After being released on bail, Ann Dekaf disappeared! Fortunately, investigators were closely monitoring her network activity using the SMTP protocol before she left town.
The police chief said, “We believe Ann may have contacted her secret lover, Mr. X, before leaving, and the packet capture might contain clues about her whereabouts.”
You are a professional investigator, and your task is to find out what emails Ann sent, where she went, and gather evidence, including:
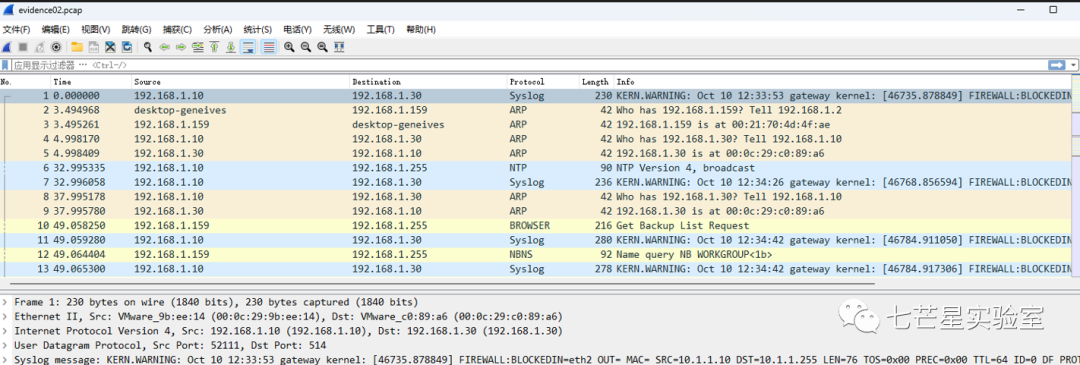
Analysis process: Step 1: Use Wireshark to open data packets.
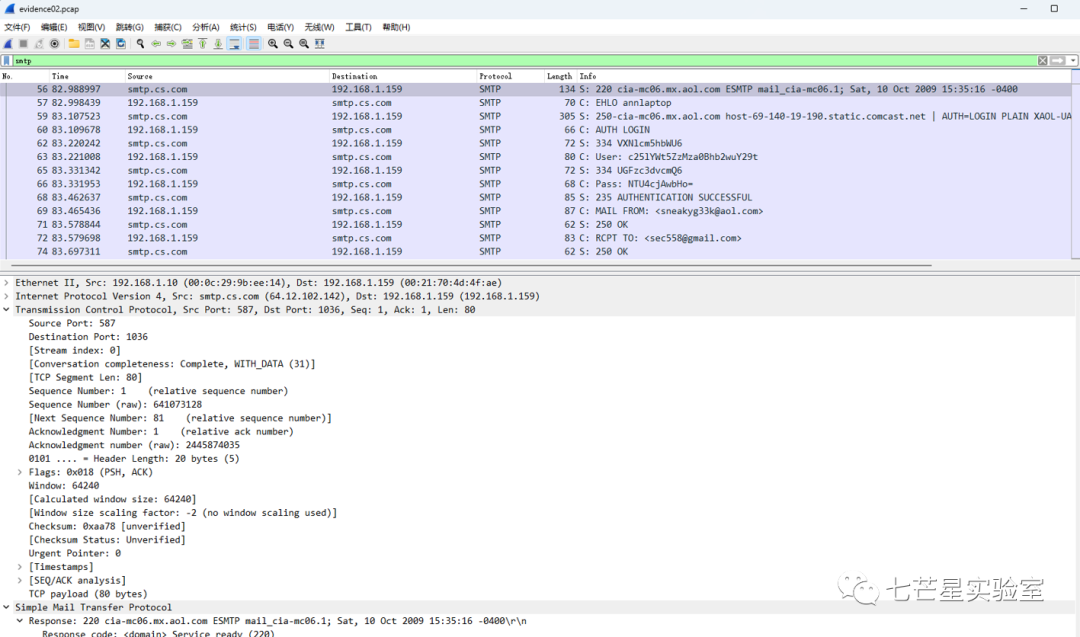
Step 2: Since email communication is being used, we can directly filter the SMTP protocol.
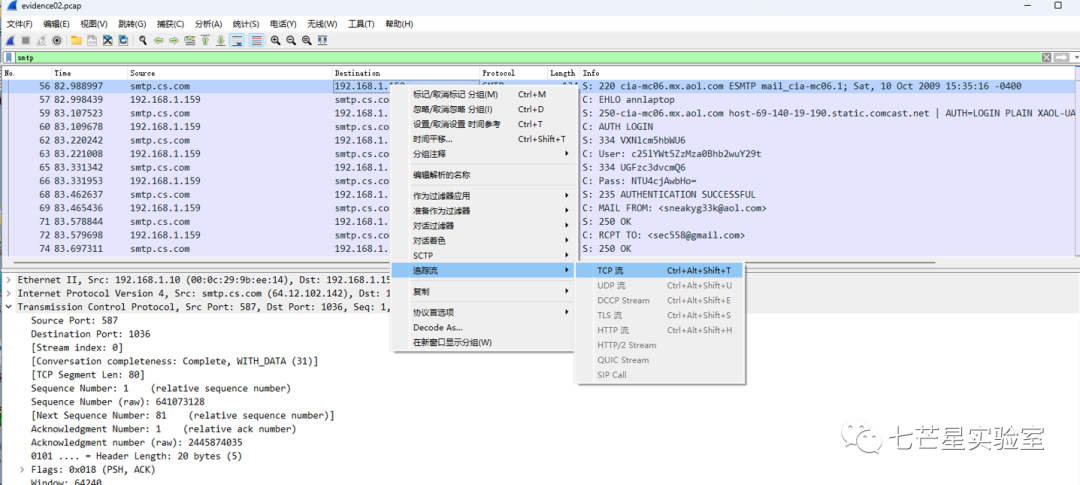
Step 3: Directly trace the TCP data stream to obtain communication data information.
From below, you can see the answer to our first question:
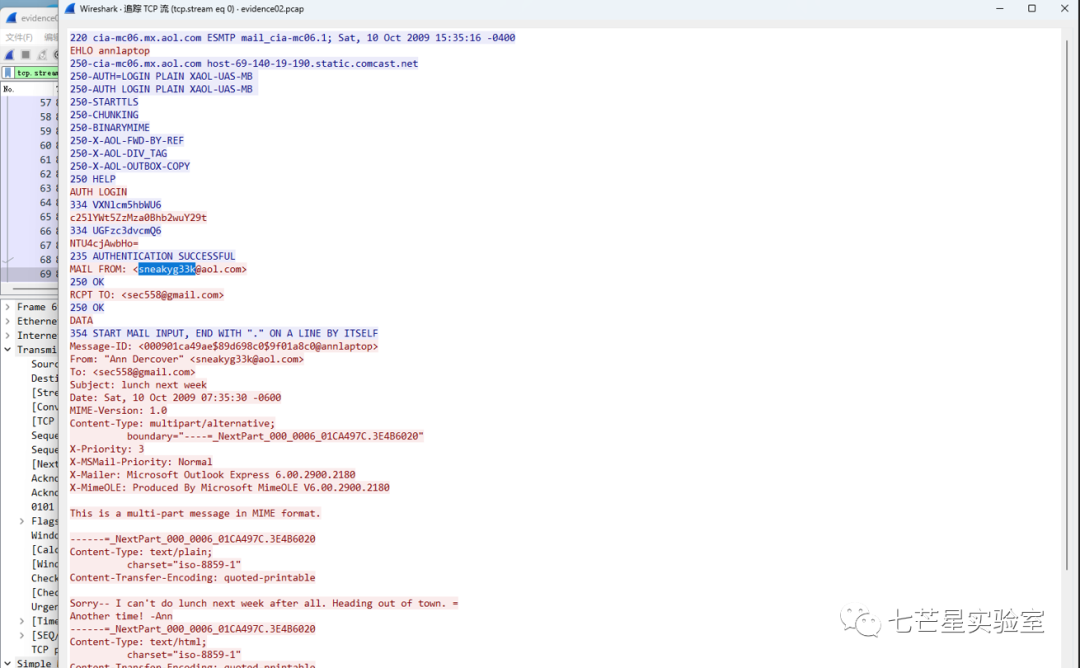
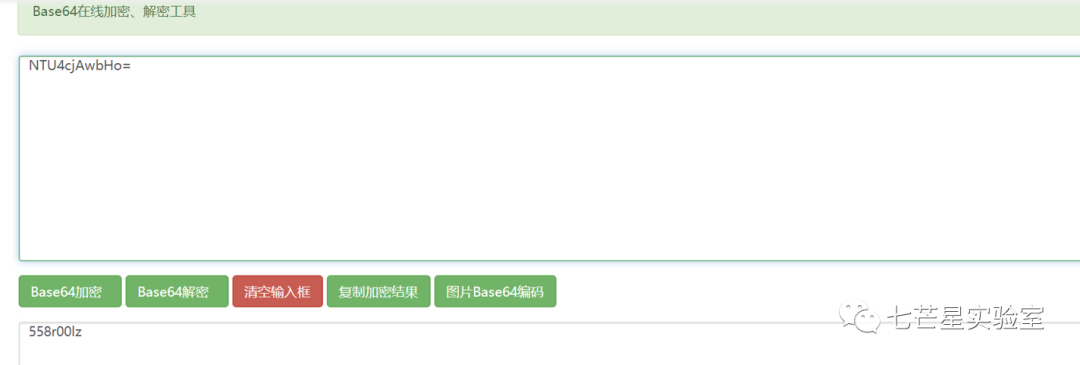
At the beginning of the data packet, we can see there is some authenticated message information. The SMTP 334 response code indicates authentication credentials are needed. The server sends a response to the client, requesting the client to input a username and password for authentication, which is a method of authentication in SMTP. Subsequently, the client performed an authentication, indicated by the SMTP 235 response code, meaning authentication was successful. When the client sends authentication information (e.g., username and password) to the SMTP server, the server returns the 235 response code to indicate successful authentication. The credentials are encoded using Base64, which we can decode to get the answer to the second question:
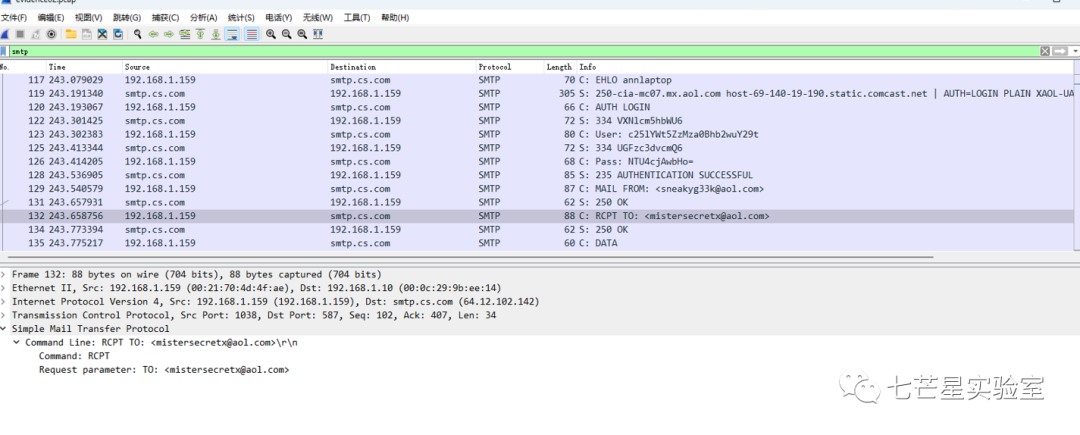
Simultaneously, when we look at the current packet content, we found nothing, so we continue tracking to discover the second mail reception address.
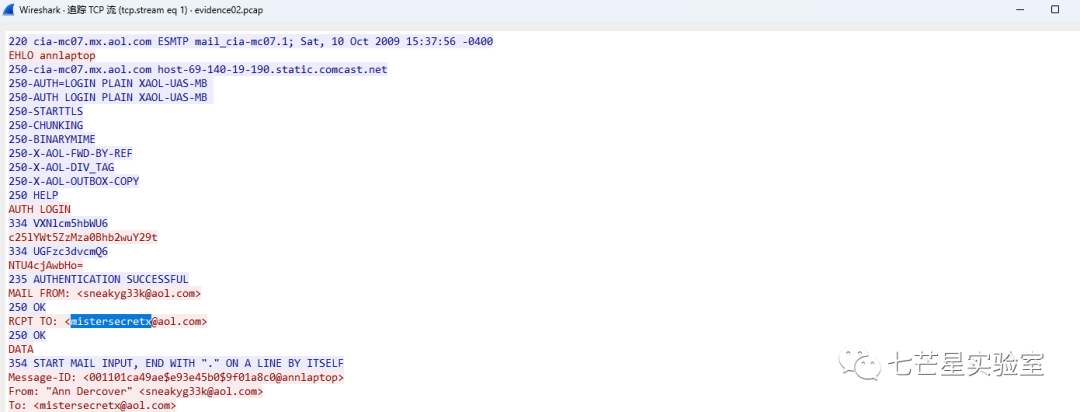
Tracking the current data packet stream information, we discovered encrypted communication text content, confirming that the current packet’s receiving mail address is the answer we are seeking for the third question:
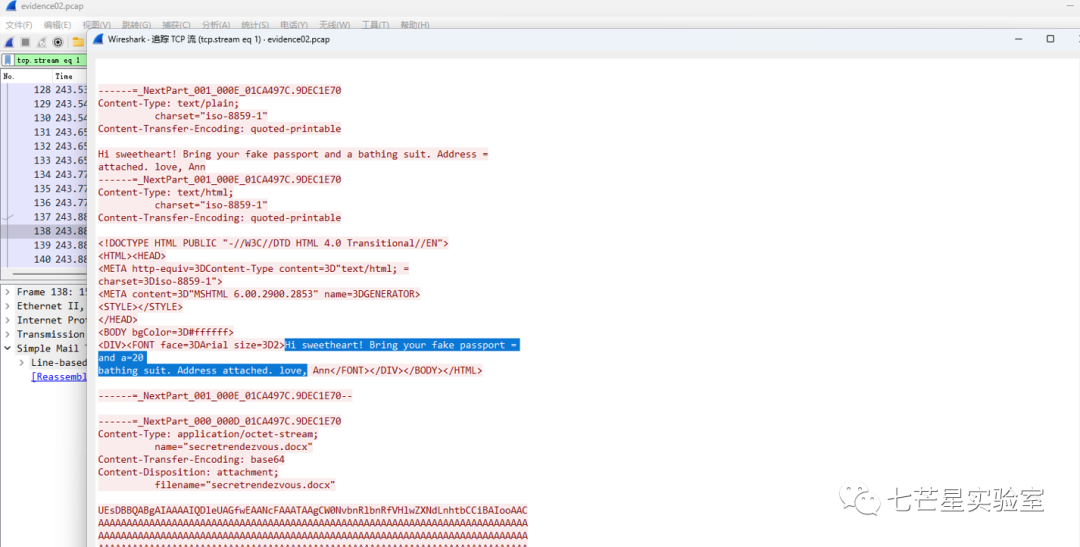
From the data packet, we obtained the answer to the fourth question:
From the data packet, we also obtained the answer to the fifth question:
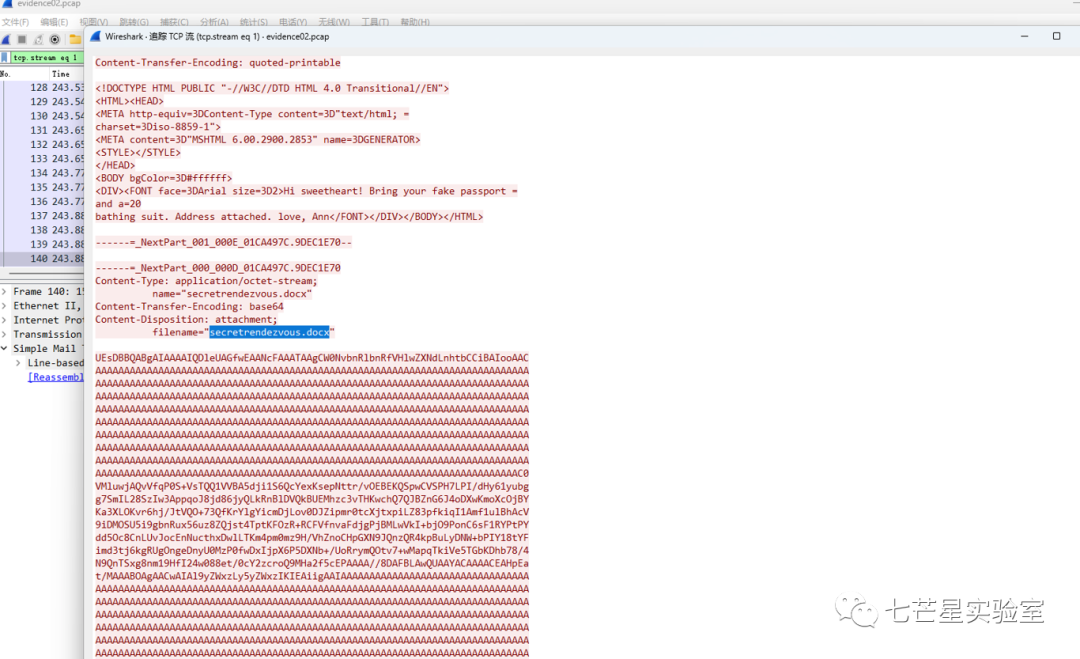
From the above packet, we can see the packet header already indicates that the current packet uses Base64 encoding. Thus, we will decode it and download the zip file.
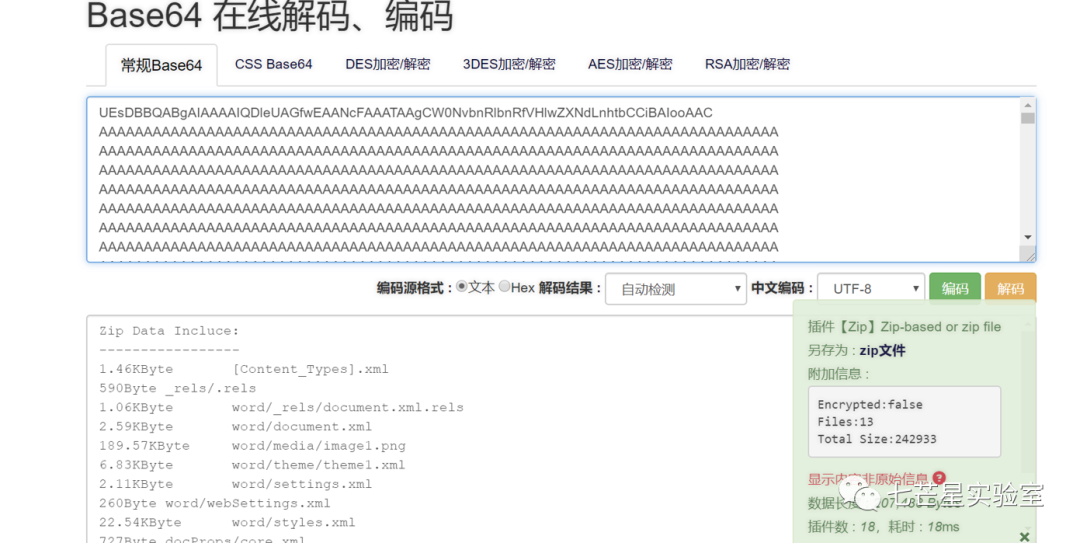
The website will default to treating this as a zip file because docx files and zip files share the same format. Therefore, after downloading it, we just need to rename it as a docx file and then open the file to obtain the content, which is the answer to the fifth question:
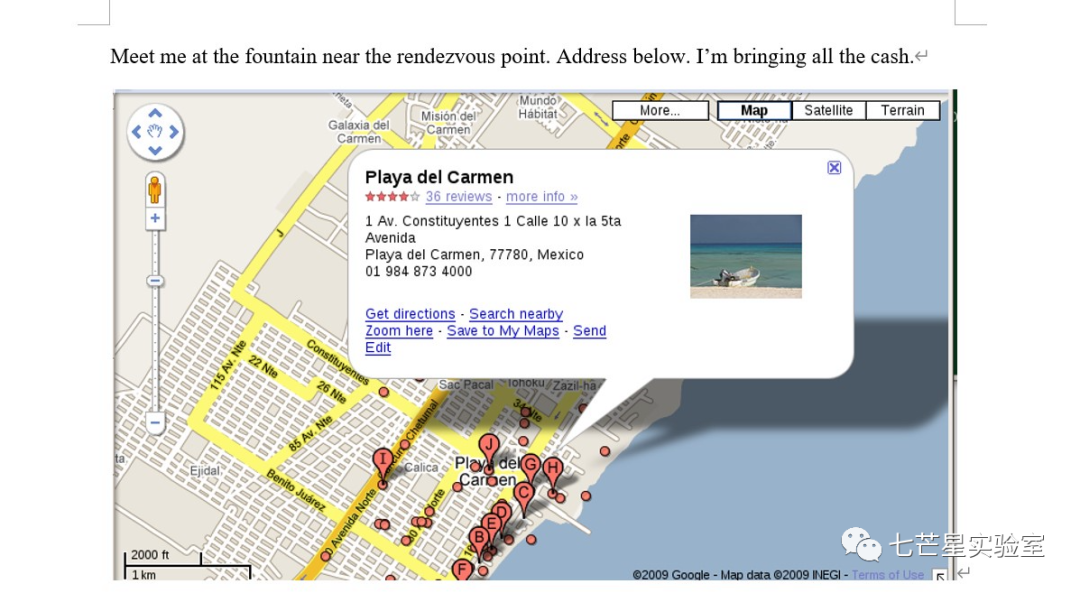
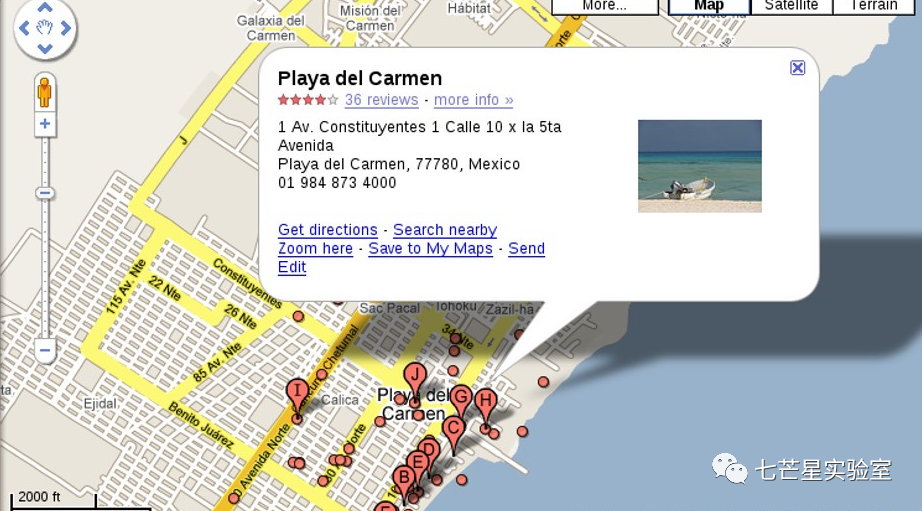
From the above file, we can see the rendezvous address information, which is the answer to the sixth question:
The seventh question requires us to obtain the Md5sum value information of an embedded image in the Word document. However, it is important to note that the image cannot be directly saved elsewhere and then have its MD5 value calculated. Instead, we can take an alternative route by renaming the docx file to a zip file, extracting the source file information from the zip file, and then calculating the MD5 value.
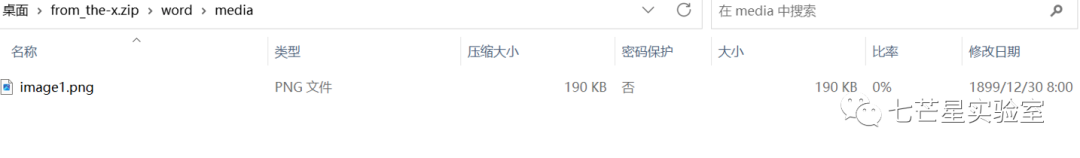
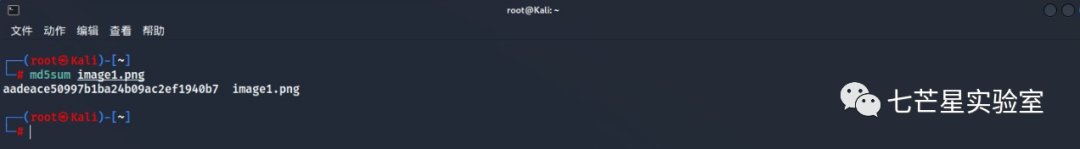
Then, in Kali, use MD5sum to calculate the file’s Md5 value to get the answer to the final question:
This article primarily focuses on SMTP, the email communication protocol, as the basis to analyze and secure evidence by examining network data packets. It primarily involves the use of Wireshark display filters, SMTP packet analysis, communication data source file recovery, file MD5 calculation forensics, and other related knowledge. Overall, it is considered a very good example.



