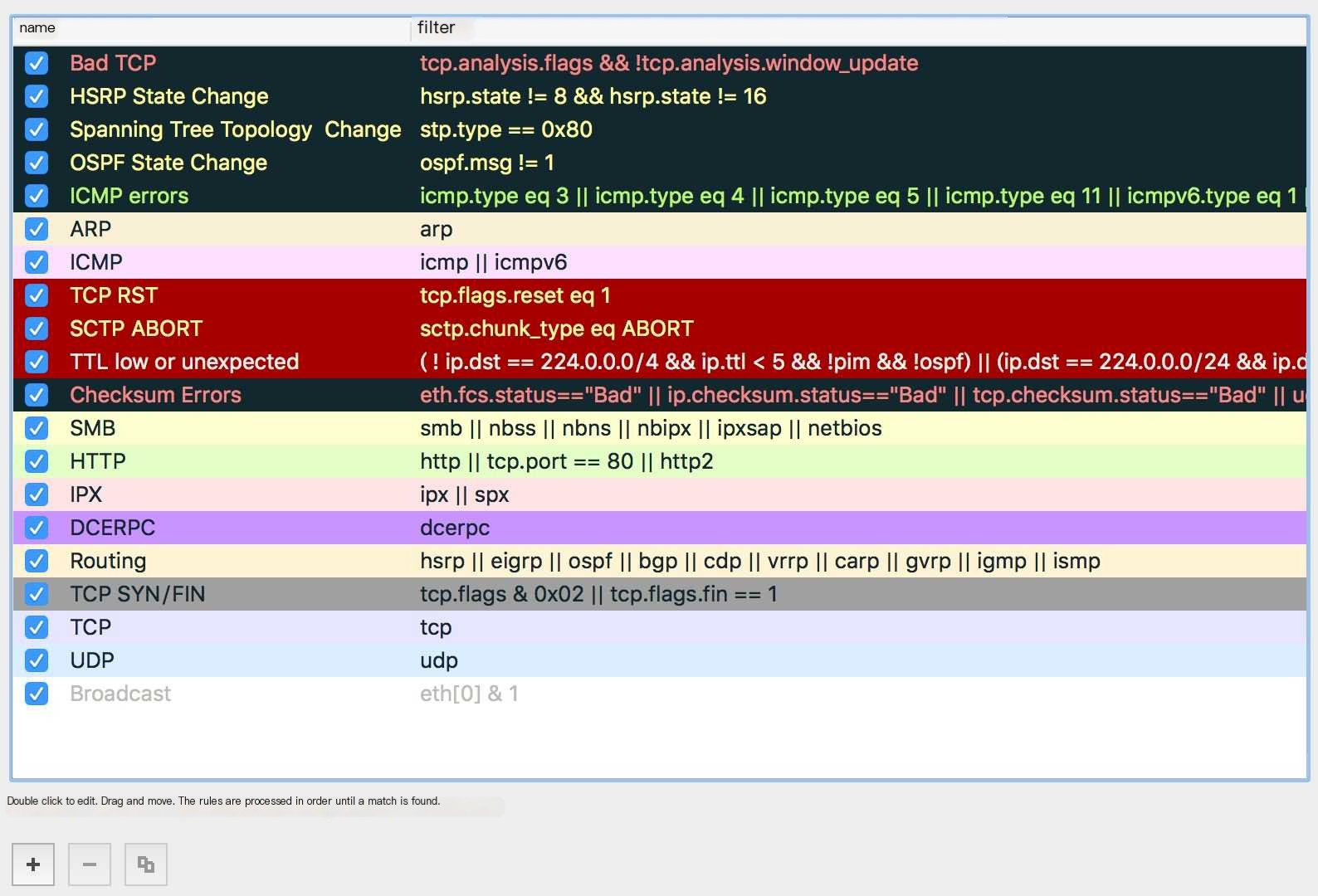
Wireshark has a default set of coloring rules, which can be expanded in the Packet Details panel to view the coloring rules.
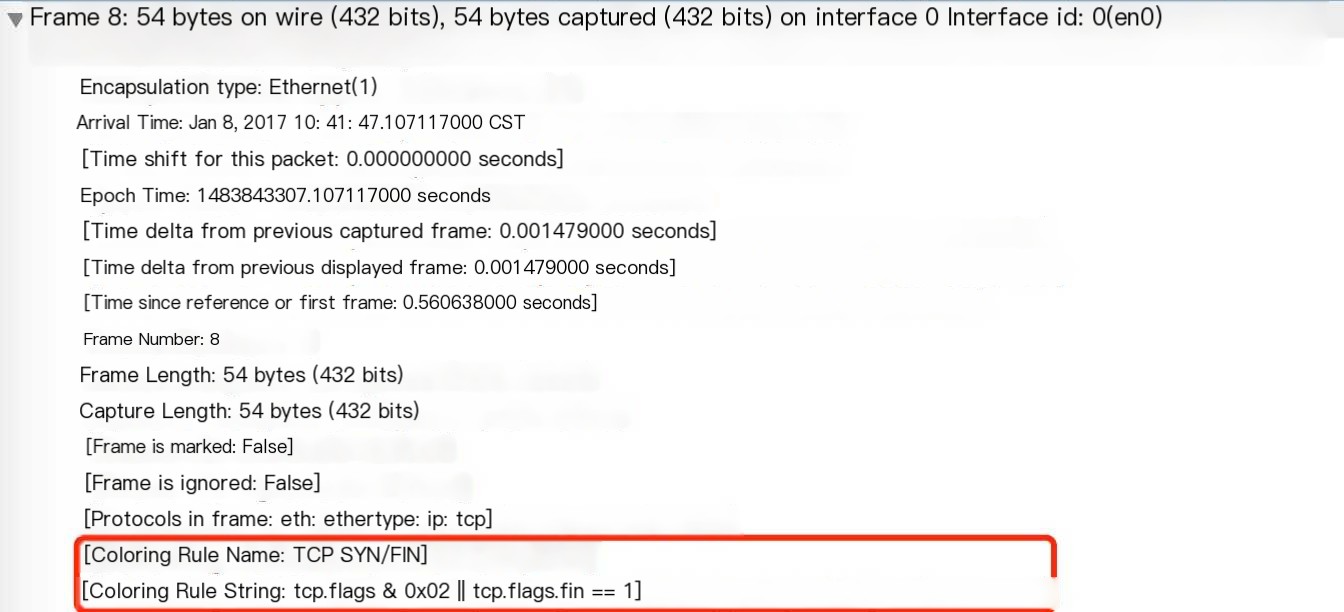
In View | Coloring Rules, open the Coloring Rules window where you can create, delete, select, or deselect rules.
3. Wireshark Prompts
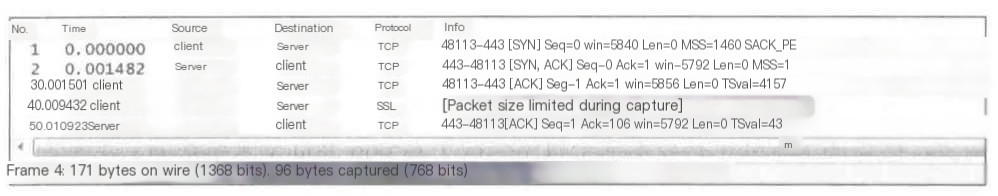
1) Packet size limited during capture
This indicates that the marked packet was not fully captured. This is generally due to packet capture methods, with some operating systems defaulting to capture only the first 96 bytes of each frame.
Packet 4 is 171 bytes in total, but only 96 bytes were captured.
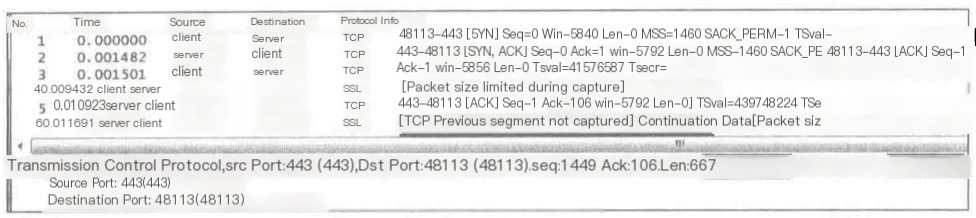
2) TCP Previous segment not captured
If Wireshark finds that the Seq of a subsequent packet is greater than Seq+Len, it realizes a segment is missing.
If the missing segment cannot be found in the entire network packet (excluding out-of-order packets), it will issue a prompt.
Packet 6 has a Seq of 1449 which is greater than Packet 5’s Seq+Len=1+1=1, indicating that a packet of 1448 bytes is missing, specifically “Seq=1, Len=1448”.
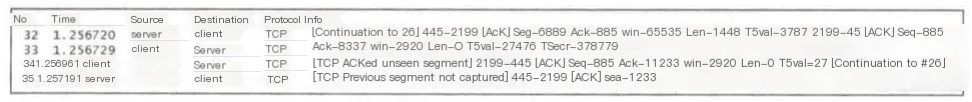
3) TCP ACKed unseen segment
When Wireshark discovers that the packet being acknowledged was not captured, it will issue a prompt.
Packet 32 Seq+Len=6889+1448=8337, indicating that the next packet Seq=8337.
However, we see Packet 35 Seq=11233, meaning that data from 8337 to 11232 was not captured.
4) TCP Out-of-Order
When Wireshark finds the Seq number of a subsequent packet is less than the Seq+Len of the previous packet, it assumes an out-of-order and issues a prompt.
Packet 3362 Seq is less than Packet 3360 Seq, indicating an out-of-order.

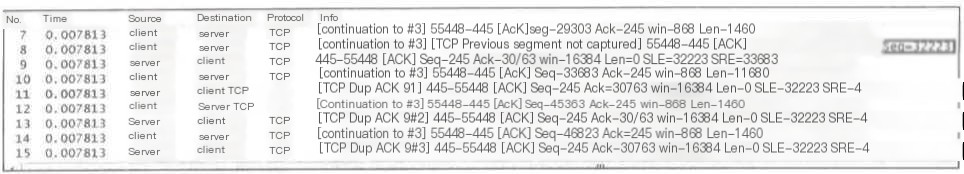
5) TCP Dup ACK
When out-of-order or packet loss occurs, the receiver will receive packets with Seq numbers greater than expected. Each such packet prompts an ACK with the expected Seq value, notifying the sender.
Packet 7 expects the next Seq=30763, but Packet 8 Seq=32223, indicating that Packet Seq=30763 was lost, with Packet 9 sending Ack=30763, expressing “I want Seq=30763.”
Packet 10, 12, and 14 are all greater than 30763, triggering a response with an Ack for each.
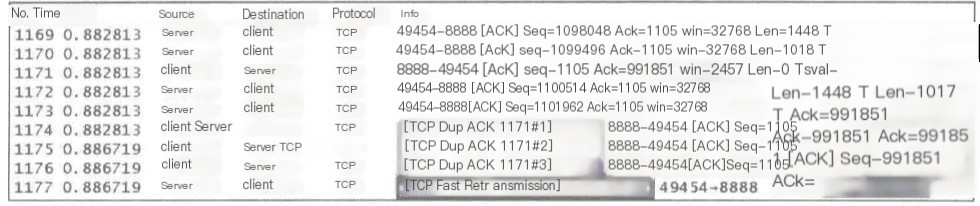
6) TCP Fast Retransmission
When a sender receives 3 or more 【TCP Dup ACK】, it realizes the previous packet might be lost and retransmits it quickly.
7) TCP Retransmission
If a packet is truly lost and there are no subsequent packets to trigger 【Dup Ack】 at the receiver, it will not retransmit quickly.
In such cases, the sender must wait for a timeout to retransmit.
After Packet 1053 was sent, no corresponding Ack was received, forcing a retransmission after more than 100 milliseconds.

8) TCP zerowindow
“win” in a packet represents the size of the receive window. When Wireshark detects a “win=0” in a packet, it generates a prompt.
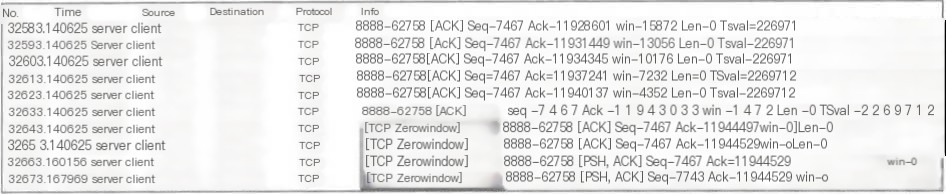
9) TCP window Full
This prompt indicates that the sender of the packet has exhausted the receive window advertised by the other party.
When Wireshark calculates that the Middle East has 65535 bytes unacknowledged, it issues this prompt.
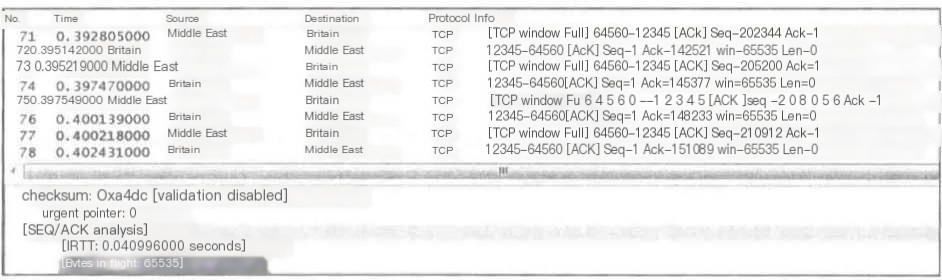
【TCP window Full】 means the sender cannot temporarily send data;
【TCP zerowindow】 means the sender cannot temporarily receive data.
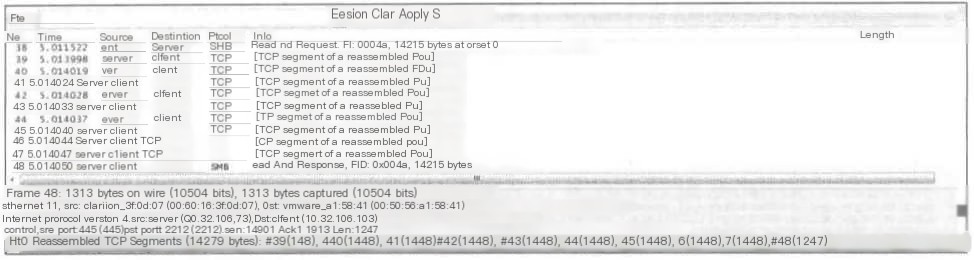
10) TCP segment of a reassembled PDU
Wireshark can virtually group TCP packets belonging to the same application layer PDU.
After receiving large messages from the upper layer, the TCP layer breaks them into segments for transmission. If a host responds to a query or command with a lot of data exceeding the maximum TCP MSS,
the host will send multiple packets to transmit this data (note: these packets are not fragmented).
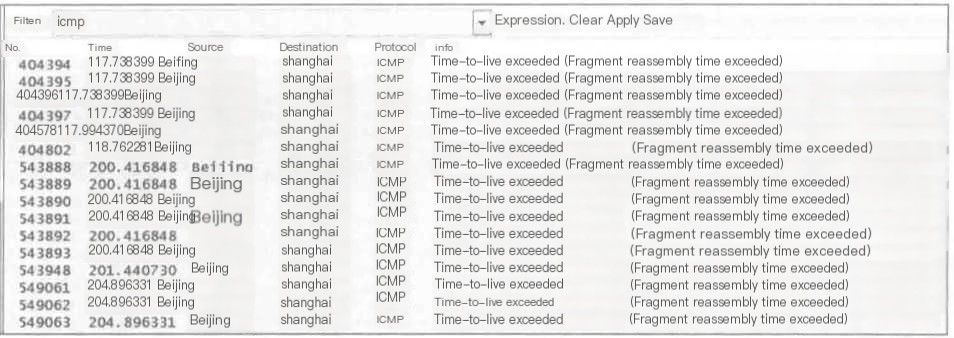
11) Time-to-live exceeded (Fragment reassembly time exceeded)
Indicates that the sender of this packet previously received some fragments, but for some reasons could not assemble them timely.
Today’s article ends here, thank you for reading, Java Architects Must See wish you promotion and salary increase, and good luck every year.



